WO2015118840A1 - 通信装置、車両制御装置、および車両制御システム - Google Patents
通信装置、車両制御装置、および車両制御システム Download PDFInfo
- Publication number
- WO2015118840A1 WO2015118840A1 PCT/JP2015/000388 JP2015000388W WO2015118840A1 WO 2015118840 A1 WO2015118840 A1 WO 2015118840A1 JP 2015000388 W JP2015000388 W JP 2015000388W WO 2015118840 A1 WO2015118840 A1 WO 2015118840A1
- Authority
- WO
- WIPO (PCT)
- Prior art keywords
- communication
- vehicle control
- authentication
- key
- vehicle
- Prior art date
- Legal status (The legal status is an assumption and is not a legal conclusion. Google has not performed a legal analysis and makes no representation as to the accuracy of the status listed.)
- Ceased
Links
Images
Classifications
-
- B—PERFORMING OPERATIONS; TRANSPORTING
- B60—VEHICLES IN GENERAL
- B60R—VEHICLES, VEHICLE FITTINGS, OR VEHICLE PARTS, NOT OTHERWISE PROVIDED FOR
- B60R25/00—Fittings or systems for preventing or indicating unauthorised use or theft of vehicles
- B60R25/20—Means to switch the anti-theft system on or off
- B60R25/24—Means to switch the anti-theft system on or off using electronic identifiers containing a code not memorised by the user
-
- B—PERFORMING OPERATIONS; TRANSPORTING
- B60—VEHICLES IN GENERAL
- B60R—VEHICLES, VEHICLE FITTINGS, OR VEHICLE PARTS, NOT OTHERWISE PROVIDED FOR
- B60R25/00—Fittings or systems for preventing or indicating unauthorised use or theft of vehicles
- B60R25/20—Means to switch the anti-theft system on or off
- B60R25/2018—Central base unlocks or authorises unlocking
-
- B—PERFORMING OPERATIONS; TRANSPORTING
- B60—VEHICLES IN GENERAL
- B60R—VEHICLES, VEHICLE FITTINGS, OR VEHICLE PARTS, NOT OTHERWISE PROVIDED FOR
- B60R25/00—Fittings or systems for preventing or indicating unauthorised use or theft of vehicles
- B60R25/20—Means to switch the anti-theft system on or off
- B60R25/23—Means to switch the anti-theft system on or off using manual input of alphanumerical codes
-
- G—PHYSICS
- G07—CHECKING-DEVICES
- G07C—TIME OR ATTENDANCE REGISTERS; REGISTERING OR INDICATING THE WORKING OF MACHINES; GENERATING RANDOM NUMBERS; VOTING OR LOTTERY APPARATUS; ARRANGEMENTS, SYSTEMS OR APPARATUS FOR CHECKING NOT PROVIDED FOR ELSEWHERE
- G07C9/00—Individual registration on entry or exit
- G07C9/00174—Electronically operated locks; Circuits therefor; Nonmechanical keys therefor, e.g. passive or active electrical keys or other data carriers without mechanical keys
- G07C9/00309—Electronically operated locks; Circuits therefor; Nonmechanical keys therefor, e.g. passive or active electrical keys or other data carriers without mechanical keys operated with bidirectional data transmission between data carrier and locks
-
- G—PHYSICS
- G07—CHECKING-DEVICES
- G07C—TIME OR ATTENDANCE REGISTERS; REGISTERING OR INDICATING THE WORKING OF MACHINES; GENERATING RANDOM NUMBERS; VOTING OR LOTTERY APPARATUS; ARRANGEMENTS, SYSTEMS OR APPARATUS FOR CHECKING NOT PROVIDED FOR ELSEWHERE
- G07C9/00—Individual registration on entry or exit
- G07C9/00174—Electronically operated locks; Circuits therefor; Nonmechanical keys therefor, e.g. passive or active electrical keys or other data carriers without mechanical keys
- G07C9/00309—Electronically operated locks; Circuits therefor; Nonmechanical keys therefor, e.g. passive or active electrical keys or other data carriers without mechanical keys operated with bidirectional data transmission between data carrier and locks
- G07C2009/00555—Electronically operated locks; Circuits therefor; Nonmechanical keys therefor, e.g. passive or active electrical keys or other data carriers without mechanical keys operated with bidirectional data transmission between data carrier and locks comprising means to detect or avoid relay attacks
-
- G—PHYSICS
- G07—CHECKING-DEVICES
- G07C—TIME OR ATTENDANCE REGISTERS; REGISTERING OR INDICATING THE WORKING OF MACHINES; GENERATING RANDOM NUMBERS; VOTING OR LOTTERY APPARATUS; ARRANGEMENTS, SYSTEMS OR APPARATUS FOR CHECKING NOT PROVIDED FOR ELSEWHERE
- G07C2209/00—Indexing scheme relating to groups G07C9/00 - G07C9/38
- G07C2209/60—Indexing scheme relating to groups G07C9/00174 - G07C9/00944
- G07C2209/63—Comprising locating means for detecting the position of the data carrier, i.e. within the vehicle or within a certain distance from the vehicle
Definitions
- the present disclosure relates to a communication device capable of communicating with a vehicle control device, a vehicle control device, and a vehicle control system.
- a communication device that can communicate with a vehicle control device a communication device that is used for authentication with the vehicle control device is known (for example, see Patent Document 1).
- This communication device functions as a key of the vehicle control device by performing authentication through communication with the vehicle control device.
- the function can be restricted by setting such as prohibiting the function of opening the trunk of the vehicle.
- a vehicle control device that performs vehicle control preset in the vehicle when authentication with the authentication device possessed by the user is successful, a portable device that functions as the authentication device, The communication device configured to be communicable with both of the communication device functions as the authentication device, and performs wireless communication with the portable device when performing authentication with the vehicle control device.
- a communication device and an authentication device that performs authentication with the vehicle control device when wireless communication with the portable device is established.
- the communication device can be used as a device for performing authentication with the vehicle control device only within a communicable range with the portable device. Therefore, when this communication apparatus is owned by a person other than the owner of the vehicle, it is possible to limit the area in which the vehicle can be controlled.
- a vehicle control device that performs preset vehicle control in a vehicle when authentication with an authentication device possessed by a user is successful is described in the first aspect as the authentication device.
- the communication device is configured to be communicable.
- the communication device can be used as a device for performing authentication with the vehicle control device only within a communicable range with the portable device. Therefore, when this communication apparatus is owned by a person other than the owner of the vehicle, it is possible to limit the area in which the vehicle can be controlled.
- the vehicle control system functions as a vehicle control device that performs vehicle control preset in the vehicle when authentication with the authentication device possessed by the user is successful, and the authentication device.
- a communication device configured to be communicable with both the vehicle control device and the portable device.
- the communication device is configured as the communication device described in the first aspect.
- the said vehicle control apparatus is comprised as a vehicle control apparatus as described in a 2nd aspect.
- the communication device can be used as a device for performing authentication with the vehicle control device only within a communicable range with the portable device. Therefore, when this communication apparatus is owned by a person other than the owner of the vehicle, it is possible to limit the area in which the vehicle can be controlled.
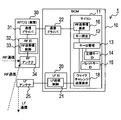
- FIG. 1A is a block diagram illustrating a schematic configuration of a vehicle control system to which the present disclosure is applied
- FIG. 1B is a block diagram showing a schematic configuration of a regular key
- FIG. 1C is a block diagram illustrating a schematic configuration of a bullet key
- FIG. 1D is a block diagram showing a schematic configuration of RFT [1] and BCM
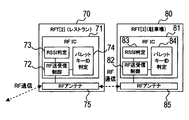
- FIG. 1E is a block diagram showing a schematic configuration of RFT [2] and RFT [3].
- FIG. 2 is a flowchart showing an unlock process executed by the BCM microcomputer.
- FIG. 3 is a flowchart showing unlock processing executed by the microcomputer of the bullet key.
- FIG. 4 is a flowchart showing unlock processing executed by the regular key microcomputer.
- FIG. 5 is a flowchart showing distance setting processing executed by the microcomputer of the bullet key.
- FIG. 6 is a flowchart showing the distance setting process executed by the restaurant RFT [2].
- FIG. 7 is a flowchart showing the distance setting process executed by the RFT [3] of the parking lot.
- FIG. 8 is a ladder chart showing an example of unlock processing and distance setting processing.
- FIG. 9 is a flowchart showing a start process executed by the BCM microcomputer.
- FIG. 10 is a flowchart showing a start process executed by the regular key microcomputer.
- FIG. 11 is a flowchart showing a start process executed by the microcomputer of the bullet key.
- FIG. 12 is a ladder chart showing an example of the start process.
- the regular key 40a which is a portable device possessed by the user
- a BCM (Body Control Module) 10 mounted on the vehicle communicate with each other to perform authentication. It is a system that enables In particular, the vehicle control system 1 of the present embodiment is configured so that authentication can be performed using the regular key 40a and the bullet key 40b that can communicate with the BCM 10.
- the vehicle control system 1 includes a BCM 10, a regular key 40 a, a bullet key 40 b, and a plurality of RFT (Radio Frequency Transceiver) 30, 70, and 80. Yes.
- the BCM 10 is mounted on a vehicle such as a passenger car, and performs authentication with the regular key 40a and the bullet key 40b. If this authentication is successful, for example, a vehicle drive device (engine control device, etc .: not shown), etc. Send an operation permission signal to. That is, the regular key 40a and the bullet key 40b function as wireless keys (portable devices) in the vehicle, and the BCM 10 functions as an authentication device.
- a vehicle drive device engine control device, etc .: not shown
- the RFT [1] 30 among the plurality of RFTs 30, 70, 80 is provided for the BCM 10.
- the RFT [2] 70 is arranged in an arbitrary building such as a restaurant, and the RFT [3] 80 is arranged in a parking lot corresponding to the building.
- the BCM 10 is configured as a computer (microcomputer 11) including a CPU, a memory (not shown), and the like.
- the BCM 10 performs functions as a key collation 12, a key ID management 13, an RF transmission / reception request 16, and a wake challenge transmission request 18. Further, the BCM 10 records a regular key ID 14 and a bullet key ID 15.
- the function as the key collation 12 collates the key ID that it has with the key ID obtained by LF communication or RF communication, and determines whether these IDs match. When these IDs match, unlocking of the door and driving of the vehicle are permitted.
- the regular key ID 14 and the bullet key ID 15 are read according to the processing executed by the function of the key collation 12.
- the function as the RF transmission / reception request 16 manages the operation as an interface for managing the transmission / reception of data to be subjected to RF (radio frequency) communication. Specifically, information transmitted from the regular key 40a and the bullet key 40b is received.
- the BCM 10 includes an LFIC 20 that is a circuit for performing LF communication, and a communication driver 22 that performs communication with the RFT 30.
- the LFIC 20 is disposed between the LF antenna 25 and the microcomputer 11 and transmits data instructed by the microcomputer 11 to be transmitted by LF communication and transmits data received through the LF antenna 25 to the microcomputer 11. (Immobility transmission / reception control 21).
- the RFT 30 includes a communication driver 31, an RFIC 32, and an RF antenna 34.
- the communication driver 31 communicates with a communication driver of another device such as the BCM 10.
- the RFIC 32 has a function as an RF transmission / reception control 33 that transmits and receives data by RF communication via the RF antenna 34.
- the regular key 40a includes an LF antenna 41a, an RF antenna 42a, an RFIC 43a, a microcomputer 50a, and an NFC (Near Field Communication) antenna 57a.
- the RFIC 43 has a function as an RF transmission / reception control 44 and a function as a bullet key ID determination 45.
- bullet key ID determination 45 it is determined whether or not the bullet key ID received via the RF antenna 42a is registered as the bullet key ID 55 described later using the function of the key collation 52 described later. I do.
- the microcomputer 50 a includes a CPU (not shown) and a memory (not shown), and functions as an LF reception control 51, a key verification 52, a key ID management 53, and an NFC transmission / reception control 56. Note that the microcomputer 50a may be configured by hardware such as an IC.
- control is performed to extract data from the LF signal received via the LF antenna 41a.
- NFC transmission / reception control 56 data is transmitted / received by NFC communication via the NFC antenna 57a.
- the functions as the key verification 52 and the key ID management 53 are the same as the functions of the key verification 12 and the key ID management 13 in the BCM 10.
- the microcomputer 50a includes a recording area (regular key ID 54, bullet key ID 55) for recording a regular key ID and a bullet key ID.
- a recording area for recording a regular key ID and a bullet key ID.
- the regular key ID and the bullet key ID are read from and written to the recording areas of the regular key ID 54 and the bullet key ID 55.
- the bullet key 40b includes an LF antenna 41b, an RF antenna 42b, an RFIC 43b, a microcomputer 50b, and an NFC (Near Field Communication) antenna 57b.
- the microcomputer 50b functions as an LF reception control 51, a key ID management 53, and an NFC transmission / reception control 56, and includes a recording area for the bullet key ID (valet key ID 55). These functions and recording areas are the same as the configuration of the regular key 40a in the microcomputer 50a.
- the RFIC 43b has a function as an RF sensitivity setting 46 and an RF output setting 47 in addition to the function as the RF transmission / reception control 44 described above.
- the reception sensitivity and output corresponding to this communication distance are set so that communication can be performed by the communication distance by RF communication set according to the external command.
- the RFT [2] 70 includes an RFIC 71 and an RF antenna 75.
- the RFIC 71 has respective functions as an RF transmission / reception control 72, an RSSI (Received Signal Strength: Received Signal Strength) Indicator 73, and a bullet key ID determination 74.
- the intensity of the signal received via the RF antenna 75 is detected, and the output and sensitivity according to the intensity of the signal are set.
- the bullet key ID determination 74 it is determined whether or not the ID of the bullet key 40b received via the RF antenna 75 matches a preset one.
- the RFT [3] 80 includes an RFIC 81 and an RF antenna 85.
- the RFIC 81 has functions as an RF transmission / reception control 82, an RSSI determination 83, and a bullet key ID determination 84 similar to the RF transmission / reception control 72, RSSI determination 73, and bullet key ID determination 74 of RFT [2] 70.
- the unlocking process is a process for unlocking the vehicle on which the BCM 10 is mounted, and is performed by the BCM 10, the regular key 40a, and the bullet key 40b communicating with each other.
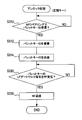
- FIG. 2 shows an unlocking process by the BCM 10, and this process is started when a vehicle door switch (unlock switch) is operated, for example.
- an LF request signal requesting to return an ID is transmitted to the regular key 40a or the bullet key 40b located within the range of LF communication (S110). . Then, it is determined whether or not RF communication data including the ID of the normal key 40a is received from the normal key 40a or the bullet key 40b (S120).
- the unlock process by the bullet key 40b is a process that is started when NFC communication is established with the regular key 40a, for example.
- pairing is performed by NFC, and the ID of the bullet key 40b is transmitted to the regular key 40a (S210). Subsequently, it is determined whether an LF request signal has been received from the BCM 10 (S220).
- the process proceeds to S240 described later. If an LF request signal has been received (S220: YES), the received LF request signal is converted into an RF signal and transmitted as an LF gateway signal (S230). That is, the bullet key 40b functions as a gateway for relaying data.
- the RF reply signal is transmitted as an RF signal (S250). Also in this process, the bullet key 40b functions as a gateway. In the processing of S230 and S250, the ID of the bullet key is added and the data is transferred.
- data to be relayed may be encrypted.
- the data is transmitted by simply adding the ID of the bullet key without performing processing such as decryption on the data.
- the set time indicates the time for which the bullet key 40b is valid with respect to the regular key 40a. That is, after performing NFC communication with the regular key 40a, the bullet key 40b can be used only within the set time range.
- the received ID of the bullet key 40b is recorded in the area of the bullet key ID 55 (S312), and the ID of the bullet key 40b is transmitted to the BCM 10 (S314).
- the BCM 10 records this ID in the area of the bullet key 15 as an accessible key.
- the RF reply signal includes data obtained by encrypting its own ID (ID of the regular key 40a).
- the bullet key 40b of this embodiment has a distance setting function for setting a communicable distance with the regular key 40a.
- the bullet key 40b communicates with the facility-side RFT (RFT [2] 70 at the restaurant and RFT [3] at the parking lot) so that the optimum communicable distance according to the facility can be set. ing.
- This process is a process that is started at an arbitrary timing such as when the NFC communication with the regular key 40a is completed.
- the distance setting process is not an indispensable configuration, and a prescribed value (a preset value) can be used as the communicable distance.
- an area adjustment request is transmitted by RF communication (S410). Then, it is determined whether or not a reception success notification has been received from the RFT [2] 70 of the restaurant (S420).
- reception success notification has not been received (S420: NO)
- the process returns to S410. If a reception success notification has been received (S420: YES), it is determined whether or not various setting values (distance correction value and polling cycle) have been received from the RFT [2] 70 of the restaurant via RF communication (S430). ). If various setting values have not been received (S430: NO), the process of S430 is repeated.
- distance setting processing by the restaurant RFT [2] 70 will be described with reference to FIG. This process is started when, for example, the RFT [2] 70 of the restaurant is turned on, and then repeatedly executed.
- an area adjustment RF signal is transmitted (S520).
- the area adjustment RF signal is a signal for setting an optimum communicable distance according to the distance between the restaurant RFT [2] 70 and the parking lot RFT [3] 80.
- distance correction is performed from the signal strength (RSSI) and distance data (distance conversion value and area adjustment signal) (S550). That is, in order to make the distance range up to RFT [3] 80 of the parking lot a communicable range, this distance is corrected according to the acquired distance data. Then, the distance correction value and the polling cycle are transmitted by RF communication (S560).
- RSSI signal strength
- distance data distance conversion value and area adjustment signal
- a signal including the distance converted value and the area adjustment signal is transmitted by RF communication (S630). Then, it is determined whether a reception success signal has been received from the RFT [2] 70 of the restaurant (S640). If the reception success signal has not been received (S640: NO), the process returns to S610.
- reception success signal has been received (S640: YES)
- the distance setting process by the RFT [3] 80 in the parking lot is terminated.
- the bullet key 40b communicates with the restaurant RFT [2] to set the output and sensitivity according to the size of the area where the bullet key 40b is allowed to be used (see FIG. 8B). .
- the output of the bullet key 40b and the sensitivity setting are also notified to the BCM 10.
- the BCM 10 communicates with the bullet key 40b, but the bullet key 40b also communicates with the regular key 40a and authenticates with the BCM 10 using the ID of the regular key 40a ( (See FIG. 8C).
- start process which is a process when starting a vehicle (engine start or the like) in a vehicle on which the BCM 10 is mounted, will be described.
- the start process is performed in cooperation with the BCM 10, the regular key 40a, and the bullet key 40b.
- FIGS. 9 to 11 an example of starting the engine will be described as an example of starting the vehicle.
- This process is a process that is started when the user operates a start switch for starting the vehicle.
- an LF request signal requesting to return an ID is transmitted to the regular key 40a or the bullet key 40b located within the range of LF communication (S720). Then, it is determined whether or not RF communication data including the ID of the regular key 40a is received from the regular key 40a or the bullet key 40b (S730).
- the process returns to S720. If the RF communication data is received (S730: YES), the ID included in the RF communication data is collated (S740), and whether or not it matches the ID registered as the regular key ID 14 or the bullet key 15 or not. Is determined (S750).
- an LF request signal for requesting to return an ID is transmitted to the regular key 40a or the bullet key 40b located within the range of LF communication (S770). This process is suspended for a specified time (for example, about 1 minute) after the previous transmission of the LF request signal.
- This process is started when the power of the regular key 40a is turned on, for example, and is repeatedly executed thereafter.
- the start process by the bullet key 40b is a process that is started when NFC communication is established with the regular key 40a, for example.
- the process of S210 in FIG. 3 is omitted, but the same process may be performed at the beginning (before the process of S910).
- the RF reply signal is transmitted as an RF signal (S940).
- the start processing by the bullet key 40b is finished.
- a configuration that limits the usage time after NFC communication (the process of S260) may be employed.
- the BCM 10 communicates with the bullet key 40b, but the bullet key 40b also communicates with the regular key 40a and authenticates with the BCM 10 using the ID of the regular key 40a (FIG. 12 (A)).
- an ID request (RF communication continuation request) is periodically issued from the bullet key 40b from the BCM 10 to authenticate the ID (see FIG. 12B). At this time, if the ID authentication fails (including the case where the ID is not returned), the vehicle is stopped.
- the microcomputer 50b performs wireless communication with the regular key 40a when performing authentication with the BCM 10, and the microcomputer 50b performs authentication with the BCM 10 when wireless communication with the regular key 40a is established. carry out.
- the bullet key 40b of the present disclosure can be used as an apparatus for performing authentication with the BCM 10 only within a communicable range with the regular key 40a. Therefore, when this bullet key 40b is owned by a person other than the owner of the vehicle, it is possible to limit the area in which the vehicle can be controlled.
- the microcomputer 50b of the bullet key 40b acquires the authentication information necessary for authentication with the BCM 10 from the normal key 40a by performing wireless communication with the normal key 40a, and acquires the authentication information from the normal key 40a. Authentication with the BCM 10 is performed using the authentication information.
- Such a vehicle control system 1 can function as a relay device (gateway) that relays authentication information from the regular key 40a to the BCM 10. Therefore, it is not necessary for the bullet key 40b to exchange authentication information directly with the BCM 10, so that the process (preparation) when starting communication with the BCM 10 can be simplified. Further, even if the authentication information is encrypted, the encrypted authentication information can be relayed as it is, so there is no need to perform decryption in the bullet key 40b, and the bullet can be maintained while maintaining security.
- the configuration of the key 40b can be simplified.
- the microcomputer 50b of the bullet key 40b provides communication information for communicating with the regular key 40a using NFC communication that enables communication by bringing the bullet key 40b and the regular key 40a close to each other. Exchange.
- the microcomputer 50b of the bullet key 40b uses LF communication to acquire a start signal to start authentication with the BCM 10, and when receiving the start signal, uses RF communication different from LF communication. Wireless communication with the regular key 40a.
- the communication method since the communication method is changed, a communication distance suitable for the communication method can be easily ensured. Moreover, according to the vehicle control system 1, the communication technique currently used in the vehicle can be adopted as it is.
- the microcomputer 50b of the bullet key 40b transmits a start signal to the regular key 40a.
- Such a vehicle control system 1 can function as a relay device that relays the start signal to the regular key 40a. Therefore, information (authentication information) corresponding to the start signal can be acquired from the regular key 40a.
- the microcomputer 11 of the BCM 10 monitors the communication state with the bullet key 40b, and prohibits the continuation of vehicle control when the communication with the bullet key 40b is cut off.
- the present disclosure is applied to the process of unlocking the door and the process of starting the vehicle, but the present disclosure can be applied to any process in vehicle control.
- each process has been described as a process performed by software executed by a microcomputer.
- the process may be realized by hardware such as a circuit capable of performing an equivalent process.
- the BCM 10 in the above embodiment corresponds to a vehicle control device in the present disclosure
- the regular key 40a in the above embodiment corresponds to a portable device in the present disclosure
- the bullet key 40b in the above embodiment corresponds to a communication device in the present disclosure.
- the NFC communication in the above embodiment corresponds to the first communication method referred to in the present disclosure
- the LF communication in the above embodiment corresponds to the second communication method referred to in the present disclosure
- the RF communication corresponds to the third communication method in the present disclosure.
- the processes in S230 and S920 correspond to the portable device communication apparatus in the present disclosure
- the processes in S250 and S940 in the above embodiment correspond to the authentication apparatus in the present disclosure. .
- process of S210 in the above embodiment corresponds to a communication information exchange apparatus in the present disclosure
- process of S220 in the above embodiment corresponds to a start signal acquisition apparatus in the present disclosure
- processes in S770 and S780 in the above embodiment correspond to the communication monitoring device in the present disclosure
- the process in S790 in the above embodiment corresponds to the control prohibition device in the present disclosure.
- each section is expressed as S110, for example.
- each section can be divided into a plurality of subsections, while a plurality of sections can be combined into one section.
- each section configured in this manner can be referred to as a device, module, or means.
Landscapes
- Engineering & Computer Science (AREA)
- Mechanical Engineering (AREA)
- Computer Networks & Wireless Communication (AREA)
- Physics & Mathematics (AREA)
- General Physics & Mathematics (AREA)
- Lock And Its Accessories (AREA)
Priority Applications (1)
| Application Number | Priority Date | Filing Date | Title |
|---|---|---|---|
| US15/116,837 US9855917B2 (en) | 2014-02-10 | 2015-01-29 | Communication apparatus, vehicle control device, and vehicle control system |
Applications Claiming Priority (2)
| Application Number | Priority Date | Filing Date | Title |
|---|---|---|---|
| JP2014-023600 | 2014-02-10 | ||
| JP2014023600A JP6374175B2 (ja) | 2014-02-10 | 2014-02-10 | 通信装置、車両制御装置、および車両制御システム |
Publications (1)
| Publication Number | Publication Date |
|---|---|
| WO2015118840A1 true WO2015118840A1 (ja) | 2015-08-13 |
Family
ID=53777655
Family Applications (1)
| Application Number | Title | Priority Date | Filing Date |
|---|---|---|---|
| PCT/JP2015/000388 Ceased WO2015118840A1 (ja) | 2014-02-10 | 2015-01-29 | 通信装置、車両制御装置、および車両制御システム |
Country Status (3)
| Country | Link |
|---|---|
| US (1) | US9855917B2 (enExample) |
| JP (1) | JP6374175B2 (enExample) |
| WO (1) | WO2015118840A1 (enExample) |
Families Citing this family (12)
| Publication number | Priority date | Publication date | Assignee | Title |
|---|---|---|---|---|
| US10179568B2 (en) * | 2015-10-13 | 2019-01-15 | Faraday & Future Inc. | Seamless vehicle access system |
| WO2017074803A1 (en) * | 2015-10-30 | 2017-05-04 | Faraday & Future Inc. | Authentication control system for a vehicle |
| US9606539B1 (en) | 2015-11-04 | 2017-03-28 | Zoox, Inc. | Autonomous vehicle fleet service and system |
| US11283877B2 (en) | 2015-11-04 | 2022-03-22 | Zoox, Inc. | Software application and logic to modify configuration of an autonomous vehicle |
| US10401852B2 (en) | 2015-11-04 | 2019-09-03 | Zoox, Inc. | Teleoperation system and method for trajectory modification of autonomous vehicles |
| US12265386B2 (en) | 2015-11-04 | 2025-04-01 | Zoox, Inc. | Autonomous vehicle fleet service and system |
| WO2017079341A2 (en) | 2015-11-04 | 2017-05-11 | Zoox, Inc. | Automated extraction of semantic information to enhance incremental mapping modifications for robotic vehicles |
| JP6569862B2 (ja) * | 2016-01-21 | 2019-09-04 | 株式会社デンソー | アンテナ出力調整装置 |
| US10717413B2 (en) * | 2018-12-05 | 2020-07-21 | Valeo Comfort And Driving Assistance | Actuation of vehicle systems using device-as-key and computer vision techniques |
| JP7284701B2 (ja) * | 2019-12-26 | 2023-05-31 | 株式会社東海理化電機製作所 | 通信装置及びシステム |
| JP7287303B2 (ja) * | 2020-02-07 | 2023-06-06 | トヨタ自動車株式会社 | 車両 |
| JP7450291B2 (ja) * | 2021-09-29 | 2024-03-15 | 株式会社ユピテル | 中継システム |
Citations (6)
| Publication number | Priority date | Publication date | Assignee | Title |
|---|---|---|---|---|
| JPH11208419A (ja) * | 1998-01-30 | 1999-08-03 | Toyota Motor Corp | 車両制御システム |
| JP2003041825A (ja) * | 2001-07-30 | 2003-02-13 | Mazda Motor Corp | 遠隔解錠方法、情報処理装置及び情報処理プログラム、並びにユーザー端末及び該ユーザー端末を制御するための制御プログラム |
| JP2012028854A (ja) * | 2010-07-20 | 2012-02-09 | Tokai Rika Co Ltd | 携帯機 |
| JP2013159980A (ja) * | 2012-02-06 | 2013-08-19 | Denso Corp | 車両用電子キーシステム |
| JP2013185376A (ja) * | 2012-03-08 | 2013-09-19 | Omron Automotive Electronics Co Ltd | 通信システム、通信方法、および携帯機 |
| JP2013245468A (ja) * | 2012-05-25 | 2013-12-09 | Nippon Soken Inc | スマートシステム |
Family Cites Families (5)
| Publication number | Priority date | Publication date | Assignee | Title |
|---|---|---|---|---|
| KR20060111570A (ko) * | 2003-12-10 | 2006-10-27 | 마츠시타 덴끼 산교 가부시키가이샤 | 도난방지시스템 |
| JP4433304B2 (ja) | 2005-02-17 | 2010-03-17 | マツダ株式会社 | スマートキーレスシステム |
| US20090231094A1 (en) * | 2008-03-14 | 2009-09-17 | Delphi Technologies, Inc. | Multiple vehicle remote keyless entry apparatus |
| DE102009040420A1 (de) * | 2009-09-07 | 2011-03-10 | Li-Tec Battery Gmbh | Prozessorgesteuertes Zugangsberechtigungs- und Batteriemanagement für Elektrofahrzeuge |
| JP2014205978A (ja) * | 2013-04-11 | 2014-10-30 | トヨタ自動車株式会社 | スマートエントリー用携帯機 |
-
2014
- 2014-02-10 JP JP2014023600A patent/JP6374175B2/ja not_active Expired - Fee Related
-
2015
- 2015-01-29 WO PCT/JP2015/000388 patent/WO2015118840A1/ja not_active Ceased
- 2015-01-29 US US15/116,837 patent/US9855917B2/en active Active
Patent Citations (6)
| Publication number | Priority date | Publication date | Assignee | Title |
|---|---|---|---|---|
| JPH11208419A (ja) * | 1998-01-30 | 1999-08-03 | Toyota Motor Corp | 車両制御システム |
| JP2003041825A (ja) * | 2001-07-30 | 2003-02-13 | Mazda Motor Corp | 遠隔解錠方法、情報処理装置及び情報処理プログラム、並びにユーザー端末及び該ユーザー端末を制御するための制御プログラム |
| JP2012028854A (ja) * | 2010-07-20 | 2012-02-09 | Tokai Rika Co Ltd | 携帯機 |
| JP2013159980A (ja) * | 2012-02-06 | 2013-08-19 | Denso Corp | 車両用電子キーシステム |
| JP2013185376A (ja) * | 2012-03-08 | 2013-09-19 | Omron Automotive Electronics Co Ltd | 通信システム、通信方法、および携帯機 |
| JP2013245468A (ja) * | 2012-05-25 | 2013-12-09 | Nippon Soken Inc | スマートシステム |
Also Published As
| Publication number | Publication date |
|---|---|
| US9855917B2 (en) | 2018-01-02 |
| US20170144630A1 (en) | 2017-05-25 |
| JP2015151681A (ja) | 2015-08-24 |
| JP6374175B2 (ja) | 2018-08-15 |
Similar Documents
| Publication | Publication Date | Title |
|---|---|---|
| JP6374175B2 (ja) | 通信装置、車両制御装置、および車両制御システム | |
| US20240404336A1 (en) | System and method for communicating with a vehicle | |
| US10196039B2 (en) | System and method for keyless entry and remote starting vehicle with an OEM remote embedded in vehicle | |
| JP6626565B2 (ja) | 車両の起動方法 | |
| JP6505711B2 (ja) | 制御装置と識別要素との間のデータ交換により自動車内でコマンドをトリガするための方法 | |
| JP6594880B2 (ja) | 自動車との自動ペアリングが可能な携帯電話、及び自動ペアリング方法 | |
| US9786108B2 (en) | NFC based secure car key | |
| JP6292719B2 (ja) | 車両無線通信システム、車両制御装置、携帯機 | |
| JP6695774B2 (ja) | 生体認証併用電子キーシステム | |
| KR20190029920A (ko) | 자동차의 제어 시스템 및 제어 방법 | |
| US20190110199A1 (en) | Car sharing system | |
| CN109658547B (zh) | 车辆共享系统 | |
| JP2014150425A (ja) | 制御システム | |
| CN110001576A (zh) | 用于控制对车辆访问的方法和用于控制对车辆访问的系统 | |
| WO2016092766A1 (ja) | 通信システム | |
| JP2019055656A (ja) | カーシェアリングシステム | |
| JP2017203314A (ja) | 無線通信システム | |
| KR101406192B1 (ko) | 스마트단말을 이용한 차량액세스 제어 시스템 및 방법 | |
| JP2020113065A (ja) | 情報管理システム | |
| KR101334461B1 (ko) | 패시브 키리스 엔트리 스마트 키를 위한 보안 시스템 및 그 방법 | |
| EP3640880B1 (en) | Vehicular control system | |
| JP2018053489A (ja) | スマートキーシステム | |
| JP6964976B2 (ja) | 車両用通信装置 | |
| JP2022109041A (ja) | ロック制御システム及びロック制御方法 | |
| JP2022119385A (ja) | 認証システム、機器制御方法、及び検出ユニット |
Legal Events
| Date | Code | Title | Description |
|---|---|---|---|
| 121 | Ep: the epo has been informed by wipo that ep was designated in this application |
Ref document number: 15746780 Country of ref document: EP Kind code of ref document: A1 |
|
| WWE | Wipo information: entry into national phase |
Ref document number: 15116837 Country of ref document: US |
|
| NENP | Non-entry into the national phase |
Ref country code: DE |
|
| 122 | Ep: pct application non-entry in european phase |
Ref document number: 15746780 Country of ref document: EP Kind code of ref document: A1 |