WO2023013102A1 - 情報処理装置及び情報処理方法、並びにコンピュータプログラム - Google Patents
情報処理装置及び情報処理方法、並びにコンピュータプログラム Download PDFInfo
- Publication number
- WO2023013102A1 WO2023013102A1 PCT/JP2022/003807 JP2022003807W WO2023013102A1 WO 2023013102 A1 WO2023013102 A1 WO 2023013102A1 JP 2022003807 W JP2022003807 W JP 2022003807W WO 2023013102 A1 WO2023013102 A1 WO 2023013102A1
- Authority
- WO
- WIPO (PCT)
- Prior art keywords
- application
- transaction
- information processing
- unit
- data
- Prior art date
- Legal status (The legal status is an assumption and is not a legal conclusion. Google has not performed a legal analysis and makes no representation as to the accuracy of the status listed.)
- Ceased
Links
Images
Classifications
-
- G—PHYSICS
- G06—COMPUTING OR CALCULATING; COUNTING
- G06F—ELECTRIC DIGITAL DATA PROCESSING
- G06F21/00—Security arrangements for protecting computers, components thereof, programs or data against unauthorised activity
- G06F21/30—Authentication, i.e. establishing the identity or authorisation of security principals
- G06F21/44—Program or device authentication
-
- G—PHYSICS
- G06—COMPUTING OR CALCULATING; COUNTING
- G06F—ELECTRIC DIGITAL DATA PROCESSING
- G06F21/00—Security arrangements for protecting computers, components thereof, programs or data against unauthorised activity
- G06F21/60—Protecting data
- G06F21/62—Protecting access to data via a platform, e.g. using keys or access control rules
-
- G—PHYSICS
- G06—COMPUTING OR CALCULATING; COUNTING
- G06F—ELECTRIC DIGITAL DATA PROCESSING
- G06F9/00—Arrangements for program control, e.g. control units
- G06F9/06—Arrangements for program control, e.g. control units using stored programs, i.e. using an internal store of processing equipment to receive or retain programs
- G06F9/46—Multiprogramming arrangements
- G06F9/54—Interprogram communication
- G06F9/542—Event management; Broadcasting; Multicasting; Notifications
-
- H—ELECTRICITY
- H04—ELECTRIC COMMUNICATION TECHNIQUE
- H04L—TRANSMISSION OF DIGITAL INFORMATION, e.g. TELEGRAPHIC COMMUNICATION
- H04L9/00—Cryptographic mechanisms or cryptographic arrangements for secret or secure communications; Network security protocols
- H04L9/08—Key distribution or management, e.g. generation, sharing or updating, of cryptographic keys or passwords
- H04L9/0891—Revocation or update of secret information, e.g. encryption key update or rekeying
-
- H—ELECTRICITY
- H04—ELECTRIC COMMUNICATION TECHNIQUE
- H04L—TRANSMISSION OF DIGITAL INFORMATION, e.g. TELEGRAPHIC COMMUNICATION
- H04L9/00—Cryptographic mechanisms or cryptographic arrangements for secret or secure communications; Network security protocols
- H04L9/32—Cryptographic mechanisms or cryptographic arrangements for secret or secure communications; Network security protocols including means for verifying the identity or authority of a user of the system or for message authentication, e.g. authorization, entity authentication, data integrity or data verification, non-repudiation, key authentication or verification of credentials
- H04L9/3271—Cryptographic mechanisms or cryptographic arrangements for secret or secure communications; Network security protocols including means for verifying the identity or authority of a user of the system or for message authentication, e.g. authorization, entity authentication, data integrity or data verification, non-repudiation, key authentication or verification of credentials using challenge-response
- H04L9/3273—Cryptographic mechanisms or cryptographic arrangements for secret or secure communications; Network security protocols including means for verifying the identity or authority of a user of the system or for message authentication, e.g. authorization, entity authentication, data integrity or data verification, non-repudiation, key authentication or verification of credentials using challenge-response for mutual authentication
Definitions
- this disclosure relates to an information processing apparatus and information processing method equipped with a device that performs transactions with an external device, and a computer program.
- the secure element is a device protected by tamper-resistant hardware, and enables secure contactless communication with the reader/writer using mutual authentication and encryption.
- a communication method conforming to NFC (Near Field Communication), which is a short-range wireless communication standard, or the like can be used, but a detailed description thereof will be omitted in this specification.
- service functions can be done.
- SP application an application program distributed by a provider (service provider: SP) that provides each service function, and starting the SP application.
- SP service provider
- service functions e.g. charging electronic money
- service functions e.g. display of usage history and balance
- SP application an application program
- SP application a transaction between a secure element in an information terminal and a reader/writer occurs, for example, by a manual operation in which the user holds the information terminal over the reader/writer. do not have. Therefore, in order to display the balance in the SP application, it is necessary for the SP application to grasp the transaction information between the secure element and the reader/writer.
- information related to a transaction is stored in a second storage unit in the secure element, and the data acquisition unit on the information processing device side reads the information from the second storage unit at the timing when the transaction is executed.
- an information processing apparatus that analyzes the position of the device, the surrounding situation, the user, the operation of the device, the operation of the user, and the like (see Patent Document 1).
- the transaction information analysis processing performed in the data acquisition unit is performed by middleware, and on this information processing device, it is impossible for the SP application to grasp the transaction information performed between the secure element and the reader/writer. Can not.
- An object of the present disclosure is to provide an information processing device, an information processing method, and a computer program for processing information related to transactions executed between a device in the main body and an external device.
- the present disclosure has been made in consideration of the above problems, and a first aspect thereof is an information processing device equipped with a device that performs transactions with an external device, a detection unit that detects that a transaction has occurred between the device and the external device; an acquisition unit that acquires data from the device in response to the detection of the occurrence of the transaction by the detection unit; a determination unit that analyzes the data acquired by the acquisition unit and determines an application to be notified; a verification unit that verifies the validity of the notification target application; a notification unit that notifies an appropriate application whose validity has been confirmed among the notification targets, of the data acquired by the acquisition unit; It is an information processing device comprising
- the acquisition unit acquires data to be processed for the transaction and data related to the processing of the transaction. Further, the determination unit specifies a service ID related to the transaction based on the data acquired by the acquisition unit, and determines an application to be notified based on the service ID.
- the verification unit verifies the validity of the application based on the application verification information obtained from the server and the application information obtained from the operating system.
- the verification information includes the application's package name and signature value.
- the notification unit notifies the appropriate application based on the information for each application obtained from the server.
- the information for each application acquired from the server includes at least one of priority of notification, notification time limit, and operation when the notification time limit is exceeded.
- a second aspect of the present disclosure is an information processing method in a device equipped with a device that performs transactions with an external device, comprising: a detection step of detecting that a transaction has occurred between the device and the external device; an obtaining step of obtaining data from the device in response to detecting the occurrence of the transaction in the detecting step; a determination step of analyzing the data acquired in the acquisition step and determining an application to be notified; a verification step of verifying the legitimacy of the notification target application; a notification step of notifying an appropriate application whose validity has been confirmed among the notification targets of the data acquired in the acquisition; It is an information processing method having
- a third aspect of the present disclosure provides an information processing device equipped with a device that performs transactions with an external device, a detection unit that detects that a transaction has occurred between the external devices of the device; an acquisition unit that acquires data from the device in response to the detection of the occurrence of the transaction by the detection unit; a determination unit that analyzes the data acquired by the acquisition unit and determines an application to be notified; a verification unit that verifies the validity of the notification target application; a notification unit that notifies an appropriate application whose validity has been confirmed among the notification targets of the data acquired by the acquisition unit; A computer program written in computer readable form to cause it to function as a
- a computer program according to the third aspect of the present disclosure defines a computer program written in a computer-readable format so as to implement predetermined processing on a computer.
- a cooperative action is exhibited on the computer, and the same effects as the information processing device according to the first aspect of the present disclosure are achieved.
- a fourth aspect of the present disclosure is an information processing apparatus equipped with a device that performs a transaction with an external device and installed with an application that provides a service related to the transaction, a notification unit that notifies the application of data to be processed of the transaction; a presentation unit that presents the information about the processing target data received by the application; It is an information processing device comprising
- a fifth aspect of the present disclosure is an information processing method executed by an application installed in a device installed with a device that performs a transaction with an external device and an application that provides a service related to the transaction. hand, a receiving step of receiving data to be processed of the transaction; a presentation step of presenting information about the received data to be processed; It is an information processing method having
- a sixth aspect of the present disclosure provides an information processing device equipped with a device that performs a transaction with an external device and having an application that provides services related to the transaction installed, a receiving unit that receives data to be processed of the transaction; a presentation unit that presents information about the received data to be processed; A computer program written in computer readable form to cause it to function as a
- an information processing device an information processing method, and a computer program for notifying an appropriate application of information regarding transactions performed between a device in the main body and an external device.
- FIG. 1 is a diagram showing a hardware configuration example of an information processing apparatus 100.
- FIG. FIG. 2 is a diagram showing the internal configuration of the secure element section 114.
- FIG. 3 is a diagram showing a data structure for storing transaction processing target data in the memory 204 in the secure element unit 114.
- FIG. 4 is a diagram showing a configuration example of data relating to transaction processing.
- FIG. 5 is a diagram showing a stack structure of software operating on the information processing apparatus 100.
- FIG. FIG. 6 is a diagram showing an operation example between software layers when notifying the SP application of transaction information.
- FIG. 7 is a flowchart showing a processing procedure for notifying the SP application of transaction information between the secure element unit 114 and the reader/writer 120 .
- FIG. 8 is a diagram showing a schematic operation example between software layers when verifying the legitimacy of an SP application.
- FIG. 9 is a diagram showing an example of a processing sequence for verifying the legitimacy of an SP application that is a transaction notification target.
- FIG. 10 is a diagram showing the data structure of SP application attribute information acquired from the SIM server.
- FIG. 11 is a diagram showing the data structure of the header portion that specifies the uniqueness of a transaction.
- FIG. 12 is a diagram showing the data structure of the payload of transaction information related to payment.
- FIG. 13 is a diagram showing the data structure of the payload of transaction information other than payment.
- FIG. 14 is a diagram showing an example of updating the screen according to the occurrence of transactions.
- FIG. 15 is a diagram showing another example of updating the screen according to the occurrence of transactions.
- FIG. 1 schematically shows a hardware configuration example of an information processing apparatus 100 to which the present disclosure is applied.
- the information processing apparatus 100 is assumed to be a multifunctional information terminal such as a smart phone or a tablet equipped with a secure element, but may be other types of information equipment such as a personal computer (PC).
- PC personal computer
- the illustrated information processing device 100 includes a CPU (Central Processing Unit) 101, a ROM (Read Only Memory) 102, a RAM (Random Access Memory) 103, a host bus 104, a bridge 105, an expansion bus 106, an interface It includes a unit 107 , an input unit 108 , an output unit 109 , a storage unit 110 , a drive 111 , a communication unit 113 and a secure element (SE) unit 114 .
- a CPU Central Processing Unit
- ROM Read Only Memory
- RAM Random Access Memory
- the CPU 101 functions as an arithmetic processing device and a control device, and controls the overall operation of the information processing device 100 according to various programs.
- the ROM 102 nonvolatilely stores programs (basic input/output system, etc.) used by the CPU 101, operation parameters, and the like.
- the RAM 103 is used to load programs used in the execution of the CPU 101 and to temporarily store parameters such as work data that change as appropriate during program execution.
- the programs loaded into the RAM 103 and executed by the CPU 101 are, for example, various application programs, an operating system (OS), middleware (MW), and the like.
- the CPU 101, ROM 102 and RAM 103 are interconnected by a host bus 104 comprising a CPU bus or the like.
- the CPU 101 can implement various functions and services by executing various application programs under the execution environment provided by the OS through cooperative operations of the ROM 102 and the RAM 103 .
- the OS is, for example, Android by Google Inc. in the United States.
- the application program includes an SP application distributed by an SP provider regarding the service function of the secure element.
- the host bus 104 is connected to the expansion bus 106 via the bridge 105 .
- the information processing apparatus 100 it is not necessary for the information processing apparatus 100 to be configured such that the circuit components are separated by the host bus 104, the bridge 105 and the expansion bus 106, and an implementation in which almost all circuit components are interconnected by a single bus (not shown). may be
- the interface unit 107 connects peripheral devices such as the input unit 108, the output unit 109, the storage unit 110, the drive 111, the communication unit 113, and the secure element (SE) unit 114 according to the standard of the expansion bus 106.
- peripheral devices such as the input unit 108, the output unit 109, the storage unit 110, the drive 111, the communication unit 113, and the secure element (SE) unit 114 according to the standard of the expansion bus 106.
- peripheral devices such as the input unit 108, the output unit 109, the storage unit 110, the drive 111, the communication unit 113, and the secure element (SE) unit 114 according to the standard of the expansion bus 106.
- the information processing apparatus 100 may further include peripheral devices (not shown).
- the peripheral devices may be built in the main body of the information processing device 100, or some of the peripheral devices may be externally connected to the main body of the information processing device 100.
- the input unit 108 is composed of an input control circuit and the like that generates an input signal based on an input from the user and outputs it to the CPU 101 .
- the input unit 108 is, for example, a touch panel or a microphone, but may also include other mechanical operators such as buttons.
- the input unit 108 may include a camera mounted on the information terminal.
- the output unit 109 includes a display device such as a liquid crystal display (LCD) device, an organic EL (Electro-Luminescence) display device, and an LED (Light Emitting Diode), and displays various data such as video data as an image or text. or display a GUI (Graphical User Interface) screen. Also, the output unit 109 includes an audio output device such as a speaker and headphones, and converts audio data and the like into audio and outputs the audio.
- LCD liquid crystal display
- organic EL Electro-Luminescence
- LED Light Emitting Diode
- the output unit 109 includes an audio output device such as a speaker and headphones, and converts audio data and the like into audio and outputs the audio.
- the storage unit 110 stores programs (applications, OS, middleware, etc.) executed by the CPU 101 and files such as various data.
- the storage unit 110 is composed of, for example, a large-capacity storage device such as an SSD (Solid State Drive), but may also include an external storage device such as an HDD (Hard Disk Drive).
- the removable storage medium 112 is a cartridge-type storage medium such as a microSD card.
- the drive 111 performs read and write operations on the removable storage medium 113 loaded therein.
- the drive 111 outputs data read from the removable recording medium 112 (for example, still images and moving images) to the RAM 103 and writes data on the RAM 103 to the removable recording medium 112 .
- the communication unit 113 is a device that performs wireless communication such as cellular communication networks such as 4G and 5G, Wi-Fi (registered trademark), and Bluetooth (registered trademark).
- the communication unit 113 may include a terminal such as HDMI (registered trademark) (High-Definition Multimedia Interface), and may further include a function of performing HDMI (registered trademark) communication with a display or the like.
- the secure element (SE) unit 114 is a device protected by tamper-resistant hardware called an IC chip or RFID tag. Tamper resistance means that internal analysis (reverse engineering) and modification are extremely difficult. implemented by means of In addition, the secure element unit 114 is capable of secure contactless communication with the reader/writer 120 using mutual authentication and encryption. Non-contact communication is performed using electromagnetic waves emitted from the reader/writer 120 . The communication is a symmetrical communication that does not use sub-carriers and takes place at a rate of 212 kbps/424 kbps using a frequency band of 13.56 MHz.
- the secure element section 114 is capable of managing multi-purpose data within a single secure element module. Individual access rights can be set for each piece of data in the memory within the secure element unit 114, thereby realizing secure interoperability between applications.
- the operation of the information processing device 100 is asynchronously (or an advance notice is given without the need to start the application). ), a transaction is performed between the secure element unit 114 and the reader/writer 120 .
- the transaction referred to here is processing related to various service functions such as credit card function, ticket function, personal authentication function, ticket function, electronic money or settlement function. Transactions can be safely performed by using the tamper resistance of the secure element unit 114 .
- transaction processing target data (e.g., electronic money) is stored in a secure memory that prevents data falsification, data leakage, and unauthorized use by excluding direct access from the outside. Stored in an area (described later). Furthermore, in this embodiment, data relating to transaction processing is also stored in the secure element unit 114 together. Data related to transaction processing shall include information that can be used to recognize "processing with service ID XX has occurred", etc.).
- FIG. 2 schematically shows the internal configuration of the secure element section 114.
- the secure element unit 114 includes an antenna unit 201, an analog unit 202 connected to the antenna unit 201, a digital control unit 203, a memory 204, and an external interface (external IF) 205, and is installed in the information processing apparatus 100. It is
- the secure element section 114 may be configured with a one-chip semiconductor integrated circuit, or may be configured with two-chip semiconductor integrated circuits by separating the RF analog front end and the logic circuit section.
- the antenna section 201 and the analog section 202 constitute a contactless interface between the secure element section 114 and the reader/writer 120 .
- the antenna unit 201 transmits and receives contactless data to and from the reader/writer 120 .
- the analog section 202 processes analog signals transmitted and received from the antenna section 201, such as detection, modulation/demodulation, and clock extraction.
- the reader/writer 120 transmits a modulated carrier wave containing a data read request or a data write request and an unmodulated carrier wave for reply from the secure element section 114 .
- the analog section 202 reflects and transmits from the antenna section 201 a carrier wave in which reply data is superimposed on a non-modulated carrier wave.
- the NFC communication system is used for contactless communication with the reader/writer 120.
- secure non-contact communication is possible with the reader/writer 120 using mutual authentication and encryption.
- the digital control unit 203 comprehensively controls processing of data transmitted and received between the reader/writers 120 and other operations within the secure element unit 114 .
- the digital controller 203 also has a locally connected addressable memory 204 .
- the memory 204 is composed of a non-volatile storage device such as EEPROM (Electrically Erasable Programmable Read Only Memory), and is related to various service functions such as ticket function, electronic money or payment function, credit card function, ticket function, and personal authentication function (That is, it is used to store data (to be processed in a transaction).
- the digital control unit 203 builds a hierarchical structure (see FIG. 3) in the memory space of the memory 204 and stores data to be processed for transactions. Furthermore, in this embodiment, data related to transaction processing (see FIG. 4) is also stored in memory 204 .
- the memory 204 may be used to write program codes executed by the digital control unit 203 or to store work data during program execution.
- the external interface 205 is a functional module for the digital control unit 203 to wire-connect the main body of the information processing apparatus 100 according to the interface protocol for connecting with the interface unit 107 on the information processing apparatus 100 side.
- Data written in the memory 204 can be transferred to the main body of the information processing apparatus 100 (CPU 101 or RAM 103) via the external interface 205.
- the information processing apparatus 100 side (for example, a software program executed by the CPU 101 ) can perform operations such as reading data from and writing data to the memory 204 via the external interface 205 and the digital control unit 203 .
- FIG. 3 schematically shows a data structure in a memory area for storing transaction processing target data, constructed in the memory 204 within the secure element unit 114 .
- This memory area is a memory area that can be accessed under the control of the digital control unit 203. By excluding direct access from the outside, it is possible to prevent data falsification, data leakage, and unauthorized use of data. safe memory area.
- data is managed according to a hierarchical structure in units of "area”, "service”, and "user block data”.
- Area corresponds to "directory” or "folder”, and it is also possible to create areas hierarchically under areas.
- An area is formed for each service provider, for example, and multiple areas may be formed in memory 204 if secure element unit 114 supports multiple service providers. Of course, multiple areas can be formed for one service provider, and one area can be shared by multiple service providers.
- Service is a concept that manages data access rights or encryption methods. Specifically, data stored under a service is controlled based on access rights or an encryption method determined for the service. For example, assume that service A in FIG. 3 stores unencrypted data, and service B stores data encrypted by a predetermined encryption method. In this case, user block data A-1 and user block data A-2, which are relatively less important data, can be stored under service A without being encrypted. On the other hand, user block data B-1, which is data of relatively high importance, can be encrypted by an encryption method determined by service B and stored under service B.
- FIG. A plurality of services can also exist per hierarchical structure.
- User block data is a storage area for storing data used for processing by the secure element unit 114 (that is, data to be processed) or the data itself, and there may be a plurality of such data per hierarchical structure.
- data related to transaction processing (see FIG. 4) is also stored in the memory 204.
- FIG. 4 shows a configuration example of data relating to transaction processing.
- the data related to each transaction process includes the path of the data to be processed in the memory area (see FIG. 3), the data to be processed itself, the hash value of the data to be processed, and the like.
- the digital control unit 203 When executing a transaction with the reader/writer 120, the digital control unit 203 converts the data to be processed and the path of the data to be processed in the memory area (see FIG. 3) as data relating to the processing of the transaction. Store. Furthermore, the digital control unit 203 calculates a hash value of the data to be processed, and stores the hash value together as data related to the processing of the transaction.
- the digital control unit 203 may appropriately add data other than the data shown in FIG.
- the digital control unit 203 may add data relating to the attributes of the data to be processed (eg, content, type, importance, etc.).
- the digital control unit 203 may replace the data shown in FIG. 4 with other corresponding data.
- the digital control unit 203 may replace the path of the data to be processed with arbitrary data that can identify the data to be processed.
- the digital control unit 203 may calculate a hash value including not only the data to be processed but also data other than the data to be processed (for example, the path of the data to be processed). As a result, the main body of the information processing apparatus 100 can verify the integrity of not only the data to be processed but also the data other than the data to be processed.
- FIG. 5 schematically shows the stack structure of software operating on the information processing apparatus 100 .
- a software stack consists of a device driver layer, an OS layer, a middleware layer, and an application layer in order from the lowest layer.
- Device driver layer The lowest layer, the device driver layer, is composed of a set of device drivers that individually control each piece of hardware included in the information processing apparatus 100 .
- the “hardware” referred to here includes a device driver for drive control for each hardware component constituting the input unit 108, the output unit 109, the storage unit 110, the drive 111, the communication unit 113, and the like. be.
- a device driver for the secure element unit 114 (denoted as "SE driver” in FIG. 5) is also provided.
- SE driver Secure element unit
- the device driver has the function of notifying the OS of the event when an event occurs in the corresponding device.
- Event notification is performed, for example, by processing such as generation of an interrupt or polling.
- the SE driver for example, it is possible to detect the occurrence of an event by receiving an interrupt signal from the external interface unit 205 in the secure element unit 114 or by polling the status register in the external interface unit 205.
- the SE driver uses the function of the “contactless communication applet” to detect an event that contactless communication between the secure element unit 114 and the reader/writer 120 starts and ends (or when the secure element unit 114 carrier on and off events), notify the OS.
- device drivers control device-specific hardware operations such as data input/output operations and device driving operations for corresponding devices.
- the SE driver responds to an access request from an upper layer to the secure element unit 114 (specifically, an access request from an application (SP application) via middleware), and the external interface unit 205 in the secure element unit 114. It has a function of performing transactions such as data reading and data writing with respect to the memory 204 through the memory 204 .
- This function is assumed to be implemented by a "transaction applet”.
- the OS and middleware can access the transaction applet via OMAPI (Open mobile API).
- Transactional applets store data for transactional processing. Transaction processing target data is handled in units called APDUs (Application Protocol Data Units).
- the structure of the memory space for storing transaction processing target data has already been described with reference to FIG.
- a mechanism is introduced that enables recognition of the content of processing (for example, "Processing with service ID XX has occurred") when writing to the memory 204 from the reader/writer 120 occurs.
- the OS provides applications with an execution environment including functions commonly used by many applications and basic hardware control functions. For example, if the information processing apparatus 100 is an information terminal such as a smart phone or a tablet, Android of Google, Inc., etc., corresponds to the OS. When the OS is Android, information related to the entire system, such as event notifications from device drivers, is sent to all applications using a mechanism called "BroadcastIntent.” An Intent is a message object exchanged between one or more activities or services included in an application running on Android.
- Middleware is located between the OS and applications and provides functions commonly used by various software. For example, specific or individual functions with limited fields or uses are provided by middleware rather than by the OS. Since not all models of information terminals such as smartphones and tablets are equipped with a secure element, it is assumed in this embodiment that functions related to the use of the secure element unit 114 are provided as middleware. Also, GUI functions and the like are provided as middleware. However, the middleware functions not related to the secure element unit 114 are not directly related to the present disclosure, so the description thereof is kept to a minimum in this specification.
- SE access client and “service integration client” are included as functions related to the use of the secure element unit 114 provided by middleware.
- the “SE access client” is a function that accesses the secure element unit 114 .
- the “service integration client” is a function that manages information about the service being used in the secure element unit 114 in cooperation with a server (hereinafter referred to as "service integration server”) (not shown in FIG. 5). .
- Application layer The highest application layer consists of a set of application software that are used according to their respective work purposes. Each application software uses the functions provided by the OS and middleware to achieve its work purpose. For example, it is assumed that application software for telephone, email, camera, calendar/schedule management, etc. is installed in the information processing apparatus 100 . These general application software are not directly related to this disclosure and are only minimally described here.
- one or more SP applications that provide service functions (ticket function, electronic money or payment function, credit card function, ticket function, personal authentication function, etc.) using the secure element unit 114 are Assume that it is installed in the information processing apparatus 100 .
- the information processing apparatus 100 installed with such an SP application can operate as an IC card that provides a corresponding service function.
- the service integration client manages, for each SP application installed in the information processing apparatus 100, a service ID that identifies a service to be used and a card ID (CID) that identifies a card that can be referenced from the SP application.
- the SP application When the SP application actively accesses information in the secure element section 114, the SP application must occupy the right to use the secure element section 114.
- the SP application performs usage application procedures to the service integration client, and the service integration client requests the service integration server to confirm the legitimacy (identity) of the SP application and to operate the secure elements permitted for the SP application. After the inquiry, the SP application becomes a state in which the right to use the secure element unit 114 is occupied. Therefore, when the SP application tries to access the secure element unit 114, processing time, network load, and server load due to occupation of the right to use the secure element unit 114 are required.
- the SP application that has occupied the right to use the secure element unit 114 accesses the secure element unit 114 through the SE access client, which is a middleware function, that is, reads data from or writes data to the memory 204 in the secure element unit 114. Action can be performed.
- the SE access client should perform access restrictions such as verifying the SP application requesting access to the secure element unit 114 and prohibiting simultaneous access to the secure element unit 114 by multiple SP applications. I have to.
- the information processing apparatus 100 in which the transaction notification function SP application is installed can operate as an IC card that provides the corresponding service function. For example, a manual operation of holding the information processing device 100 over the reader/writer 120 by the user causes a transaction between the secure element unit 114 mounted on the information processing device 100 and the reader/writer 120 .
- the SE access client in the middleware restricts access to the secure element unit 114 (SP application verification, simultaneous access prohibition by multiple SP applications, etc.) to ensure security. ing. Under such access restrictions, if each SP application regularly and actively tries to access the memory 204 in the secure element unit 114 in order to grasp the latest information, access conflicts from a plurality of SP applications may occur. is likely to occur.
- the SP application cannot immediately detect changes in information in the memory 204 that occur without prior notice by simply accessing it periodically, so the information acquired by the SP application from the memory 204 lacks real-time performance. Furthermore, even if the information in the memory 204 does not change, the SP application needs to access it periodically, which leads to wasteful processing.
- the service integration client needs to access the service integration server to verify the validity of the SP application and acquire a list of cards that can be referenced from the SP application. Therefore, there is a processing load for the information processing apparatus 100 to connect to the network, and the server load increases.
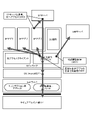
- FIG. 6 shows an operation example between software layers when notifying the SP application of transaction information between the secure element unit 114 and the reader/writer 120 .
- a transaction occurs between the secure element unit 114 mounted on the information processing apparatus 100 and the reader/writer 120 by a manual operation in which the user holds the information processing apparatus 100 over the reader/writer 120 (S601). Such transactions occur without notice to the associated SP App.
- a carrier wave is transmitted from the reader/writer 120 in a transaction.
- the carrier wave includes a modulated carrier wave containing a data read request or data write request from the reader/writer 120 and a non-modulated carrier wave for reply from the secure element unit 114 .
- transaction data is stored in the transaction applet.
- the contactless communication applet of the SE driver detects that a transaction has occurred between the secure element unit 114 and the reader/writer 120, it notifies the OS of the event (S602). Then, when the OS detects the event, it sends a Broadcast to notify the upper layer that the state of the system has changed (S603).
- the service integration client in the middleware When the service integration client in the middleware receives the event notification broadcast from the OS, it accesses the transaction applet via OMAPI. Then, the service integration client acquires the data (APDU) to be processed for the corresponding transaction from the secure element unit 114 through the transaction applet (S604). At that time, the service integration client acquires data related to transaction processing together with transaction processing target data.
- the service integration client analyzes the acquired data for each SP (service provider) and determines the SP application that requires notification of transaction information (S605).
- the data related to transaction processing which is acquired together with the transaction processing target data, contains information that can be used to recognize "processing with service ID XX has occurred," etc.). Therefore, the service integration client can identify the service ID related to the transaction by analyzing the data related to the transaction processing, and can determine the SP application to be notified based on the service ID.
- the service integration client verifies the legitimacy of each SP application determined as a notification target (S606).
- the service integration client verifies the legitimacy of the SP application based on verification information obtained in advance from the server. Specifically, the package name of the SP application and the signature value of the SP application are used as verification information.
- a Service Information Management (SIM) server manages information including verification information for each SP application. The details of the processing for verifying the legitimacy of the notification target SP application will be given later.
- SIM Service Information Management
- the service integration client notifies the appropriate SP application whose validity has been verified of the transaction information (S607). Details of transaction information to be notified to the SP application will be given later.
- the information is notified at predetermined time intervals between the SP applications. This is because there is a possibility that the SP application will receive notification of the transaction information and start accessing the secure element unit 114 .
- Reasons for access include automatic charging due to a decrease in the balance after a transaction, and reading processing of the point balance associated with payment.
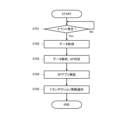
- FIG. 7 shows, in the form of a flowchart, a processing procedure for notifying the SP application of transaction information executed between the secure element unit 114 and the reader/writer 120, which is executed within the information processing apparatus 100.
- the illustrated processing procedure is realized mainly by the service integration client included in the middleware layer.
- the service integration client is notified via the OS of an event indicating that a transaction has been performed between the secure element unit 114 and the reader/writer 120 (Yes in step S701).
- the service integration client accesses the transaction applet in the SE driver via OMAPI to acquire transaction processing target data and transaction processing data (step S702).
- the service integration client analyzes the acquired data for each SP (service provider) and determines the SP application that requires notification of transaction information (step S703).
- Data related to transaction processing includes information that can be used to recognize "service ID XX processing has occurred", etc.), so the service integration client can identify the corresponding service ID by data analysis, and the service ID The SP application to be notified can be determined based on.
- the service integration client verifies the legitimacy of each SP application determined as a notification target based on the verification information for each SP application obtained in advance from the SIM server (step S704).
- the details of the processing for verifying the legitimacy of the notification target SP application will be given later.
- the service integration client notifies the appropriate SP application whose validity has been verified of the transaction information (step S705). Details of transaction information to be notified to the SP application will be given later.
- Section E describes in detail the validation processing of the SP application that is executed when the SP application to be notified is determined in the transaction notification function described in section D above. explain.
- Fig. 8 shows a schematic operation example between software layers when verifying the validity of the SP application that is the target of the transaction notification.
- the service integration client acquires verification information for each SP application installed in the information processing device 100 from the SIM server in advance (S801).
- the verification information includes information such as a package name that uniquely identifies the SP application, an SP application signature value (an application signer's certificate hash, etc.), and the like.
- the service integration client can detect the event through reception of a broadcast from the OS.
- the service integration client analyzes the data obtained through the transaction applet for each SP, determines the SP application to be notified of the transaction information, and then obtains the verification information obtained in advance from the SIM server. is used to verify the legitimacy of each SP application to be notified (S802). Then, the service integration client notifies the transaction information to each SP application whose validity has been successfully verified.
- the SP application can use the transaction information notified from the service integration client to quickly present information that has changed due to the transaction, such as the balance display.
- the SP application cooperates with the SP server to perform user notification and access to the secure element unit 114 (S803).
- the SP application in cooperation with the SP server, accesses the secure element unit 114 and provides services related to the relevant service functions, such as auto-charging due to a decrease in the balance after a transaction, and processing to read the point balance associated with payment. Make arrangements with your provider.
- Fig. 9 shows an example of a processing sequence between software modules for verifying the validity of the SP application that is the target of the transaction notification.
- SP application A and SP application B are targeted for transaction notification due to space limitations. Also, to simplify the explanation, it is assumed that both SP application A and SP application B have successfully verified the validity.
- the service integration client requests attribute information of each SP application installed in the information processing device 100 from the SIM server (SEQ901).
- the SIM server returns the requested attribute information of each SP application (SEQ902).
- the attribute information of the SP application includes verification information, and the acquisition of the attribute information from the SIM server is a preliminary process for verifying the legitimacy of the SP application. For example, every time the middleware is started, the service integration client checks update information on the SIM server periodically (for example, once every 30 days, once every 100 times, etc.), and updates each installed SP application. Get the latest attribute information in advance.
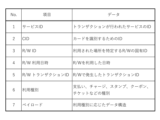
- FIG. 10 exemplifies the data structure of SP application attribute information that the service integration client acquires from the SIM server. More precisely, the service integration client acquires a data list as shown in FIG. 10 from the SIM server for each SP application. Each data will be explained below.
- Service ID consists of a value that uniquely represents the service implemented by the SP application. For example, in the case of an SP application that performs payment, it is a value that uniquely represents the payment service.
- the service ID is an alphanumeric value such as "SV123456" provided by the middleware developer (platformer that provides the secure element).
- “Information that uniquely identifies the SP application” is the package name of the SP application, such as "com.spapp.app”.
- “Signature Value” is, for example, the SP App Signer Certificate Hash in hexadecimal. It is possible to obtain the signer certificate of the SP application from the OS, calculate a hash value, and compare the hash value with the signature value included in the attribute information of the SP application to verify the legitimacy of the SP application.
- Priority indicates the priority of notification of transaction information with a value of 1-10. When a plurality of SP applications are valid notification targets, transaction information is notified in order from the SP application with the highest priority.
- Notification time limit indicates a numerical value from 0 to 3 for the time for which the SP application allows notification delay.
- Action when notification deadline is exceeded indicates with a value of 0 or 1 whether to give up or carry out notification when the delay time specified in "notification deadline” is exceeded.
- the service integration client specifies the SP application to be notified, and each SP application to be notified (SP application A in the example shown in FIG. 9). and SP application B).
- the service integration client first identifies the SP application to be notified.
- the service integration client analyzes the data related to transaction processing and specifies the service ID
- the service integration client compares it with the attribute information (see FIG. 10) of each SP application acquired in advance in the pre-processing, and finds the SP with the matching service ID.
- An app can be specified as a notification target.
- two applications, SP application A and SP application B, are specified as notification targets.
- the service integration client requests the verification information of the SP application to be notified by each SP (SEQ903), and in response, the OS returns the verification information of each SP application (SEQ904).
- the OS for smartphones such as Android of Google Inc. grasps the verification information of each SP application through the mutual authentication procedure that is performed when installing the application. Therefore, the service integration client can acquire the verification information of each SP application to be notified by inquiring the OS.
- the service integration client verifies the legitimacy of each SP application to be notified (SEQ905).
- the service integration client performs verification by comparing the verification information included in the attribute information of each SP application to be notified with the verification information of the corresponding SP application obtained from the OS. It can be determined that there is In the processing sequence example shown in FIG. 9, the validity of both SP application A and SP application B specified as notification targets is confirmed.
- smartphones that use Android as the OS can install applications from sources other than the official app store.
- the user misunderstands the application created by disguising its appearance and package name as a legitimate application and installs it on his/her own terminal. information may be leaked, misused, or altered.
- the validity of the SP application is verified using verification information that is a combination of the package name of the SP application and the signature value of the SP application.
- the information in 114 can be protected from leakage, unauthorized use, tampering, and the like.
- the service integration client notifies the target SP application, whose validity has been confirmed, of the transaction processing target data.
- the validity of both SP application A and SP application B has been confirmed. SEQ907).
- the notifications are sent in order of priority included in the attribute information of each SP application.
- SP application A has a higher priority than SP application B.
- SP application B has a higher priority than SP application B.
- notification processing SEQ906
- SP application B SEQ907
- Reasons for access include automatic charging due to a decrease in the balance after a transaction, and reading processing of the point balance associated with payment. If the time interval for receiving notifications between SP applications is not sufficiently long, processing such as access to the secure element unit 114 may compete between SP applications A and B that have received notifications before and after.
- This data structure consists of a header part that identifies the uniqueness of a transaction and a payload that corresponds to the type of transaction.
- Fig. 11 shows the data structure of the header part that specifies the uniqueness of the transaction.
- the header part that specifies the uniqueness of a transaction is a common data structure that does not depend on the transaction usage type (settlement or other than settlement).
- a service ID is identification information that uniquely identifies a service processed by a transaction (for example, a service for which payment was made).
- CID is identification information for identifying a card.
- the R/W ID is identification information unique to the reader/writer that is the partner of the transaction. Based on the R/W ID, it is possible to identify the location of use.
- the R/W usage date and time is the date and time when the reader/writer was used (or the date and time when the transaction was executed).
- the R/W transaction ID is identification information of a transaction generated by the reader/writer.
- the usage type indicates the type of transaction such as payment, charge, stamp, coupon, and ticket.
- the payload consists of a data structure according to the usage type.
- FIG. 12 shows the data structure of the payload of transaction information related to payment as an example of the data structure of the payload according to the transaction usage type.
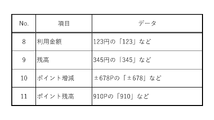
- the payload for payment includes data updated by the transaction, such as usage amount, balance, point increase/decrease, and point balance.
- FIG. 13 shows the data structure of the payload of transaction information other than payment as another example of the payload data structure according to the transaction usage type.
- the payload in this case includes a service-specific identification ID and face/design information.
- the service-specific specific ID is a unique ID that can be defined by the service provider, such as a ticket-specific ID or a coupon-specific ID.
- the card face/design information is information that defines stamps and card face designs, and includes, for example, an ID that is used as part of the URL (Uniform Resource Locator) of a business partner.
- the payload of transaction information related to payment may also include a service-specific identification ID and face/design information.
- a transaction is generated by a manual operation of holding the information processing apparatus 100 over the reader/writer 120, and there is no need to start the SP application at that time, and there is no notice to the SP application.
- the SP application had to actively access the secure element unit 114 to acquire the latest data (usage amount, balance, increase/decrease in points, point balance, etc.) changed by the transaction.
- the transaction information notification function according to the present disclosure, all related SP applications can immediately detect that the data in the secure element unit 114 has changed due to a transaction.
- such a notification function to the SP application is realized by implementing the function shown in FIG. 6 in the service integration client in the middleware. Therefore, according to the notification function according to the present disclosure, the SP application can grasp the transaction information without accessing the secure element unit 114, and promptly present the latest information such as the balance display that has changed due to the transaction. can.
- the number of accesses to the secure element unit 114 by the SP application is minimized. can reduce the incidence of In a situation where simultaneous access to the secure element unit 114 by multiple SP applications is prohibited, it is particularly effective to be able to suppress access conflicts.
- the SP application it becomes unnecessary for the SP application to apply to the service integration client and to make an inquiry to the service integration server in order to occupy the right to use the secure element unit 114. It also reduces load and server load.
- the transaction information notification function when the data in the secure element unit 114 changes due to a transaction such as charging, the related SP application immediately updates information such as the balance, and always The latest information can be presented on the screen of the information processing apparatus 100 or the like.
- FIG. 14 shows an example of updating the screen in response to changes in the data in the secure element section 114 due to the occurrence of transactions. Specifically, FIG. 14 shows how the electronic money balance being presented on the screen of the smartphone is immediately updated to the latest information due to the occurrence of a transaction (payment, charge, etc.).
- the information processing device 100 (smartphone) is held over the reader/writer 120 and a transaction such as payment or charge occurs, the information in the secure element section 114 changes.
- the SP application to be notified is notified of the latest information in the secure element unit 114 after the determination and validity verification of the SP application to be notified.
- the SP application to be notified changes the electronic money balance on the screen from the amount before the transaction (1,234 yen) to the amount after the transaction (5,678 yen) immediately. can be updated and presented. When updating the presented amount, there is no need for a user operation such as activating the SP application, or for the SP application to occupy the right to use the secure element unit 114 .
- FIG. 15 shows another example of updating the screen in response to changes in the data in the secure element unit 114 due to the occurrence of a transaction.
- the partial electronic money balance that has changed due to the occurrence of a transaction (payment, charge, etc.) is immediately updated. is shown.
- the information processing device 100 (smartphone) is held over the reader/writer 120 and a transaction such as payment or charge using the electronic money C occurs, the information of the electronic money C changes within the secure element section 114 .
- an SP application related to the service of electronic money C is determined to be a notification target, and after the validity of the SP application is verified, the notification target SP application receives the electronic money C in the secure element unit 114. The latest information of is notified.
- the balance of the electronic money C can be immediately updated and presented on the integrated balance display screen of the Wallet application.
- the SP application that receives the notification acquires and displays a coupon based on the usage information of the electronic money C in the background of the screen update processing, or rather invites the user to start the SP application. (User Experience) can also be realized.
- the SP application when the SP application actively acquires information in the secure element unit 114 as before, the SP application generally performs a usage application procedure to the service integration client, and the service integration client obtains information from the SP application. After confirmation of legitimacy (identity) and an inquiry about the operation of the secure element permitted by the SP application, the SP application occupies the right to use the secure element unit 114 . Therefore, if an attempt is made to start the SP application and present the latest data in the secure element unit 114 (e.g., to present the balance) as before, the processing time, network load, and server load.
- the transaction information notification function it is possible to notify information such as transaction processing target data to a plurality of related SP applications.
- Such a simultaneous notification function to a plurality of SP applications is specifically realized by implementing the data analysis and SP determination functions shown in FIG. 6 in the service integration client in the middleware.
- a plurality of SP applications using the same electronic money can update their information.
- the transaction information notification function can control the SP application to which the notification is sent. Even if a transaction occurs between the secure element unit 114 and the reader/writer 120, only the SP application that needs changed information as a result of the transaction is determined as a notification target, and the information is not notified to the SP application that should not be notified. can do.
- the transaction information notification function it is possible to verify the legitimacy of an SP application that has been determined to be a notification target, so as not to pass transaction information to an unauthorized application. For example, there are cases where an unauthorized SP application is created in which the appearance and package name are disguised to look like the real thing.
- an unauthorized SP application since the validity of the SP application is verified using verification information obtained by combining the package name of the SP application and the signature value of the SP application, unauthorized SP applications are excluded, and the information in the secure element unit 114 is Leakage, unauthorized use, tampering, etc. can be prevented.
- the present disclosure is applied to a smart phone equipped with a secure element such as an IC chip that performs contactless communication, but the gist of the present disclosure is not limited to this.
- the present disclosure can also be applied to various types of information processing devices equipped with devices that perform transactions with external devices through wireless or wired communication other than contactless communication, so that information on transactions performed between the devices and external devices can be appropriately transmitted. Application can be notified.
- An information processing device equipped with a device that performs transactions with an external device, a detection unit that detects that a transaction has occurred between the device and the external device; an acquisition unit that acquires data from the device in response to the detection of the occurrence of the transaction by the detection unit; a determination unit that analyzes the data acquired by the acquisition unit and determines an application to be notified; a verification unit that verifies the validity of the notification target application; a notification unit that notifies an appropriate application whose validity has been confirmed among the notification targets, of the data acquired by the acquisition unit;
- An information processing device comprising:
- the detection unit detects the occurrence of the transaction based on the transmission from the operating system;
- the information processing apparatus according to (1) above.
- the acquisition unit acquires data from the device via OMAPI;
- the information processing apparatus according to any one of (1) and (2) above.
- the acquisition unit acquires data to be processed of the transaction and data related to the processing of the transaction;
- the information processing apparatus according to any one of (1) to (3) above.
- the determination unit identifies a service ID related to the transaction based on the data acquired by the acquisition unit, and determines an application to be notified based on the service ID; Information processing according to any one of (1) to (4) above
- the determination unit analyzes the data related to the processing of the transaction acquired by the acquisition unit and identifies a service ID related to the transaction;
- the information processing apparatus according to (5) above.
- the verification unit verifies the validity of the application based on the application verification information obtained from the server and the application information obtained from the operating system;
- the information processing apparatus according to any one of (1) to (6) above.
- the verification information includes the package name and signature value of the application;
- the notification unit notifies the appropriate application of data to be processed for the transaction.
- the information processing apparatus according to any one of (1) to (8) above.
- the notification unit When there are a plurality of suitable applications, the notification unit notifies the applications at predetermined time intervals.
- the information processing apparatus according to any one of (1) to (9) above.
- the notification unit notifies the appropriate application based on information for each application obtained from the server.
- the information processing apparatus according to any one of (1) to (10) above.
- the information for each application obtained from the server includes at least one of notification priority, notification deadline, and operation when the notification deadline is exceeded;
- the information processing device according to (11) above.
- the device conducts transactions with the external device through contactless communication;
- the information processing apparatus according to any one of (1) to (12) above.
- the contactless communication is communication that performs mutual authentication and encryption.
- the information processing device according to (13) above.
- the transaction occurs without prior notice without launching an application installed in the information processing device.
- the information processing apparatus according to any one of (1) to (13) above.
- An information processing method comprising:
- An information processing device equipped with a device that performs transactions with an external device, a detection unit that detects that a transaction has occurred between the external devices of the device; an acquisition unit that acquires data from the device in response to the detection of the occurrence of the transaction by the detection unit; a determination unit that analyzes the data acquired by the acquisition unit and determines an application to be notified; a verification unit that verifies the validity of the notification target application; a notification unit that notifies an appropriate application whose validity has been confirmed among the notification targets of the data acquired by the acquisition unit; A computer program written in computer readable form to act as a
- An information processing device equipped with a device that performs a transaction with an external device and having an application installed therein that provides a service related to the transaction, a notification unit that notifies the application of data to be processed of the transaction; a presentation unit that presents the information about the processing target data received by the application;
- an information processing device equipped with a device that performs a transaction with an external device and installed with an application that provides a service related to the transaction; a receiving unit that receives data to be processed of the transaction; a presentation unit that presents information about the received data to be processed;
Landscapes
- Engineering & Computer Science (AREA)
- Theoretical Computer Science (AREA)
- Computer Security & Cryptography (AREA)
- Software Systems (AREA)
- General Engineering & Computer Science (AREA)
- General Physics & Mathematics (AREA)
- Physics & Mathematics (AREA)
- Computer Hardware Design (AREA)
- Signal Processing (AREA)
- Computer Networks & Wireless Communication (AREA)
- Multimedia (AREA)
- Health & Medical Sciences (AREA)
- Bioethics (AREA)
- General Health & Medical Sciences (AREA)
- Stored Programmes (AREA)
- Financial Or Insurance-Related Operations Such As Payment And Settlement (AREA)
Priority Applications (3)
| Application Number | Priority Date | Filing Date | Title |
|---|---|---|---|
| JP2023539604A JPWO2023013102A1 (enExample) | 2021-08-06 | 2022-02-01 | |
| US18/293,377 US20240338433A1 (en) | 2021-08-06 | 2022-02-01 | Information processing apparatus, information processing method, and computer program |
| CN202280053163.9A CN117730323A (zh) | 2021-08-06 | 2022-02-01 | 信息处理装置、信息处理方法和计算机程序 |
Applications Claiming Priority (2)
| Application Number | Priority Date | Filing Date | Title |
|---|---|---|---|
| JP2021129455 | 2021-08-06 | ||
| JP2021-129455 | 2021-08-06 |
Publications (1)
| Publication Number | Publication Date |
|---|---|
| WO2023013102A1 true WO2023013102A1 (ja) | 2023-02-09 |
Family
ID=85155501
Family Applications (1)
| Application Number | Title | Priority Date | Filing Date |
|---|---|---|---|
| PCT/JP2022/003807 Ceased WO2023013102A1 (ja) | 2021-08-06 | 2022-02-01 | 情報処理装置及び情報処理方法、並びにコンピュータプログラム |
Country Status (4)
| Country | Link |
|---|---|
| US (1) | US20240338433A1 (enExample) |
| JP (1) | JPWO2023013102A1 (enExample) |
| CN (1) | CN117730323A (enExample) |
| WO (1) | WO2023013102A1 (enExample) |
Citations (2)
| Publication number | Priority date | Publication date | Assignee | Title |
|---|---|---|---|---|
| JP2005050262A (ja) * | 2003-07-31 | 2005-02-24 | Matsushita Electric Ind Co Ltd | Icモジュール、icカード、携帯端末、及びサービス処理方法 |
| JP2011028688A (ja) * | 2009-07-29 | 2011-02-10 | Felica Networks Inc | 情報処理装置、プログラム、および情報処理システム |
Family Cites Families (6)
| Publication number | Priority date | Publication date | Assignee | Title |
|---|---|---|---|---|
| JPWO2007119550A1 (ja) * | 2006-04-05 | 2009-08-27 | パナソニック株式会社 | システム管理装置 |
| US10311427B2 (en) * | 2006-12-29 | 2019-06-04 | Google Technology Holdings LLC | Method and system for monitoring secure application execution events during contactless RFID/NFC communication |
| JP2009049454A (ja) * | 2007-08-13 | 2009-03-05 | Sony Corp | 情報通信端末、情報処理方法及びプログラム |
| JP5260081B2 (ja) * | 2008-02-25 | 2013-08-14 | パナソニック株式会社 | 情報処理装置及びその制御方法 |
| CN103455750B (zh) * | 2013-08-26 | 2016-08-10 | 北京视博数字电视科技有限公司 | 一种嵌入式设备的高安验证方法及装置 |
| CN110557395B (zh) * | 2019-09-06 | 2021-07-02 | 东信和平科技股份有限公司 | 一种安全元件访问接口协议适配方法及装置 |
-
2022
- 2022-02-01 JP JP2023539604A patent/JPWO2023013102A1/ja active Pending
- 2022-02-01 CN CN202280053163.9A patent/CN117730323A/zh active Pending
- 2022-02-01 US US18/293,377 patent/US20240338433A1/en active Pending
- 2022-02-01 WO PCT/JP2022/003807 patent/WO2023013102A1/ja not_active Ceased
Patent Citations (2)
| Publication number | Priority date | Publication date | Assignee | Title |
|---|---|---|---|---|
| JP2005050262A (ja) * | 2003-07-31 | 2005-02-24 | Matsushita Electric Ind Co Ltd | Icモジュール、icカード、携帯端末、及びサービス処理方法 |
| JP2011028688A (ja) * | 2009-07-29 | 2011-02-10 | Felica Networks Inc | 情報処理装置、プログラム、および情報処理システム |
Also Published As
| Publication number | Publication date |
|---|---|
| JPWO2023013102A1 (enExample) | 2023-02-09 |
| US20240338433A1 (en) | 2024-10-10 |
| CN117730323A (zh) | 2024-03-19 |
Similar Documents
| Publication | Publication Date | Title |
|---|---|---|
| US8391837B2 (en) | Method, system and trusted service manager for securely transmitting an application to a mobile phone | |
| US10936719B2 (en) | Preserving trust data during operating system updates of a secure element of an electronic device | |
| US8352749B2 (en) | Local trusted services manager for a contactless smart card | |
| US8806199B2 (en) | Writing application data to a secure element | |
| US9173102B2 (en) | Method for updating a data carrier | |
| US9667426B2 (en) | Information processing apparatus, program, storage medium and information processing system | |
| US8799574B2 (en) | Method and devices for installing and retrieving linked MIFARE applications | |
| US20110281558A1 (en) | Telecommunications chip card and mobile telephone device | |
| CN106415591A (zh) | 用于nfc的电子设备、系统及方法 | |
| CN112613872A (zh) | 作为协议接口的类型4nfc标记 | |
| CN101755435B (zh) | 用于管理唯一存储设备标识的方法、服务器和移动通信设备 | |
| JP2019153310A (ja) | 情報処理装置、情報処理方法、およびプログラム | |
| WO2023013102A1 (ja) | 情報処理装置及び情報処理方法、並びにコンピュータプログラム | |
| US20240303115A1 (en) | Information processing apparatus and program | |
| US20220358299A1 (en) | Systems, methods, and computer-accessible mediums for repressing or turning off the read of a digital tag | |
| JP2007249544A (ja) | 電子媒体およびそれを含む情報端末 | |
| JP2007052492A (ja) | 情報処理装置および方法、並びにプログラム | |
| HK40029505A (en) | Information processing device and information processing method | |
| JP2018116724A (ja) | 携帯可能電子装置 | |
| KR20150074819A (ko) | 금융 마이크로 sd 카드를 구비한 결제 단말 장치 및 이의 실행 방법 |
Legal Events
| Date | Code | Title | Description |
|---|---|---|---|
| 121 | Ep: the epo has been informed by wipo that ep was designated in this application |
Ref document number: 22852531 Country of ref document: EP Kind code of ref document: A1 |
|
| WWE | Wipo information: entry into national phase |
Ref document number: 2023539604 Country of ref document: JP |
|
| WWE | Wipo information: entry into national phase |
Ref document number: 202280053163.9 Country of ref document: CN |
|
| NENP | Non-entry into the national phase |
Ref country code: DE |
|
| 122 | Ep: pct application non-entry in european phase |
Ref document number: 22852531 Country of ref document: EP Kind code of ref document: A1 |