EP2058769B1 - Procédé d'affranchissement et système d'expédition de courrier avec augmentation de frais de port centrale - Google Patents
Procédé d'affranchissement et système d'expédition de courrier avec augmentation de frais de port centrale Download PDFInfo
- Publication number
- EP2058769B1 EP2058769B1 EP08017285A EP08017285A EP2058769B1 EP 2058769 B1 EP2058769 B1 EP 2058769B1 EP 08017285 A EP08017285 A EP 08017285A EP 08017285 A EP08017285 A EP 08017285A EP 2058769 B1 EP2058769 B1 EP 2058769B1
- Authority
- EP
- European Patent Office
- Prior art keywords
- franking
- key
- idakey
- postal
- image
- Prior art date
- Legal status (The legal status is an assumption and is not a legal conclusion. Google has not performed a legal analysis and makes no representation as to the accuracy of the status listed.)
- Not-in-force
Links
Images
Classifications
-
- G—PHYSICS
- G07—CHECKING-DEVICES
- G07B—TICKET-ISSUING APPARATUS; FARE-REGISTERING APPARATUS; FRANKING APPARATUS
- G07B17/00—Franking apparatus
- G07B17/00733—Cryptography or similar special procedures in a franking system
-
- G—PHYSICS
- G07—CHECKING-DEVICES
- G07B—TICKET-ISSUING APPARATUS; FARE-REGISTERING APPARATUS; FRANKING APPARATUS
- G07B17/00—Franking apparatus
- G07B17/00016—Relations between apparatus, e.g. franking machine at customer or apparatus at post office, in a franking system
- G07B17/0008—Communication details outside or between apparatus
- G07B2017/00153—Communication details outside or between apparatus for sending information
- G07B2017/00169—Communication details outside or between apparatus for sending information from a franking apparatus, e.g. for verifying accounting
-
- G—PHYSICS
- G07—CHECKING-DEVICES
- G07B—TICKET-ISSUING APPARATUS; FARE-REGISTERING APPARATUS; FRANKING APPARATUS
- G07B17/00—Franking apparatus
- G07B17/00459—Details relating to mailpieces in a franking system
- G07B17/00508—Printing or attaching on mailpieces
- G07B2017/00572—Details of printed item
- G07B2017/0058—Printing of code
-
- G—PHYSICS
- G07—CHECKING-DEVICES
- G07B—TICKET-ISSUING APPARATUS; FARE-REGISTERING APPARATUS; FRANKING APPARATUS
- G07B17/00—Franking apparatus
- G07B17/00733—Cryptography or similar special procedures in a franking system
- G07B2017/00846—Key management
Definitions
- the invention relates to a franking method and mailing system with central postage collection.
- the mailing system includes a data center of a mail carrier, an operator data center, and at least one meter.
- the mail carrier transports the mail pieces franked by the franking machine to the mail center.
- the purpose of the invention is to provide a secure mailing system with simple franking devices. So far, there was no simple solution that requires the sender either a personal computer (PC) with printer or a special very easy-to-use franking device, but requires neither an online connection for each franking nor a security module. Such an offline solution without a security module becomes possible if the postal carriers carry out the postage determination and billing as part of their service provision.
- PC personal computer
- postage fees are due if the corresponding postage stamps are ordered or delivered, for example in the form of stamps, computer printing and delivery lists, franking imprints on franking machines and PC franking solutions and franking service, etc.
- postal carriers proceed to fully automatically record the processed mail for the purposes of address recognition and additional services such as shipment tracking, it is also possible to collect the postage due postage processing at the mail center.
- a handwritten signature represents a sender's biometric identity that the sender applies to a mailing by making a handwritten signature using a digitizer pen.
- a mail carrier then scans the signature and has a central remote service check that the read signature is valid. In the remote service and the digitizer was originally registered by means of signature sample.
- the digitizer pin writes information to a Radio Frequency Identity Device (RFID) with the RFID tag attached to the mailing device.
- RFID Radio Frequency Identity Device
- the mail carrier receives a response and applies the result on the mailpiece if it is positive.
- a biometric sender identifier does not allow a unique device identifier. There is no integrity check sum provided via the sender ID.
- the sender can deliver a larger amount of mail by simultaneously providing a mailing manifest.
- manifest mailing systems not the sender but the posting post office determines the required postage amount based on the posting list. On the individual mail items, therefore, only one feature must be attached, which establishes a reference to the associated posting list (permit imprint). Unusually, an RFID tag is provided for this purpose.
- a sender ID is only provided in the form of an RFID information feature.
- a mailing ID uniquely identifies the mail piece, whereby the mailing ID can consist of the following parts: sender account number, date, tray ID, piece ID in mailtray, e-mail address of the sender, shipment value, shipment category and mail carrier.
- an error-correcting code CRC
- MAC message authentication code
- Integrity checks are designed to prevent mail items from being mailed to a wrong mail tray or from incorrect mailing to a wrong pallet, etc. due to technical errors (error-correcting code) or fraudulent manipulation (digital signature or message authentication code). Therefore, an RFID tag must be affixed to the individual mailpieces, but it is difficult for the large number of senders to ensure that the same conditions prevail for all. This is hardly possible if the sender attaches the RFID tag to the mail piece. A wrong adhesive can cause an RFID tag to peel off. For the sender, it is not readily possible to read information from the RFID tag. To store this information in the RFID tag, the sender would require the use of special equipment.
- the mail carrier sends back to the sender a list of shipment IDs, which he prints on his mail.
- the sender then delivers his mail to the mail carrier.
- the posting list is already available to the mail carrier at this time.
- the ShipmentID by itself does not designate a sender, but is merely an index in a posting list. A meaning receives this consignment ID only in connection with the posting list.
- the ShipmentID is not a unique identifier that can be used on all the mailpieces of a postage meter and can identify the sender.
- a method for mail processing and mail processing system is known, with staggered mail processing.
- a Identification of the sender takes place by means of a chip card, which the customer of the private mail carrier carries with him and inserts in a card reader of the mailing station (mailbox) when the customer gives up the mail. It is envisaged that the customer will receive a receipt on the post inserted in a mailbox and initially delivered to a first carrier / location.
- the chip card serves as a customer card, which already has an identification number.
- Each mail item is provided with a machine-readable mark consisting of a number specific to each mail item and further shipping data.
- the first carrier transports the mail from the post office (mailbox) to the first location and franks the letter with a franking stamp and makes a debit from the customer account at a customer bank and delivers the franked letter at a postal distribution center of a second carrier, which carries the post ,
- a conventional franking is carried out and a conventional posting list is generated.
- the due postage amount will be determined and charged while the mail is being delivered.
- the corresponding markings are applied to the postal items.
- the mark may include the date and time of delivery and also an identification of the customer, which has been previously read from the customer card in the loading station. This procedure can be referred to as "semi-central postage collection". Security checks in addition to the consignment ID and sender ID were not disclosed.
- the invention has for its object to avoid the disadvantages and to provide and build a franking and mailing system with central Porto collection, which is still guaranteed by means of simpler and user-friendly franking devices, the security of the system.
- the franking device is to apply a tamper-proof device identifier on the mail piece.
- this object is achieved by a method having the features of claim 1 and a mailing system having the features of claim 17.
- each franking device uses an individual device identifier which is stamped on all of its franking imprints.
- the mail carrier associates the device identifier with an electronic device account, to which he later assigns all postage for postal items bearing the corresponding device identifier.
- Billing with the customer can be carried out in a time-decoupled manner from the booking.
- the sender's bank account is debited with the accrued costs of an electronic device account, preferably at the end of each accounting period.
- the central postage collection enables franking solutions at the sender, which can work safely offline and without a security module.
- the mail items must carry a counterfeit-proof identifier of the sender or of his franking device, so that the postage costs can be correctly assigned to the originating senders.
- This is achieved by means of a symmetrical encryption of parameters and with a key that alters with each franking imprint and which can be kept synchonous in the carrier data center, without requiring any communication between the franking device and the carrier data center for each franking. Rather, an initial initialization of the franking device is sufficient.
- a secret first franking picture key is transmitted in encrypted form from the franking device via the operator data center to the mail carrier data center.
- the latter can be encrypted in the franking device by means of a private communication key and decrypted in the operator data center by means of a public communication key.
- the secret first franking key can be further transmitted encrypted to the mail carrier data center.
- the latter thus has a currently valid first franking image verification key, which is stored assigned to the sender or his device identifier.
- a marking on a mail piece or a franking picture has at least one device identifier of the franking device, a key generation number and an integrity check code.
- the latter allows a check of the integrity of such parameters as device identifier and key generation number because the latter are encrypted by means of the currently valid first franking image key to the integrity check code.
- the device identifier of the franking device, the key generation number and the first franking picture key are transmitted to the data center of the mail carrier.
- a currently valid second franking image key is generated in the franking device from the first or previously valid franking image key, which corresponds to a currently valid second franking image verification key, but which is generated on the mail carrier side.
- the local key generation number in a franking device and its local copy on the side of the mail carrier are kept synchronized in order to be able to derive the currently valid franking image verification key from a previously valid franking image verification key.
- Each device ID is uniquely associated with a customer account that has spent postage at the end of each pay period Be billed.
- the key generation number is changed in the franking device, whereby a stepwise change of the key generation number takes place by a predetermined numerical value. For example, the key generation number is incremented by one.
- a next valid cryptographic key is derived from the currently valid cryptographic key according to a first algorithm.
- the franking device is equipped with electronics for securely managing a postal identity and is called Postal Identity Management Device (PIMD) for better differentiation from the ordinary franking machines.
- PIMD Postal Identity Management Device
- a remote scan can be sent there and evaluation of franking images to be checked, which have been applied by the franking device to the mailpieces.
- An integrity check code is generated according to a second crypto-algorithm by means of the secret cryptographic franking key of the sender of the sender, the device identifier of the franking device and the current key generation number, whereby the franking image, at least the device identifier of the franking device, the current key generation number and the integrity check code can be scanned contains.
- deriving a franking image verification key that corresponds to the next secret franking image key from the first franking image key and from the current key generation number that can be scanned in the franking image by each further mail piece can be carried out according to a first crypto algorithm, if a new franking image key from a predecessor is used for each franking image of the franking picture key was derived according to the same first crypto-algorithm. It is envisaged that an evaluation of the scanned data by means of a test procedure in the data center of the mail carrier comprises a determination of the mathematical relationship of the sampled key generation number to the copy of the last used key generation number.
- the value of the change from the copy of the most recently used key generation number results from the product of each increment with the number of changes.
- stepwise changing the key generation number by a predetermined number in preparation of a subsequent franking picture key results from the number of changes.
- a franking image verification key is calculated according to the first crypto algorithm, the first crypto algorithm being applied as many times as dictated by the mathematical relationship.
- the mail piece is subject to sorting and the scanned data to error handling if stepping the key generation number by a predetermined number does not produce the expected result, ie, the mathematical relationship of the given mathematical relationship does not match. This is the case, for example, if the established mathematical relationship does not result from the number of changes.
- a comparison integrity check code may be computed in the data center to obtain the Cryptographically verify the scanned integrity check code.
- a central postage is charged at the data center of the mail carrier, if the authenticity of the integrity check code has been verified.
- a mailing system with central postage collection includes a mail center mail center and data center, an operator data center, and a plurality of postage meters. The mail carrier transports the postal items franked by the franking machine in the usual way to the letter center.
- Each franking device is in contact with the operator data center via a communication connection via the network and via a communication connection as required, which registers the device identifier of its users and offers additional services.
- Each franking machine can print franking imprints on letters and / or labels for mail pieces, which are subsequently delivered to the mail center for further mailing, which is communicatively connected to the data center of the mail carrier.
- the data center of the letter center is connected via a communication link to the network and can also communicate with the operator data center, as conversely the operator data center with the letter center data center.
- information from the postage meter may be routed via the operator data center to the data center of the mail carrier, even though the postage meter will not enter into direct communication with the data center of the mail carrier. Due to the aforementioned information, the data center of the mail carrier for the evaluation of information of the franking image in a position, in particular for reading and assigning the Device identifier to a sender and to postage fees for postal items of the same sender to a separate account or error handling. It is provided that the franking device contains a key generation means which generates a new franking picture key for each next franking picture.
- communication means are provided in order to establish synchronicity between the franking device and the data center as required via the communication connection.
- the data center evaluation means include second means for security checking each scanned franking image which, when it is possible to establish synchronicity between the scanned key generation number and its calculated copy and between the secret cryptographic key and the calculated indicia key, displays a compare integrity check code in Data Center calculates to cryptographically verify the scanned integrity check code.
- a means for booking the postage for postal items of the same sender on a separate account and a means for error handling is provided in the data center of the mail carrier, wherein the central postage collection is performed when the authenticity of the integrity check code has been proven.
- the second means for security checking are programmed so that a determination of the mathematical relationship of the sampled key generation number to the copy of the last used key generation number takes place, wherein a franking image verification key corresponding to the current subsequent franking image key of the franking device the first generated according to the determined mathematical relationship z times, and the franking image verification key together with the copy of the currently used key generation number and the device identifier to form a comparison integrity check code after the second crypto Algorithm is used.
- a franking system with different variants of communication links between an operator data center and franking devices is shown.
- Small mobile franking devices 10, 10 ', 10 ", 10 * can generate franking imprints with their printer module into which a device identifier is forged counterfeit-proof
- Such postage meters are also referred to below as a Postal Identity Management Device (PIMD)
- PIMD Postal Identity Management Device
- Each PIMD is connected via a communication link 11 , 11 ', 11 ", 11 * via network 18 and a communication link 19 in contact with the operator data center 14. There, it registers the device identifier for its users and receives additional services offered.
- Each PIMD may print franking imprints 9.3 on letters 9 and / or labels for mail pieces that are subsequently delivered to a mail center data center 7 for further mailing.
- the letter center 7 is connected via a communication link 8 to the network 18 and can also communicate with the operator data center 14, as conversely the operator data center 14 with the mail center data center 7.
- the communication links 8 and 19 allow, for example, a communication via Internet or telephone network ,
- This code M is calculated using an algorithm for a message authentication code (MAC) over the above-mentioned data ( Henk CA van Tilborg: Encyclopedia of Cryptography and Security; Springer-Verlag New York, 2005, pages 361-367 ).
- MAC message authentication code
- HMAC hash based message authentication code
- a secret cryptographic key of the sender is used according to the following formula (1): M ⁇ HMAC IDAKey ⁇ . . f G ⁇ i IDAKey i ,
- f is a function with the parameters g , i and IDAKeyi.
- the function f returns the string g
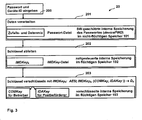
- a franking device During the initialization of a franking device, its key generation number is set to one and an initial cryptographic (first) key IDAKey 1 is generated.
- the key generation numbers and cryptographic keys received by the mail carrier and subsequently managed are denoted by j and IDAKey j , respectively.
- the aim is to synchronize the local generation number i in a postage meter and its local copy j on the mail carrier side. How this goal is achieved will be explained in more detail by examining franking imprints and troubleshooting in the following steps.
- the key generation number i in the PIMD is increased by one and a new cryptographic key IDAKey i + 1 is derived from the current key IDAKey i according to formula (3): IDAKey i + 1 ⁇ hash j ⁇ IDAKey i
- hash value after a hash function is also among other things Henk CA van Tilborg: Encyclopedia of Cryptography and Security; Springer-Verlag New York, 2005, pages 256-264 out.
- the key generation number i and the cryptographic key IDAKey i are used. This ensures that each cryptographic key is used for at most one franking.
- the franked shipments are delivered as known to the desired mail carrier.
- the mail carrier sorts the mailpieces, automatically reads the franking imprints including the contained barcodes, then transports the mailpieces to the destination address and delivers them there.
- the present invention assumes that Before sorting, all mail items are read and their barcodes can be recognized to approximately 100% and decoded correctly.
- the plain text information is evaluated and used to determine the postage value.
- the postage value can be easily read.
- the printed postage value can be checked on a random basis.
- the postage value is not printed and read, but determined directly from the physical parameters (length, width, thickness, weight, additional services) of the mailing in the letter center.
- the mail carrier prints on the mailpiece the last stored key generation number of the relevant franking device and sends it back to the operator of the recognized franking device.
- the latter should also be notified electronically via the return and the current key generation number known at the data center (e-mail, SMS) so that in the meantime he does not frank further mailpieces with incorrect key generation numbers.
- test fails by means of the third test step (III), then there is a fatal error, because since the key generation number i of the generating PIMD and its copy j in the checking letter center match, ie check (II) was successful, the cryptographic keys would also have to match. In this case, reinitialize and register the PIMD.
- a new initialization can preferably take place in that the data center 7 of the mail carrier generates a new franking picture key IDAKey * j and determines a difference value ⁇ according to the following formula (8): ⁇ ⁇ IDAKey 1 XOR IDAKey * ⁇
- the difference ⁇ is then printed on the return shipment, which is sent back to the sender of the item.
- the difference value ⁇ is additionally transmitted by electronic means to the data center 14 of the operator of the recognized franking device. Since the first franking picture key is known to the operator data center and is logically linked to the new franking picture key via the exclusive-or-function, the new franking picture key IDAKey * j can be determined. The new franking picture key can now be sent or transmitted to the relevant PIMD by way of secure communication. The steps required in PIMD initialization may be modified to apply to the PIMD adopting the new franking image key.
- the Fig. 1b shows a schematic representation of a printed letter top with a first field for the sender address or advertising, with a second field 9.2 for a mark in the recipient address field and a third field 9.3 for the franking.
- the aforementioned marking and / or franking contains a tamper-proof device identifier.
- the device identifier / franking imprints are encoded coded in 2D barcodes. Due to the small amount of data, the device identifier can also be printed as a 1D barcode.
- GS1-128 UCC / EAN-128
- USPS OneCode are suitable here. These barcodes are reliably readable at high speed and at the same time allow the reader to automatically correct a certain error rate. They are already being read in many mail letter centers and do not require any further investment in scanner technology.
- OCR fonts could be used to print and read the device identifiers.
- a postal market of up to 17 million senders therefore requires 7 bytes, a market up to 4 billion senders 8 bytes, and a market up to 1.09 billion senders 9-byte device identifiers. A total of approx.
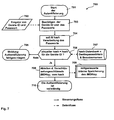
- the Fig. 1c shows a schematic representation of the processes at the letter carrier.
- a marking and / or franking has been generated in a first step 1, which comprises generating a tamper-proof device identifier
- the item of mail is transported.
- a white arrow indicates the transport direction.
- a first evaluation means are provided communicatively connected to one another in step 301, a decoding and error correction of the information after scanning, in step 302, a determination of the respective sender and in step 303 a determination to carry the postage.
- the first evaluation means comprises a database, which is coupled to a server.
- steps 302 and 303 may be reversed, or the two steps may be concurrently performed.
- each scanned franking image is provided, preferably a server that is secured against misuse.
- a query is made for a verification of the franking device identifier g . If verification is possible after passing through steps 301 to 304, then in step 306, the postage fee is booked in the context of the central postage collection to the account of the sender determined in step 302. If, however, verification is not possible after passing through steps 301 to 304, then this is determined in query step 305 and branched to an error handling step 307.
- the testing of frankings and the three test steps have already been explained above.
- a turn signal is generated in order to prevent the further transport of the mail piece in the fourth step 4 and instead to cause a sorting out of the mailpiece.
- the mailpiece is transported to the recipient when the addressee (recipient) of the mailpiece has been notified and has agreed to delivery.
- the item of mail can be returned to the sender if the sender of the item has been notified and has agreed to a return. Otherwise, an undeliverable mail piece will be destroyed.
- As part of the delivery to the addressee (recipient) of the mail piece is also a posting, but on the recipient name.
- As part of the error handling further investigation and also a registration undeliverable mail pieces can be made.
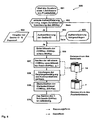
- FIG. 2 A block diagram 100 of a franking bank (PIMD's) is in the FIG. 2 shown.
- the franking device has a keyboard 112, a display unit 114 (LCD) and a printer module 116 (printer), which are provided with a keyboard each associated control electronics (keyboard controller 111, display controller 113, printer driver 115) are connected. It also has a processor 104 (CPU), a memory management unit 117 (MMU), as well as volatile and nonvolatile memories (volatile memory 102, 107 and nonvolatile memory 101, 103) and a serial input / output communication interface 109 Data exchange with an operator data center.
- the communication interface can be wired (eg USB, LAN, etc.) or wireless (eg WLAN, GSM, Bluetooth).
- Timed driver 108 accessing a volatile memory 102 and a cryptographically encrypting driver 106 accessing a non-volatile memory 103.
- Timed driver 108 writes data to volatile memory 102 (RAM, SD-RAM) and clears that data as soon as that data has not been accessed for a time-out set in the operating program. The deletion is done by automatically overwriting the data with bytes randomly generated by the driver. If you then try to read the data, the driver outputs only the previously random data.
- the cryptographically encrypting driver 106 writes data in encrypted form to the non-volatile memory 103 (e.g., Flash) using a hard-coded symmetric block cipher key. If this data is then read out again, the driver first decrypts the data with the same hard-coded key.
- the non-volatile memory 103 e.g., Flash
- the program code for controlling the franking device is preferably in the program memory 105 (NV memory), for example in a flash memory, but may alternatively be in an EPROM block.
- NV memory program memory
- EPROM EPROM block
- Communication within the meter passes over an internal bus 110 and is controlled by the memory management unit 117 (MMU) when saving data.
- MMU memory management unit 117
- the volatile memory 107 is provided as a working memory.
- the communication interface 109 may be connected to an operator data center via an internal or external modem (not shown) for data exchange or other suitable communication device.
- the communication links, the communication network and the communication devices at the ends of the communication links form the communication means in a known manner.
- the aforementioned means 103 to 107 form a key generation means which generates a new franking picture key for each next franking picture by calculating. This is based on the immediately preceding franking key.
- the latter and a communication key are both stored in the nonvolatile memory 103.
- the calculation is performed using a first and second crypto algorithm before franking, wherein for a first franking image, a first integrity check code is generated based on the second crypto algorithm, wherein for each subsequent franking image a subsequent franking image key from a predecessor of the franking image key derived according to the first crypto-algorithm and an integrity check code is generated, based on the subsequent franking image key, a key generation number, a device identifier of the franking device and based on the second crypto-algorithm.
- a PIMD 10 may communicate securely with its operator data center 14, typically using a bi-directionally authenticated and optionally encrypted communication protocol. Common methods are based on a key agreement protocol (Henk CA van Tilborg: Encyclopedia of Cryptography and Security; Springer-Verlag New York, 2005, page 325) or key establishment.
- a first routine 201 is processed to process the data to form a password by a random and data mix (salt & hash) and in a file in the nonvolatile memory 101 Software protected to save internally.
- the first routine 201 thus leads to a password storage on a lower level of the memory protection.
- a second routine 202 for deriving an internal encryption key IMDKey and timestamping it in an IMDKey file in volatile memory 102.
- the second routine 202 thus results in volatile storage at a middle level of memory protection.
- a third routine 203 follows for encrypting keys COMKey and IDAKey by means of the internal encryption key IMDKey and an encrypted internal volatile storage of data in the volatile memory 103, the data containing the encrypted keys.
- the third routine 203 thus results in volatile storage at an upper level of memory protection.
- the PIMD preferably uses two keys or key pairs to secure its interactions with neighbor systems.
- a communication key COMKey is used for the electronic communication with the operator data center . This can be a symmetric key. Alternatively, an asymmetric key pair can be used. In the case of an asymmetric key pair , we call the private communication key COMPrivKey and the public communication key COMPubKey.
- a secret franking key IDAKey is used to form the integrity check code M , the latter being used in the mailing data center Franking is printed on the mailpiece.
- This is preferably a symmetric key.
- Both keys COMKey and IDAKey or COMPrivKey and IDAKey are stored in an encrypted internal memory area, for example in the volatile memory 103 of the Postal Identity Management Device (PIMD) and are decrypted only when required. After use, the plaintext copies of both keys are deleted immediately and the corresponding memory areas are overwritten with random bit patterns, so that the plain keys can not be read out by unauthorized persons.
- PIMD Postal Identity Management Device
- an internal encryption key IMDKey is used for a symmetric block cipher, for example Advanced Encryption Standard (AES).
- AES Advanced Encryption Standard
- This internal encryption key IMDKey is not permanently stored in plain text, but is derived from the password algorithmically if necessary. Plain-text copies of the internal encryption key IMDKey are temporarily held in volatile memory 102 (time-controlled internal storage) and deleted there once their time-out has expired without being used.
- a random bit string (salt) is generated ( Henk CA van Tilborg: Encyclopedia of Cryptography and Security; Springer-Verlag New York, 2005, page 541 ).
- the random bit string is appended to the user-selected password.
- the result is mapped to a hash value (eg SHA256) by a hash function (ibid, hash function, page 256-264) and from this the franking image key IDAKey is derived by either using the hash value directly or by hashing it.
- the salt and hash value for a password are then stored in the password file indexed by passwords (soft protected internal memory).
- passwords soft protected internal memory
- software obfuscation techniques are used which, for example, store a data set in several parts which are located in the memory 101 at different addresses.
- the Fig. 4 shows as routine 400 a flowchart for initializing a PIMD.
- a query for new passwords takes place in step 403.
- the new passwords are those that have been entered twice.
- a double entry of the passwords must be made.
- this is not intended to preclude repeated entry of identical passwords, nor a single entry of a password, wherein the franking device can recognize in another way that a routine 400 for initializing a PIMD should run.
- an input is made to the type of routine that is about to expire and a password input in a second input, or vice versa.
- the password input are possible than by hand, provided that the franking device has a correspondingly adapted interface.
- the password input via Chip card, which requires that the franking device has a read / write unit for smart cards. Also, therefore, no double entry of the passwords must be made if it can be determined in another way whether it is intended to replace a previous one with a new current password.
- the password is processed by a process known per se (salt & hash process), already mentioned above in connection with Figure 3 was pointed out.
- step 405 the new password is stored in a password key file in non-volatile memory 101.
- step 406 a new encryption key IMDKey k is derived from the new hash value formed in step 404.
- the new encryption key IMDKey k is internally stored in the volatile memory 102 in a timed manner in step 407.
- step 408 following step 406, a new communication key COMKey and franking image key IDAKey 1 can now be generated. These two keys are encrypted in the following step 409 in the crypto driver 106 to data D k 1 , which are then stored internally volatile in the following step 410.
- the franking image key IDAKey 1 is a first key which is used to form an integrity check code M.
- the COMKey is a communication key for electronic communication with the operator data center .
- Encryption of the two slots COMKey and IDAKey 1 is performed in step 409 by using the new encryption key IMDKey k when encrypting according to one of the known encryption algorithms, for example according to the Avanced Encryption Standard (AES) algorithm according to formula (9): AES IMDKey k COMKey ⁇ IDAKey 1 ⁇ D k ⁇ 1
- AES Avanced Encryption Standard
- step 411 After the internal storage of the data D k1 of the encrypted key COMKey and IDAKey 1 in step 410, the sub-process in step 411 follows Fig. 8 performed and the first franking key IDAKey 1 sent. During the initialization of the franking device, in addition to the first franking picture key IDAKey 1 , the device identifier g of the franking device and the key generation number i are also transmitted to the data center of the mail carrier. In subsequent step 412, the initialization of the PIMD is complete.
- the operation of initializing a PIMD is one of the main processes and ends with the transmission of the generated first franking picture key IDAKey 1 to the mail carrier via a secure communication protocol.
- the mail carrier then registers the new franking device with its device identifier g, its first key generation number i and the associated franking image key IDAKey i , which are used to form an integrity check code M.
- the first key generation number i preferably has the value 'one'.
- Routine 500 of the PIMD causes the password to be changed, that is, to update the password of the PIMD.
- a verification of the authenticity of the device ID takes place in the third step 503. If the authentication of the device ID has failed, then a fourth step 504 is branched and the routine 500 ends. Otherwise, if the authenticity check of the device ID was successful, a branch is made to a sixth step 506 to query for new passwords.
- a query for the newly entered password can be made in the sixth step 506.
- a new password can be entered twice and in the sixth step 506 is asked for such a double entry of a new password.
- the postage meter may optionally recognize in another manner that a password-switching routine 500 is to occur.
- other variants of the password input are possible than by hand, which requires that the franking device has a correspondingly adapted interface.
- the new password is stored in a password and key file in an eighth step 508 and proceeded to the ninth step 509, to retrieve internally stored data D k , the data being encrypted Keys included.
- the encrypted internal storage of the keys in the volatile memory 103 was carried out in the form of data D k already before the routine 500 in step 410 (FIG. Figure 4 ) or 203 ( Fig. 3 ).
- the extracted data D k are decrypted by means of the active internal key IMDKey k to the two keys required in plain text. These are the secret franking image key IDAKey k and the secret communication key COMKey or private communication key COMPubKey.
- a new internal encryption key IMDKey k + 1 is derived from the new hash value hash k + 1 , which was determined in the seventh step 507.
- the required keys are re-encrypted by means of the new IMDKey k + 1 , whereby the required keys result from the decryption in the ninth step 509.
- the re-encryption takes place again, for example, according to the Advanced Encryption Standard (AES) algorithm according to the formula (10) to the new encrypted data D k +1 : AES ⁇ IMDKey k + 1 COMKey k ⁇ IDAKey k ⁇ D k + 1
- a twelfth step 512 following the eleventh step 511 an internal volatile storage of the new encrypted data D k +1 again takes place in the volatile memory 103.
- a timed internal volatile memory of the new one also takes place in a thirteenth step 513 internal encryption key IMDKey k + 1 in the volatile memory 102. Changing the password is complete in the fourteenth step 514.
- the Fig. 6 shows as routine 600 a flowchart for calculating a franking imprint.
- the routine 600 for calculating a franking imprint belongs to the main processes. After the start of a processing of the data of a franking imprint in the first step 601, a query is made in the second step 602 as to whether a renewed authentication of the device ID is necessary because the timing of the storage of the IMDKey has taken place. If this is the case, then - in a manner not shown - a message, for example via the display, which prompts the user of the franking device to enter the device ID and the password.
- a sub-process of operating a PIMD for authentication of the device ID expires. If authentication of the device ID is not possible, then a step 605 is reached and a message is displayed indicating that the authentication failed. Otherwise, if the query in the second step 602 reveals that device ID re-authentication is unnecessary, or if the device ID authentication was successful in the fourth step 604, then a sixth step 606 is branched. In the sixth step 606, the data D i encrypted internally in the volatile memory 103 are decrypted by means of the active IMDKey i to form the plaintext keys .
- an integrity check code M is formed according to the aforementioned formula (1) or (2).
- processing of the franking data and image data together with the integrity check code M takes place in order to generate a unique franking imprint as a result of the routine 600.
- the key generation number i for the current one Franking next following the franking increased by the value of one.
- a next encryption key IMDKey i is derived , an encryption of the keys IDAKey i and COMKey i by means of the active IMDKey i and an encrypted internal storage of the keys IDAKey i and COMKey i .
- the clear keys and the encryption key are overwritten in the volatile memories 102 and 103.
- a message about the integrity of the check code can be output.
- the routine 600 for calculating a franking imprint is completed.
- the Fig. 7 As a first sub-routine 700, a flowchart for authenticating a device ID is shown.
- the sub-routine 700 is one of the sub-processes of operating a PIMD following in both main processes Fig. 5 and 6 as well as in the sub-process Fig. 8 is needed.
- the operation of the PIMD initiated by passing through the subroutine is started in the first step 701 and leads to the device ID authentication.
- the second step 702 of the first subroutine 700 an input of the device ID and the password is made, and then, if the input is confirmed in the third step 703, a fourth step 704 of the first subroutine 700 is reached, to perform a salt & hash processing of the password.
- a query is made as to whether a current hash value is equal to a hash value for the device ID.
- a hash database with a list of device passwords and user names is accessed to locate the hash value for the device ID. If the query does not result in equality in the sixth step 706, then a branch is made to a fifth step 705 and a message is output that the authentication has failed. Otherwise, a branch is made to an eighth step 708 for deriving an encryption key from the current hash value.
- the encryption key is stored internally in a timed manner until the Timing the storage of IMDKeys occurs (step 709). Thus, the tenth step 710 of the first sub-routine 700 is reached and the authentication is complete.
- the Fig. 8 As a second sub-routine 800, a flowchart when sending a postage meter key of the PIMD to the data center of the mail carrier is shown.
- the sending of franking picture keys IDAKey belongs to the sub-processes of operating a PIMD.
- the operation of transmitting an IDAKey of a PIMD is shown in more detail. This second subroutine is needed when a PIMD sends its IDAKey to the mail carrier at the end of its initialization.
- the sub-process of sending the key of a franking imprint is started in the first step 801 and reaches a second step 802 in order to query whether re-authentication is necessary due to the time-out of storage of the IDAKey . If so, then step 804 of the second subroutine may be branched. Assuming that an input (step 803) of the device ID and the password is made, the first sub-routine 700, ie, a sub-process, may - as shown Fig. 7 Expire for device ID authentication. Otherwise, a branch is made to the sixth step 806 of the second sub-routine 800 if no re-authentication is necessary because of the time-out of storage of the internal encryption key IMDKey .
- a renewed device ID authentication is thus bypassed, and in the sixth step 806 of the second subroutine 800, the data D is decrypted by means of the internal encryption key IMDKey to the clear keys COMKey and IDAKey 1 .
- the first franking picture key IDAKey 1 is encrypted and further parameters, such as at least the device identifier g of the franking device and the key generation number, are encrypted i , by means of the communication key COMKey according to the formula (11): AES COMKey .
- the data D1 is transmitted to the data center of the mail carrier and received and decrypted there.
- the receipt of the franking image key IDAKey 1 and further parameters g and i is confirmed.
- receipt of the acknowledgment of receipt of the communication partner takes place.
- the plain keys COMKey and IDAKey 1 are overwritten with random data.
- the sub-process of sending the first franking picture key IDAKey 1 in the tenth step 810 of the second sub-routine 800 is completed.
- the first franking picture key IDAKey 1 indirectly enters the data center 7 of the mail carrier via the data center 14 of the operator or manufacturer of the franking device.
- the data center 7 of the mail carrier is the direct communication partner.
- step 606 after the formation of a check code M in step 606 and after its processing in step 608, the next franking image key is derived in step 610.
- the sequence can also be reversed by first deriving the next franking image key and then a Forming a check code M and its processing is made.
- a corresponding order In the sequence of steps in a review of the franking data in the data center of course, a corresponding order must be selected so that after scanning the franking image or a marking of the mail piece in the generation of new franking picture keys again synchronicity is achieved.
- the aforementioned password change routine 500 the query for a new password according to other criteria, as was shown in the embodiment.
- the entry of the new password itself can be done in other ways, as was shown in the embodiment.
- the aforementioned routines can be adapted to the different postal regulations for the various countries and used analogously.
Claims (21)
- Procédé d'affranchissement avec relevé centralisé du montant d'affranchissement dans le centre de données d'un transporteur postal, avec génération d'un premier code d'impression d'affranchissement (IDAKey1 ) pendant une initialisation de l'affranchisseuse, avec création d'une impression d'affranchissement à l'aide de l'affranchisseuse, et avec un dispositif d'évaluation de l'impression d'affranchissement éloigné de l'affranchisseuse, comportant les étapes- que le premier code d'impression d'affranchissement (IDAKey1 ) soit transmis de l'affranchisseuse au dispositif éloigné d'évaluation destiné au contrôle d'impressions d'affranchissement sur des articles postaux,- qu'à chaque code d'impression d'affranchissement (IDAKey1 ) soit attribué un numéro de génération de code (i), qui sera modifié d'une valeur numérique définie constante (h) en passant d'un code d'impression d'affranchissement au suivant,- que la déduction d'un prochain code d'impression d'affranchissement (IDAKeyi+h ) du code d'impression d'affranchissement précédent (IDAKeyi ) soit généré selon un premier algorithme cryptographique,- qu'un nouveau code d'impression d'affranchissement soit déduit pour chaque impression d'affranchissement,- que soit créé un code de contrôle d'intégrité (M) basé sur le nouveau code d'impression d'affranchissement (IDAKeyi ), le numéro de génération de code (i) qui lui est affecté, l'identification d'appareil (g) de l'affranchisseuse et sur un second algorithme cryptographique,- que l'impression d'affranchissement contienne de manière scannable au moins l'identification d'appareil (g) de l'affranchisseuse, le numéro de génération de code (i) et le code de contrôle d'intégrité (M),- que pour l'affranchissement les impressions d'affranchissement soient imprimées sur les articles postaux,- que les articles postaux soient transportés et livrés dans un centre de tri de courrier du transporteur postal,- que les impressions d'affranchissement soient scannées et contrôlées chez le transporteur postal dans une opération durant laquelle le code de contrôle d'intégrité (M) est vérifié cryptographiquement, en formant un code de contrôle d'intégrité comparatif (Mref) pour la comparaison avec le code de contrôle d'intégrité (M) imprimé et que- les frais soient enregistrés pour la comptabilisation centrale, lesdits frais étant facturés à l'expéditeur des articles postaux à la fin de la période de décompte de manière découplée temporellement de la comptabilisation.
- Procédé selon la revendication 1, caractérisé par les étapes suivantes :- transmission de données d'au moins une identification d'appareil (g) de l'affranchisseuse, d'un premier numéro de génération de code i= 1 et du premier code (IDAKey1 ) à un centre de données éloigné chez le transporteur postal avant la fin de l'initialisation (400) de l'affranchisseuse, et enregistrement interne crypté du premier code d'impression d'affranchissement (IDAKey1 ) généré dans la mémoire volatile de l'affranchisseuse,ou
génération d'un code d'impression d'affranchissement (IDAKeyi ) déduit selon le premier algorithme cryptographique et enregistrement interne crypté du code d'impression d'affranchissement (IDAKeyi ) déduit,- identification d'un ordre d'affranchissement par l'affranchisseuse pour un article postal devant être imprimé et démarrage du calcul d'une impression d'affranchissement avec génération d'un code de contrôle d'intégrité (M) selon le deuxième algorithme cryptographique, et dont la génération s'effectue selon l'identification d'appareil (g) de l'affranchisseuse, du numéro de génération de code (i) et du premier code d'impression d'affranchissement (IDAKey1 ) ou d'un code d'impression d'affranchissement déduit (IDAKeyi ), et dont le premier code d'impression d'affranchissement (IDAKey1 ) sauvegardé en interne de manière cryptée ou le code d'impression d'affranchissement (IDAKeyi ) déduit est décrypté en code d'impression d'affranchissement (IDAKey 1, IDAKeyi)présenté en texte clair, à l'aide d'une clé cryptographique (IMDKey) interne,- traitement des données de l'impression d'affranchissement avec le code de contrôle d'intégrité (M),- impression de l'article postal avec une impression d'affranchissement qui contient au minimum le marquage de l'identification d'appareil (g) de l'affranchisseuse, du numéro de génération de code (i) et du code de contrôle d'intégrité (M),- modification pas à pas du numéro de génération de code (i) d'une valeur numérique (h) définie, déduction du prochain code d'impression d'affranchissement (IDAKeyi + h) à partir du numéro actuel de génération de code (i), cryptage au moins du prochain code d'impression d'affranchissement (IDAKeyi + h) et d'une clé de communication (COMKey) à l'aide de la clé cryptographique (IMDKey) interne et enregistrement interne crypté du prochain code d'impression d'affranchissement (IDAKeyi + h) et de la clé de communication (COMKey) ainsi que l'écrasement dans la mémoire volatile de l'affranchisseuse de la clé de communication (COMKey) présente en texte clair, du code d'impression d'affranchissement (IDAKeyi +h) et de son prédécesseur (IDAKeyi ),- transport au centre de tri de courrier par le transporteur postal des articles postaux affranchis par l'affranchisseuse,- livraison de l'article postal au centre de tri de courrier du transporteur postal et scannage de l'impression d'affranchissement et évaluation des données scannées à l'aide d'un procédé de vérification dans le centre de données du transporteur postal, durant lequel le code de contrôle d'intégrité (M) est vérifié cryptographiquement avec un code actuel correspondant au code d'impression d'affranchissement (IDAKeyi ),- relevé centralisé du montant d'affranchissement au centre de données du transporteur postal, si l'authenticité du code de contrôle d'intégrité (M) est prouvée, ou encore,- déroulement d'une routine de traitement d'erreur, si l'authenticité du code de contrôle d'intégrité (M) n'a pas pu être prouvée ou encore si une identification d'appareil (g) de l'affranchisseuse ou un numéro de génération de code (i) contient une erreur. - Procédé selon les revendications 1 et 2, caractérisé en ce que le numéro de génération de code (i) soit augmenté de la valeur 1 (h = 1) à chaque opération d'affranchissement.
- Procédé selon la revendication 3, caractérisé en ce que, pour un prochain numéro de génération de code (i+ 1), la déduction du prochain code d'impression d'affranchissement (IDAKeyi+1 ) s'opère, à partir du numéro actuel de génération de code (i) et du code actuel d'impression d'affranchissement (IDAKeyi), d'après le premier algorithme cryptographique et selon la formule suivante :
- Procédé selon les revendications 1 à 4, caractérisé en ce qu'un code d'authentification d'une empreinte cryptographique de message avec clé (HMAC - keyed-hash message authentication code), basé sur une fonction de hachage, soit utilisé comme premier algorithme cryptographique.
- Procédé selon les revendications 1 à 5, caractérisé en ce que la génération d'un code de contrôle d'intégrité (M) s'opère selon le deuxième algorithme cryptographique à l'aide d'un code d'impression d'affranchissement cryptographique secret (IDAKeyi ) de l'expéditeur, de l'identification d'appareil (g) de l'affranchisseuse et de son numéro actuel de génération de code (i), d'après la formule:
- Procédé selon les revendications 1 à 5, caractérisé en ce que la génération d'un code de contrôle d'intégrité (M) s'opère selon le deuxième algorithme cryptographique à l'aide d'un code d'impression d'affranchissement cryptographique secret IDAKeyi de l'expéditeur, de l'identification d'appareil (g) de l'affranchisseuse et de son numéro actuel de génération de code (i), d'après la formule:
- Procédé selon une des revendications 6 ou 7, caractérisé en ce qu'une évaluation des données scannées soit effectuée à l'aide d'un procédé de vérification dans le centre de données du transporteur postal et que ladite évaluation comporte une détermination de la relation mathématique du numéro de génération de code (i∓x) actuellement scanné par rapport à la copie (j) du numéro de génération de code (i) lu en dernier, et dont la valeur (x), de la modification de la copie (j) du numéro de génération de code (i) lu en dernier, résulte du produit de la valeur de pas (h) et du nombre (z) de modifications, et dont une clé de vérification d'impression d'affranchissement (IDAKeyJ ) actuelle est calculée, ladite clé correspondant au code d'impression d'affranchissement (IDAKeyj∓h ) scanné, si la relation mathématique est identique à une relation mathématique prédéfinie J = j + x with x = h z, et dont la copie (J) locale correspond au numéro de génération de code (i∓x) lu actuellement et dont l'article postal est soumis à un tri sélectif de rejet et les données scannées à un traitement d'erreur, si la relation mathématique ne correspond pas à la relation mathématique prédéfinie.
- Procédé selon la revendication 8, caractérisé en ce que l'article postal soit retourné à l'expéditeur, si la relation mathématique du numéro de génération de code (i∓x) ne correspond pas à la relation mathématique prédéfinie par rapport à la copie (j) du numéro de génération de code (i) lu en dernier et que l'expéditeur de l'article postal a été informé et a donné son accord pour un retour.
- Procédé selon la revendication 8, caractérisé en ce que l'article postal soit retourné à l'expéditeur, si la relation mathématique du numéro de génération de code (i∓x) actuellement scanné ne correspond pas à la relation mathématique prédéfinie par rapport à la copie (j) du numéro de génération de code (i) lu en dernier et que l'expéditeur de l'article postal a été informé et a donné son accord pour un retour.
- Procédé selon l'une des revendications 8 à 10, caractérisé en ce que le traitement suivant de données scannées chez le transporteur postal soit effectué par une routine (300) qui comporte, un décodage (301) des données scannées, une identification de l'expéditeur respectif (302), une détermination (303) du montant d'affranchissement respectif, une vérification de sécurité (304) de chaque impression d'affranchissement et une comptabilisation centrale (306) du montant d'affranchissement sur un compte de l'expéditeur, ainsi que soit effectué un transport (4) et une livraison (5) des articles postaux correctement affranchis aux destinataires ou que les articles postaux soient soumis à un tri sélectif de rejet au centre de tri de courrier, si le traitement continu des données scannées n'est pas possible dans la routine (300), et dont- l'identification de l'expéditeur respectif (302) comporte une recherche d'après l'identification d'appareil (g) de l'affranchisseuse dans une base de données du centre de tri de courrier ou du centre de données et d'après la copie (j) enregistrée correspondante du numéro de génération de code (i) lu en dernier, pour lequel il existe un code d'impression d'affranchissement correspondant enregistré,- la vérification de sécurité (304) de chaque impression d'affranchissement comporte une détermination de la relation mathématique du numéro de génération de code (i ∓x) par rapport à la copie (j) du numéro de génération de code (i) lu en dernier ainsi qu'une vérification cryptographique du code de contrôle d'intégrité (M), et dont une clé de vérification d'impression d'affranchissement (IDAKeyJ ) avec J = j + x, correspondante au code d'impression d'affranchissement (IDAKeyi±x ) actuel suivant de l'affranchisseuse, soit créé selon le premier algorithme cryptographique, et dont le premier algorithme cryptographique soit utilisé z fois en correspondance avec la détermination de la relation mathématique, ainsi que la clé de vérification d'impression d'affranchissement (IDAKeyJ ) générée soit utilisée ensemble avec la copie (J) du numéro de génération de code (i∓x) actuellement scanné et avec l'identification d'appareil (g) pour former le code de contrôle d'intégrité comparatif (Mref), d'après le deuxième algorithme cryptographique.
- Procédé selon la revendication 1, caractérisé en ce que la sécurité de l'identification d'appareil (g) soit assurée au minimum par la saisie d'un mot de passe.
- Procédé selon la revendication 12, caractérisé en ce que soit demandé la saisie du mot de passe existant et de l'identification d'appareil (g), et que leur authenticité soit vérifiée, avant le calcul d'une impression d'affranchissement, si une durée prédéfinie pour l'enregistrement de la clé cryptographique interne (IMDKey) est écoulée.
- Procédé selon la revendication 12, caractérisé en ce que le mot de passe existant puisse être modifié si nécessaire avant le calcul d'une impression d'affranchissement, et qu'avant ladite modification du mot de passe existant, la saisie du mot de passe existant et de l'identification d'appareil (g) soit demandée et que leur authenticité soit vérifiée.
- Procédé selon la revendication 12, caractérisé en ce que la sécurité de l'identification d'appareil soit assurée par une combinaison des mesures suivantes:a) Saisie du mot de passe à l'aide du clavier ou encore à l'aide d'un support d'identification utilisant la technologie RFID, d'une carte magnétique, d'une carte à puce ou d'un appareil portable relié à un réseau personnel faisant partie de l'environnement de l'affranchisseuse.b) Authentification de l'identification d'appareil sur chaque impression d'affranchissement dans l'environnement du transporteur postal, pour exclure toute utilisation d'identifications d'appareils erronées.c) Authentification unique de l'identification d'appareil sur chaque impression d'affranchissement dans l'environnement du transporteur postal, pour exclure toute ré-utilisation d'authentifications copiées d'identifications d'appareils erronées.d) Sécurisation par cryptage au minimum de la liaison de communication au centre de données de l'exploitant.e) Gestion de comptes séparés d'utilisateurs par un système d'exploitation connu d'un ordinateur personnel en rapport avec l'utilisation d'affranchisseuses utilisées par plusieurs opérateurs.
- Procédé selon la revendication 15, caractérisé en ce qu'un premier code d'impression d'affranchissement (IDAKey 1) généré soit transmis, via une liaison de communication sécurisée et pendant une initialisation de l'affranchisseuse, au centre de données d'un exploitant et ensuite au centre de données du transporteur postal.
- Système d'envoi d'articles postaux avec relevé centralisé du montant d'affranchissement dans le centre de données d'un transporteur postal, avec une affranchisseuse (10, 10', 10", 10*), qui peut créer des impressions d'affranchissement et qui comporte un moyen de génération de codes, et dont ledit moyen de génération de codes comporte un processeur (104), une mémoire de programme (105), un pilote codé cryptographiquement (106) et des mémoires (103, 107),- et dont le moyen de génération de codes génère, pendant une initialisation de l'affranchisseuse, un premier code d'impression d'affranchissement (IDAKey 1), qui est transmis par l'affranchisseuse au centre de données du transporteur postal pour une évaluation à distance d'impressions d'affranchissement à vérifier sur des articles postaux,- et dont chaque code d'impression d'affranchissement (IDAKeyi ) fait l'objet d'une affectation d'un numéro de génération de code (i), qui est modifié d'une valeur numérique définie constante (h) en passant d'un code d'impression d'affranchissement au suivant,- et dont la déduction d'un prochain code d'impression d'affranchissement (IDAKeyi + h) du code d'impression d'affranchissement précédent (IDAKeyi ) soit généré selon un premier algorithme cryptographique,- et dont un nouveau code d'impression d'affranchissement soit déduit pour chaque impression d'affranchissement,- et dont soit créé un code de contrôle d'intégrité (M) basé sur le nouveau code d'impression d'affranchissement (IDAKeyi ), sur le numéro de génération de code (i) qui lui est affecté, sur l'identification d'appareil (g) de l'affranchisseuse et sur un second algorithme cryptographique,- et dont l'impression d'affranchissement contienne de manière scannable au moins l'identification d'appareil (g) de l'affranchisseuse, le numéro de génération de code (i) et le code de contrôle d'intégrité (M),- et dont l'affranchisseuse est destinée à l'affranchissement, durant lequel les impressions d'affranchissement sont imprimées sur des articles postaux.- et dont un centre de tri de courrier du transporteur postal est prévu pour la livraison des articles postaux transportés,- et dont des moyens de scannage d'impressions d'affranchissement dans le centre de tri de courrier et des premiers moyens d'évaluation pour la vérification d'impressions d'affranchissement dans le centre de données du transporteur postal, reliés entre eux en matière de communication, sont prévus, et dont le code de contrôle d'intégrité (M) est vérifié cryptographiquement en utilisant un code de contrôle d'intégrité comparatif (Mref) pour la comparaison avec le code de contrôle d'intégrité (M) imprimé, ainsi- que soient prévus des moyens destinés à la comptabilisation des montants d'affranchissement pour des articles postaux d'un même expéditeur sur un compte séparé dans le centre de données du transporteur postal, et dont le relevé centralisé du montant d'affranchissement est ensuite effectué si l'authenticité du code de contrôle d'intégrité est établie et justifiée, et que les frais soient enregistrés pour la comptabilisation centrale, lesdits frais étant facturés à l'expéditeur des articles postaux à la fin de la période de décompte de manière découplée temporellement de la comptabilisation.
- Procédé d'envoi d'articles postaux selon la revendication 17, caractérisé en ce,- que le système comporte des moyens de communication prévus pour effectuer un transfert de données au minimum d'une identification d'appareil (g) de l'affranchisseuse, d'un premier numéro de génération de code (i=1) et du premier code (IDAKey1 ) à un centre de données du transporteur postal avant la fin de l'initialisation (400) de l'affranchisseuse, et dont ladite affranchisseuse est équipée d'une interface de communication (109) possédant une entrée/sortie de série pour l'échange de données avec un centre de données d'exploitant (14), et dont ladite affranchisseuse transmet le premier code d'impression d'affranchissement (IDAKey1 ) via le centre de données d'exploitant (14) pour l'évaluation à distance d'impressions d'affranchissement devant être vérifiées sur des articles postaux, au centre de données (7) du transporteur postal,- que la mémoire (103), le processeur (104), le pilote (106) et la mémoire (107) soient programmés pour la génération d'un nouveau code d'impression d'affranchissement et pour le calcul d'une impression d'affranchissement avant la création d'un affranchissement dans l'affranchisseuse par un code de programme enregistré dans la mémoire de programme (105) pour la commande de l'affranchisseuse, et dont le code d'impression d'affranchissement (IDAKeyi ) soit déduit d'un prédécesseur enregistré selon le premier algorithme cryptographique, et dont une sauvegarde interne du code d'impression d'affranchissement (IDAKeyi ) déduit soit effectuée sous forme cryptée, et dont un ordre d'affranchissement soit détecté par l'affranchisseuse pour un article postal devant être imprimé et que soit démarré le calcul d'une impression d'affranchissement avec création d'un code de contrôle d'intégrité (M) selon le second algorithme cryptographique, et dont la génération soit effectuée en fonction de l'identification d'appareil (g) de l'affranchisseuse, du numéro de génération de code (i) et du premier code d'impression d'affranchissement (IDAKey1 ) ou d'un code d'impression d'affranchissement (IDAKeyi ) déduit, et dont le premier code d'impression d'affranchissement (IDAKeyi ) enregistré de manière cryptée en interne ou le code d'impression d'affranchissement (IDAKeyi ) déduit soit décrypté en code d'impression d'affranchissement (IDAKey1 , IDAKeyi ) présent en texte clair, et dont les données d'impression d'affranchissement soient traitées avec le code de contrôle d'intégrité (M) et que l'article postal soit imprimé avec une impression d'affranchissement qui contient un marquage présentant au moins l'identification d'appareil (g) de l'affranchisseuse, le numéro de génération de code (i) et le code de contrôle d'intégrité (M), et dont le numéro de génération de code (i) soit modifié pas à pas d'une valeur numérique définie (h) et que le prochain code d'impression d'affranchissement (IDAKeyi + h) soit déduit du numéro actuel de génération de code (i), et dont au moins le prochain code d'impression d'affranchissement (IDAKeyi ) + h) et une clé de communication (COMKey) soient cryptés à l'aide de la clé cryptographique interne (IMDKey) et que soit effectuée une sauvegarde interne du prochain code d'impression d'affranchissement (IDAKeyi ) + h) et de la clé de communication (COMKey) ainsi que l'écrasement de la clé de communication (COMKey) présente en texte clair et du code d'impression d'affranchissement (IDAKeyi + h) et de son prédécesseur (IDAKeyi ), dans la mémoire volatile de l'affranchisseuse,- que soient prévus des moyens pour transporter les articles postaux affranchis par l'affranchisseuse et pour livrer l'article postal au centre de tri de courrier du transporteur postal.- que soient prévus des moyens pour le scannage de l'impression d'affranchissement au centre de tri de courrier et des moyens pour évaluer les données scannées à l'aide d'un procédé de vérification dans le centre de données du transporteur postal, durant lequel le code de contrôle d'intégrité (M) scanné est vérifié cryptographiquement avec un code actuel correspondant au code d'impression d'affranchissement (IDAKeyi ),- que soient prévus des moyens pour le relevé centralisé des montants d'affranchissement au centre de données du transporteur postal, ledit relevé centralisé du montant d'affranchissement étant réalisé si l'authenticité du code de contrôle d'intégrité (M) est prouvée,- que soient prévus des moyens pour le déroulement d'une routine de traitement d'erreur, ladite routine de traitement d'erreur entrant en action si l'authenticité du code de contrôle d'intégrité (M) n'a pas pu être prouvée ou encore si une identification d'appareil (g) de l'affranchisseuse ou un numéro de génération de code (i) contient une erreur.
- Système d'envoi d'articles postaux selon la revendication 17, caractérisé en ce que le traitement suivant de données scannées soit effectué dans le centre de tri de courrier du transporteur postal ou dans le centre de données du transporteur postal.
- Système d'envoi d'articles postaux selon la revendication 17, caractérisé en ce que le moyen de génération de codes de l'affranchisseuse soit programmé pour effectuer un calcul avant l'affranchissement en utilisant le premier et le second algorithme cryptographique, et dont un premier code de contrôle d'intégrité basé sur le second algorithme cryptographique soit généré pour une première impression d'affranchissement, et dont, pour chaque impression d'affranchissement suivante, soit déduit un code d'impression d'affranchissement suivant à partir d'un prédécesseur du code d'impression d'affranchissement selon le premier algorithme cryptographique et que soit créé un code de contrôle d'intégrité, basé sur le code d'impression d'affranchissement suivant, un numéro de génération de code, une identification d'appareil de l'affranchisseuse et sur le second algorithme cryptographique.
- Système d'envoi d'articles postaux selon les revendications 17 à 19, caractérisé en ce que soient prévues, une mémoire non volatile (101) pour la sauvegarde de mot de passe sur un niveau inférieur de la protection mémoire, une mémoire volatile (102) pour une sauvegarde temporelle de la clé cryptographique interne (IMDKey) dans un fichier IMDKey sur un niveau médian de la protection mémoire ainsi qu'une mémoire (103) pour une sauvegarde volatile interne cryptée de données sur un niveau supérieur de la protection mémoire, et dont les données de la mémoire (103) destinée à la sauvegarde interne volatile cryptée de données sur un niveau supérieur de la protection mémoire, contiennent le code d'impression d'affranchissement (IDAKey) et la clé de communication (COMKey) sous forme cryptée.
Applications Claiming Priority (1)
| Application Number | Priority Date | Filing Date | Title |
|---|---|---|---|
| DE102007052458A DE102007052458A1 (de) | 2007-11-02 | 2007-11-02 | Frankierverfahren und Postversandsystem mit zentraler Portoerhebung |
Publications (2)
| Publication Number | Publication Date |
|---|---|
| EP2058769A1 EP2058769A1 (fr) | 2009-05-13 |
| EP2058769B1 true EP2058769B1 (fr) | 2011-07-20 |
Family
ID=40420537
Family Applications (1)
| Application Number | Title | Priority Date | Filing Date |
|---|---|---|---|
| EP08017285A Not-in-force EP2058769B1 (fr) | 2007-11-02 | 2008-10-01 | Procédé d'affranchissement et système d'expédition de courrier avec augmentation de frais de port centrale |
Country Status (4)
| Country | Link |
|---|---|
| US (1) | US8046304B2 (fr) |
| EP (1) | EP2058769B1 (fr) |
| AT (1) | ATE517405T1 (fr) |
| DE (1) | DE102007052458A1 (fr) |
Families Citing this family (11)
| Publication number | Priority date | Publication date | Assignee | Title |
|---|---|---|---|---|
| US7818268B2 (en) * | 2001-10-16 | 2010-10-19 | Fitzsimmons Todd E | System and method for mail verification |
| ITMI20082364A1 (it) * | 2008-12-31 | 2010-07-01 | Incard Sa | Metodo per proteggere un dispositivo crittografico contro attacchi spa, dpa e temporali |
| FR2952459B1 (fr) * | 2009-11-10 | 2011-12-16 | Neopost Technologies | Procede de securisation des affranchissements au travers d'un reseau de telecommunication |
| WO2013177509A1 (fr) * | 2012-05-25 | 2013-11-28 | Pharmasecure, Inc. | Système et procédé permettant de générer et de gérer des codes d'authentification de produits |
| US9412131B2 (en) * | 2012-06-26 | 2016-08-09 | Francotyp-Postalia Gmbh | Method and arrangement for specifying services provided by a franking machine |
| US9536067B1 (en) * | 2014-01-01 | 2017-01-03 | Bryant Christopher Lee | Password submission without additional user input |
| US10339489B2 (en) | 2015-02-13 | 2019-07-02 | One Stop Mailing LLC | Parcel processing system and method |
| DE102017211421A1 (de) * | 2017-07-05 | 2019-01-10 | Bundesdruckerei Gmbh | Verfahren zur Validierung einer mit einer Vorfrankierung versehenen Postsache |
| JP2021514493A (ja) * | 2018-02-07 | 2021-06-10 | クリプト リンクス リミテッド | 署名方法、システム、及び/又はデバイス |
| DE102018128360A1 (de) * | 2018-11-13 | 2020-05-14 | Francotyp-Postalia Gmbh | Gutverarbeitungsgerät |
| CN112207045A (zh) * | 2020-09-08 | 2021-01-12 | 徐展拓 | 一种具有自动筛选功能的智能制造芯片检测装置 |
Family Cites Families (30)
| Publication number | Priority date | Publication date | Assignee | Title |
|---|---|---|---|---|
| US5375172A (en) | 1986-07-07 | 1994-12-20 | Chrosny; Wojciech M. | Postage payment system employing encryption techniques and accounting for postage payment at a time subsequent to the printing of postage |
| US4873645A (en) * | 1987-12-18 | 1989-10-10 | Pitney Bowes, Inc. | Secure postage dispensing system |
| DE3840041A1 (de) | 1988-11-26 | 1990-06-07 | Helmut Lembens | Anordnung zum frankieren von postgut |
| US6233568B1 (en) * | 1994-01-03 | 2001-05-15 | E-Stamp Corporation | System and method for automatically providing shipping/transportation fees |
| US5612889A (en) | 1994-10-04 | 1997-03-18 | Pitney Bowes Inc. | Mail processing system with unique mailpiece authorization assigned in advance of mailpieces entering carrier service mail processing stream |
| US5742682A (en) | 1995-03-31 | 1998-04-21 | Pitney Bowes Inc. | Method of manufacturing secure boxes in a key management system |
| US5680456A (en) * | 1995-03-31 | 1997-10-21 | Pitney Bowes Inc. | Method of manufacturing generic meters in a key management system |
| US5982896A (en) * | 1996-12-23 | 1999-11-09 | Pitney Bowes Inc. | System and method of verifying cryptographic postage evidencing using a fixed key set |
| GB9704159D0 (en) | 1997-02-28 | 1997-04-16 | Neopost Ltd | Security and authentication of postage indicia |
| DE19711998A1 (de) * | 1997-03-13 | 1998-09-17 | Francotyp Postalia Gmbh | Postverarbeitungssystem mit einer über Personalcomputer gesteuerten druckenden Maschinen-Basisstation |
| DE19748954A1 (de) * | 1997-10-29 | 1999-05-06 | Francotyp Postalia Gmbh | Verfahren für eine digital druckende Frankiermaschine zur Erzeugung und Überprüfung eines Sicherheitsabdruckes |
| US6233565B1 (en) * | 1998-02-13 | 2001-05-15 | Saranac Software, Inc. | Methods and apparatus for internet based financial transactions with evidence of payment |
| DE19913067A1 (de) * | 1999-03-17 | 2000-09-21 | Francotyp Postalia Gmbh | Verfahren zur automatischen Installation von Frankiereinrichtungen und Anordnung zur Durchführung des Verfahrens |
| US6847951B1 (en) * | 1999-03-30 | 2005-01-25 | Pitney Bowes Inc. | Method for certifying public keys used to sign postal indicia and indicia so signed |
| DE19925194B4 (de) | 1999-06-01 | 2010-08-12 | Francotyp-Postalia Gmbh | Verfahren zur Postgutverarbeitung und Postgutverarbeitungssystem |
| WO2001029779A1 (fr) * | 1999-10-18 | 2001-04-26 | Stamps.Com | Base de donnees sure et recuperable pour systeme en ligne relatif a des articles porteurs de valeur |
| DE10023145A1 (de) * | 2000-05-12 | 2001-11-15 | Francotyp Postalia Gmbh | Frankiermaschine und Verfahren zur Freigabe einer Frankiermaschine |
| US6934839B1 (en) * | 2000-06-30 | 2005-08-23 | Stamps.Com Inc. | Evidencing and verifying indicia of value using secret key cryptography |
| US6938016B1 (en) * | 2000-08-08 | 2005-08-30 | Pitney Bowes Inc. | Digital coin-based postage meter |
| US6868407B1 (en) * | 2000-11-02 | 2005-03-15 | Pitney Bowes Inc. | Postage security device having cryptographic keys with a variable key length |
| US6944770B2 (en) * | 2001-05-17 | 2005-09-13 | Intelli-Mark Technologies, Inc. | Methods and systems for generating and validating value-bearing documents |
| US7225166B2 (en) * | 2002-03-22 | 2007-05-29 | Neopost Technologies | Remote authentication of two dimensional barcoded indicia |
| US6801833B2 (en) | 2002-09-10 | 2004-10-05 | Pitney Bowes Inc. | Method for maintaining the integrity of a mailing using radio frequency identification tags |
| US7069253B2 (en) * | 2002-09-26 | 2006-06-27 | Neopost Inc. | Techniques for tracking mailpieces and accounting for postage payment |
| US7110576B2 (en) | 2002-12-30 | 2006-09-19 | Pitney Bowes Inc. | System and method for authenticating a mailpiece sender |
| DE10305730B4 (de) * | 2003-02-12 | 2005-04-07 | Deutsche Post Ag | Verfahren zum Überprüfen der Gültigkeit von digitalen Freimachungsvermerken |
| DE102004014427A1 (de) * | 2004-03-19 | 2005-10-27 | Francotyp-Postalia Ag & Co. Kg | Verfahren für ein servergesteuertes Sicherheitsmanagement von erbringbaren Dienstleistungen und Anordnung zur Bereitstellung von Daten nach einem Sicherheitsmanagement für ein Frankiersystem |
| US20060002550A1 (en) * | 2004-05-25 | 2006-01-05 | Pitney Bowes Incorporated | Method and system for generation of cryptographic keys and the like |
| US7243842B1 (en) * | 2004-07-27 | 2007-07-17 | Stamps.Com Inc. | Computer-based value-bearing item customization security |
| US7912788B2 (en) * | 2004-09-29 | 2011-03-22 | Pitney Bowes Inc. | Mutual authentication system and method for protection of postal security devices and infrastructure |
-
2007
- 2007-11-02 DE DE102007052458A patent/DE102007052458A1/de not_active Withdrawn
-
2008
- 2008-09-26 US US12/238,747 patent/US8046304B2/en not_active Expired - Fee Related
- 2008-10-01 AT AT08017285T patent/ATE517405T1/de active
- 2008-10-01 EP EP08017285A patent/EP2058769B1/fr not_active Not-in-force
Also Published As
| Publication number | Publication date |
|---|---|
| ATE517405T1 (de) | 2011-08-15 |
| US8046304B2 (en) | 2011-10-25 |
| EP2058769A1 (fr) | 2009-05-13 |
| DE102007052458A1 (de) | 2009-05-07 |
| US20090119219A1 (en) | 2009-05-07 |
Similar Documents
| Publication | Publication Date | Title |
|---|---|---|
| EP2058769B1 (fr) | Procédé d'affranchissement et système d'expédition de courrier avec augmentation de frais de port centrale | |
| EP0944027B1 (fr) | Machine à affranchir et un procédé pour générer des données valables pour affranchir | |
| EP1405274B1 (fr) | Procede de verification de la validite de mentions d'affranchissement numeriques | |
| DE69724345T2 (de) | System zur kontrollierten Annahme von Poststücken, das sicher die Wiederverwendung einer ursprünglich für ein Poststück erzeugten digitalen Wertmarke bei einem später vorbereiteten anderen Poststück zum Beglaubigen der Bezahlung der Postgebühren ermöglicht | |
| DE69435016T2 (de) | System zum Austauschen elektronischer Daten für den Nachweis von Postgebühren | |
| DE3841394C2 (de) | Verfahren für die Ausgabe von Postgebühren | |
| DE3613008A1 (de) | Portogebuehren- und versandinformations-aufbringungssystem | |
| DE69637237T2 (de) | Verfahren and Vorrichtung zur Authentifizierung von Postgebührenabrechnungsberichten | |
| EP0892368B1 (fr) | Procédé pour le téléchargement de données statistiques et de recensement en ensembles statistiques lors du chargement des données | |
| EP2017791A1 (fr) | Procédé, dispositif et système logistique destinés au transport d'envois postaux | |
| DE3613025C2 (de) | Nichtgesichertes Portogebühren-Aufbringungssystem | |
| DE19757653C2 (de) | Verfahren und postalisches Gerät mit einer Chipkarten-Schreib/Leseeinheit zum Nachladen von Änderungsdaten per Chipkarte | |
| DE69931388T2 (de) | Verfahren und system zur erstellung und überprüfung von frankierzeichen | |
| DE69932605T2 (de) | System und verfahren zur verwaltung von frankiermaschinenlizenzen | |
| DE19711998A1 (de) | Postverarbeitungssystem mit einer über Personalcomputer gesteuerten druckenden Maschinen-Basisstation | |
| EP1337974B1 (fr) | Procede servant a porter des marques d'affranchissement sur des envois postaux | |
| WO2004061779A1 (fr) | Procede et dispositif pour le traitement d'information graphique figurant sur des surfaces d'articles postaux | |
| DE60015907T2 (de) | Verfahren und Vorrichtung zur Erzeugung von Nachrichten welche eine prüfbare Behauptung enthalten dass eine Veränderliche sich innerhalb bestimmter Grenzwerte befindet | |
| EP1279147B1 (fr) | Procede servant a pourvoir des envois postaux de mentions d'affranchissement | |
| DE69930202T2 (de) | Verfahren zur Begrenzung der Schlüsselbenutzung in einem Frankiersystem welches kryptographisch gesicherte Briefmarken produziert | |
| EP1340197B1 (fr) | Procede pour apposer des marques d'affranchissement sur des envois postaux | |
| DE69924946T2 (de) | Verfahren und Vorrichtung zum dynamischen Anordnen und Drucken von einer Vielzahl von Postwertzeichen auf einem Poststück | |
| EP2140429A1 (fr) | Procédé et dispositif d'affranchissement d'un envoi postal avec enregistrement d'une information d'identification dans une liste positive | |
| EP1486028A1 (fr) | Procede et dispositif permettant de creer des documents infalsifiables verifiables |
Legal Events
| Date | Code | Title | Description |
|---|---|---|---|
| PUAI | Public reference made under article 153(3) epc to a published international application that has entered the european phase |
Free format text: ORIGINAL CODE: 0009012 |
|
| AK | Designated contracting states |
Kind code of ref document: A1 Designated state(s): AT BE BG CH CY CZ DE DK EE ES FI FR GB GR HR HU IE IS IT LI LT LU LV MC MT NL NO PL PT RO SE SI SK TR |
|
| AX | Request for extension of the european patent |
Extension state: AL BA MK RS |
|
| 17P | Request for examination filed |
Effective date: 20090519 |
|
| 17Q | First examination report despatched |
Effective date: 20090617 |
|
| AKX | Designation fees paid |
Designated state(s): AT BE BG CH CY CZ DE DK EE ES FI FR GB GR HR HU IE IS IT LI LT LU LV MC MT NL NO PL PT RO SE SI SK TR |
|
| R17C | First examination report despatched (corrected) |
Effective date: 20090617 |
|
| GRAP | Despatch of communication of intention to grant a patent |
Free format text: ORIGINAL CODE: EPIDOSNIGR1 |
|
| GRAS | Grant fee paid |
Free format text: ORIGINAL CODE: EPIDOSNIGR3 |
|
| GRAA | (expected) grant |
Free format text: ORIGINAL CODE: 0009210 |
|
| AK | Designated contracting states |
Kind code of ref document: B1 Designated state(s): AT BE BG CH CY CZ DE DK EE ES FI FR GB GR HR HU IE IS IT LI LT LU LV MC MT NL NO PL PT RO SE SI SK TR |
|
| REG | Reference to a national code |
Ref country code: GB Ref legal event code: FG4D Free format text: NOT ENGLISH |
|
| REG | Reference to a national code |
Ref country code: CH Ref legal event code: EP |
|
| REG | Reference to a national code |
Ref country code: DE Ref legal event code: R096 Ref document number: 502008004236 Country of ref document: DE Effective date: 20110915 |
|
| REG | Reference to a national code |
Ref country code: SE Ref legal event code: TRGR |
|
| REG | Reference to a national code |
Ref country code: NL Ref legal event code: T3 |
|
| PG25 | Lapsed in a contracting state [announced via postgrant information from national office to epo] |
Ref country code: HR Free format text: LAPSE BECAUSE OF FAILURE TO SUBMIT A TRANSLATION OF THE DESCRIPTION OR TO PAY THE FEE WITHIN THE PRESCRIBED TIME-LIMIT Effective date: 20110720 Ref country code: PT Free format text: LAPSE BECAUSE OF FAILURE TO SUBMIT A TRANSLATION OF THE DESCRIPTION OR TO PAY THE FEE WITHIN THE PRESCRIBED TIME-LIMIT Effective date: 20111121 Ref country code: NO Free format text: LAPSE BECAUSE OF FAILURE TO SUBMIT A TRANSLATION OF THE DESCRIPTION OR TO PAY THE FEE WITHIN THE PRESCRIBED TIME-LIMIT Effective date: 20111020 Ref country code: LT Free format text: LAPSE BECAUSE OF FAILURE TO SUBMIT A TRANSLATION OF THE DESCRIPTION OR TO PAY THE FEE WITHIN THE PRESCRIBED TIME-LIMIT Effective date: 20110720 Ref country code: IS Free format text: LAPSE BECAUSE OF FAILURE TO SUBMIT A TRANSLATION OF THE DESCRIPTION OR TO PAY THE FEE WITHIN THE PRESCRIBED TIME-LIMIT Effective date: 20111120 Ref country code: FI Free format text: LAPSE BECAUSE OF FAILURE TO SUBMIT A TRANSLATION OF THE DESCRIPTION OR TO PAY THE FEE WITHIN THE PRESCRIBED TIME-LIMIT Effective date: 20110720 |
|
| REG | Reference to a national code |
Ref country code: IE Ref legal event code: FD4D |
|
| PG25 | Lapsed in a contracting state [announced via postgrant information from national office to epo] |
Ref country code: PL Free format text: LAPSE BECAUSE OF FAILURE TO SUBMIT A TRANSLATION OF THE DESCRIPTION OR TO PAY THE FEE WITHIN THE PRESCRIBED TIME-LIMIT Effective date: 20110720 Ref country code: CY Free format text: LAPSE BECAUSE OF FAILURE TO SUBMIT A TRANSLATION OF THE DESCRIPTION OR TO PAY THE FEE WITHIN THE PRESCRIBED TIME-LIMIT Effective date: 20110720 Ref country code: GR Free format text: LAPSE BECAUSE OF FAILURE TO SUBMIT A TRANSLATION OF THE DESCRIPTION OR TO PAY THE FEE WITHIN THE PRESCRIBED TIME-LIMIT Effective date: 20111021 Ref country code: SI Free format text: LAPSE BECAUSE OF FAILURE TO SUBMIT A TRANSLATION OF THE DESCRIPTION OR TO PAY THE FEE WITHIN THE PRESCRIBED TIME-LIMIT Effective date: 20110720 Ref country code: LV Free format text: LAPSE BECAUSE OF FAILURE TO SUBMIT A TRANSLATION OF THE DESCRIPTION OR TO PAY THE FEE WITHIN THE PRESCRIBED TIME-LIMIT Effective date: 20110720 |
|
| BERE | Be: lapsed |
Owner name: FRANCOTYP-POSTALIA G.M.B.H. Effective date: 20111031 |
|
| PG25 | Lapsed in a contracting state [announced via postgrant information from national office to epo] |
Ref country code: SK Free format text: LAPSE BECAUSE OF FAILURE TO SUBMIT A TRANSLATION OF THE DESCRIPTION OR TO PAY THE FEE WITHIN THE PRESCRIBED TIME-LIMIT Effective date: 20110720 Ref country code: IE Free format text: LAPSE BECAUSE OF FAILURE TO SUBMIT A TRANSLATION OF THE DESCRIPTION OR TO PAY THE FEE WITHIN THE PRESCRIBED TIME-LIMIT Effective date: 20110720 Ref country code: CZ Free format text: LAPSE BECAUSE OF FAILURE TO SUBMIT A TRANSLATION OF THE DESCRIPTION OR TO PAY THE FEE WITHIN THE PRESCRIBED TIME-LIMIT Effective date: 20110720 |
|
| PLBE | No opposition filed within time limit |
Free format text: ORIGINAL CODE: 0009261 |
|
| STAA | Information on the status of an ep patent application or granted ep patent |
Free format text: STATUS: NO OPPOSITION FILED WITHIN TIME LIMIT |
|
| PG25 | Lapsed in a contracting state [announced via postgrant information from national office to epo] |
Ref country code: EE Free format text: LAPSE BECAUSE OF FAILURE TO SUBMIT A TRANSLATION OF THE DESCRIPTION OR TO PAY THE FEE WITHIN THE PRESCRIBED TIME-LIMIT Effective date: 20110720 Ref country code: MC Free format text: LAPSE BECAUSE OF NON-PAYMENT OF DUE FEES Effective date: 20111031 Ref country code: RO Free format text: LAPSE BECAUSE OF FAILURE TO SUBMIT A TRANSLATION OF THE DESCRIPTION OR TO PAY THE FEE WITHIN THE PRESCRIBED TIME-LIMIT Effective date: 20110720 |
|
| 26N | No opposition filed |
Effective date: 20120423 |
|
| PG25 | Lapsed in a contracting state [announced via postgrant information from national office to epo] |
Ref country code: DK Free format text: LAPSE BECAUSE OF FAILURE TO SUBMIT A TRANSLATION OF THE DESCRIPTION OR TO PAY THE FEE WITHIN THE PRESCRIBED TIME-LIMIT Effective date: 20110720 |
|
| PG25 | Lapsed in a contracting state [announced via postgrant information from national office to epo] |
Ref country code: BE Free format text: LAPSE BECAUSE OF NON-PAYMENT OF DUE FEES Effective date: 20111031 |
|
| REG | Reference to a national code |
Ref country code: DE Ref legal event code: R097 Ref document number: 502008004236 Country of ref document: DE Effective date: 20120423 |
|
| PG25 | Lapsed in a contracting state [announced via postgrant information from national office to epo] |
Ref country code: MT Free format text: LAPSE BECAUSE OF FAILURE TO SUBMIT A TRANSLATION OF THE DESCRIPTION OR TO PAY THE FEE WITHIN THE PRESCRIBED TIME-LIMIT Effective date: 20110720 |
|
| PG25 | Lapsed in a contracting state [announced via postgrant information from national office to epo] |
Ref country code: ES Free format text: LAPSE BECAUSE OF FAILURE TO SUBMIT A TRANSLATION OF THE DESCRIPTION OR TO PAY THE FEE WITHIN THE PRESCRIBED TIME-LIMIT Effective date: 20111031 |
|
| PG25 | Lapsed in a contracting state [announced via postgrant information from national office to epo] |
Ref country code: LU Free format text: LAPSE BECAUSE OF NON-PAYMENT OF DUE FEES Effective date: 20111001 |
|
| PG25 | Lapsed in a contracting state [announced via postgrant information from national office to epo] |
Ref country code: BG Free format text: LAPSE BECAUSE OF FAILURE TO SUBMIT A TRANSLATION OF THE DESCRIPTION OR TO PAY THE FEE WITHIN THE PRESCRIBED TIME-LIMIT Effective date: 20111020 |
|
| PG25 | Lapsed in a contracting state [announced via postgrant information from national office to epo] |
Ref country code: TR Free format text: LAPSE BECAUSE OF FAILURE TO SUBMIT A TRANSLATION OF THE DESCRIPTION OR TO PAY THE FEE WITHIN THE PRESCRIBED TIME-LIMIT Effective date: 20110720 |
|
| PG25 | Lapsed in a contracting state [announced via postgrant information from national office to epo] |
Ref country code: HU Free format text: LAPSE BECAUSE OF FAILURE TO SUBMIT A TRANSLATION OF THE DESCRIPTION OR TO PAY THE FEE WITHIN THE PRESCRIBED TIME-LIMIT Effective date: 20110720 |
|
| REG | Reference to a national code |
Ref country code: DE Ref legal event code: R081 Ref document number: 502008004236 Country of ref document: DE Owner name: FRANCOTYP-POSTALIA GMBH, DE Free format text: FORMER OWNER: FRANCOTYP-POSTALIA GMBH, 16547 BIRKENWERDER, DE Effective date: 20150330 |
|
| REG | Reference to a national code |
Ref country code: FR Ref legal event code: PLFP Year of fee payment: 8 |
|
| PGFP | Annual fee paid to national office [announced via postgrant information from national office to epo] |
Ref country code: GB Payment date: 20151021 Year of fee payment: 8 Ref country code: CH Payment date: 20151021 Year of fee payment: 8 Ref country code: IT Payment date: 20151028 Year of fee payment: 8 Ref country code: DE Payment date: 20150827 Year of fee payment: 8 |
|
| PGFP | Annual fee paid to national office [announced via postgrant information from national office to epo] |
Ref country code: AT Payment date: 20151022 Year of fee payment: 8 Ref country code: SE Payment date: 20151021 Year of fee payment: 8 Ref country code: NL Payment date: 20151021 Year of fee payment: 8 Ref country code: FR Payment date: 20151023 Year of fee payment: 8 |
|
| REG | Reference to a national code |
Ref country code: DE Ref legal event code: R119 Ref document number: 502008004236 Country of ref document: DE |
|
| REG | Reference to a national code |
Ref country code: CH Ref legal event code: PL |
|
| REG | Reference to a national code |
Ref country code: NL Ref legal event code: MM Effective date: 20161101 |
|
| REG | Reference to a national code |
Ref country code: AT Ref legal event code: MM01 Ref document number: 517405 Country of ref document: AT Kind code of ref document: T Effective date: 20161001 |
|
| GBPC | Gb: european patent ceased through non-payment of renewal fee |
Effective date: 20161001 |
|
| REG | Reference to a national code |
Ref country code: FR Ref legal event code: ST Effective date: 20170630 |
|
| PG25 | Lapsed in a contracting state [announced via postgrant information from national office to epo] |
Ref country code: DE Free format text: LAPSE BECAUSE OF NON-PAYMENT OF DUE FEES Effective date: 20170503 Ref country code: CH Free format text: LAPSE BECAUSE OF NON-PAYMENT OF DUE FEES Effective date: 20161031 Ref country code: GB Free format text: LAPSE BECAUSE OF NON-PAYMENT OF DUE FEES Effective date: 20161001 Ref country code: FR Free format text: LAPSE BECAUSE OF NON-PAYMENT OF DUE FEES Effective date: 20161102 Ref country code: LI Free format text: LAPSE BECAUSE OF NON-PAYMENT OF DUE FEES Effective date: 20161031 |
|
| PG25 | Lapsed in a contracting state [announced via postgrant information from national office to epo] |
Ref country code: NL Free format text: LAPSE BECAUSE OF NON-PAYMENT OF DUE FEES Effective date: 20161101 Ref country code: AT Free format text: LAPSE BECAUSE OF NON-PAYMENT OF DUE FEES Effective date: 20161001 Ref country code: SE Free format text: LAPSE BECAUSE OF NON-PAYMENT OF DUE FEES Effective date: 20161002 |
|
| PG25 | Lapsed in a contracting state [announced via postgrant information from national office to epo] |
Ref country code: IT Free format text: LAPSE BECAUSE OF NON-PAYMENT OF DUE FEES Effective date: 20161001 |