WO2010100838A1 - 無線基地局装置、無線端末装置、および基地局認証方法 - Google Patents
無線基地局装置、無線端末装置、および基地局認証方法 Download PDFInfo
- Publication number
- WO2010100838A1 WO2010100838A1 PCT/JP2010/000951 JP2010000951W WO2010100838A1 WO 2010100838 A1 WO2010100838 A1 WO 2010100838A1 JP 2010000951 W JP2010000951 W JP 2010000951W WO 2010100838 A1 WO2010100838 A1 WO 2010100838A1
- Authority
- WO
- WIPO (PCT)
- Prior art keywords
- base station
- time slot
- authentication
- data
- station authentication
- Prior art date
- Legal status (The legal status is an assumption and is not a legal conclusion. Google has not performed a legal analysis and makes no representation as to the accuracy of the status listed.)
- Ceased
Links
Images
Classifications
-
- H—ELECTRICITY
- H04—ELECTRIC COMMUNICATION TECHNIQUE
- H04W—WIRELESS COMMUNICATION NETWORKS
- H04W12/00—Security arrangements; Authentication; Protecting privacy or anonymity
- H04W12/06—Authentication
-
- H—ELECTRICITY
- H04—ELECTRIC COMMUNICATION TECHNIQUE
- H04W—WIRELESS COMMUNICATION NETWORKS
- H04W72/00—Local resource management
- H04W72/02—Selection of wireless resources by user or terminal
-
- H—ELECTRICITY
- H04—ELECTRIC COMMUNICATION TECHNIQUE
- H04W—WIRELESS COMMUNICATION NETWORKS
- H04W88/00—Devices specially adapted for wireless communication networks, e.g. terminals, base stations or access point devices
- H04W88/08—Access point devices
Definitions
- the present invention relates to a radio base station apparatus, a radio terminal apparatus, and a base station authentication method that perform radio communication by time division multiple access, and in particular, a radio communication in which a plurality of radio terminal apparatuses authenticate to a radio base station apparatus.
- the present invention relates to a radio base station apparatus, a radio terminal apparatus, and a base station authentication method in the system.
- the authentication communication is communication for transmitting / receiving authentication information including identification information such as a device ID (identifier) of a wireless communication device and a password in order to authenticate a communication partner.
- the authentication process is a process of confirming the authenticity of the partner (whether or not it is a genuine partner) by verifying the authentication information received from the partner by the authentication communication.
- the wireless communication device starts data communication with the other party only when it is confirmed that the other party is authentic. As a result, data communication with a non-authentic partner can be prevented, and information leakage to a third party can be prevented.
- the first is whether or not the content of the received authentication information is created by a genuine wireless communication device.
- digital signature and electronic authentication techniques are widely used to confirm this matter.
- the second is whether or not the received authentication information is created by the other party who is currently performing authentication communication. That is, it is whether or not the received authentication information is a result of “unauthorized interception of the authentication information transmitted by the authentic wireless communication device and retransmission of the authentication information by a third party”. Such an impersonation act by retransmitting authentication information that has been illegally intercepted is generally called “replay attack”.
- challenge / response authentication is widely used to confirm the second item.
- Challenge / response authentication is a technique that eliminates information sent by a replay attack by using random values that differ from time to time.
- one of the wireless communication devices selects a value, for example, at random, and transmits the selected value to the wireless communication device that is a genuine counterpart.
- the wireless communication apparatus that has received the random value adds a signature to the received random value by using the secret information shared in advance, and returns it by including it in the authentication information.
- the wireless communication device that has received the authentication information confirms the validity of the signature and confirms whether or not the random value included in the authentication information matches the transmitted random value. Then, the wireless communication apparatus determines that the transmission source of the received authentication information is an authentic partner only when these values match. Thereby, the wireless communication apparatus can eliminate the replay attack.
- Challenge / response authentication requires transmission time for transmitting random values.
- individual authentication processing is performed in as short a time as possible. It is desirable that
- Patent Document 1 discloses a technique for shortening individual authentication processing in a wireless communication system of a time division multiple access system (time division multiple access system, hereinafter referred to as “TDMA system”).
- TDMA system time division multiple access system
- the wireless communication device that performs authentication is referred to as a “wireless terminal device”
- the wireless communication device that is authenticated is referred to as a “wireless base station device”.
- authentication for the wireless terminal device to confirm that the communication partner is a genuine wireless base station device is referred to as “base station authentication”.
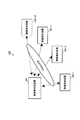
- FIG. 1 is a schematic diagram for explaining the TDMA system.
- a plurality of wireless terminal devices 30-1 to 30-3 are randomly assigned time slots each time authentication communication is started.
- Each wireless terminal device 30 communicates with the wireless base station device 20 using the assigned time slot.
- the TDMA scheme prevents radio wave interference in communication between the plurality of radio terminal apparatuses 30-1 to 30-3 and enables one-to-many individual communication.
- Each frame and each time slot is identified by a number assigned to each frame.
- the frame number and the time slot number change with time.
- the value obtained by combining the frame number and the time slot number is a value that varies from time to time.
- the time slot number is selected at random. Therefore, a value obtained by combining the frame number and the time slot number has randomness.
- Patent Document 1 uses this combination value as a random value in challenge / response authentication.
- FIG. 2 is a sequence diagram showing the overall operation of the wireless communication system using time slot numbers as random values.
- the first radio terminal apparatus 30-1 makes an authentication request to the radio base station apparatus 20 using the time slot of the time slot number N of the frame of the frame number M. Transmit (S41). Then, the radio base station apparatus 20 generates authentication data from the values M and N using a shared function shared in advance with the first radio terminal apparatus 30-1 (S42), and the generated authentication Data is transmitted to the first wireless terminal device 30-1 (S43). Similarly, first radio terminal apparatus 30-1 generates authentication data from values M and N using a shared function, and whether the generated authentication data matches the authentication data received from the radio base station apparatus or not. (S44). If the two data match, the first radio terminal apparatus 30-1 starts data communication with the radio base station apparatus 20 (S45). Subsequently, for example, in the time slot of the next time slot number N + 1, for example, the second wireless terminal device 30-2 similarly transmits an authentication request.
- Patent Document 1 does not need to transmit a random value separately, and can perform base station authentication in a shorter time.
- time slot length the time length of the time slot.
- the technique described in Patent Document 1 cannot effectively reduce the time slot length, and there is a problem that the number of wireless terminal devices that can perform base station authentication within a certain time is limited. is there. The reason is as follows.
- An object of the present invention is to provide a radio base station apparatus, a radio terminal apparatus, and a base station authentication method in which more radio terminal apparatuses can perform base station authentication within a predetermined time.
- a radio base station apparatus of the present invention is a radio base station apparatus that performs radio communication with a plurality of radio terminal apparatuses by time division multiple access, and receives response information indicating that base station authentication is started from the radio terminal apparatus.
- a response information receiving unit for receiving, a base station authentication data generating unit for generating base station authentication data in which information indicating presence / absence of reception of the response information for each time slot is aggregated, and the generated base station authentication data, And a base station authentication data transmitter for transmitting to the wireless terminal device.
- a radio terminal apparatus is one of a plurality of radio terminal apparatuses that perform radio communication with a radio base station apparatus by time division multiple access, and a time slot selection unit that selects a time slot is selected.
- Response information indicating that base station authentication is started using the time slot is transmitted to the radio base station apparatus, and base station authentication data is transmitted corresponding to the transmitted response information.
- base station authentication data receiving unit and the received base station authentication data indicate that the response information has been received in the selected time slot.
- a base station authenticating unit that performs base station authentication with respect to the transmission source.
- the base station authentication method of the present invention is a base station authentication method performed between a radio base station apparatus and a plurality of radio terminal apparatuses that perform radio communication with the radio base station by time-division multiple access.
- a terminal device selecting a time slot, and using the selected time slot, transmitting response information indicating that base station authentication is started to the radio base station device; and the radio base station device Generating base station authentication data in which information indicating presence / absence of reception of the response information for each time slot is aggregated, and transmitting the generated base station authentication data to the wireless terminal device; and the wireless terminal device However, based on whether the received base station authentication data indicates that the response information has been received in the selected time slot, the base station And performing a base station authentication for the sender proof data.
- more wireless terminal devices can perform base station authentication within a certain period of time.
- Schematic diagram for explaining the TDMA system Sequence diagram showing the overall operation of a wireless communication system employing conventional technology 1 is a system configuration diagram showing an example of a configuration of a radio communication system according to Embodiment 1 of the present invention. Schematic diagram showing an example of an environment to which the wireless communication system according to the first embodiment is applied.
- FIG. 3 is a sequence diagram illustrating an example of the overall operation of the wireless communication system according to the first embodiment.
- FIG. 2 is a block diagram showing an example of a configuration of a radio base station apparatus according to Embodiment 1 FIG.
- FIG. 3 is a block diagram illustrating an example of a configuration of a wireless terminal device according to the first embodiment.
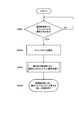
- the flowchart which shows an example of operation
- the flowchart which shows an example of operation
- FIG. Flowchart showing an example of operation of the time slot management unit of the radio base station apparatus according to Embodiment 1
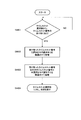
- FIG. 6 is a flowchart showing an example of the operation of the communication control unit of the wireless terminal device according to the first embodiment.
- Flowchart showing an example of operation of the receiving unit of the wireless terminal device according to Embodiment 1 6 is a flowchart showing an example of the operation of the time slot selection unit of the wireless terminal device according to Embodiment 1.
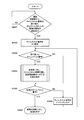
- 6 is a flowchart illustrating an example of an operation of a selection status management unit of the wireless terminal device according to the first embodiment.
- FIG. 8 is a flowchart showing an example of the operation of the time slot management unit of the wireless terminal device according to the first embodiment.
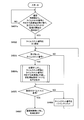
- 6 is a flowchart illustrating an example of operation of a transmission unit of the wireless terminal device according to the first embodiment.
- 8 is a flowchart showing an example of the operation of the comparison data generation unit of the wireless terminal device according to the first embodiment.
- 6 is a flowchart illustrating an example of operation of a base station authentication unit of the wireless terminal device according to the first embodiment.
- the block diagram which shows an example of a structure of the radio base station apparatus which concerns on Embodiment 2 of this invention.
- the figure which shows an example of the data structure of the response in which the random number value in Embodiment 2 was embedded FIG.
- FIG. 9 is a block diagram showing an example of a configuration of a radio base station apparatus according to Embodiment 2
- FIG. 9 is a sequence diagram illustrating an example of the overall operation of the wireless communication system according to the second embodiment.
- 8 is a flowchart showing an example of the operation of the time slot selection unit of the wireless terminal device according to the second embodiment.
- 8 is a flowchart showing an example of the operation of the selection status management unit of the wireless terminal device according to the second embodiment. 8 is a flowchart showing an example of the operation of the time slot management unit of the wireless terminal device according to the second embodiment. 8 is a flowchart illustrating an example of operation of a transmission unit of a wireless terminal device according to Embodiment 2.
- FIG. 3 is a system configuration diagram showing an example of a configuration of the radio communication system according to Embodiment 1 of the present invention.
- radio communication system 100 includes radio base station apparatus 200 and first to third radio terminal apparatuses 300-1 to 300-3 located in the communication area of radio base station apparatus 200. And have.
- the first to third wireless terminal apparatuses 300-1 to 300-3 have the same configuration.
- the first to third radio terminal apparatuses 300-1 to 300-3 will be collectively referred to as the radio terminal apparatus 300 as appropriate.
- the radio base station apparatus 200 performs radio communication using the TDMA scheme with the first to third radio terminal apparatuses 300-1 to 300-3.
- FIG. 4 is a schematic diagram illustrating an example of an environment to which the wireless communication system 100 is applied.
- an unspecified number of pedestrians 410 that pass through the communication area 400 of the radio base station apparatus 200 each carry a radio terminal apparatus 300.
- the wireless terminal device 300 is, for example, an active tag that is a kind of RFID (radio frequency identification).
- the radio base station apparatus 200 is, for example, an active tag reader / writer.
- the number of wireless terminal devices 300 that are simultaneously located in the communication area 400 varies. For example, as shown in FIG. 3, when the fourth radio terminal apparatus 300-4 moves to the communication area, the radio base station apparatus 200 performs radio communication using the TDMA scheme with the fourth radio terminal apparatus 300-4. Do.
- the wireless communication system 100 is applied to, for example, a child watching service.
- a child watching service is a service that detects when a child passes or goes to school and detects whether or not the child is going to and from school, and if there is an abnormality, notifies the teacher or guardian to that effect.
- the radio base station apparatus 200 is installed at a school gate, and the radio terminal apparatus 300 is carried by a child. When going to and from school, many children are expected to pass within a short time.
- the wireless communication system 100 is applied to, for example, a vehicle approach notification service.
- vehicle approach notification service is a service that detects that when a pedestrian is passing near a corner that is likely to be a blind spot for the vehicle, and notifies surrounding vehicles.
- the radio base station apparatus 200 is installed at a corner, and the radio terminal apparatus 300 is carried by a pedestrian.
- the wireless terminal device 300 performs individual data communication with the wireless base station device 200 using the time slot assigned to the wireless terminal device 300.
- a user carrying the wireless terminal device receives services such as passage recording and information provision through the individual data communication.
- radio terminal apparatus 300 randomly selects a time slot to be used for communication and uses radio access station apparatus 200 to determine which time slot has been selected using the selected time slot. To notify.
- the time slot is identified using the time slot number.
- the time slot synchronization is performed, for example, when the radio base station apparatus 200 notifies each radio terminal apparatus 300 of the frame start position by transmitting an authentication start request described later.
- each wireless terminal device 300 determines the legitimacy (in this case, whether it is the wireless base station device 200) of the other party to start data communication, prior to data communication, Base station authentication.
- each wireless terminal device 300 confirms in this authentication that the received authentication information is not due to a replay attack. This is because a third party may impersonate the wireless base station device 200 and attempt to start data communication with the wireless terminal device 300 for an unauthorized purpose.
- radio communication system 100 performs base station authentication with contents different from the conventional one, thereby enabling more radio terminal apparatuses 300 to perform base station authentication within a certain period of time.
- the description will be given focusing on the part related to base station authentication in the configuration and operation of the wireless communication system 100.
- shared information information that is shared and used between the radio base station apparatus 200 and the radio terminal apparatus 300 in base station authentication (hereinafter referred to as “shared information”) is set in each apparatus in advance at the time of shipment of each apparatus. It is assumed that The shared information includes a wireless data format and command code, a data generation rule for generating base station authentication data, a data generation rule for generating comparison data described later, the number of slots, a slot interval, and the like. Including.
- the shared information may be transmitted from the radio base station apparatus 200 to the radio terminal apparatus 300 every time base station authentication is performed. For example, the radio base station apparatus 200 adds the shared information to the authentication start request or the base station authentication data. Then, the wireless terminal device 300 acquires the shared information from the transmitted authentication start request or base station authentication data.
- FIG. 5 is a sequence diagram illustrating an example of the overall operation of the wireless communication system 100.
- the radio base station apparatus 200 periodically broadcasts an authentication start request, which is an instruction to start authentication communication, to the radio terminal apparatus 300 located in the communication area 400 (S2100).
- an authentication start request which is an instruction to start authentication communication
- the base station authentication described later is executed every time the wireless terminal device 300 receives an authentication start request.
- the above-mentioned predetermined interval is desirably a length that fits within the communication area passing time of the wireless terminal device 300.
- This communication area passage time can be calculated from the size of the communication area 400 and the average moving speed of the user carrying the wireless terminal device 300. Further, it is desirable that the above-mentioned predetermined interval has a length including a time slot for base station authentication and a time slot for data communication.
- Broadcast transmission to the wireless terminal device 300 located in the communication area 400 is hereinafter simply referred to as “broadcast transmission”.
- broadcast transmission it is assumed that first to third wireless terminal apparatuses 300-1 to 300-3 are present in communication area 400 as shown in FIG.
- Each of the first to third wireless terminal apparatuses 300-1 to 300-3 that has received the authentication start request selects at least one time slot, for example, at random in response to the received authentication start request ( S2200).
- first to third radio terminal apparatuses 300-1 to 300-3 each transmit a response indicating the start of base station authentication to radio base station apparatus 200 using the selected time slot (S2300). ).
- FIG. 6 is a diagram showing an example of the data configuration of the authentication start request and response.
- the wireless data 510 includes a synchronization code 511, a length 512, a command code 513, and a checksum 514 arranged in this order.
- the synchronization code 511 describes a predetermined code indicating the start of wireless data.
- the length 512 describes the length of the subsequent data (here, the total length of the command code 513 and the checksum 514), for example, in byte length.
- the command code 513 describes a command code indicating the type of the wireless data.
- the checksum 514 describes an error detection code of the wireless data.
- the radio base station apparatus 200 describes a predetermined command code indicating that the radio data 510 is an authentication start request in the command code 513, and generates radio data for the authentication start request.
- the wireless terminal device 300 detects the start of wireless data based on the synchronization code 511, and extracts the command code 513 and the checksum 514 based on the length 512. Then, when the above-described predetermined command code is described in the command code 513, the wireless terminal device 300 determines that the wireless data 510 is an authentication start request. Further, the wireless terminal device 300 determines whether there is an error in the wireless data 510 based on the checksum 514.
- the wireless terminal device 300 describes a predetermined command code (ACKnowledgement: ACK) in the command code 513, and generates response wireless data.
- the predetermined command code is information indicating that the wireless data 510 is a response to the authentication start request.
- Radio base station apparatus 200 detects the start of radio data based on synchronization code 511 and extracts command code 513 and checksum 514 based on Length 512.
- Radio base station apparatus 200 determines that radio data 510 is a response when the above-mentioned predetermined command code is described in command code 513. Furthermore, the radio base station apparatus 200 determines whether or not there is an error in the radio data 510 based on the checksum 514.
- the radio base station apparatus 200 receives responses from the first to third radio terminal apparatuses 300-1 to 300-3. Then, the radio base station apparatus 200 generates base station authentication data based on the reception status indicating the presence / absence of reception for each time slot (S2400 in FIG. 5).
- the base station authentication data is data in which the presence or absence of a response to the authentication start request for each time slot is aggregated for a plurality of time slots. Details of the base station authentication data will be described later.
- the radio base station apparatus 200 broadcasts the authentication information to the first to third radio terminal apparatuses 300-1 to 300-3 (S2500).
- the authentication information includes base station authentication data generated by the radio base station device 200 and identification information such as a device ID and a password.
- the authentication information is stored in wireless data in the same format as the authentication start request and response, and is transmitted and received.
- FIG. 7 is a diagram showing an example of the data configuration of authentication information including base station authentication data, and corresponds to FIG. The same parts as those in FIG.
- the authentication information wireless data 520 includes a synchronization code 511, a length 512, a command code 513, base station authentication data 521, identification information 522, and a checksum 514 arranged in this order.
- Length 512 describes the total length of command code 513, base station authentication data 521, identification information 522, and checksum 514.
- the radio base station apparatus 200 describes a predetermined command code indicating that the radio data 520 is authentication information in the command code 513, and generates the radio data 520 of authentication information.
- the wireless terminal device 300 extracts the base station authentication data 521 and the identification information 522.
- the checksum 514 may be an electronic signature.
- the radio base station apparatus 200 transmits authentication information including base station authentication data by generating and transmitting such radio data 520.
- the first to third radio terminal apparatuses 300-1 to 300-3 generate comparison data based on which time slot is selected (S2600 in FIG. 5).
- the comparison data is data in which an identifier indicating the presence / absence of selection is associated with each time slot. Details of the comparison data will be described later.
- the first to third radio terminal apparatuses 300-1 to 300-3 are based on the base station authentication data included in the authentication information received from the radio base station apparatus 200 and the generated comparison data. Authentication is performed (S2700). Specifically, the first to third wireless terminal apparatuses 300-1 to 300-3 compare the base station authentication data with the comparison data, and determine whether or not these data are consistent.
- the state in which the base station authentication data and the comparison data are consistent includes that all of the selected time slots indicated by the comparison data are included in the time slots indicated by the base station authentication data. It is a state that has been. Details of determination of matching between the base station authentication data and the comparison data will be described later.
- the first to third wireless terminal apparatuses 300-1 to 300-3 have the authentication information transmission source as the authentic partner (here, the wireless base station apparatus 200). ), The communication is continued, and the data communication is performed. Specifically, the wireless terminal device 300 transmits a notification that the base station authentication has been successful to the wireless base station device 200. Further, the radio terminal apparatus 300 performs data communication with the radio base station apparatus 200 using a data communication time slot arranged after the base station authentication time slot.
- the first to third wireless terminal apparatuses 300-1 to 300-3 do not authenticate the transmission source of the authentication information (for example, perform a replay attack). And the data communication is not performed.
- the radio base station apparatus 200 desirably gives a signature to the authentication information for the purpose of preventing falsification of the transmitted authentication information.
- the wireless terminal device 300 verifies whether or not a genuine signature is given to the authentication information in the base station authentication.
- FIG. 8 is a schematic diagram illustrating an example of a data generation rule for generating base station authentication data by the radio base station apparatus 200.
- the number of the last time slot of the frame used for base station authentication (hereinafter referred to as “default time slot number”) is assumed to be “n”. Further, it is assumed that first to third radio terminal apparatuses 300-1 to 300-3 select time slots with time slot numbers “0”, “2”, and “n”, respectively.
- the radio base station apparatus 200 sets “1” as an identifier indicating that the time slot is a response from the radio terminal apparatus 300, and “0” indicates that the time slot is a response without a response.
- the radio base station apparatus 200 sets the value of the identifier corresponding to the received time slot numbers “0”, “2”, “n” to “1”, and identifiers corresponding to all other time slot numbers.
- Information having the value of “0” as “0” is held as a reception status. That is, the reception status is information indicating the presence / absence of a response for each time slot.
- the data generation rule for the base station authentication data is such that the identifiers indicating the presence or absence of a response are arranged in ascending order of time slot numbers.
- the base station authentication data generated by the radio base station apparatus 200 is “1, 0, 1, 0,.
- the first to third wireless terminal apparatuses 300-1 to 300-3 each generate comparison data based on the selection situation indicating the presence / absence of selection for each time slot (S2400).
- FIG. 9 is a schematic diagram illustrating an example of a data generation rule for generating comparison data by the wireless terminal device 300. Here, an outline of generation of comparison data by the first wireless terminal device 300-1 is illustrated.
- the first wireless terminal device 300-1 has selected the time slot number “0”.
- first wireless terminal apparatus 300-1 sets “1” as an identifier indicating that it is a selected (response was made) time slot, and was not selected (response was not made).
- An identifier indicating the presence is “0”.
- the time slot selection status in first radio terminal apparatus 300-1 is that the value of the identifier corresponding to time slot number “0” is “1”, and the other time slots The identifier value corresponding to the number is “0”.
- the data generation rule for comparison data is the content in which the identifiers indicating the presence or absence of selection are arranged in ascending order of time slot numbers, and is the same as the data generation rule for base station authentication data.
- the comparison data generated by the radio base station apparatus 200 is “1, 0, 0, 0,..., 0”.
- FIG. 10 is a schematic diagram showing a relationship between base station authentication data and comparison data in each wireless terminal device 300 in the examples shown in FIGS. 8 and 9.
- the base station authentication data generated by the wireless terminal device 300 is “1, 0, 1, 0,..., 1”.
- the comparison data generated by the first to third wireless terminal apparatuses 300-1 to 300-3 are “1, 0, 0, 0,..., 0”, “0, 0” in order. , 1, 0, ..., 0 ",” 0, 0, 0, 0, ..., 1 ".
- the bit position where the value “1” of each comparison data is the value “1”. This is because the presence / absence of response transmission / reception and the time slot in which the response transmission / reception is performed match between the radio base station apparatus 200 and each radio terminal apparatus 300. This is also because the data generation rule for base station authentication data and the data generation rule for comparison data have the same content in which identifiers are arranged in ascending order of time slot numbers.
- bit position where the value “1” of each comparison data is the value “1” means that one wireless terminal device 300 uses a plurality of time slot numbers. The same applies to cases. That is, the same applies when the wireless terminal device 300 selects a plurality of time slots and transmits a response.
- the bit position where the value of the comparison data is “1” is the value “1”, which indicates that the base station authentication data and the comparison data match.
- Such consistency between the base station authentication data and the comparison data can be performed, for example, by determining whether or not the logical product of the base station authentication data and the comparison data matches the comparison data.
- the time slot number to be used for the response is randomly selected as described above. Thereby, the base station authentication data and the comparison data have high randomness.
- FIG. 11 is a schematic diagram illustrating an example of how a plurality of wireless terminal devices 300 select the same time slot number.
- Each wireless terminal device 300 performs carrier sense in the selected time slot before transmitting a response.
- each wireless terminal device 300 detects that another wireless terminal device 300 has responded first in the selected time slot, it is assumed that the wireless terminal device 300 has transmitted a response without actually transmitting a response. It is desirable to perform processing.
- it is possible to perform base station authentication in the same manner as in the case where the time slot number is selected independently while preventing collision. Note that when actual data communication is performed after the base station authentication, the use time slot is adjusted again so that there is no overlap.
- the reliability of the base station authentication may be reduced. For example, when base station authentication data in which all bits have the value “1” is generated, if a replay attack is performed using this base station authentication data, base station authentication is performed in all wireless terminal devices 300. Will be successful.
- the radio base station apparatus 200 desirably monitors the total number of bits having the value “1” when generating the base station authentication data. In this case, the radio base station apparatus 200 performs processing without transmitting base station authentication data when the total number of bits having the value “1”, that is, the number of timeslots having received a response exceeds a predetermined threshold.
- the authentication start request is transmitted again after a predetermined interval. At this time, the radio base station apparatus 200 may update the number of slots and transmit an authentication start request.
- the sequence diagram of the present embodiment shown in FIG. 5 is compared with the sequence diagram of the conventional radio communication system shown in FIG. .
- generation and transmission of base station authentication data must be completed for each time slot. For example, when three wireless terminal devices are located in the communication area of the wireless base station device, generation and transmission of base station authentication data are performed at least three times.
- three wireless terminal apparatuses 300-1 to 300-3 are located in communication area 400 shown in FIG. 4, but generation and transmission of base station authentication data is performed at least once. It only takes one by one.
- radio communication system 100 can reduce the length of each time slot by the time required for generating and transmitting base station authentication data.
- radio communication system 100 according to the present embodiment transmits authentication start request, generates base station authentication data, and transmits base station authentication data separately from the time slot used for a response to the authentication start request. It takes time to complete. However, since both are performed once, the increased time can be suppressed to be less than the total time to be reduced. Further, when a signature is added to the base station authentication data, only one signature is required.
- radio communication system 100 can increase the number of time slots that can be arranged for a certain period of time, and more radio terminal apparatuses 300 can perform base station authentication within a certain period of time. It can be performed.
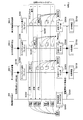
- FIG. 12 is a block diagram showing an example of the configuration of the radio base station apparatus 200. As shown in FIG.
- the radio base station apparatus 200 includes a communication control unit 210, a transmission unit 220, a time slot management unit 230, a reception unit 240, a reception status management unit 250, and a base station authentication data generation unit 260.
- the communication control unit 210 controls the overall operation of the radio base station apparatus 200.
- the communication control unit 210 is connected to a transmission unit 220, a time slot management unit 230, a reception unit 240, and a base station authentication data generation unit 260.
- the transmission unit 220 generates an authentication start request and broadcasts the generated authentication start request. In addition, the transmission unit 220 performs broadcast transmission of authentication information including the base station authentication data generated by the base station authentication data generation unit 260.
- the time slot management unit 230 holds a predetermined slot number and a predetermined time slot interval (time slot length) in advance.
- the time slot management unit 230 is connected to the transmission unit 220 and the reception unit 240.
- the time slot management unit 230 manages a time slot shared with the wireless terminal device 300 located in the communication area 400 after at least the transmission unit 220 broadcasts the authentication start request.
- the receiving unit 240 receives a response to the authentication start request transmitted from the wireless terminal device 300 for each time slot, and notifies the reception status management unit 250 of the presence / absence of the received response for each time slot. Note that the transmission of this response in each wireless terminal device 300 is performed using the time slot selected by the wireless terminal device 300.
- the reception status management unit 250 is connected to the reception unit 240. Then, the reception status management unit 250 manages the reception status indicating whether or not there is a response for each time slot in the reception unit 240.
- the base station authentication data generation unit 260 holds data generation rules for base station authentication data in advance.
- the base station authentication data generation unit 260 is connected to the reception status management unit 250. Then, the base station authentication data generation unit 260 generates base station authentication data based on the data generation rules held based on the reception status managed by the reception status management unit 250.
- the radio base station apparatus 200 includes, for example, a CPU (central processing unit), a storage medium such as a ROM (read only memory) storing a control program, and a working memory such as a RAM (random access memory).
- a CPU central processing unit
- ROM read only memory
- working memory such as a RAM (random access memory).
- the function of each unit is realized by the CPU executing the control program.
- FIG. 13 is a block diagram illustrating an example of the configuration of the wireless terminal device 300.
- a radio terminal apparatus 300 includes a communication control unit 310, a reception unit 320, a time slot selection unit 330, a selection status management unit 340, a time slot management unit 350, a transmission unit 360, a comparison data generation unit 370, and a base station.
- An authentication unit 380 is included.
- the communication control unit 310 controls the overall operation of the wireless terminal device 300.
- the communication control unit 310 is connected to a reception unit 320, a time slot selection unit 330, a time slot management unit 350, a transmission unit 360, a comparison data generation unit 370, and a base station authentication unit 380.
- the receiving unit 320 receives an authentication start request and authentication information including base station authentication data transmitted from the radio base station apparatus 200, respectively.
- the time slot selecting unit 330 randomly selects a time slot used for a response to the authentication start request from the time slots managed by the time slot managing unit 350.
- the selection status management unit 340 is connected to the time slot selection unit 330. Then, the selection status management unit 340 manages the selection status indicating the presence / absence of selection for each time slot in the time slot selection unit 330.
- the time slot management unit 350 holds a predetermined slot number and a predetermined time slot interval (time slot length) in advance.
- the time slot management unit 350 is connected to the reception unit 320 and the transmission unit 360. Then, the time slot management unit 350 manages a time slot shared with the radio base station apparatus 200 after at least the time slot selection unit 330 selects a time slot.
- the transmission unit 360 transmits a response to the authentication start request to the radio base station apparatus 200 using the time slot selected by the time slot selection unit 330.
- the comparison data generation unit 370 holds data generation rules for comparison data in advance.
- the comparison data generation unit 370 is connected to the selection status management unit 340. Then, the comparison data generation unit 370 generates comparison data according to the data generation rule stored in advance based on the selection status managed by the selection status management unit 340.
- the base station authentication unit 380 performs base station authentication based on whether or not the received base station authentication data matches the comparison data generated by the comparison data generation unit 370.
- the radio base station apparatus 200 includes, for example, a CPU, a storage medium such as a ROM storing a control program, and a working memory such as a storage medium. In this case, the function of each unit is realized by the CPU executing the control program.
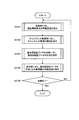
- FIG. 14 is a flowchart showing an example of the operation of the communication control unit 210 of the radio base station apparatus 200.
- the communication control unit 210 instructs the transmission unit 220 to broadcast the authentication start request (S3101), and then the process is returned from the transmission unit 220.
- the communication control unit 210 manages time, for example, instructs the transmission unit 220 to broadcast the authentication start request at an arbitrary time interval.
- the communication control unit 210 instructs the time slot management unit 230 to start management of the time slot (S3102).
- the communication control unit 210 instructs the base station authentication data generation unit 260 to generate base station authentication data (S3103).
- the communication control unit 210 passes the base station authentication data to the transmission unit 220, and includes authentication information including the base station authentication data. Is sent (S3104). Then, the communication control unit 210 determines whether or not the end of the process related to base station authentication is instructed by an operator operation or the like, and repeats the above-described process while not instructing to end (S3105).
- FIG. 15 is a flowchart showing an example of the operation of the transmission unit 220 of the radio base station apparatus 200.
- the transmission unit 220 receives an instruction to broadcast an authentication start request from the communication control unit 210, and every time an instruction is received (S3201: YES), broadcasts an authentication start request (S3202). The process is returned to the communication control unit 210 (S3203). Further, the transmission unit 220 accepts an instruction for broadcast transmission of authentication information including base station authentication data from the communication control unit 210. Whenever the instruction is received (3204: YES), the transmission unit 220 broadcasts the authentication information including the base station authentication data (S3205). When the transmission is completed, the process returns to the communication control unit 210 (S3203). ).
- FIG. 16 is a flowchart showing an example of the operation of the time slot management unit 230 of the radio base station apparatus 200.
- the time slot management unit 230 receives a time slot management start instruction from the communication control unit 210, and performs time slot management (S3302 to S3305) each time an instruction is received (S3301: YES).
- the time slot management unit 230 first sets the time slot number to the initial value “0” (S3302). Next, the time slot management unit 230 increments the time slot number until the time slot number reaches the predetermined time slot number based on the predetermined time slot interval (S3305). Meanwhile, the time slot management unit 230 passes each time slot number and a predetermined time slot interval to the receiving unit 240 and instructs reception of a response (S3303 to S3305).
- the time slot management unit 230 returns the process to the communication control unit 210 (S3306).
- FIG. 17 is a flowchart showing an example of the operation of the receiving unit 240 of the radio base station apparatus 200.
- the receiving unit 240 receives a specification of a time slot number and a time slot interval and a reception instruction from the time slot management unit 230. Next, every time an instruction is received (S3401: YES), the receiving unit 240 waits for a response from the wireless terminal device 300 in units of the specified time slot interval (S3402 to S3406).
- the receiving unit 240 first starts time measurement (S3402), and determines whether a response has been received from the wireless terminal device 300 until the predetermined slot interval is reached (S3403).
- the receiving unit 240 notifies the reception status management unit 250 of a time slot number and a reception notification that is information indicating that the response has been received. (S3407).
- the reception status management unit 250 is provided with a time slot number and information indicating that no response has been received. A certain unreceived notification is handed over (S3408).
- the reception unit 240 After receiving the reception notification or the non-reception notification to the reception status management unit 250, the reception unit 240 returns the processing to the time slot management unit 230 when the processing is returned from the reception status management unit 250.
- FIG. 18 is a flowchart showing an example of the operation of the reception status management unit 250 of the radio base station apparatus 200.
- the reception status management unit 250 receives a time slot number and a reception notification or non-reception notification from the reception unit 240. Next, each time a notification is received (S3501: YES), the reception status management unit 250 manages a reception status in which the received time slot number is associated with an identifier corresponding to the notification content (S3502 to 3505).
- the reception status management unit 250 first sets the time slot number to the initial value “0” (S3502). Next, the reception status management unit 250 increments the time slot number until the time slot number reaches a predetermined time slot number n, and determines whether or not a reception notification is received corresponding to each time slot number. .
- the reception status management unit 250 associates and manages the time slot number and the identifier indicating reception (S3504). If the reception status management unit 250 has not received a reception notification (received a non-reception notification) (S3503: NO), the reception status management unit 250 manages the time slot number in association with an identifier indicating non-reception (S3505). ).
- the reception status management unit 250 returns the processing to the reception unit 240 (S3508).
- FIG. 19 is a flowchart showing an example of the operation of the base station authentication data generation unit 260 of the radio base station apparatus 200.
- the base station authentication data generation unit 260 receives an instruction to generate base station authentication data from the communication control unit 210.
- the base station authentication data generation unit 260 acquires the reception status from the reception status management unit 250 every time an instruction to generate base station authentication data is received (S3601: YES) (S3602).
- the base station authentication data generation unit 260 generates base station authentication data according to a predetermined data generation rule (S3603). Then, the base station authentication data generation unit 260 passes the generated base station authentication data to the communication control unit 210 and returns the process (S3604).
- base station authentication data generation section 260 generates base station authentication data according to the data generation rules described with reference to FIG. That is, base station authentication data generation section 260 generates base station authentication data by rearranging information associated with each time slot number in the reception state in ascending order of time slot numbers.
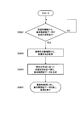
- FIG. 20 is a flowchart illustrating an example of the operation of the communication control unit 310 of the wireless terminal device 300.
- the communication control unit 310 instructs the reception unit 320 to receive an authentication start request (S4101).
- the communication control unit 310 next instructs the time slot selection unit 330 to select a time slot number for responding to the authentication start request (S4102).
- the communication control unit 310 is returned from the time slot selection unit 330 together with the time slot number.
- the communication control unit 310 passes the time slot number received from the time slot selection unit 330 to the time slot management unit 350 and instructs the start of time slot management (S4103).
- the communication control unit 310 instructs the comparison data generation unit 370 to generate comparison data (S4104).
- the communication control unit 310 instructs the reception unit 320 to receive the authentication information including the base station authentication data from the radio base station apparatus 200 ( S4105).
- the communication control unit 310 is returned from the receiving unit 320 together with the base station authentication data.
- the communication control unit 310 passes the base station authentication data received from the reception unit 320 and the comparison data received from the comparison data generation unit 370 to the base station authentication unit 380, and instructs base station authentication. (S4106).
- the communication control unit 310 returns the process from the base station authentication unit 380 together with the authentication result.
- the communication control unit 310 continues the communication process (S4108). If the received authentication result is “NG” (S4107: NO), the communication control unit 310 ends the communication process (S4109).
- the communication control unit 310 determines whether or not the end of the process related to the base station authentication is instructed by a user operation or the like, and repeats the above process while the end of the process is not instructed (S4110).
- FIG. 21 is a flowchart illustrating an example of the operation of the reception unit 320 of the wireless terminal device 300.
- the receiving unit 320 receives an instruction to receive an authentication start request from the communication control unit 310, and waits for reception of the authentication start request each time an instruction is received (S4201: YES). And the receiving part 320 will return a process to the communication control part 310, if the authentication start request
- the receiving unit 320 receives an instruction to receive authentication information including base station authentication data from the communication control unit 310, and waits for reception of the authentication information every time an instruction is received (S4204: YES). Then, when receiving the authentication information including the base station authentication data from the radio base station apparatus 200 (S4205: YES), the receiving unit 320 passes the received base station authentication data to the communication control unit 310 and returns the process. (S4203).
- FIG. 22 is a flowchart illustrating an example of the operation of the time slot selection unit 330 of the wireless terminal device 300.
- the time slot selection unit 330 receives a time slot selection instruction from the communication control unit 310. Next, every time an instruction is received (S4301: YES), the time slot selection unit 330 randomly selects at least one time slot number within a predetermined time slot number range (S4302).
- the time slot selection unit 330 notifies the selection status management unit 340 of the selected time slot number (S4303).
- the time slot selection unit 330 passes the time slot number to the communication control unit 310 and returns the processing (S4304).
- FIG. 23 is a flowchart illustrating an example of the operation of the selection status management unit 340 of the wireless terminal device 300.
- the selection status management unit 340 receives the time slot number from the time slot selection unit 330. Next, every time a time slot number is received (S4401: YES), the selection status management unit 340 manages the selection status in which the received time slot number is associated with an identifier indicating that it has been selected (S4402). . Then, the selection status management unit 340 manages the selection status in which a time slot number other than the received time slot number is associated with an identifier indicating that the time slot number is not selected (S4403), and the time slot selection unit 330 performs processing. Return (S4404).
- FIG. 24 is a flowchart showing an example of the operation of the time slot management unit 350 of the wireless terminal device 300.
- the time slot management unit 350 receives a time slot number and an instruction to start time slot management from the communication control unit 310. Each time the time slot management unit 350 receives a time slot number and a time slot management start instruction (S4501: YES), the time slot management unit 350 performs time slot management (S4502 to S4506).
- the time slot management unit 350 first sets the time slot number to the initial value “0” (S4502). Next, the time slot management unit 350 increments the time slot number based on the predetermined time slot interval until the time slot number reaches the predetermined time slot number (S4506). Meanwhile, the time slot management unit 350 determines whether or not the incremented time slot number matches the time slot number received from the communication control unit 310.
- the time slot management unit 350 passes a predetermined time slot interval to the transmission unit 360 and instructs transmission of a response to the authentication start request (S4504). . Then, when the incrementing time slot number reaches the predetermined time slot number (S4505: YES), the time slot management unit 350 returns the processing to the communication control unit 310 (S4507).
- FIG. 25 is a flowchart illustrating an example of the operation of the transmission unit 360 of the wireless terminal device 300.
- the transmission unit 360 receives from the time slot management unit 350 a time slot interval and a response transmission instruction for the authentication start request. Next, each time an instruction is received (S4601: YES), the transmission unit 360 generates and transmits a response to the authentication start request within the designated time slot interval (S4602, 4603).
- the transmission unit 360 first starts time measurement (S4602), and transmits a response to the radio base station apparatus 200 (S4603). Next, when the designated time slot interval has elapsed since the start of measurement (S4604: YES), the transmission unit 360 returns the processing to the time slot management unit 350 (S4605).
- FIG. 26 is a flowchart illustrating an example of the operation of the comparison data generation unit 370 of the wireless terminal device 300.
- the comparison data generation unit 370 receives an instruction to generate comparison data from the communication control unit 310. Then, each time the comparison data generation unit 370 receives an instruction to generate comparison data (S4701: YES), the comparison data generation unit 370 acquires the selection status from the selection status management unit 340 (S4702).
- the comparison data generation unit 370 generates comparison data according to a predetermined data generation rule (S4703). Then, the comparison data generation unit 370 passes the generated comparison data to the communication processing unit 1107 and returns the process (S4704).
- the comparison data generation unit 370 generates comparison data according to the data generation rule described with reference to FIG. That is, the comparison data generation unit 370 generates comparison data by rearranging information associated with each time slot number in the selection situation in ascending order of the time slot numbers.
- FIG. 27 is a flowchart showing an example of the operation of the base station authentication unit 380 of the wireless terminal device 300.
- the base station authentication unit 380 receives base station authentication data and comparison data, and a base station authentication instruction from the communication control unit 310.
- the base station authentication unit 380 calculates the logical product (AND) of the base station authentication data and the comparison data every time an instruction for base station authentication is received (S4801: YES) (S4802). Then, the base station authentication unit 380 determines whether or not the calculation result matches the comparison data. In addition, the base station authentication unit 380 determines whether the bit position where the value is “1” in the bit pattern of the comparison data matches the bit position corresponding to the bit pattern of the base station authentication data. Whether or not (both are “1”) may be determined.
- the base station authentication unit 380 determines that the received base station authentication data is not due to a replay attack. The base station authentication unit 380 then passes the identifier “authentication OK” to the communication control unit 310 and returns the processing (S4804).
- the base station authentication unit 380 determines that the received base station authentication data is due to the replay attack. The base station authentication unit 380 then passes the identifier “authentication NG” to the communication control unit 310 and returns the process (S4805).
- each unit realizes the operation of the radio base station apparatus 200, the operation of the radio terminal apparatus 300, and the operation of the radio communication system 100 described with reference to FIGS.
- radio communication system 100 can generate and use common base station authentication data that is effective with respect to defense against replay attacks in a plurality of radio terminal apparatuses 300. . Therefore, radio communication system 100 according to the present embodiment can reduce the number of times base station authentication data is generated and the number of times signatures are assigned to base station authentication data. In addition, radio communication system 100 according to the present embodiment can reduce the number of transmissions of base station authentication data by performing broadcast transmission.
- the radio communication system 100 eliminates the replay attack in each radio terminal device 300, and reduces the computation time and transmission time of the base station authentication data for each radio terminal device 300, which has been conventionally required. Can be reduced. As a result, radio communication system 100 according to the present embodiment realizes a reduction in time slot length, and allows more radio terminal apparatuses 300 to perform base station authentication within a certain period of time.
- the radio communication system 100 generates variable information such as “a time slot selected by each radio terminal device 300” and “the number of selected time slots” for generating base station authentication data. Are used in combination. Thereby, even if a third party tries a replay attack using the base station authentication data transmitted from the radio base station apparatus 200 in the past, the base station authentication data and the current comparison data do not match. Therefore, radio communication system 100 according to the present embodiment can improve the security level of authentication.
- the number of wireless terminal devices 300 for which one base station authentication data is generated is not limited to the number described above.
- the data generation rules for base station authentication data and comparison data are not limited to the above-mentioned contents, and contents arranged in descending order of time slot numbers and other various sorting functions for time slot numbers are adopted. can do.
- the creation of the base station authentication data and the creation of the comparison data may not be performed in units of frames, but may be performed in units of some time slots among a plurality of time slots constituting the frame. That is, the predetermined time slot number n may be smaller than the number of time slots of a frame in which a response to the authentication start request is performed. In this case, a plurality of base station authentication data are generated and transmitted for one frame. Thereby, depending on the data generation rules of the base station authentication data and the comparison data, the generation time, transmission time, and collation time of each data can be further shortened.
- the second embodiment of the present invention adds a random value generated by the wireless terminal device to the response to the authentication start request, and uses the random value for generating the base station authentication data and the comparison data. Randomness is further improved.
- FIG. 28 is a block diagram showing an example of the configuration of radio terminal apparatus 300a according to the present embodiment, and corresponds to FIG. 13 of the first embodiment. Parts that are the same as or correspond to those in FIG. 13 are given the same reference numerals, and descriptions thereof are omitted.
- the wireless terminal device 300a includes a time slot selection unit 330a, a selection status management unit 340a, a time slot management unit 350a, and a transmission unit 360a different from the configuration shown in FIG. Furthermore, the wireless terminal device 300a newly includes a random number generation unit 390a.
- the random number generation unit 390a is disposed in the time slot selection unit 330a, for example.
- the random number generation unit 390a generates a random value using, for example, a known pseudorandom number generation method. However, the random number generation unit 390a generates a random value within a range other than “0”, which is an identifier indicating unreceived and unselected, and in a size that can be embedded in a response.
- the time slot selection unit 330a generates a random value for each selected time slot using the random number generation unit 390a. Then, the time slot selection unit 330a passes the generated random number value to the selection status management unit 340a and the communication control unit 310.
- the selection status management unit 340a When the selection status management unit 340a receives the random value from the time slot selection unit 330a, the selection status management unit 340a manages the selection status in which the time slot number and the random value are associated with each other.
- the time slot management unit 350a When the time slot management unit 350a receives a random value from the time slot selection unit 330a, the time slot management unit 350a instructs the transmission unit 360a to transmit a response in which the random value is embedded as a response.
- the transmission unit 360a receives a response transmission instruction and a random value from the time slot management unit 350a. Then, the transmission unit 360a generates a response in which the received random number value is embedded, and transmits the response using the selected slot as a response to the authentication start request.
- FIG. 29 is a diagram illustrating an example of a data structure of a response in which a random number value is embedded, and corresponds to FIG. 6 of the first embodiment. The same parts as those in FIG.
- the response wireless data 530 in which the random value is embedded is configured by arranging a synchronization code 511, a length 512, a command code 513, a random value 531 and a checksum 514 in this order.
- Length 512 describes the total length of command code 513, random number value 531, and checksum 514.
- the wireless terminal device 300 describes a predetermined command code indicating that the wireless data 530 is a response and stores a random number in the command code 513. In addition, the wireless terminal device 300 describes the generated random value in the random value 531 and generates response wireless data 530 in which the random value is embedded.
- the predetermined command code is described in the command code 513
- the radio base station apparatus 200 determines that the radio data 510 is a response, and extracts the random value 531.
- Such a wireless terminal device 300a transmits the generated random number value as a response to the wireless base station device 200a, and uses the data in which the random number value and the identifier indicating unselected are arranged in ascending order of time slot numbers as comparison data. Can be generated. Then, the wireless terminal device 300a performs base station authentication based on whether or not the selected random number value is associated with the selected time slot number in the base station authentication data sent from the wireless base station device 200a. Can do.
- FIG. 30 is a block diagram showing an example of the configuration of radio base station apparatus 200a according to the present embodiment, and corresponds to FIG. 12 of the first embodiment. Portions that are the same as or correspond to those in FIG. 12 are given the same reference numerals, and descriptions thereof are omitted.
- the radio base station apparatus 200a includes a receiving unit 240a and a receiving status management unit 250a different from these instead of the receiving unit 240 and the receiving status management unit 250 shown in FIG.
- the receiving unit 240a When receiving the response to the authentication start request, the receiving unit 240a passes the random number value embedded in the ACK message sent as a response instead of the reception notification to the reception status management unit 250a.
- the reception status management unit 250a When the reception status management unit 250a receives a random value from the reception unit 240a, the reception status management unit 250a manages the reception status in which the time slot number and the random value are associated with each other.
- Such a radio base station apparatus 200a can generate, as base station authentication data, data in which received random values and identifiers indicating non-reception are arranged in ascending order of time slot numbers.
- FIG. 31 is a sequence diagram showing an example of the overall operation of the radio communication system having radio base station apparatus 200a and radio terminal apparatus 300a, and corresponds to FIG. 5 of the first embodiment.
- FIG. 32 is a schematic diagram illustrating an example of a data generation rule for base station authentication data by the radio base station apparatus 200a, and corresponds to FIG. 8 of the first embodiment.
- FIG. 33 is a schematic diagram illustrating an example of a data generation rule for comparison data by the wireless terminal device 300a, and corresponds to FIG. 9 of the first embodiment.
- each wireless terminal device 300a includes the generated random value in each of the response to the wireless base station device 200a and the selection status. Also, the radio base station apparatus 200a manages the reception status including the received random number value.
- FIG. 34 is a flowchart showing an example of the operation of the receiving unit 240a of the radio base station apparatus 200a, and corresponds to FIG. 17 of the first embodiment.
- the receiving unit 240a When receiving a response from the wireless terminal device 300a (S3403: YES, S3405: YES), the receiving unit 240a passes the time slot number and the random number value included in the response to the reception status management unit 250a ( S3407a).
- FIG. 35 is a flowchart showing an example of the operation of the reception status management unit 250a of the radio base station apparatus 200a, and corresponds to FIG. 18 of the first embodiment.
- the reception status management unit 250a manages the time slot notified of the random value from the receiving unit 240a (S3503a: YES) by associating the time slot number with the random value (S3504a).
- base station authentication data in which a random number value is embedded is generated and broadcast.
- FIG. 36 is a flowchart showing an example of the operation of the time slot selection unit 330a of the wireless terminal device 300a, and corresponds to FIG. 22 of the first embodiment.
- the time slot selection unit 330a generates a random value for each selected time slot using the random number generation unit 390a (S4302a). Then, the time slot selection unit 330a notifies the selection status management unit 340a of the selected time slot number and a random value corresponding to the time slot number (S4303a), and the processing is returned from the selection status management unit 340a. . Next, the time slot selection unit 330a passes the selected time slot number and the random value corresponding to the time slot number to the communication control unit 310, and returns the process (S4304a).
- FIG. 37 is a flowchart showing an example of the operation of the selection status management unit 340a of the wireless terminal device 300a, and corresponds to FIG. 23 of the first embodiment.
- the selection status management unit 340a receives the time slot number and the random value corresponding to the time slot number from the time slot selection unit 330a (S4401a: YES). Next, the selection status management unit 340a manages the received time slot number in association with the random value (S4402a).
- FIG. 38 is a flowchart showing an example of the operation of the time slot management unit 350a of the wireless terminal device 300a, and corresponds to FIG. 24 of the first embodiment.
- the time slot management unit 350a receives a time slot number and a random value corresponding to the time slot number from the communication control unit 310, and is instructed to start management of the time slot (S4501a: YES). Next, the time slot management unit 350a starts incrementing the time slot number. Then, when the time slot of the received time slot number arrives (S4503: YES), the time slot management unit 350a passes the time slot interval and a random value corresponding to the time slot number to the transmission unit 360a. Then, the time slot management unit 350a instructs a response to the authentication start request (S4504a).
- FIG. 39 is a flowchart illustrating an example of the operation of the transmission unit 360a of the wireless terminal device 300a, and corresponds to FIG. 25 of the first embodiment.
- the transmission unit 360a receives the time slot interval and the random value corresponding to the time slot number from the time slot management unit 350a (S4601a: YES). Next, the transmission unit 360a transmits the received random value to the radio base station apparatus 200a as a response to the authentication start request using the current time slot (S4603a).
- comparison data including a random value is generated and transmitted to the radio base station apparatus 200a.
- the base station authentication unit 380 of the wireless terminal device 300a performs, for example, binary data and takes a logical product, and determines whether the result of the logical product matches the comparison data. It is sufficient to determine whether or not and match.
- the radio terminal apparatus 300a according to the present embodiment uses a random number value in combination with the three fluctuating values described in the first embodiment when generating the base station authentication data. Therefore, the wireless terminal device 300a according to the present embodiment can realize authentication with higher safety.
- the wireless terminal device 300a that does not transmit a response due to duplication with another wireless terminal device 300a determines data matching based on whether or not it is the slot that received the response, rather than a random number value match / mismatch. It is desirable to do. That is, the determination of data consistency of the wireless terminal device 300a is based on whether or not the value of the position corresponding to the selected time slot in the base station authentication data is “0”. .
- a wireless base station device that is a wireless communication device to be authenticated is fixedly installed and a wireless terminal device that is a wireless communication device that performs authentication moves.
- the present invention is not limited to this. All or some of the plurality of radio terminal apparatuses may be fixedly installed, and the radio base station apparatus may move, or both the plurality of radio terminal apparatuses and the radio base station apparatus may move.
- the radio base station apparatus may add a data generation rule for comparison data corresponding to the base station authentication data held by the radio base station apparatus as shared information to the authentication start request or the base station authentication data. good.
- the comparison data generation unit acquires a comparison data generation rule from the authentication start request or the shared information added to the base station authentication data.
- the radio base station apparatus and each radio terminal apparatus may switch the data generation rules for base station authentication data and comparison data to be used between each base station authentication.
- the execution order of the data generation rules may be set in advance, and information indicating which data generation rule is used every time base station authentication is started. You may replace it.
- the base station authentication data is not necessarily data in which identifiers for each time slot are arranged, and is data in which the presence / absence of a response for each time slot is aggregated for a plurality of time slots, and is analyzed on the wireless terminal device side. Any data can be used. For example, data describing the time slot number of the time slot in which there was a response can be considered.
- a radio base station apparatus, a radio terminal apparatus, and a base station authentication method enable a radio base station apparatus, a radio terminal apparatus, and a base that allow more radio terminal apparatuses to perform base station authentication within a certain period of time. This is useful as a station authentication method.
Landscapes
- Engineering & Computer Science (AREA)
- Computer Security & Cryptography (AREA)
- Computer Networks & Wireless Communication (AREA)
- Signal Processing (AREA)
- Mobile Radio Communication Systems (AREA)
Priority Applications (2)
| Application Number | Priority Date | Filing Date | Title |
|---|---|---|---|
| EP10748441.2A EP2405683B1 (en) | 2009-03-04 | 2010-02-16 | Wireless base station apparatus, wireless terminal apparatus, and base station authentication method |
| US13/254,433 US9084113B2 (en) | 2009-03-04 | 2010-02-16 | Wireless base station apparatus, wireless terminal apparatus, and base station authentication method |
Applications Claiming Priority (2)
| Application Number | Priority Date | Filing Date | Title |
|---|---|---|---|
| JP2009051319A JP5225894B2 (ja) | 2009-03-04 | 2009-03-04 | 無線基地局装置、無線端末装置、無線通信システム、および基地局認証方法 |
| JP2009-051319 | 2009-03-04 |
Publications (1)
| Publication Number | Publication Date |
|---|---|
| WO2010100838A1 true WO2010100838A1 (ja) | 2010-09-10 |
Family
ID=42709410
Family Applications (1)
| Application Number | Title | Priority Date | Filing Date |
|---|---|---|---|
| PCT/JP2010/000951 Ceased WO2010100838A1 (ja) | 2009-03-04 | 2010-02-16 | 無線基地局装置、無線端末装置、および基地局認証方法 |
Country Status (4)
| Country | Link |
|---|---|
| US (1) | US9084113B2 (enExample) |
| EP (1) | EP2405683B1 (enExample) |
| JP (1) | JP5225894B2 (enExample) |
| WO (1) | WO2010100838A1 (enExample) |
Families Citing this family (11)
| Publication number | Priority date | Publication date | Assignee | Title |
|---|---|---|---|---|
| WO2011046630A1 (en) * | 2009-10-14 | 2011-04-21 | Qualcomm Incorporated | Transmission failure detection in the random access procedure in time division synchronous code division multiple access (td-scdma) networks |
| US9026813B2 (en) | 2010-11-22 | 2015-05-05 | Qualcomm Incorporated | Establishing a power charging association on a powerline network |
| US9021278B2 (en) * | 2011-08-10 | 2015-04-28 | Qualcomm Incorporated | Network association of communication devices based on attenuation information |
| JP2013110677A (ja) * | 2011-11-24 | 2013-06-06 | Mega Chips Corp | 通信システムおよび通信装置 |
| KR101920893B1 (ko) | 2014-01-28 | 2018-11-21 | 후아웨이 디바이스 (둥관) 컴퍼니 리미티드 | 자원 할당 방법 및 사용자 장비 |
| JP6570275B2 (ja) * | 2015-03-12 | 2019-09-04 | 綜合警備保障株式会社 | 警備システム及び警備方法 |
| CN113163347B (zh) * | 2016-10-01 | 2022-09-09 | 华为技术有限公司 | 一种广播承载管理的方法及其设备 |
| JP2019062417A (ja) * | 2017-09-27 | 2019-04-18 | カルソニックカンセイ株式会社 | 無線通信システムおよび無線通信方法 |
| CN112399411B (zh) * | 2019-07-31 | 2022-04-29 | 上海华为技术有限公司 | 一种认证接入网设备的方法以及相关设备 |
| CN111628869B (zh) * | 2020-05-27 | 2022-07-22 | 南通华欣民福工业技术有限公司 | 一种基站存储n的节点与基站双向认证方法 |
| CN111615110B (zh) * | 2020-05-27 | 2022-12-20 | 南通华欣民福工业技术有限公司 | 一种节点存储n的节点与基站双向认证方法 |
Citations (4)
| Publication number | Priority date | Publication date | Assignee | Title |
|---|---|---|---|---|
| JP2000003420A (ja) * | 1998-06-11 | 2000-01-07 | Toshiba Corp | 位置認識システム |
| JP2006099343A (ja) * | 2004-09-29 | 2006-04-13 | Saxa Inc | Icタグリーダ |
| JP2009038588A (ja) * | 2007-08-01 | 2009-02-19 | Panasonic Corp | 無線通信方法、無線通信システム及び無線通信装置 |
| JP2009051319A (ja) | 2007-08-24 | 2009-03-12 | Denso Corp | 車両用凍結除去装置 |
Family Cites Families (11)
| Publication number | Priority date | Publication date | Assignee | Title |
|---|---|---|---|---|
| US6950521B1 (en) * | 2000-06-13 | 2005-09-27 | Lucent Technologies Inc. | Method for repeated authentication of a user subscription identity module |
| US6973566B2 (en) * | 2001-07-09 | 2005-12-06 | Advanced Micro Devices, Inc. | Software modem with privileged mode oversight of control parameters |
| US7257098B2 (en) * | 2001-07-10 | 2007-08-14 | Hitachi Kokusai Electric Inc. | Wireless communications equipment |
| US20080258864A1 (en) * | 2004-10-28 | 2008-10-23 | Mitsubishi Electeic Corporation | Communication Apparatus and Communication Method |
| WO2007072814A1 (ja) * | 2005-12-19 | 2007-06-28 | Nippon Telegraph And Telephone Corporation | 端末識別方法、認証方法、認証システム、サーバ、端末、無線基地局、プログラムおよび記録媒体 |
| JP2007258986A (ja) * | 2006-03-22 | 2007-10-04 | Toshiba Corp | 通信装置、通信方法および通信プログラム |
| JP4781890B2 (ja) | 2006-04-11 | 2011-09-28 | 日本電信電話株式会社 | 通信方法及び通信システム |
| US8060741B2 (en) * | 2006-12-29 | 2011-11-15 | Industrial Technology Research Institute | System and method for wireless mobile network authentication |
| JP5042640B2 (ja) * | 2007-01-17 | 2012-10-03 | パナソニック株式会社 | 無線認証システム |
| JP4899941B2 (ja) * | 2007-03-05 | 2012-03-21 | パナソニック電工株式会社 | 質問器、応答器、及び、無線認証システム |
| US20100118698A1 (en) | 2007-08-01 | 2010-05-13 | Panasonic Corporation | Radio communication method, radio communication system, radio communication device, and congestion control method |
-
2009
- 2009-03-04 JP JP2009051319A patent/JP5225894B2/ja not_active Expired - Fee Related
-
2010
- 2010-02-16 EP EP10748441.2A patent/EP2405683B1/en not_active Not-in-force
- 2010-02-16 WO PCT/JP2010/000951 patent/WO2010100838A1/ja not_active Ceased
- 2010-02-16 US US13/254,433 patent/US9084113B2/en not_active Expired - Fee Related
Patent Citations (4)
| Publication number | Priority date | Publication date | Assignee | Title |
|---|---|---|---|---|
| JP2000003420A (ja) * | 1998-06-11 | 2000-01-07 | Toshiba Corp | 位置認識システム |
| JP2006099343A (ja) * | 2004-09-29 | 2006-04-13 | Saxa Inc | Icタグリーダ |
| JP2009038588A (ja) * | 2007-08-01 | 2009-02-19 | Panasonic Corp | 無線通信方法、無線通信システム及び無線通信装置 |
| JP2009051319A (ja) | 2007-08-24 | 2009-03-12 | Denso Corp | 車両用凍結除去装置 |
Also Published As
| Publication number | Publication date |
|---|---|
| JP2010206655A (ja) | 2010-09-16 |
| EP2405683A1 (en) | 2012-01-11 |
| EP2405683A4 (en) | 2016-04-27 |
| EP2405683B1 (en) | 2018-06-27 |
| US20110317672A1 (en) | 2011-12-29 |
| JP5225894B2 (ja) | 2013-07-03 |
| US9084113B2 (en) | 2015-07-14 |
Similar Documents
| Publication | Publication Date | Title |
|---|---|---|
| JP5225894B2 (ja) | 無線基地局装置、無線端末装置、無線通信システム、および基地局認証方法 | |
| EP1271853B1 (en) | Communication device, method and system for interference reduction | |
| US8249093B2 (en) | Communication method and communication device as well as computer program | |
| EP1903705B1 (en) | Radio resource assigning method and communication apparatus | |
| EP3413676B1 (en) | Method and device for transmitting prach signals in unauthorized spectrum | |
| US20150055615A1 (en) | Handshaking method and apparatus for ofdm systems with unknown sub-channel availability | |
| WO2008069245A1 (ja) | 無線通信システム、無線端末局、無線基地局および無線通信方法 | |
| CN102761402A (zh) | Ism频段数据通信实现方法、装置和一种无线通信系统 | |
| KR20180126445A (ko) | 피드백 정보를 전송하는 방법 및 장치 | |
| CN113067658A (zh) | 窄带自组网通信控制方法及相关设备 | |
| JP2019013011A (ja) | マルチバンド無線チャンネルにおけるライセンスフィードバックを使用したアンライセンス帯域通信のための認知イネーブラを実現する装置及び方法 | |
| US9801005B2 (en) | Method of period allocation for medium and wireless communication system thereof | |
| CN111466144B (zh) | 发送数据的方法、接收数据的方法、终端设备和网络设备 | |
| JP4704909B2 (ja) | 基地局装置及び基地局装置の制御方法 | |
| EP1768279A1 (en) | Radio communication system | |
| JP2006197032A (ja) | データ伝送システム | |
| US7260359B2 (en) | Method for transmission of data between a master station and a slave station, and a data transmission system | |
| CN110603784B (zh) | 通信方法、移动单元、接口单元和通信系统 | |
| JP7011192B2 (ja) | 無線通信装置、無線通信システム、及び無線通信方法 | |
| US12457634B2 (en) | Communication system and communication method | |
| JP5704682B2 (ja) | 無線通信システム、干渉防止方法 | |
| Vukovic et al. | Simple asynchronous multiple access (SAMA) for ad hoc wireless networks in unlicensed bands |
Legal Events
| Date | Code | Title | Description |
|---|---|---|---|
| 121 | Ep: the epo has been informed by wipo that ep was designated in this application |
Ref document number: 10748441 Country of ref document: EP Kind code of ref document: A1 |
|
| WWE | Wipo information: entry into national phase |
Ref document number: 13254433 Country of ref document: US Ref document number: 2010748441 Country of ref document: EP |
|
| NENP | Non-entry into the national phase |
Ref country code: DE |