WO2009116338A1 - コンテンツ送信装置、コンテンツ受信装置 - Google Patents
コンテンツ送信装置、コンテンツ受信装置 Download PDFInfo
- Publication number
- WO2009116338A1 WO2009116338A1 PCT/JP2009/052504 JP2009052504W WO2009116338A1 WO 2009116338 A1 WO2009116338 A1 WO 2009116338A1 JP 2009052504 W JP2009052504 W JP 2009052504W WO 2009116338 A1 WO2009116338 A1 WO 2009116338A1
- Authority
- WO
- WIPO (PCT)
- Prior art keywords
- content
- authentication
- home
- information
- outside
- Prior art date
- Legal status (The legal status is an assumption and is not a legal conclusion. Google has not performed a legal analysis and makes no representation as to the accuracy of the status listed.)
- Ceased
Links
Images
Classifications
-
- H—ELECTRICITY
- H04—ELECTRIC COMMUNICATION TECHNIQUE
- H04L—TRANSMISSION OF DIGITAL INFORMATION, e.g. TELEGRAPHIC COMMUNICATION
- H04L9/00—Cryptographic mechanisms or cryptographic arrangements for secret or secure communications; Network security protocols
- H04L9/32—Cryptographic mechanisms or cryptographic arrangements for secret or secure communications; Network security protocols including means for verifying the identity or authority of a user of the system or for message authentication, e.g. authorization, entity authentication, data integrity or data verification, non-repudiation, key authentication or verification of credentials
- H04L9/3271—Cryptographic mechanisms or cryptographic arrangements for secret or secure communications; Network security protocols including means for verifying the identity or authority of a user of the system or for message authentication, e.g. authorization, entity authentication, data integrity or data verification, non-repudiation, key authentication or verification of credentials using challenge-response
- H04L9/3273—Cryptographic mechanisms or cryptographic arrangements for secret or secure communications; Network security protocols including means for verifying the identity or authority of a user of the system or for message authentication, e.g. authorization, entity authentication, data integrity or data verification, non-repudiation, key authentication or verification of credentials using challenge-response for mutual authentication
-
- H—ELECTRICITY
- H04—ELECTRIC COMMUNICATION TECHNIQUE
- H04L—TRANSMISSION OF DIGITAL INFORMATION, e.g. TELEGRAPHIC COMMUNICATION
- H04L12/00—Data switching networks
- H04L12/28—Data switching networks characterised by path configuration, e.g. LAN [Local Area Networks] or WAN [Wide Area Networks]
- H04L12/2803—Home automation networks
- H04L12/283—Processing of data at an internetworking point of a home automation network
- H04L12/2834—Switching of information between an external network and a home network
-
- H—ELECTRICITY
- H04—ELECTRIC COMMUNICATION TECHNIQUE
- H04L—TRANSMISSION OF DIGITAL INFORMATION, e.g. TELEGRAPHIC COMMUNICATION
- H04L63/00—Network architectures or network communication protocols for network security
- H04L63/04—Network architectures or network communication protocols for network security for providing a confidential data exchange among entities communicating through data packet networks
- H04L63/0428—Network architectures or network communication protocols for network security for providing a confidential data exchange among entities communicating through data packet networks wherein the data content is protected, e.g. by encrypting or encapsulating the payload
-
- H—ELECTRICITY
- H04—ELECTRIC COMMUNICATION TECHNIQUE
- H04L—TRANSMISSION OF DIGITAL INFORMATION, e.g. TELEGRAPHIC COMMUNICATION
- H04L63/00—Network architectures or network communication protocols for network security
- H04L63/08—Network architectures or network communication protocols for network security for authentication of entities
-
- H—ELECTRICITY
- H04—ELECTRIC COMMUNICATION TECHNIQUE
- H04L—TRANSMISSION OF DIGITAL INFORMATION, e.g. TELEGRAPHIC COMMUNICATION
- H04L9/00—Cryptographic mechanisms or cryptographic arrangements for secret or secure communications; Network security protocols
- H04L9/08—Key distribution or management, e.g. generation, sharing or updating, of cryptographic keys or passwords
- H04L9/0816—Key establishment, i.e. cryptographic processes or cryptographic protocols whereby a shared secret becomes available to two or more parties, for subsequent use
- H04L9/0838—Key agreement, i.e. key establishment technique in which a shared key is derived by parties as a function of information contributed by, or associated with, each of these
-
- H—ELECTRICITY
- H04—ELECTRIC COMMUNICATION TECHNIQUE
- H04N—PICTORIAL COMMUNICATION, e.g. TELEVISION
- H04N21/00—Selective content distribution, e.g. interactive television or video on demand [VOD]
- H04N21/20—Servers specifically adapted for the distribution of content, e.g. VOD servers; Operations thereof
- H04N21/25—Management operations performed by the server for facilitating the content distribution or administrating data related to end-users or client devices, e.g. end-user or client device authentication, learning user preferences for recommending movies
- H04N21/258—Client or end-user data management, e.g. managing client capabilities, user preferences or demographics, processing of multiple end-users preferences to derive collaborative data
- H04N21/25866—Management of end-user data
- H04N21/25875—Management of end-user data involving end-user authentication
-
- H—ELECTRICITY
- H04—ELECTRIC COMMUNICATION TECHNIQUE
- H04N—PICTORIAL COMMUNICATION, e.g. TELEVISION
- H04N21/00—Selective content distribution, e.g. interactive television or video on demand [VOD]
- H04N21/40—Client devices specifically adapted for the reception of or interaction with content, e.g. set-top-box [STB]; Operations thereof
- H04N21/41—Structure of client; Structure of client peripherals
- H04N21/4104—Peripherals receiving signals from specially adapted client devices
- H04N21/4126—The peripheral being portable, e.g. PDAs or mobile phones
- H04N21/41265—The peripheral being portable, e.g. PDAs or mobile phones having a remote control device for bidirectional communication between the remote control device and client device
-
- H—ELECTRICITY
- H04—ELECTRIC COMMUNICATION TECHNIQUE
- H04N—PICTORIAL COMMUNICATION, e.g. TELEVISION
- H04N21/00—Selective content distribution, e.g. interactive television or video on demand [VOD]
- H04N21/40—Client devices specifically adapted for the reception of or interaction with content, e.g. set-top-box [STB]; Operations thereof
- H04N21/41—Structure of client; Structure of client peripherals
- H04N21/422—Input-only peripherals, i.e. input devices connected to specially adapted client devices, e.g. global positioning system [GPS]
- H04N21/4227—Providing Remote input by a user located remotely from the client device, e.g. at work
-
- H—ELECTRICITY
- H04—ELECTRIC COMMUNICATION TECHNIQUE
- H04N—PICTORIAL COMMUNICATION, e.g. TELEVISION
- H04N21/00—Selective content distribution, e.g. interactive television or video on demand [VOD]
- H04N21/40—Client devices specifically adapted for the reception of or interaction with content, e.g. set-top-box [STB]; Operations thereof
- H04N21/43—Processing of content or additional data, e.g. demultiplexing additional data from a digital video stream; Elementary client operations, e.g. monitoring of home network or synchronising decoder's clock; Client middleware
- H04N21/432—Content retrieval operation from a local storage medium, e.g. hard-disk
- H04N21/4325—Content retrieval operation from a local storage medium, e.g. hard-disk by playing back content from the storage medium
-
- H—ELECTRICITY
- H04—ELECTRIC COMMUNICATION TECHNIQUE
- H04N—PICTORIAL COMMUNICATION, e.g. TELEVISION
- H04N21/00—Selective content distribution, e.g. interactive television or video on demand [VOD]
- H04N21/40—Client devices specifically adapted for the reception of or interaction with content, e.g. set-top-box [STB]; Operations thereof
- H04N21/43—Processing of content or additional data, e.g. demultiplexing additional data from a digital video stream; Elementary client operations, e.g. monitoring of home network or synchronising decoder's clock; Client middleware
- H04N21/436—Interfacing a local distribution network, e.g. communicating with another STB or one or more peripheral devices inside the home
- H04N21/43615—Interfacing a Home Network, e.g. for connecting the client to a plurality of peripherals
-
- H—ELECTRICITY
- H04—ELECTRIC COMMUNICATION TECHNIQUE
- H04N—PICTORIAL COMMUNICATION, e.g. TELEVISION
- H04N21/00—Selective content distribution, e.g. interactive television or video on demand [VOD]
- H04N21/40—Client devices specifically adapted for the reception of or interaction with content, e.g. set-top-box [STB]; Operations thereof
- H04N21/43—Processing of content or additional data, e.g. demultiplexing additional data from a digital video stream; Elementary client operations, e.g. monitoring of home network or synchronising decoder's clock; Client middleware
- H04N21/436—Interfacing a local distribution network, e.g. communicating with another STB or one or more peripheral devices inside the home
- H04N21/43622—Interfacing an external recording device
-
- H—ELECTRICITY
- H04—ELECTRIC COMMUNICATION TECHNIQUE
- H04N—PICTORIAL COMMUNICATION, e.g. TELEVISION
- H04N21/00—Selective content distribution, e.g. interactive television or video on demand [VOD]
- H04N21/40—Client devices specifically adapted for the reception of or interaction with content, e.g. set-top-box [STB]; Operations thereof
- H04N21/43—Processing of content or additional data, e.g. demultiplexing additional data from a digital video stream; Elementary client operations, e.g. monitoring of home network or synchronising decoder's clock; Client middleware
- H04N21/436—Interfacing a local distribution network, e.g. communicating with another STB or one or more peripheral devices inside the home
- H04N21/4367—Establishing a secure communication between the client and a peripheral device or smart card
-
- H—ELECTRICITY
- H04—ELECTRIC COMMUNICATION TECHNIQUE
- H04N—PICTORIAL COMMUNICATION, e.g. TELEVISION
- H04N21/00—Selective content distribution, e.g. interactive television or video on demand [VOD]
- H04N21/40—Client devices specifically adapted for the reception of or interaction with content, e.g. set-top-box [STB]; Operations thereof
- H04N21/47—End-user applications
- H04N21/475—End-user interface for inputting end-user data, e.g. personal identification number [PIN], preference data
- H04N21/4753—End-user interface for inputting end-user data, e.g. personal identification number [PIN], preference data for user identification, e.g. by entering a PIN or password
-
- H—ELECTRICITY
- H04—ELECTRIC COMMUNICATION TECHNIQUE
- H04N—PICTORIAL COMMUNICATION, e.g. TELEVISION
- H04N21/00—Selective content distribution, e.g. interactive television or video on demand [VOD]
- H04N21/60—Network structure or processes for video distribution between server and client or between remote clients; Control signalling between clients, server and network components; Transmission of management data between server and client, e.g. sending from server to client commands for recording incoming content stream; Communication details between server and client
- H04N21/63—Control signaling related to video distribution between client, server and network components; Network processes for video distribution between server and clients or between remote clients, e.g. transmitting basic layer and enhancement layers over different transmission paths, setting up a peer-to-peer communication via Internet between remote STB's; Communication protocols; Addressing
- H04N21/633—Control signals issued by server directed to the network components or client
- H04N21/6332—Control signals issued by server directed to the network components or client directed to client
- H04N21/6334—Control signals issued by server directed to the network components or client directed to client for authorisation, e.g. by transmitting a key
- H04N21/63345—Control signals issued by server directed to the network components or client directed to client for authorisation, e.g. by transmitting a key by transmitting keys
-
- H—ELECTRICITY
- H04—ELECTRIC COMMUNICATION TECHNIQUE
- H04N—PICTORIAL COMMUNICATION, e.g. TELEVISION
- H04N7/00—Television systems
- H04N7/16—Analogue secrecy systems; Analogue subscription systems
- H04N7/162—Authorising the user terminal, e.g. by paying; Registering the use of a subscription channel, e.g. billing
- H04N7/165—Centralised control of user terminal ; Registering at central
-
- H—ELECTRICITY
- H04—ELECTRIC COMMUNICATION TECHNIQUE
- H04N—PICTORIAL COMMUNICATION, e.g. TELEVISION
- H04N7/00—Television systems
- H04N7/16—Analogue secrecy systems; Analogue subscription systems
- H04N7/173—Analogue secrecy systems; Analogue subscription systems with two-way working, e.g. subscriber sending a programme selection signal
- H04N7/17309—Transmission or handling of upstream communications
-
- H—ELECTRICITY
- H04—ELECTRIC COMMUNICATION TECHNIQUE
- H04N—PICTORIAL COMMUNICATION, e.g. TELEVISION
- H04N7/00—Television systems
- H04N7/16—Analogue secrecy systems; Analogue subscription systems
- H04N7/173—Analogue secrecy systems; Analogue subscription systems with two-way working, e.g. subscriber sending a programme selection signal
- H04N7/17309—Transmission or handling of upstream communications
- H04N7/17318—Direct or substantially direct transmission and handling of requests
-
- H—ELECTRICITY
- H04—ELECTRIC COMMUNICATION TECHNIQUE
- H04L—TRANSMISSION OF DIGITAL INFORMATION, e.g. TELEGRAPHIC COMMUNICATION
- H04L12/00—Data switching networks
- H04L12/28—Data switching networks characterised by path configuration, e.g. LAN [Local Area Networks] or WAN [Wide Area Networks]
- H04L12/2803—Home automation networks
- H04L2012/2847—Home automation networks characterised by the type of home appliance used
- H04L2012/2849—Audio/video appliances
-
- H—ELECTRICITY
- H04—ELECTRIC COMMUNICATION TECHNIQUE
- H04L—TRANSMISSION OF DIGITAL INFORMATION, e.g. TELEGRAPHIC COMMUNICATION
- H04L2209/00—Additional information or applications relating to cryptographic mechanisms or cryptographic arrangements for secret or secure communication H04L9/00
- H04L2209/60—Digital content management, e.g. content distribution
- H04L2209/603—Digital right managament [DRM]
Definitions
- the present invention relates to a transmission device, a reception device, and a content transmission method suitable for protecting the copyright of transmitted content when transmitting and receiving content such as video and audio via a network.
- HDDs hard disk drives
- DTV digital tuner built-in television
- BDs digital broadcast programs
- Digital AV devices such as recorders have been commercialized one after another.
- these digital AV devices can be equipped with digital interfaces such as wired / wireless LAN (Local Area Network), IEEE 1394, USB, etc., and digital contents can be transmitted via the network. .
- digital interfaces such as wired / wireless LAN (Local Area Network), IEEE 1394, USB, etc.
- DTCP Digital Transmission Content Protection
- content is classified and managed as “no copy restriction”, “one-time copy allowed”, and “copy prohibited”, and the recording device records only the content of “no copy restriction” and “one-time copy allowed”,
- the content of “one-time copy allowed” is treated as “copy not possible” after recording once, and on the bus except for the content of “no copy restriction”, the transmission side performs encryption processing and performs transmission, Unlimited content copying is prohibited.
- the DTCP-IP system in which the DTCP system is extended to an IP network and further security is enhanced.
- a technique for determining whether or not the content is subject to copyright protection, such as a broadcast program recorded at home is an in-home network so that it is not distributed outside the home without limitation. ing.
- a content transmitting device and a receiving device capable of limiting the legitimate viewing of the content to the range of personal use It is another object of the present invention to provide a content transmission method.
- the content transmission device Authenticate that the devices are properly certified with each other in accordance with the first authentication protocol with the content receiving device connected to the home network, and confirm that the content receiving device exists in the home.
- a first authentication means to confirm External access information sharing means for sharing information necessary for access from outside the home with the content receiving device;
- Device information management means for holding and managing information related to the content receiving device that has been successfully authenticated by the first authentication means, and information shared by the external access information sharing means;
- a second authentication means for authenticating The first key information that can be shared with the content receiving apparatus by executing the authentication process by the first authentication means, or the second key that can be shared by executing the authentication process by the second authentication means Encryption means for performing encryption processing of content to be transmitted to the content receiving device using key information; With Only when the authentication process is successful with the content receiving apparatus using the first authentication means, the access information required outside the home using the outside access information sharing means Sharing, registering information about the content receiving device and the out-of-home access information using the device information management means, Only when the authentication process with the content receiving apparatus is successful using the second authentication processing means, the content is encrypted and transmitted to the content receiving apparatus outside the home using the encryption means. To do.
- System configuration example One block configuration example of DTV
- HDD recorder PC block configuration example One block configuration example of a mobile phone
- Configuration example of the device information management unit Configuration example of device information
- Configuration example of device information System configuration example An example of a sequence for executing content transfer from a content receiving device outside the home to a content transmitting device inside the home.
- Mobile phone content transmitter list screen example Mobile phone content list screen example
- Configuration example of device information An example of a sequence for executing content transfer from a content receiving device outside the home to a content transmitting device inside the home.
- the feature of this embodiment is that content in the house can be viewed on a content receiving apparatus outside the home while preventing unauthorized viewing / duplication without exceeding the range of personal use of the content.
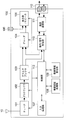
- FIG. 1 shows a system configuration, and it is assumed that the user A accesses a device in the home from the outside.
- the DTV 100, the HDD recorder 200, and the PC 300 owned by the user A are connected to the network via the hub 11 via a wired LAN.
- the hub 11 can be connected to the Internet 3 via the router 12.
- the user A's mobile phone 500 can communicate with the wireless access point 22 and can be connected to the Internet 3 via the router 21. Further, the user B's PC 400 can be connected to the Internet 3 in the same manner. Further, the DTV 600 installed outside the office can be connected to the Internet 3 via the router 21.
- IP Internet Protocol
- TCP Transmission Control Protocol
- UDP User Datagram Protocol
- RTP Real-time Transport Protocol
- HTTP Hyper Text Transfer Protocol
- FTP File Transfer Protocol
- Each of the mobile phone 500 and the routers 12 and 21 has an IP address for identifying itself on the LAN.
- a 48-bit MAC (Media Access Control) address is given in advance to the interface unit of each network communication processing circuit at the time of manufacture.
- the routers 12 and 21 are operated as DHCP servers by DHCP (Dynamic Host Configuration Protocol), which has been widely used for automatic address setting in the network.
- An IP address may be allocated.
- each device can determine its own IP address from the upper 64 bits of the IP address of the routers 12 and 21 and the MAC address by a method called stateless automatic setting.
- each device in the user home 1 is connected by a wired LAN, but a LAN using a wireless access point, IEEE 1394, USB, Bluetooth, or the like may be used.
- a LAN using a wireless access point IEEE 1394, USB, Bluetooth, or the like may be used.
- the hub 11 and the router 12 or the wireless access point 22 and the router 21 may be integrated.
- the routers 12 and 21 are connected to the Internet through a modem or photoelectric converter (not shown) or by a modem or photoelectric converter built in the router.
- the type of connection to the Internet may be any type such as a high-speed access line such as ADSL (Asymmetric Digital Subscriber line) or optical fiber, ISDN (Integrated Services Digital Network), an analog telephone line, or a mobile communication network such as a mobile phone.
- ADSL Asymmetric Digital Subscriber line
- ISDN Integrated Services Digital Network
- an analog telephone line or a mobile communication network such as a mobile phone.
- the network configuration in the outing destination 2 is the same as described above.
- a technology such as a port forward function of a router or a VPN (Virtual Private Network) may be used.
- the DTV 600 has the same configuration.
- the DTV 100 includes a tuner 101, a descrambler 102, a demultiplexer 103, a decoder 104, a display unit / speaker 105, a digital terminal 106, an input processing unit 107, a device authentication processing unit 108, a device information management unit 109, and an encryption / decryption processing unit 110. , A communication processing unit 111, a digital input / output terminal 112, and a control unit 113.
- the tuner 101 is a part that selects a desired channel from a plurality of channels received from the broadcasting station via the antenna 10 and demodulates a digitally modulated program.
- the descrambler 102 is a part that unscrambles a program that is being executed so as to be able to receive only a channel contracted with a service provider.
- the demultiplexer 103 is a part that extracts audio data and video data from a broadcast program.
- the decoder 104 is a part that decodes the compressed audio data and video data received from the broadcast program and the digital input / output terminal 112 and expands them to the original audio signal and video signal.
- the display / speaker 105 is a part that reproduces an output signal from the decoder 104 and a signal input from the digital terminal 106. It may be external rather than internal.
- the digital terminal 106 is a part to which uncompressed digital data is input, such as HDMI (High-Definition Multimedia Interface).
- the input processing unit 107 is a part where the user operates the DTV 100 using a remote controller, a touch panel, or the like.
- the device authentication processing unit 108 is a device mutually authorized in accordance with a specific authentication protocol with another AV device in order to transfer the content subject to copyright protection via the LAN. Is a part that shares the key used for content encryption / decryption.
- Examples of the specific authentication protocol include the DTCP method.
- the device information management unit 109 is a part that manages information related to the AV device that has been successfully authenticated by the device authentication processing unit 108.
- the encryption / decryption processing unit 110 is a part that encrypts or decrypts the content received via the digital input / output terminal 112 via a broadcast program or LAN using the key shared by the device authentication processing unit 108. .
- the communication processing unit 111 is a part that transmits and receives content and control commands to and from other AV devices connected via a LAN through the digital input / output terminal 112.
- the transmitted content is transmitted with an identification code such as “no copy restriction”, “one-time copy permitted”, “copy prohibited”, “copy not permitted” indicating how to handle the content.
- the digital input / output terminal 112 is a part for inputting / outputting contents and control commands via the LAN.
- the control unit 113 is a part that comprehensively controls the operation of each unit in the DTV 100.
- the HDD recorder 200 includes an input processing unit 201, a device authentication processing unit 202, a device information management unit 203, a recording / playback processing unit 204, an HDD 205, an encryption / decryption processing unit 206, a communication processing unit 207, a digital input / output terminal 208, and a decoder. 209, a digital terminal 210, and a control unit 211.
- the recording / playback processing unit 204 is a part that performs recording control for recording content in the HDD 205 and playback control for playing back the content recorded in the HDD 205.
- the HDD 205 is a built-in memory that records broadcast programs.
- a removable HDD, an optical disk, a memory card, and a hybrid form combining these can be considered.
- the digital terminal 210 is a part that outputs uncompressed digital data output from the decoder 209 to an external display unit or speaker. Other parts are the same as those of the DTV 100.
- the PC 300 includes a tuner 301, a descrambler 302, a demultiplexer 303, a decoder 304, a display unit / speaker 305, a digital terminal 306, an input processing unit 307, a device authentication processing unit 308, a device information management unit 309, and a recording / playback processing unit 310.
- the wireless encryption / decryption processing unit 315 performs security on wireless LAN such as WEP (WiredreEquivalentiPrivacy) for content received via the wireless LAN via the wireless communication processing unit 316 or content output from the encryption / decryption processing unit 312. This is a portion that is encrypted / decrypted using a known encryption method that is standardly used for the purpose of protection.
- a wireless communication method used for a mobile phone such as 3G or W-CDMA (Wideband Code Division Multiple Access) may be used.
- the wireless communication processing unit 316 is a part that transmits / receives contents and control commands to / from the wireless access point 22 and other AV devices connected by a wireless LAN. Not only wireless LAN Other parts are the same as those of the DTV 100 and the HDD recorder 200.
- the PC 400 may have the same configuration.
- the mobile phone 500 includes a tuner 501, a descrambler 502, a demultiplexer 503, a decoder 504, a display unit / speaker 505, a digital terminal 506, a camera imaging unit 507, a communication processing unit 508, an input processing unit 509, a device authentication processing unit 510, A device information management unit 511, a recording / playback processing unit 512, a recording memory 513, an encryption / decryption processing unit 514, a wireless encryption / decryption processing unit 515, a wireless communication processing unit 516, and a control unit 517 are configured.
- the camera imaging unit 507 is a part that captures images with a camera.
- the recording memory 513 is a non-volatile memory that stores information such as moving images / still images captured by the camera imaging unit 507, programs received via the tuner 501, personal information, address book, and the like. A built-in or removable memory form is conceivable. Other parts are the same as those of the DTV 100, HDD recorder 200, and PC 300.
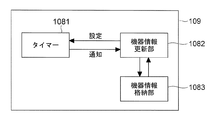
- the device information management unit 109 includes a timer 1081, a device information update unit 1082, and a device information storage unit 1083.
- the timer 1081 is used when the device authentication processing unit 108 (same for 202, 308, and 510) confirms whether or not an authentication partner device exists in the home, or a registration stored in the device information storage unit 1083 described later. This is the part used for time measurement when managing the expiration date of information.
- the device information update unit 1082 is a part that manages the expiration date of registration information held in a device information storage unit 1083 described later, and performs registration / update / deletion as necessary.
- the device information storage unit 1083 is a part that holds information related to the authentication partner device when the device authentication processing unit 108 succeeds in device authentication.
- the device information 70 includes a management table 700 and a device information table 710.
- the management table 700 includes a maximum device authentication maximum number 701, a counter maximum value 702, and an external access maximum number 703.
- the maximum device authentication maximum number 701 indicates the maximum number that device authentication can be performed between the content transmission device and the reception device using the device authentication processing unit 108.
- the maximum counter value 702 indicates the maximum counter value set in the timer 1081.
- the external access maximum number 703 indicates the maximum number that permits a content access request from outside the house.
- the device information table 710 includes ID 711, device ID 712, address information 713, counter value 714, remote access key 715, remote access key label 715A, and access status 716.
- ID 711 indicates the registration number of the table.
- Device ID 712 indicates an identifier for uniquely identifying each device.
- device-specific information such as a unique ID used in IEEE 1394 or a device ID used in DTCP, which is generated by a specific certificate authority and stored in advance in a nonvolatile memory when each device is manufactured. have.
- information such as a public key may be included.
- the address information 713 indicates the IP address and MAC address of each device on the network.
- the counter value 714 indicates the current value of the counter set in the timer 1081.
- the out-of-home access key 715 indicates key information used in authentication / encryption / decryption processing when content is transferred among the home, the content transmitting device, and the content receiving device outside the home.
- the remote access key label 715A indicates an identifier used to identify the remote access key 715.
- the access status 716 indicates a transfer status (for example, stop / in-home / out-of-home) between the content transmission device and the reception device.
- TCP is used as a protocol for transmission / reception of information for device authentication processing.
- the reception confirmation is received from the other device.
- a communication path capable of detecting a transmission error is secured.
- data transmission / reception for establishing and discarding a connection by TCP is omitted.
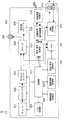
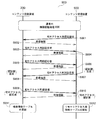
- an authentication request is created from the content receiving device 100 side.
- the device authentication processing unit 108 of the content receiving apparatus 100 attaches the device-specific information including the device ID described above to the authentication request and a certificate for the information, and sends the information to the content transmitting device 200 via the communication processing unit 111 ( S801).
- the device authentication processing unit 202 of the content transmission device 200 receives the authentication request via the communication processing unit 207 and sends the reception confirmation to the content reception device 100 (S802), the device authentication processing unit 202 of the content transmission device 200 An authentication request is generated from the user side, and the unique information of the content transmitting apparatus 200 and its certificate are attached to the content receiving apparatus 100 in the same manner as in the case of the content receiving apparatus (S803).
- the device authentication processing unit 108 of the content receiving apparatus 100 receives the authentication request and sends a reception confirmation to the content transmitting apparatus 100 (S804).
- the device authentication processing unit 202 of the content transmitting apparatus 200 verifies each piece of information received in the authentication request, and sends an authentication response with parameters necessary for generating key information to the content receiving apparatus 100 (S805). .
- the device authentication processing unit 108 of the content receiving apparatus 100 receives the authentication response and sends the reception confirmation to the content transmitting apparatus 200 (S806), and then creates an authentication response from its own side, as in the case of the content transmitting apparatus. Is sent to the content transmission apparatus 200 with a parameter necessary for generating key information (S807), and an authentication key common to the content transmission apparatus 200 is generated using the necessary parameter.
- the device authentication processing unit 202 of the content transmitting apparatus 200 receives the authentication response and sends a reception confirmation to the content receiving apparatus 100 (S808), and uses the necessary parameters in common with the content receiving apparatus 100 as in the case of the content receiving apparatus. Generate an authentication key.
- the device authentication processing unit 108 of the content transmitting device 200 and the device authentication processing unit 202 of the content receiving device generate and share a common authentication key.
- the content transmitting apparatus 200 transmits to the content receiving apparatus 100 that preparation for in-home confirmation is performed in order to confirm whether the content receiving apparatus 100 is a device existing in the house (S809).
- the device authentication processing unit 108 of the content receiving apparatus 100 receives the notification of the in-home confirmation preparation and sends the reception confirmation to the content transmitting apparatus 200 (S810), it creates the in-home confirmation preparation notification from its own side and transmits the content.
- the data is sent to the apparatus 200 (S811).
- the device authentication processing unit 202 of the content transmitting apparatus 200 When the device authentication processing unit 202 of the content transmitting apparatus 200 receives the notification of the in-home confirmation preparation and sends the reception confirmation to the content receiving apparatus 100 (S812), it sends the in-home confirmation setting request with the information necessary for in-home confirmation to the content. The data is sent to the receiving apparatus 100 (S813).
- the device authentication processing unit 108 of the content receiving apparatus 100 receives the home confirmation setting request, makes preparations necessary for home confirmation, and sends the reception confirmation to the content transmitting apparatus 200 (S814).
- the device authentication processing unit 202 of the content transmission device 200 Upon receiving the reception confirmation, the device authentication processing unit 202 of the content transmission device 200 activates the timer 1081 in the device information management unit 203 and then checks whether the content reception device 100 exists in the home. Is sent to the content receiving apparatus 100 (S815).
- the device authentication processing unit 108 of the content receiving apparatus 100 receives the in-home confirmation execution request and sends the reception confirmation to the content transmitting apparatus 200 (S816).
- the device authentication processing unit 202 of the content transmission apparatus 200 stops the timer 1081, and a measured value (T1) from when the in-home confirmation execution request is issued until the reception confirmation is received is a predetermined value. Confirm that (T) is not exceeded.
- measurement value (T1) ⁇ predetermined value (T) it is determined that content receiving apparatus 100 exists in the home and is within the range of personal use, and content receiving apparatus 100 is the home confirmation result. (S817).
- measured value (T1)> predetermined value (T) content receiving apparatus 100 determines that there is a possibility that it exists outside the house, interrupts the subsequent processing, and ends the device authentication processing. .
- the device authentication processing unit 108 of the content receiving device 100 that has received the in-home confirmation result sends a reception confirmation to the content transmitting device 200 (S818), and the device authentication processing unit 202 of the content transmitting device 200 encrypts the content.
- An exchange key to be used is generated, the exchange key is encrypted using the authentication key, and sent to the content receiving apparatus 100 together with an ID for identifying the exchange key (S819).
- the device authentication processing unit 108 of the content receiving apparatus 100 decrypts the exchange key transmitted from the content transmitting apparatus 200 using the authentication key, and sends a reception confirmation (S820).
- the device authentication processing unit 202 of the content transmitting device 200 registers information related to the content receiving device 100 in the device information table 710 in the device information management unit 203 (S821). For example, as shown in the record 721 of ID 711 in the device information table 710, the device ID of the content receiving apparatus 100 received in S801 is set to the device ID 712, and the MAC address of the content receiving apparatus 100 on the network is set as address information. Then, the counter maximum value 702 in the management table 700 is set to the counter value 714, and “stop” is set to the access status 716.
- the device authentication processing unit 202 of the content transmitting device 200 and the device authentication processing unit 108 of the content receiving device 100 share a common exchange key.
- the exchange key is used to generate a common key for encrypting / decrypting content.
- a well-known key generation / key exchange algorithm may be used to generate the authentication key, exchange key, and common key. Further, the processes of S809 and S813 and the processes of S817 and S819 may be summarized.
- the above procedure explained the device authentication process executed between the content transmitting device and the content receiving device when transferring content at home.
- the device authentication processing procedure for remote access executed between the HDD recorder 200 (content transmitting device) and the mobile phone 500 (content receiving device) is shown in FIG. It explains using.
- the content transmission device 200 and the content reception device 500 perform the device authentication process 800 described with reference to FIG.
- the device authentication processing unit 510 of the content receiving device 500 creates an out-of-home access authentication request and sends it to the content transmitting device 200 (S901).
- the remote access authentication request may include a random number generated using a predetermined calculation algorithm, the device-specific information, or the like.
- the device authentication processing unit 202 of the content transmitting apparatus 200 receives the authentication request for outside access and sends the reception confirmation to the content receiving apparatus 500 (S902), the outside of the house from the own side as in the case of the content receiving apparatus.
- An access authentication request is created and sent to the content receiving apparatus 500 (S903).
- the device authentication processing unit 510 of the content receiving device 500 receives the out-of-home access authentication request and sends a reception confirmation to the content transmitting device 200 (S904).
- the device authentication processing unit 202 of the content transmitting apparatus 200 verifies each information received in the remote access authentication request, and receives the remote access authentication response with the parameters necessary for generating the key information.
- the data is sent to the device 500 (S905).
- the device authentication processing unit 510 of the content receiving device 500 receives the remote access authentication response and sends the reception confirmation to the content transmitting device 200 (S906), and then creates an external access authentication response from its own side.
- the remote access authentication response with the parameters necessary for generating the key information is sent to the content transmission apparatus 200 (S907), and the necessary parameters are used in common with the content transmission apparatus 200. Generate an authentication key.
- the device authentication processing unit 202 of the content transmission device 200 receives the authentication response for outside access and sends the reception confirmation to the content reception device 500. Similar to the content reception device 500, the device authentication processing unit 202 uses the necessary parameters in common with the content reception device 500. The authentication key is generated (S908). Then, the device authentication processing unit 202 of the content transmitting device 200 generates an out-of-home access key dedicated to the content receiving device 500 for use in device authentication processing and content encryption when using content from outside the home, in S908. Using the generated authentication key, an out-of-home access key is encrypted and sent to the content receiving apparatus 500 (S909).
- the device authentication processing unit 510 of the content receiving device 500 Upon receiving the remote access key, the device authentication processing unit 510 of the content receiving device 500 sends a reception confirmation to the content transmitting device 200 (S910), and decrypts the remote access key using the authentication key.
- the device authentication processing unit 202 of the content transmission device 200 Upon receiving the reception confirmation, the device authentication processing unit 202 of the content transmission device 200 adds information related to the content reception device 500 to the device information table 710 in the device information management unit 203 (S911). For example, as shown in the record 722 of ID 711 in the device information table 710, the ID 711, the device ID 712, the address information 713, the counter value 714, and the access status 716 are set as described above, and additionally, the content receiving device 500 The remote access key sent to the remote access key 715 is set.
- the device authentication processing unit 510 of the content receiving device 500 generates or updates the remote access information table 1000 stored in the device information management unit 511 (S912).
- the remote access information table 1000 held in the device information management unit 511 includes address information 1001, registration information 1002, and an external access common key 1003.
- Address information 1001 registers address information necessary for the content receiving device 500 to access the content transmitting device 200 and the router 12 from outside the home, such as a MAC address, an IP address, and a port number.
- the registration information 1002 registers a user name and password necessary for the content receiving device 500 to log in to the content transmitting device 200 and the router 12 from outside the house.
- the external access common key 1003 sets the remote access key received in S910.
- the content transmission device 200 and the content reception device 500 perform normal device authentication and then use the content stored in the content transmission device 200 from outside the house in response to a request from the content reception device 500.
- the remote access key generated by the content transmitting apparatus 200 is a common key dedicated to the content receiving apparatus 500 and cannot be applied to other content receiving apparatuses.
- the outside access key is used to generate a common key for device authentication processing executed at the time of content delivery request from outside the home and / or content encryption.
- a well-known key generation / key exchange algorithm may be used to generate the authentication key, exchange key, and remote access key.
- the processing of S903 to S908 is omitted, and the remote access key is encrypted using the authentication key shared in the normal device authentication processing 800 in S909 and transmitted to the content receiving apparatus 500.
- the content transmission device 200 provides a time during which the remote access authentication request can be accepted, and the content reception device 500 issues the remote access authentication request within a predetermined time. It may be necessary to do.
- the processing of S901 to S902 may be performed immediately before S819 in the normal device authentication processing 800. In this case, S909 to S910 are executed after S820, or one processing of S819 and S909 is performed. You may put together.
- the user A takes the mobile phone 500 out of the house, and uses the mobile phone (content receiving device) 500 from the outside B to view the content recorded in the HDD 205 of the HDD recorder (content transmitting device) 200.
- the procedure in this case will be described with reference to FIG.
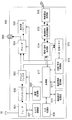
- the control unit 517 of the mobile phone 500 displays the content transmission device list screen (FIG. 15) on the display unit / speaker 505. To do.
- the content transmission device list screen 1500 is registered in the recording memory 513, the content transmission device (DTV 600) that is detected to be present on the network, and the remote access information table 1000 managed by the device information management unit 511.
- the content transmission device 200 is displayed (S1101).
- a UDP packet including a “request for detection of a device having a content transmission function” is multicast-transmitted to all apparatuses on the network.
- a method of recognizing the content transmission device by returning only the device having the function may be used, for example, SSDP (Simple Service Discovery) Protocol or DLNA (Digital Living Network Alliance).
- the control unit 517 of the content reception device 500 displays the content reception device 500 registered in the remote access information table 1000.
- a content information acquisition request is sent from the wireless communication processing unit 516 to the content transmitting apparatus 200 of the user A's home 1 via the Internet 3 via the wireless access point 22 and the router 21 (S1102).
- the control unit 211 of the content transmission device 200 sends a reception confirmation to the content reception device 500 via the communication control unit 207 (S1103), and information about part or all of the content stored in the HDD 205 (for example, title, date, Copy control information, recording time, etc.) are sent to the content receiving apparatus 500 (S1104).
- the control unit 517 of the content receiving device 500 sends a reception confirmation to the content transmitting device 200 (S1105), and displays the received content information on the display unit / speaker 505 as a content list screen (FIG. 16).
- the device authentication processing unit 510 of the content receiving apparatus 500 creates an out-of-home authentication request.
- the remote authentication request is sent to the content transmission apparatus 200 with the device-specific information including the device ID, the remote access key or a calculated value generated using the key, and a certificate (S1107). .
- the device authentication processing unit 202 of the content transmission device 200 receives the out-of-home authentication request, the device ID of the content reception device 500 is registered in the device information table 710 managed in the device information management unit 203. Then, the reception confirmation is sent to the content receiving apparatus 500 (S1108). If the device ID of the content receiving device 500 is not registered in the device information table 710, the content transmitting device 100 interrupts the subsequent processing.
- the device authentication processing unit 202 of the content transmitting apparatus 200 creates an out-of-home authentication request from its own side, and, similarly to the content receiving apparatus, the unique information of the content transmitting apparatus 200 and the out-of-home access key Alternatively, the calculated value generated using the key and a certificate are attached and sent to the content receiving apparatus 500 (S1109).
- the device authentication processing unit 510 of the content receiving device 500 receives the out-of-home authentication request and sends a reception confirmation to the content transmitting device 200 (S1110).
- the device authentication processing unit 202 of the content transmitting apparatus 200 verifies each piece of information received in the outside authentication request, generates the outside access key or a calculated value generated using the key, and generates key information.
- An out-of-home authentication response with necessary parameters is sent to the content receiving apparatus 500 (S1111).
- the device authentication processing unit 510 of the content receiving device 500 receives the remote authentication response and sends the reception confirmation to the content transmitting device 200 (S1112). Then, the device authentication processing unit 510 creates an external authentication response from its own side and transmits the content. As in the case of the apparatus, an out-of-home authentication response with parameters necessary for generating key information is sent to the content transmitting apparatus 200 (S1113), and the out-of-home authentication key shared with the content transmitting apparatus 200 using the necessary parameters Is generated.
- the device authentication processing unit 202 of the content transmission device 200 receives the out-of-home authentication response and sends a reception confirmation to the content reception device 500. Similar to the content reception device, the device authentication processing unit 202 uses the necessary parameters in common with the content reception device 500. An authentication key is generated (S1114). Then, after confirming that the counter value 714 of the content receiving device 500 in the device information table 710 is not 0 (S1115), an exchange key for outside the home used for encrypting the content is generated, and the home information The external exchange key is encrypted using the external authentication key, and is sent to the content receiving apparatus 500 together with an ID for identifying the external exchange key (S1116).
- the device authentication processing unit 510 of the content reception device 500 decrypts the remote exchange key transmitted from the content transmission device 200 using the remote authentication key, and sends a reception confirmation (S1117).
- the device authentication processing unit 202 of the content transmission device 200 Upon receiving the reception confirmation, the device authentication processing unit 202 of the content transmission device 200 updates the information related to the content reception device 500 in the device information table 710 in the device information management unit 203 (S1118). Specifically, the access status 716 is updated from “stop” to “outside home”.
- control unit 517 of the content receiving device 500 transmits a viewing request for the desired content to the content transmitting device 200 (S1119).
- an ID for identifying the remote exchange key received in S1116 may be added to the viewing request.
- the control unit 211 of the content transmitting apparatus 200 sends a reception confirmation in response to the content viewing request (S1120), the device authentication processing unit 202 checks whether the identification ID of the remote exchange key is correct, and the device information update unit 1082 The timer 1081 in the device information management unit 203 is set to be notified periodically (for example, every 1 minute interval, 10 minute interval, etc.) and started. In addition, the device authentication processing unit 202 generates a common key for encrypting content using the remote exchange key, and sets the common key in the encryption / decryption processing unit 206.
- the desired content read from the HDD 205 is sent to the content receiving device 500 while being encrypted by the encryption / decryption processing unit 206 (S1121).
- the device information update unit 1082 updates the counter value 714 in the device information table 710 (for example, decrements the counter value).
- the device authentication processing unit 510 of the content receiving apparatus 500 generates a common key for decrypting the content using the remote exchange key, and sets the common key in the encryption / decryption processing unit 514. Then, the content received via the wireless communication processing unit 516 and the wireless encryption / decryption processing unit 515 is decrypted by the encryption / decryption processing unit 514 and output to the display unit / speaker 505 while being decoded by the decoder 504.
- the device authentication processing 900 for outside access is performed between the content transmitting device and the content receiving device in advance in the home and the content receiving device that has succeeded in the authentication processing is taken out of the home. If the external authentication processes S1107 to S1117 are executed successfully, the content can be transferred from the home content transmitting device to the external content receiving device. When the content transfer is completed, the content transmission device stops the timer 1081, discards the remote exchange key, and even if the content reception device continues to issue another content viewing request, the home-only authentication process is performed again. You may make it not transmit unless it performs.
- the content transmitting apparatus can limit the number of content receiving apparatuses that can be simultaneously accessed from outside the house by using the maximum external access number 703 in the management table 700.
- the content transmitting apparatus 200 has received the “view request” for the content. However, if other requests such as “copy request” or “move request” are received from outside the house, the content is illegally used. You may make it refuse to avoid as much as possible.
- the protocol used for transmitting content from the content transmitting apparatus 200 to the content receiving apparatus 500 is not limited to a specific protocol, and RTP, HTTP, FTP, or the like can be used.
- the content encrypted by a predetermined algorithm using a common key in the payload portion of each transfer protocol may be accommodated and transmitted.
- an encryption algorithm for example, AES (Advanced Encryption Standard) which is a well-known encryption technique may be used.
- the counter value 714 in the device information table 710 that is periodically updated by the content transmission apparatus can be shared at the time of content transmission both inside and outside the house, but as shown in FIG. It is also possible to use different counter values outside the house.
- the maximum values set for the respective counter values may be different values (that is, the maximum counter value 702 for home use and the maximum counter value for home use 704 in the management table 700).
- a content receiving device that accesses a home device from outside the home performs a normal device authentication process and a device authentication process for home access in advance with the content transmitting device in the home in advance.
- the information about the content receiving device is registered in the device information table of the content transmitting device.
- a feature of the present embodiment is that it enables viewing of in-home content with an unspecified content receiving device on the go while preventing unauthorized viewing / duplication without exceeding the range of personal use of the content. is there.
- FIG. 13 shows an example of a system configuration.
- a user A takes a mobile phone 500 to the outside, and uses a large-screen DTV 600 installed at the same place as the mobile phone 500 to use the HDD recorder 200 at home. It is assumed that the content is viewed.
- the DTV 600 has the same configuration as the DTV 100.
- the user A executes the remote home access device authentication 900 between the HDD recorder 200 (content transmission device) and the mobile phone 500 at home, and the remote access key between the two. Share it.
- the user A takes the mobile phone 500 to the outside (hotel or the like) and views the content in the house with the DTV 600 in the same place
- the user A and the content transmitting apparatus 200 are in the same procedure as S1101 to S1118 in FIG. Acquisition of content information with the mobile phone 500 and device authentication processing for exclusive use outside the home are executed.
- the control unit 517 of the mobile phone 500 transmits to all devices on the network.
- a UDP packet including a “request for detection of a device having a playback function” is multicasted, and only a device having the function returns, for example, other networks on the network using the well-known technology such as DLNA. It is detected whether or not a content reproduction apparatus exists, and if it exists, a content reproduction apparatus list screen (FIG. 17) is displayed on the display unit / speaker 505.
- the control unit 517 sends a content viewing issuance request to the DTV 600 (S1401).
- the content viewing issuance request includes information regarding the content to be viewed and the address information 1001 of the content transmitting apparatus 200 registered in the remote access information table 1000, and registration information 1002 may be attached depending on circumstances.
- the DTV 600 (content receiving device) that has received the content viewing issuance request sends a reception confirmation to the controller 500 (S1402), and performs a normal device authentication process 800 with the controller 500.
- the device authentication processing unit 510 of the controller 500 uses the remote exchange key shared with the content transmitting apparatus 200 in S1116 and the identification ID as the exchange key and identification ID sent to the DTV 600 in S819.
- the same remote exchange key and the identification ID of the exchange key can be shared among the content transmitting apparatus 200, the controller 500, and the content receiving apparatus 600.
- the DTV 600 sends a content viewing request to the content transmitting apparatus 200 (S1403).
- the identification ID of the remote exchange key is added to the content viewing request.
- a data format that can be played back by the DTV 600 for example, MPEG2-TS, H.264, etc.
- Information on image quality can also be included in the content viewing request. It may be issued by a request different from the content viewing request.
- the control unit 211 of the content transmitting apparatus 200 Upon receiving the content viewing request, the control unit 211 of the content transmitting apparatus 200 sends a reception confirmation to the DTV 600 (S1404). Then, the device authentication processing unit 202 checks that the identification ID of the remote exchange key is correct, the device information update unit 1082 sets the timer 1081 in the device information management unit 203 to be notified periodically, to start.
- the device authentication processing unit 202 generates a common key for encrypting content using the remote exchange key, and sets the common key in the encryption / decryption processing unit 206.
- the desired content read from the HDD 205 is sent to the DTV 600 while being encrypted by the encryption / decryption processing unit 206 (S1405).
- the device information update unit 1082 updates the counter value 714 in the device information table 710.
- the DTV 600 generates a common key for decrypting the content using the remote exchange key, and sets the common key in the encryption / decryption processing unit 110. Then, the content received via the router 21 and the communication processing unit 111 is decrypted by the encryption / decryption processing unit 110 and output to the display unit / speaker 105 while being decoded by the decoder 104.
- the exchange key for home use can be shared between the content transmission device and the controller In such a case, the controller can pass the remote exchange key to the content receiving apparatus outside the home that has succeeded in the normal authentication process.
- the content transmitting apparatus 200 transmits an outdoor exchange key necessary for content encryption only to the controller 500. Therefore, the key exchange (normal device authentication processing 800) between the controller 500 and the content receiving device 600 is not involved.
- the feature of the present embodiment is that the controller 500 notifies the content transmitting apparatus 200 that the remote exchange key has been delivered to the content receiving apparatus 600.
- a proxy device ID 718 for setting a device ID of another device that receives content instead of the device indicated by the device ID 712 is set.
- proxy address information MAC address, IP address, etc.
- proxy counter value may be added.
- the controller 500 issues an external device setting request for content reception to the content transmission device 200 using a device-authenticated external device (in this case, the content reception device 600) instead of its own device ( S1900).
- the setting request includes information related to the content receiving device 600-such as a device ID and a MAC address.
- the content transmitting apparatus 200 that has received the external device setting request sets the device ID of the content receiving device 600 included in the request to the proxy device ID 718 in the device information table 710 (S1901), and the reception confirmation is performed by the controller. 500 is issued (S1902).
- the content reception device 600 issues a content viewing request to the content transmission device 200 (S1403).
- the viewing request includes the device ID or address information (MAC address, IP address, etc.) of the content receiving device 600.
- the content transmitting apparatus 200 that has received the content viewing request confirms whether or not the request is issued from the proxy device ID 718, and then issues a reception confirmation to the content receiving apparatus 600, using the remote exchange key. Transfer encrypted content.
- the content transmitting device 200 interrupts the content transmission to the content receiving device 600.
Landscapes
- Engineering & Computer Science (AREA)
- Signal Processing (AREA)
- Multimedia (AREA)
- Computer Security & Cryptography (AREA)
- Computer Networks & Wireless Communication (AREA)
- Databases & Information Systems (AREA)
- Computing Systems (AREA)
- Computer Hardware Design (AREA)
- General Engineering & Computer Science (AREA)
- Automation & Control Theory (AREA)
- Computer Graphics (AREA)
- Human Computer Interaction (AREA)
- Two-Way Televisions, Distribution Of Moving Picture Or The Like (AREA)
- Storage Device Security (AREA)
Priority Applications (4)
| Application Number | Priority Date | Filing Date | Title |
|---|---|---|---|
| EP09723087.4A EP2267936B1 (en) | 2008-03-17 | 2009-02-16 | Content transmission device and content reception device |
| US12/746,876 US8984646B2 (en) | 2008-03-17 | 2009-02-16 | Content transmission device and content reception device |
| CN2009801012910A CN101889413A (zh) | 2008-03-17 | 2009-02-16 | 内容发送装置、内容接收装置 |
| US14/575,902 US20150106954A1 (en) | 2008-03-17 | 2014-12-18 | Content transmission device and content reception device |
Applications Claiming Priority (2)
| Application Number | Priority Date | Filing Date | Title |
|---|---|---|---|
| JP2008-066964 | 2008-03-17 | ||
| JP2008066964A JP5331354B2 (ja) | 2008-03-17 | 2008-03-17 | コンテンツ送信装置、コンテンツ受信装置 |
Related Child Applications (2)
| Application Number | Title | Priority Date | Filing Date |
|---|---|---|---|
| US12/746,876 A-371-Of-International US8984646B2 (en) | 2008-03-17 | 2009-02-16 | Content transmission device and content reception device |
| US14/575,902 Continuation US20150106954A1 (en) | 2008-03-17 | 2014-12-18 | Content transmission device and content reception device |
Publications (1)
| Publication Number | Publication Date |
|---|---|
| WO2009116338A1 true WO2009116338A1 (ja) | 2009-09-24 |
Family
ID=41090746
Family Applications (1)
| Application Number | Title | Priority Date | Filing Date |
|---|---|---|---|
| PCT/JP2009/052504 Ceased WO2009116338A1 (ja) | 2008-03-17 | 2009-02-16 | コンテンツ送信装置、コンテンツ受信装置 |
Country Status (5)
| Country | Link |
|---|---|
| US (2) | US8984646B2 (enExample) |
| EP (1) | EP2267936B1 (enExample) |
| JP (1) | JP5331354B2 (enExample) |
| CN (1) | CN101889413A (enExample) |
| WO (1) | WO2009116338A1 (enExample) |
Cited By (4)
| Publication number | Priority date | Publication date | Assignee | Title |
|---|---|---|---|---|
| JP2010268174A (ja) * | 2009-05-14 | 2010-11-25 | Hitachi Ltd | コンテンツ送信装置及びコンテンツ受信装置 |
| JP2011082952A (ja) * | 2009-09-09 | 2011-04-21 | Sony Corp | 通信システム、通信装置及び通信方法、並びにコンピューター・プログラム |
| WO2011052121A1 (ja) * | 2009-10-30 | 2011-05-05 | パナソニック株式会社 | Avデータ受信装置、avデータ受信方法及びavデータ送受信システム |
| US8589970B2 (en) | 2009-05-14 | 2013-11-19 | Hitachi Consumer Electronics Co., Ltd. | Content transmitter and receiver apparatus and content transmitting and receiving method |
Families Citing this family (28)
| Publication number | Priority date | Publication date | Assignee | Title |
|---|---|---|---|---|
| JP5527815B2 (ja) * | 2010-05-07 | 2014-06-25 | 日立コンシューマエレクトロニクス株式会社 | コンテンツ送信装置及びコンテンツ受信装置、コンテンツ送信方法、コンテンツ受信方法 |
| JP5614016B2 (ja) * | 2009-09-09 | 2014-10-29 | ソニー株式会社 | 通信システム、通信装置及び通信方法、コンピューター・プログラム、並びに、コンテンツ提供装置及びコンテンツ提供方法 |
| CN102340496B (zh) * | 2010-07-28 | 2014-08-13 | 鸿富锦精密工业(深圳)有限公司 | 数字媒体控制器及利用其共享网络间媒体内容的方法 |
| WO2012040840A1 (en) * | 2010-09-17 | 2012-04-05 | Certicom Corp. | A mechanism for managing authentication device lifecycles |
| US8955078B2 (en) * | 2011-06-30 | 2015-02-10 | Cable Television Laboratories, Inc. | Zero sign-on authentication |
| DE102011081804B4 (de) * | 2011-08-30 | 2015-02-12 | Siemens Aktiengesellschaft | Verfahren und System zum Bereitstellen von gerätespezifischen Betreiberdaten, welche an ein Authentisierungs-Credential gebunden werden, für ein Automatisierungsgerät einer Automatisierungsanlage |
| US20130347025A1 (en) * | 2011-11-30 | 2013-12-26 | Intel Corporation | Providing remote access via a mobile device to content subject to a subscription |
| JP5774976B2 (ja) * | 2011-12-12 | 2015-09-09 | 日立マクセル株式会社 | コンテンツ送信装置及びコンテンツ送信方法 |
| TW201327370A (zh) * | 2011-12-28 | 2013-07-01 | Amtran Technology Co Ltd | 資源分享系統與方法及其播放裝置 |
| US20130191626A1 (en) | 2012-01-23 | 2013-07-25 | Panasonic Corporation | Recording device, terminal device, and content transmission system |
| US9571282B1 (en) | 2012-04-03 | 2017-02-14 | Google Inc. | Authentication on a computing device |
| JP5373151B2 (ja) * | 2012-05-21 | 2013-12-18 | シャープ株式会社 | 情報処理装置、情報処理装置の制御方法、被制御装置、被制御装置の制御方法、サーバ、サーバの制御方法、ペアリングシステム、制御プログラム、および記録媒体 |
| JP5856015B2 (ja) * | 2012-06-15 | 2016-02-09 | 日立マクセル株式会社 | コンテンツ送信装置 |
| TW201427366A (zh) * | 2012-12-28 | 2014-07-01 | Ibm | 企業網路中為了資料外洩保護而解密檔案的方法與資訊裝置 |
| US9038142B2 (en) | 2013-02-05 | 2015-05-19 | Google Inc. | Authorization flow initiation using short-term wireless communication |
| US11070860B2 (en) | 2013-02-14 | 2021-07-20 | Comcast Cable Communications, Llc | Content delivery |
| CN103152624A (zh) * | 2013-02-26 | 2013-06-12 | 中兴通讯股份有限公司 | 遥控处理方法、装置及系统 |
| US9203832B2 (en) | 2013-03-12 | 2015-12-01 | Cable Television Laboratories, Inc. | DTCP certificate authentication over TLS protocol |
| JP5865939B2 (ja) * | 2014-04-09 | 2016-02-17 | 日立マクセル株式会社 | コンテンツ送信装置及びコンテンツ送信方法 |
| US10440499B2 (en) | 2014-06-16 | 2019-10-08 | Comcast Cable Communications, Llc | User location and identity awareness |
| US10045090B2 (en) * | 2014-08-11 | 2018-08-07 | Comcast Cable Communications, Llc | Merging permissions and content access |
| US20160110555A1 (en) * | 2014-10-21 | 2016-04-21 | Institute For Information Industry | Resource sharing apparatus, method, and non-transitory computer readable storage medium thereof |
| CN104320421A (zh) * | 2014-11-18 | 2015-01-28 | 上海凌云天博光电科技有限公司 | 为MoCA设备端口设置MAC数量限制值的方法及装置 |
| JP2016177417A (ja) * | 2015-03-19 | 2016-10-06 | Nttエレクトロニクス株式会社 | 処理装置及び遠隔管理システム |
| JP6039046B2 (ja) * | 2015-12-10 | 2016-12-07 | 日立マクセル株式会社 | コンテンツ送信装置 |
| JP6064026B2 (ja) * | 2015-12-24 | 2017-01-18 | 日立マクセル株式会社 | コンテンツ送受信装置及びそれに適用されるコンテンツ送信方法 |
| JP6925907B2 (ja) * | 2017-08-09 | 2021-08-25 | オムロンヘルスケア株式会社 | データ送信装置、データ受信装置、方法及びプログラム |
| WO2024048045A1 (ja) * | 2022-08-31 | 2024-03-07 | パナソニックIpマネジメント株式会社 | 端末装置、録画管理システム、管理サーバ装置、制御方法、およびプログラム |
Citations (5)
| Publication number | Priority date | Publication date | Assignee | Title |
|---|---|---|---|---|
| JP2004180020A (ja) * | 2002-11-27 | 2004-06-24 | Toshiba Corp | 通信中継装置、通信システム及び通信制御プログラム |
| JP2005005821A (ja) | 2003-06-10 | 2005-01-06 | Hitachi Ltd | コンテンツ送信装置、コンテンツ受信装置およびコンテンツ伝送方法 |
| JP2005102021A (ja) * | 2003-09-26 | 2005-04-14 | Renesas Technology Corp | 端末装置、そのプログラム及び認証処理を行う記憶装置 |
| JP2005269288A (ja) * | 2004-03-19 | 2005-09-29 | Hitachi Ltd | コンテンツ送信装置、コンテンツ受信装置およびコンテンツ伝送方法 |
| JP2007220095A (ja) * | 2006-02-15 | 2007-08-30 | Samsung Electronics Co Ltd | 遠隔ドメインのデバイスでdrmコンテンツをローミングして使用する方法及び装置 |
Family Cites Families (10)
| Publication number | Priority date | Publication date | Assignee | Title |
|---|---|---|---|---|
| US5638448A (en) * | 1995-10-24 | 1997-06-10 | Nguyen; Minhtam C. | Network with secure communications sessions |
| TWI348450B (en) * | 2003-11-13 | 2011-09-11 | Applied Materials Inc | Break-away positioning conveyor mount for accommodating conveyor belt bends |
| US20050198506A1 (en) * | 2003-12-30 | 2005-09-08 | Qi Emily H. | Dynamic key generation and exchange for mobile devices |
| JP4608886B2 (ja) * | 2004-01-16 | 2011-01-12 | 株式会社日立製作所 | コンテンツ送信装置および方法 |
| JP4982031B2 (ja) * | 2004-01-16 | 2012-07-25 | 株式会社日立製作所 | コンテンツ送信装置、コンテンツ受信装置およびコンテンツ送信方法、コンテンツ受信方法 |
| US8028164B2 (en) * | 2004-03-19 | 2011-09-27 | Nokia Corporation | Practical and secure storage encryption |
| JP4421981B2 (ja) | 2004-09-09 | 2010-02-24 | パイオニア株式会社 | コンテンツ遠隔視聴システム、コンテンツ遠隔視聴用サーバ装置、コンテンツ遠隔視聴用記録再生装置、及びコンテンツ遠隔視聴方法、並びにコンピュータプログラム |
| JP2006323707A (ja) * | 2005-05-20 | 2006-11-30 | Hitachi Ltd | コンテンツ送信装置、コンテンツ受信装置、コンテンツ送信方法及びコンテンツ受信方法 |
| US7822863B2 (en) | 2006-05-12 | 2010-10-26 | Palo Alto Research Center Incorporated | Personal domain controller |
| JP4962117B2 (ja) * | 2007-04-25 | 2012-06-27 | コニカミノルタホールディングス株式会社 | 暗号通信処理方法及び暗号通信処理装置 |
-
2008
- 2008-03-17 JP JP2008066964A patent/JP5331354B2/ja active Active
-
2009
- 2009-02-16 WO PCT/JP2009/052504 patent/WO2009116338A1/ja not_active Ceased
- 2009-02-16 US US12/746,876 patent/US8984646B2/en active Active
- 2009-02-16 EP EP09723087.4A patent/EP2267936B1/en active Active
- 2009-02-16 CN CN2009801012910A patent/CN101889413A/zh active Pending
-
2014
- 2014-12-18 US US14/575,902 patent/US20150106954A1/en not_active Abandoned
Patent Citations (5)
| Publication number | Priority date | Publication date | Assignee | Title |
|---|---|---|---|---|
| JP2004180020A (ja) * | 2002-11-27 | 2004-06-24 | Toshiba Corp | 通信中継装置、通信システム及び通信制御プログラム |
| JP2005005821A (ja) | 2003-06-10 | 2005-01-06 | Hitachi Ltd | コンテンツ送信装置、コンテンツ受信装置およびコンテンツ伝送方法 |
| JP2005102021A (ja) * | 2003-09-26 | 2005-04-14 | Renesas Technology Corp | 端末装置、そのプログラム及び認証処理を行う記憶装置 |
| JP2005269288A (ja) * | 2004-03-19 | 2005-09-29 | Hitachi Ltd | コンテンツ送信装置、コンテンツ受信装置およびコンテンツ伝送方法 |
| JP2007220095A (ja) * | 2006-02-15 | 2007-08-30 | Samsung Electronics Co Ltd | 遠隔ドメインのデバイスでdrmコンテンツをローミングして使用する方法及び装置 |
Cited By (6)
| Publication number | Priority date | Publication date | Assignee | Title |
|---|---|---|---|---|
| JP2010268174A (ja) * | 2009-05-14 | 2010-11-25 | Hitachi Ltd | コンテンツ送信装置及びコンテンツ受信装置 |
| US8589970B2 (en) | 2009-05-14 | 2013-11-19 | Hitachi Consumer Electronics Co., Ltd. | Content transmitter and receiver apparatus and content transmitting and receiving method |
| JP2011082952A (ja) * | 2009-09-09 | 2011-04-21 | Sony Corp | 通信システム、通信装置及び通信方法、並びにコンピューター・プログラム |
| WO2011052121A1 (ja) * | 2009-10-30 | 2011-05-05 | パナソニック株式会社 | Avデータ受信装置、avデータ受信方法及びavデータ送受信システム |
| JP5266396B2 (ja) * | 2009-10-30 | 2013-08-21 | パナソニック株式会社 | Avデータ受信装置、avデータ受信方法及びavデータ送受信システム |
| US8605900B2 (en) | 2009-10-30 | 2013-12-10 | Panasonic Corporation | AV data receiving device, AV data receiving method, and AV data transmission and receiving system |
Also Published As
| Publication number | Publication date |
|---|---|
| EP2267936B1 (en) | 2018-11-28 |
| US20100268955A1 (en) | 2010-10-21 |
| US20150106954A1 (en) | 2015-04-16 |
| US8984646B2 (en) | 2015-03-17 |
| EP2267936A4 (en) | 2015-01-21 |
| JP2009225074A (ja) | 2009-10-01 |
| EP2267936A1 (en) | 2010-12-29 |
| CN101889413A (zh) | 2010-11-17 |
| JP5331354B2 (ja) | 2013-10-30 |
Similar Documents
| Publication | Publication Date | Title |
|---|---|---|
| JP5331354B2 (ja) | コンテンツ送信装置、コンテンツ受信装置 | |
| JP4881538B2 (ja) | コンテンツ送信装置およびコンテンツ送信方法 | |
| US10542307B2 (en) | Content transmission device and content transmission method | |
| JP6545835B2 (ja) | コンテンツ送信装置、および、そのコンテンツ送信方法 | |
| JPWO2010021110A1 (ja) | アクセス許可登録方法およびサーバ装置 | |
| WO2010035490A1 (ja) | データ送受信制御装置、データ送受信システム、方法、およびプログラム | |
| JP5439044B2 (ja) | コンテンツ送信装置及びコンテンツ受信装置 | |
| JP5372595B2 (ja) | コンテンツ送信装置及びコンテンツ受信装置 | |
| JP2016028480A (ja) | コンテンツ送信装置及びコンテンツ送信方法 | |
| JP5808965B2 (ja) | コンテンツ送信装置及びコンテンツ送信方法 | |
| JP5315542B2 (ja) | コンテンツ送信方法及びコンテンツ送信装置、コンテンツ受信方法及びコンテンツ受信装置 | |
| JP5734367B2 (ja) | コンテンツ送信装置、コンテンツ受信装置、コンテンツ送信方法およびコンテンツ受信方法 | |
| JP2012004916A (ja) | Avデータ送受信方法、avデータ受信装置、avデータ送信装置、avデータ受信方法、avデータ送信方法及びavデータ送受信システム | |
| JP2010087610A (ja) | データ送信装置、データ受信装置、データ送受信システム、方法、およびプログラム。 | |
| JP6095730B2 (ja) | コンテンツ送信装置及び方法 | |
| JP7042373B2 (ja) | コンテンツ送信装置 | |
| JP5695150B2 (ja) | コンテンツ送信装置及びコンテンツ送信方法 | |
| JP5163726B2 (ja) | コンテンツ送信装置、コンテンツ受信装置およびコンテンツ伝送方法 | |
| JP2011061644A (ja) | コンテンツ送信装置及びコンテンツ送信方法 | |
| JP2011087156A (ja) | データ送信装置、データ受信装置及びデータ送受信システム | |
| JP2014007473A (ja) | データ処理装置、通信装置、データ送信方法 | |
| JP5947411B2 (ja) | コンテンツ送信装置及びコンテンツ受信装置 | |
| JP2014042244A (ja) | コンテンツ送信装置及びコンテンツ送信方法 |
Legal Events
| Date | Code | Title | Description |
|---|---|---|---|
| WWE | Wipo information: entry into national phase |
Ref document number: 200980101291.0 Country of ref document: CN |
|
| 121 | Ep: the epo has been informed by wipo that ep was designated in this application |
Ref document number: 09723087 Country of ref document: EP Kind code of ref document: A1 |
|
| WWE | Wipo information: entry into national phase |
Ref document number: 2009723087 Country of ref document: EP |
|
| WWE | Wipo information: entry into national phase |
Ref document number: 12746876 Country of ref document: US |
|
| NENP | Non-entry into the national phase |
Ref country code: DE |