WO2022014193A1 - ログ管理装置及びセキュリティ攻撃検知・分析システム - Google Patents
ログ管理装置及びセキュリティ攻撃検知・分析システム Download PDFInfo
- Publication number
- WO2022014193A1 WO2022014193A1 PCT/JP2021/021285 JP2021021285W WO2022014193A1 WO 2022014193 A1 WO2022014193 A1 WO 2022014193A1 JP 2021021285 W JP2021021285 W JP 2021021285W WO 2022014193 A1 WO2022014193 A1 WO 2022014193A1
- Authority
- WO
- WIPO (PCT)
- Prior art keywords
- log
- management device
- calculation result
- statistical calculation
- log management
- Prior art date
- Legal status (The legal status is an assumption and is not a legal conclusion. Google has not performed a legal analysis and makes no representation as to the accuracy of the status listed.)
- Ceased
Links
Images
Classifications
-
- G—PHYSICS
- G06—COMPUTING OR CALCULATING; COUNTING
- G06F—ELECTRIC DIGITAL DATA PROCESSING
- G06F21/00—Security arrangements for protecting computers, components thereof, programs or data against unauthorised activity
- G06F21/50—Monitoring users, programs or devices to maintain the integrity of platforms, e.g. of processors, firmware or operating systems
- G06F21/55—Detecting local intrusion or implementing counter-measures
- G06F21/554—Detecting local intrusion or implementing counter-measures involving event detection and direct action
-
- H—ELECTRICITY
- H04—ELECTRIC COMMUNICATION TECHNIQUE
- H04L—TRANSMISSION OF DIGITAL INFORMATION, e.g. TELEGRAPHIC COMMUNICATION
- H04L63/00—Network architectures or network communication protocols for network security
- H04L63/14—Network architectures or network communication protocols for network security for detecting or protecting against malicious traffic
- H04L63/1408—Network architectures or network communication protocols for network security for detecting or protecting against malicious traffic by monitoring network traffic
- H04L63/1425—Traffic logging, e.g. anomaly detection
-
- G—PHYSICS
- G06—COMPUTING OR CALCULATING; COUNTING
- G06F—ELECTRIC DIGITAL DATA PROCESSING
- G06F11/00—Error detection; Error correction; Monitoring
- G06F11/30—Monitoring
-
- G—PHYSICS
- G06—COMPUTING OR CALCULATING; COUNTING
- G06F—ELECTRIC DIGITAL DATA PROCESSING
- G06F11/00—Error detection; Error correction; Monitoring
- G06F11/30—Monitoring
- G06F11/34—Recording or statistical evaluation of computer activity, e.g. of down time, of input/output operation ; Recording or statistical evaluation of user activity, e.g. usability assessment
-
- G—PHYSICS
- G06—COMPUTING OR CALCULATING; COUNTING
- G06F—ELECTRIC DIGITAL DATA PROCESSING
- G06F11/00—Error detection; Error correction; Monitoring
- G06F11/30—Monitoring
- G06F11/34—Recording or statistical evaluation of computer activity, e.g. of down time, of input/output operation ; Recording or statistical evaluation of user activity, e.g. usability assessment
- G06F11/3466—Performance evaluation by tracing or monitoring
- G06F11/3476—Data logging
-
- G—PHYSICS
- G06—COMPUTING OR CALCULATING; COUNTING
- G06F—ELECTRIC DIGITAL DATA PROCESSING
- G06F21/00—Security arrangements for protecting computers, components thereof, programs or data against unauthorised activity
- G06F21/50—Monitoring users, programs or devices to maintain the integrity of platforms, e.g. of processors, firmware or operating systems
- G06F21/55—Detecting local intrusion or implementing counter-measures
- G06F21/552—Detecting local intrusion or implementing counter-measures involving long-term monitoring or reporting
-
- H—ELECTRICITY
- H04—ELECTRIC COMMUNICATION TECHNIQUE
- H04L—TRANSMISSION OF DIGITAL INFORMATION, e.g. TELEGRAPHIC COMMUNICATION
- H04L41/00—Arrangements for maintenance, administration or management of data switching networks, e.g. of packet switching networks
- H04L41/50—Network service management, e.g. ensuring proper service fulfilment according to agreements
- H04L41/5061—Network service management, e.g. ensuring proper service fulfilment according to agreements characterised by the interaction between service providers and their network customers, e.g. customer relationship management
- H04L41/5067—Customer-centric QoS measurements
-
- H—ELECTRICITY
- H04—ELECTRIC COMMUNICATION TECHNIQUE
- H04L—TRANSMISSION OF DIGITAL INFORMATION, e.g. TELEGRAPHIC COMMUNICATION
- H04L63/00—Network architectures or network communication protocols for network security
- H04L63/14—Network architectures or network communication protocols for network security for detecting or protecting against malicious traffic
- H04L63/1408—Network architectures or network communication protocols for network security for detecting or protecting against malicious traffic by monitoring network traffic
- H04L63/1416—Event detection, e.g. attack signature detection
-
- H—ELECTRICITY
- H04—ELECTRIC COMMUNICATION TECHNIQUE
- H04W—WIRELESS COMMUNICATION NETWORKS
- H04W12/00—Security arrangements; Authentication; Protecting privacy or anonymity
- H04W12/12—Detection or prevention of fraud
- H04W12/121—Wireless intrusion detection systems [WIDS]; Wireless intrusion prevention systems [WIPS]
- H04W12/122—Counter-measures against attacks; Protection against rogue devices
-
- H—ELECTRICITY
- H04—ELECTRIC COMMUNICATION TECHNIQUE
- H04W—WIRELESS COMMUNICATION NETWORKS
- H04W4/00—Services specially adapted for wireless communication networks; Facilities therefor
- H04W4/30—Services specially adapted for particular environments, situations or purposes
- H04W4/40—Services specially adapted for particular environments, situations or purposes for vehicles, e.g. vehicle-to-pedestrians [V2P]
Definitions
- This application is a system for detecting and analyzing cyber attacks, and relates to a security attack detection / analysis system mainly consisting of a log management device mounted on a mobile body and a center device installed outside the mobile body.
- V2X vehicle-to-vehicle communication and road-to-vehicle communication
- vehicles have come to be equipped with a communication function, and so-called vehicles are becoming more connected.
- vehicles are more likely to be subject to cyberattacks. Since vehicles move at high speeds, they may lose control over cyber attacks, requiring stronger defenses against cyber attacks.
- Patent Document 1 describes a log output device or the like that determines whether or not a security log needs to be output.
- a security sensor is mounted on an electronic control unit (ECU) mounted on a moving vehicle, and the security sensor monitors the communication of the ECU itself and the ECU and outputs a security log.
- ECU electronice control unit
- the center device has a higher processing capacity than the electronic control device mounted on the vehicle. Therefore, even if the electronic control device mounted on the vehicle cannot detect the abnormality, the center device may be able to detect the abnormality. Further, even when the center device detects an abnormality, the information such as the security log may not be sufficient. In this case, if additional information can be obtained from the vehicle or a vehicle of the same type, more accurate abnormality detection can be performed and analysis can be performed on a plurality of vehicles.
- the log management device obtains statistical calculation results by performing statistical analysis of a plurality of logs, a log collecting unit that receives logs generated by a security sensor, a storage unit that stores the logs, and a plurality of logs. It has a statistical analysis unit and a transmission unit that transmits the log or the statistical calculation result according to a predetermined condition.
- a log management method is a log management method executed by a log management device, which receives a log generated by a security sensor, saves the log, and performs statistical analysis of a plurality of the logs. By doing so, the statistical calculation result is obtained, and the log or the statistical calculation result is transmitted according to a predetermined condition.
- the log management program is a log management program that can be executed by a log management device, receives a log generated by a security sensor, stores the log, and performs statistical analysis of a plurality of the logs. By doing so, the statistical calculation result is obtained, and the log or the statistical calculation result is transmitted according to a predetermined condition.
- the security attack detection / analysis system is a security attack detection / analysis system including a log management device and a center device, and the log management device receives a log generated by a security sensor and collects logs.
- a unit, a storage unit that stores the log, a statistical analysis unit that obtains a statistical calculation result by performing statistical analysis of a plurality of the logs, and a log or the statistical calculation result are transmitted according to predetermined conditions.
- the center device has a transmission unit, and the center device analyzes the log or the statistical calculation result with a receiving unit that receives the log or the statistical calculation result, and further logs or additional statistics based on the analysis result. It has an analysis unit that generates an upload request requesting upload of the calculation result, and a transmission unit that transmits the upload request to the log management device.
- the center device can perform attack analysis and collect necessary information.
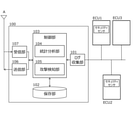
- FIG. 1 is a diagram showing a configuration example of the security attack detection / analysis system according to the embodiment of the present disclosure.
- FIG. 2 is a block diagram showing a configuration example of the log management device according to the embodiment of the present disclosure.
- FIG. 3 is a block diagram showing a configuration example of the center device according to the embodiment of the present disclosure.
- FIG. 4 is a flowchart showing the operation of the log management device according to the embodiment of the present disclosure.
- FIG. 5 is a flowchart showing the operation of the log management device according to the embodiment of the present disclosure.
- FIG. 6 is a flowchart showing the operation of the center device according to the embodiment of the present disclosure.
- FIG. 7 is a flowchart showing the operation of the center device according to the embodiment of the present disclosure.
- the configuration and method described in the dependent clause of the claims are arbitrary configurations and methods in the invention described in the independent clause of the claims.
- the configurations and methods of the embodiments corresponding to the configurations and methods described in the dependent terms, and the configurations and methods described only in the embodiments not described in the claims are arbitrary configurations and methods in the present invention.
- the configuration and method described in the embodiment when the description of the claims is broader than the description of the embodiment is also an arbitrary configuration and method in the present invention in the sense that it is an example of the configuration and method of the present invention. In either case, by describing in the independent clause of the claims, it becomes an essential configuration and method of the present invention.
- the effect described in the embodiment is an effect when the configuration of the embodiment as an example of the present invention is provided, and is not necessarily the effect of the present invention.
- the configuration disclosed in each embodiment is not closed only in each embodiment, but can be combined across the embodiments.
- the configuration disclosed in one embodiment may be combined with another embodiment.
- the disclosed configurations may be collected and combined in each of the plurality of embodiments.
- the security attack detection / analysis system 1 includes a log management device 100 and a center device 200.
- the log management device 100 is connected to the center device 200 via the communication network 2.
- the log management device 100 is "mounted" on a vehicle that is a "moving body".
- the "moving body” means a movable object, and the moving speed is arbitrary.
- the moving body is stopped.
- "mounted” includes the case where it is directly fixed to the moving body and the case where it is not fixed to the moving body but moves together with the moving body.
- it may be possessed by a person in a moving body, or it may be mounted on a cargo placed on the moving body.
- the communication network 2 is, for example, IEEE 802.11 (WiFi (registered trademark)), IEEE 802.16 (WiMAX (registered trademark)), W-CDMA (Wideband Code Division Multiple Access), HSPA (High Speed). Packet Access), LTE (Long Term Evolution), LTE-A (Long Term Evolution Advanced), 4G, 5G and the like can be used. Alternatively, DSRC (Dedicated Short Range Communication) can be used.
- a wired communication system for example, a LAN (Local Area Network), the Internet, or a fixed telephone line can be used as the communication network.
- the wireless communication network may be a combination of a wireless communication method and a wired communication method.
- a wireless communication method is used between the log management device 100 and the base station device in the cellular system
- a wired communication method such as a trunk line of a telecommunications carrier or the Internet is used between the base station device and the center device 200. It may be connected.
- the log management device 100 includes a log collection unit 101, a storage unit 102, a control unit 103, a transmission unit 106, and a reception unit 107. Further, the control unit 103 realizes the statistical analysis unit 104 and the attack detection unit 105.
- the log management device 100 may be composed of a general-purpose CPU (Central Processing Unit), a volatile memory such as RAM, a ROM, a flash memory, a non-volatile memory such as a hard disk, various interfaces, and an internal bus connecting them. can. Then, by executing the software on these hardware, it can be configured to exert the function of each functional block shown in FIG. The same applies to the center device 200 shown in FIG. 3 described later.
- the log management device 100 may be realized by dedicated hardware such as LSI.
- the log management device 100 assumes the form of an electronic control unit (ECU (Electric Control Unit), hereinafter abbreviated as ECU) as a semi-finished product, but the present invention is not limited to this.
- ECU Electronic Control Unit
- the form of a component includes a semiconductor circuit or a semiconductor module
- the form of a finished product includes a personal computer (PC), a smartphone, a mobile phone, and a navigation system.
- the log management device 100 may be composed of a plurality of ECUs in addition to a single ECU.
- the communication ECU may be in charge of communication with the outside.
- the plurality of ECUs including the communication ECU may be grasped as the log management device 100 of the present embodiment.
- the log collection unit 101 is connected to a single or a plurality of ECUs connected to the log management device 100 via an in-vehicle network, and receives security logs transmitted from security sensors provided in each ECU.
- the security sensor monitors the communication of each ECU itself and each ECU, detects an abnormality such as an attack, and makes a normal report or an abnormality report by the security log.
- the log collecting unit 101 is connected to the ECU 1, the ECU 2, and the ECU 3 via an in-vehicle network.
- the ECU 1 and the ECU 2 are provided with a security sensor that monitors the communication of each ECU itself and each ECU.
- the ECU 3 is not provided with a security sensor.
- the ECU 1, ECU 2, and ECU 3 may be provided with a defense function and a function of generating a log for notifying each ECU operating state. Then, instead of the security log, or together with the security log, this log may be the processing target of the present embodiment.
- the ECU 1, ECU 2, and ECU 3 are arbitrary ECUs, such as a drive system electronic control device that controls the engine, steering wheel, brake, etc., a vehicle body system electronic control device that controls meters, power windows, etc., a navigation device, and the like. Examples thereof include an information system electronic control device or a safety control system electronic control device that controls for preventing collision with an obstacle or a pedestrian. Further, the ECUs may not be in parallel but may be classified into a master and a slave.
- any communication method such as Ethernet (registered trademark), Wi-Fi (registered trademark), and Bluetooth (registered trademark) can be used. Can be used.
- the storage unit 102 stores the security log collected by the log collection unit 101 from the log collection unit 101 via the control unit 103 or directly from the log collection unit 101.
- the statistical calculation result obtained by the statistical analysis unit 104 which will be described later, may also be saved.
- the storage unit 102 is composed of a non-volatile memory or a volatile memory.
- the control unit 103 controls the operations of the log collection unit 101, the storage unit 102, the transmission unit 106, and the reception unit 107. Further, the control unit 103 itself realizes the statistical analysis unit 104 and the attack detection unit 105.
- the statistical analysis unit 104 obtains the statistical calculation result by performing statistical analysis of a plurality of security logs collected by the log collection unit 101.
- Examples of statistical analysis include, for example, the number of occurrences, frequency, temporal distribution, or correlation of security logs of the same type. Other examples include the number of times, frequency, temporal distribution, and correlation of attack detection results identified by the attack detection unit 105 described later from the security log.
- the statistical analysis of security logs includes both direct and indirect statistical analysis of security logs.
- the attack detection unit 105 detects an attack based on the security log collected by the log collection unit 101, and obtains an attack detection result.
- the attack detection has a plurality of stages such as attack identification, attack route identification, and damage location identification, and the attack detection unit 105 may be able to perform at least one of these stages.
- Attack identification means identifying that the anomaly is derived from a security attack.
- Attack route identification refers to identifying which ECU or which network is being attacked. Identifying the damaged part means identifying which ECU or which network is damaged.
- the attack detection result obtained by the attack detection unit 105 may be analyzed by the statistical analysis unit 104. In this case, the security log is indirectly statistically analyzed.
- the transmission unit 106 transmits the security log or the statistical calculation result to the center device via the antenna A according to the “predetermined condition”.
- the security log or the statistical calculation result is transmitted according to the "predetermined condition”.
- predetermined conditions include the number of attack detections, the upload request received from the center device, and the amount of security logs in addition to the upload request, which will be described later in the section on operation of the log management device. .. Whether or not the predetermined condition is satisfied can be determined by the control unit 103.
- the "predetermined condition" may be an internal condition related to a log or a statistical calculation result, or an external condition based on an instruction or information from another device.
- the transmission unit 106 transmits the security log and the statistical calculation result to the communication ECU. However, even in this case, the transmission unit 106 must transmit the security log and the statistical calculation result to the center device via the communication ECU.
- the receiving unit 107 receives an upload request for uploading the security log and the statistical calculation result from the center device 200 via the antenna A.
- the center device 200 has a receiving unit 201, a control unit 202, a storage unit 204, and a transmitting unit 205. Further, the control unit 202 realizes the analysis unit 203.
- the center device 200 assumes the form of a server device as a finished product in the present embodiment, but is not limited to this.
- a workstation a personal computer (PC) as a form of a finished product
- an ECU as a form of a semi-finished product
- a semiconductor circuit element as a form of a component
- the receiving unit 201 receives the security log or statistical calculation result transmitted from the log management device 100 via the antenna A.
- the control unit 202 controls the operations of the reception unit 201, the storage unit 204, and the transmission unit 205. Further, the control unit 202 itself realizes the analysis unit 203.
- the analysis unit 203 analyzes the security log or the statistical calculation result received by the reception unit 201. Then, based on the analysis result, an upload request for requesting the log management device 100 to upload an additional log or an additional statistical calculation result is generated.
- the transmission target of the upload request is not limited to the log management device 100 of the receiving source received by the receiving unit 201.
- the log management device 100 mounted on another vehicle of the same type may be the transmission target.
- “same type” is sufficient if there is some commonality, such as when the same vehicle type is installed, when the same parts are installed, when the same platform is installed, and so on.
- the storage unit 204 stores the security log and statistical calculation results received by the reception unit 201. Further, the upload request generated by the analysis unit 203 may be saved.
- the transmission unit 205 transmits an upload request to the log management device 100 that is the source of the security log and the statistical calculation result, and / or to the log management device 100 mounted on another vehicle of the same type. ..
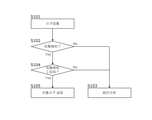
- FIG. 4 is an operation related to steady log collection of the log management device 100.
- the log collecting unit 101 receives the security logs generated and transmitted by the security sensors of the ECU 1 and the ECU 2 (S101). Then, the storage unit 102 stores the security log.
- the attack detection unit 105 detects an attack based on the received security log (S102).
- the attack detection may be at least one of attack identification, attack route identification, and damage location identification. If no attack is detected (S102: No), statistical analysis is performed on the normal log and the statistical calculation result is obtained. When an attack is detected (S102: Yes), the process is transferred to S104.
- the statistical analysis unit 104 obtains a statistical calculation result by performing statistical analysis. Further, when the predetermined condition is the number of attack detections, the control unit 103 instructs the transmission unit 106 to transmit the security log to the center device 200 when the attack detection is "or less" than the predetermined number of times, and transmits the security log. The unit 106 transmits the security log to the center device 200. Further, when the attack detection is “or more” a predetermined number of times, the control unit 103 waits for the upload request from the center device 200, instructs the transmission unit 106 to transmit the statistical calculation result to the center device 200, and transmits the result.
- the unit 106 transmits the statistical calculation result to the center device 200.
- “or more” includes both the case where a predetermined number of times is included and the case where the predetermined number of times is not included.
- the term “less than or equal to” includes both the case where a predetermined number of times is included and the case where the predetermined number of times is not included.
- the control unit 103 transmits the security log used for performing the attack detection to the transmission unit 106 to the center device 200. Instruct. Then, the transmission unit 106 transmits the security log to the center device 200 (S105). In addition to the security log, the vehicle information indicating the vehicle state output by the vehicle condition monitoring function (not shown) and the statistical calculation result of the vehicle information may be transmitted together. The same applies to the next paragraph.
- the statistical analysis unit 104 when the attack is detected for the second time or more as a predetermined condition (S104: No), the statistical analysis unit 104 performs statistical analysis of a plurality of security logs and obtains a statistical calculation result (S103). For example, the number of occurrences, frequency, temporal distribution, correlation, etc. of the same type of security log are obtained. Alternatively, the number, frequency, temporal distribution, correlation, and the like of the attack detection result specified by the attack detection unit 105 from the security log are obtained. The obtained statistical calculation result is not immediately transmitted, the control unit 103 instructs the transmission unit 106 to wait for the upload request from the center device 200 and transmit the statistical calculation result, and the transmission unit 106 transmits the statistical calculation result. do. If the statistical calculation result is sent, the number of attacks is reset. However, the obtained statistical calculation result may be promptly transmitted from the transmission unit 106.
- the predetermined number of times is set to 1 as a predetermined condition, but the predetermined number of times may be set to 2 or more.
- the predetermined number of times is 3, the security log is transmitted up to 3 times of abnormality detection, statistical analysis is performed 4 times or more to obtain the statistical calculation result, and the upload request from the center device 200 is waited for.
- the statistical calculation result may be transmitted.
- a condition other than the number of times of attack detection may be set. For example, it may be the number of times the security log is received or the frequency of reception.
- the predetermined conditions may be automatically changed as needed or according to the conditions.
- the content of the statistical analysis may also be automatically changeable as needed or according to conditions.
- the transmission target is either the security log or the statistical calculation result according to the number of attacks, it is not necessary to transmit all the logs to the center device, and the communication volume is reduced. can do. Further, since the statistical calculation result is transmitted after waiting for the request from the center device 200, it is sufficient to transmit the statistical calculation result when it is determined that the center device 200 is necessary, and the communication amount is reduced. can do. Further, according to the present embodiment, since the center device 200 does not need to obtain the statistical calculation result, the processing amount can be reduced.
- FIG. 5 shows an operation when the log management device 100 receives an upload request from the center device 200. That is, the upload request is a predetermined condition.
- the receiving unit 107 receives an upload request from the center device 200 (S111).
- the control unit 103 determines whether the security log or the statistical calculation result can be transmitted (S112).
- Vehicle information output by the vehicle condition monitoring function (not shown) is used for the determination. For example, it is determined that transmission is not possible because only standby power is available when the vehicle is in sleep mode (S112: No). When it is determined that transmission is possible (S112: Yes), the process is transferred to S113.
- the control unit 103 sends the security log to the center device 200 when the amount of the security log is a predetermined number "or less” 106.
- the transmission unit 106 transmits the security log to the center device 200.
- the control unit 103 instructs the transmission unit 106 to transmit the statistical calculation result to the center device 200 when the amount of security logs is a predetermined number “or more”, and the transmission unit 106 sends the statistical calculation result to the center device.
- the "quantity” includes not only the size of the log but also the number of logs and the frequency of receiving logs. “More than” includes both cases where a predetermined number of times is included and cases where it is not included. The term “less than or equal to” includes both the case where a predetermined number of times is included and the case where the predetermined number of times is not included.
- the control unit 103 instructs the transmission unit 106 to transmit the security logs to the center device 200. Then, the transmission unit 106 transmits the security log to the center device 200 (S114).
- the control unit 103 instructs the transmission unit 106 to transmit the statistical calculation result to the center device 200. Then, the transmission unit 106 transmits the statistical calculation result to the center device 200 (S115).
- the statistical analysis unit 104 performs statistical analysis of the reason why the security log cannot be transmitted in order to analyze the factor that the security log cannot be transmitted (S116). Then, when transmission becomes possible (S117: Yes), the process is transferred to S113 according to the latest upload request among the upload requests received so far.
- An example of the case where transmission becomes possible is the time of the next IG-ON (ignition on).
- the statistical calculation result of the statistical analysis of the reason why transmission cannot be performed may be transmitted.
- the number of security logs is set to 1 as a predetermined condition, but it may be set to 2 or more.
- the security logs may be transmitted up to the number of security logs of 3, and the statistical calculation result may be transmitted when the number of security logs is 4 or more.
- a condition other than the number of security logs may be set.
- the predetermined conditions may be automatically changed as needed or according to the conditions.
- the content of the statistical analysis may also be automatically changeable as needed or according to conditions.
- the transmission target is either the security log or the statistical calculation result according to the number of security logs, it is not necessary to transmit all the logs to the center device, and the communication volume is reduced. Can be reduced.
- the statistical calculation result is transmitted after waiting for the request from the center device 200, it is sufficient to transmit the statistical calculation result when it is determined that the center device 200 is necessary, and the communication amount is reduced. can do.
- the center device 200 does not need to obtain the statistical calculation result that needs to be performed in the process of analysis, so that the processing amount can be reduced. That is, the amount of communication with the center device 200 can be reduced without lowering the analysis accuracy of the center device 200.
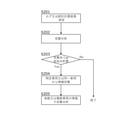
- FIG. 6 shows an operation when a security log or a statistical calculation result is received from the log management device 100 of the vehicle.
- the receiving unit 201 of the center device 200 receives the security log or the statistical calculation result transmitted from the specific vehicle (S201).
- the security log or statistical calculation result received here is a security log (S105) or statistical calculation result (S103) based on steady log collection of the log management device 100 of a specific vehicle as shown in FIG. It may also be a security log (S114) or a statistical calculation result (S115) transmitted in response to an upload request from the center device 200 as shown in FIG. That is, the flowchart of FIG. 6 is connected to and executed with reference to FIGS. 4 and 5.
- the analysis unit 203 performs attack analysis using the security log or statistical calculation result received in S201 (S202).
- the attack analysis may be performed by the same algorithm as the attack detection unit 105 of the vehicle log management device 100, but more precise attack analysis may be performed.
- As the attack analysis method a known method can be used.
- the analysis unit 203 determines that there is an attack on a specific vehicle, or if it cannot determine whether or not there is an attack and it is determined that additional analysis is necessary (S203: Yes), the analysis unit 203 shifts the processing to S204. At this time, it is further determined whether the information required for additional analysis is required only from the specific vehicle, whether the same vehicle type such as the existence of a security hole is in danger, or whether it is necessary to collect information widely. You may. When the analysis unit 203 determines that there is no attack on the specific vehicle, the analysis unit 203 ends the process.
- the analysis unit 203 instructs the transmission unit 205 to transmit an upload request in order to collect information from a specific vehicle or a part or all of the same vehicle type as the specific vehicle (S204). Then, the transmission unit 205 transmits an upload request to a specific vehicle or a part or all of the same vehicle type as the specific vehicle.
- the transmission destination of the same vehicle type can be specified by using the vehicle registration data stored in the storage unit 204 of the center device 200.
- the receiving unit 201 receives the security log or the statistical calculation result from a single vehicle which is a specific vehicle, or a plurality of vehicles which are a part or all of the same vehicle type as the specific vehicle. Then, the analysis unit 203 performs an attack analysis using these information (S205).
- a specific vehicle may or may not be included in the plurality of vehicles.
- the center device 200 can perform attack analysis, and can collect necessary information widely and perform attack analysis.
- FIG. 7 is an operation when a security log or a statistical calculation result is received from the vehicle log management device 100, as in FIG. The same steps as in FIG. 6 are omitted by quoting the description of FIG.
- the analysis unit 203 When the analysis unit 203 receives the security log from the specific vehicle in S201, the analysis unit 203 confirms with the storage unit 204 whether the statistical calculation result has been received / stored from the specific vehicle in the past (S211). If it has not been received in the past (S211: No), the analysis unit 203 instructs the transmission unit 205 to transmit an additional upload request for the statistical calculation result to the specific vehicle. Then, the transmission unit 205 transmits an additional upload request (S212). If it has been received in the past (S211: Yes), the process is transferred to S202.
- the accuracy of attack analysis can be improved by sufficiently collecting information from a specific vehicle.
- predetermined conditions are the number of attack detections and the number of security logs, but the installation location of the security sensor (for example) Depending on the importance of the communication bus to which the specific ECU) and the security sensor are connected, predetermined conditions may be set automatically or manually. For example, it may be possible to set the number of times of attack detection as a predetermined condition.
- safety-related information and privacy-related information such as location information
- other logs and predetermined conditions may be changed.
- the amount of unprocessed raw data can be increased by increasing the number of attack detections and the number of security logs as predetermined conditions.
- the amount of raw data for which the content of privacy is directly revealed can be reduced by reducing the number of attack detections and the number of security logs as predetermined conditions.
- Priority of target log and statistical calculation result When sending the target log, for example, prioritize safety-related information and privacy-related information such as location information, and send it in preference to other logs. You may do so.
- the log collection unit (101) that receives the log generated by the security sensor, and A storage unit (102) for storing the log, and A transmission unit (106) that transmits the log to the outside, It has a statistical analysis unit (104) that obtains statistical calculation results by performing statistical analysis of a plurality of the logs.
- the transmission unit is a log management device (100) that transmits the statistical calculation result to the outside instead of the log when a predetermined condition is satisfied.
- the block diagram used in the explanation of the embodiment is a classification and arrangement of the configuration of the device according to the function.
- the blocks showing each function are realized by any combination of hardware or software. Further, since the block diagram shows the function, the block diagram can be grasped as the disclosure of the invention of the method and the invention of the program that realizes the method.
- Each embodiment is premised on a log management device for a vehicle mounted on a vehicle, but the present invention also includes a dedicated or general-purpose log management device other than that for a vehicle, unless otherwise limited in the claims. It is a vehicle.
- Examples of the form of the component include a semiconductor element, an electronic circuit, a module, and a microcomputer.
- Examples of the semi-finished product include an electronic control unit (ECU) and a system board.
- Examples of finished products include mobile phones, smartphones, tablets, personal computers (PCs), workstations, and servers.
- it includes a device having a communication function and the like, and examples thereof include a video camera, a still camera, and a car navigation system.
- center device of the present disclosure is used for the purpose of providing various services. With the provision of such services, the Center Equipment of the present disclosure will be used, the methods of the present disclosure will be used, and / and the programs of the present disclosure will be executed.
- the present disclosure can be realized not only by the dedicated hardware having the configuration and the function described in each embodiment, but also a program for realizing the present disclosure recorded on a recording medium such as a memory or a hard disk, and a program thereof. It can also be realized as a combination with a general-purpose hardware having an executable dedicated or general-purpose CPU and a memory or the like.
- Programs stored in non-transitional substantive recording media of dedicated or general-purpose hardware for example, external storage devices (for example, hard disks, USB memory, CD / BD, etc.) or internal storage devices (RAM, ROM, etc.)
- dedicated or general-purpose hardware for example, external storage devices (for example, hard disks, USB memory, CD / BD, etc.) or internal storage devices (RAM, ROM, etc.)
- RAM, ROM, etc. Programs stored in non-transitional substantive recording media of dedicated or general-purpose hardware
- dedicated or general-purpose hardware for example, external storage devices (for example, hard disks, USB memory, CD / BD, etc.) or internal storage devices (RAM, ROM, etc.)
- RAM random access memory
- ROM read only memory
- Programs stored in non-transitional substantive recording media of dedicated or general-purpose hardware for example, external storage devices (for example, hard disks, USB memory, CD / BD, etc.) or internal storage devices (RAM, ROM, etc.)
- the log management device of the present disclosure has been described as an electronic control device mainly for vehicles mounted on automobiles, it is applied to all moving objects such as pedestrians, ships, aircraft, as well as motorcycles, bicycles with electric motors, and railways. It is possible to apply. In addition, it can be applied to devices used for various purposes such as mobile phones, tablets, and game machines.
Landscapes
- Engineering & Computer Science (AREA)
- Computer Security & Cryptography (AREA)
- General Engineering & Computer Science (AREA)
- Theoretical Computer Science (AREA)
- Computer Hardware Design (AREA)
- Signal Processing (AREA)
- Computer Networks & Wireless Communication (AREA)
- Physics & Mathematics (AREA)
- General Physics & Mathematics (AREA)
- Software Systems (AREA)
- Computing Systems (AREA)
- Quality & Reliability (AREA)
- General Business, Economics & Management (AREA)
- Business, Economics & Management (AREA)
- Debugging And Monitoring (AREA)
- Telephonic Communication Services (AREA)
Priority Applications (3)
| Application Number | Priority Date | Filing Date | Title |
|---|---|---|---|
| DE112021003762.5T DE112021003762T5 (de) | 2020-07-14 | 2021-06-03 | Protokollverwaltungsvorrichtung, Protokollverwaltungsverfahren, Protokollverwaltungsprogramm, und Sicherheitsangriff-Erfassungs- und Analysesystem |
| CN202180048919.6A CN115803737A (zh) | 2020-07-14 | 2021-06-03 | 日志管理装置以及安全攻击检测/分析系统 |
| US18/151,680 US12341798B2 (en) | 2020-07-14 | 2023-01-09 | Log management device, log management method, computer program product, and security attack detection and analyzing system |
Applications Claiming Priority (2)
| Application Number | Priority Date | Filing Date | Title |
|---|---|---|---|
| JP2020120721A JP7392598B2 (ja) | 2020-07-14 | 2020-07-14 | ログ管理装置及びセキュリティ攻撃検知・分析システム |
| JP2020-120721 | 2020-07-14 |
Related Child Applications (1)
| Application Number | Title | Priority Date | Filing Date |
|---|---|---|---|
| US18/151,680 Continuation US12341798B2 (en) | 2020-07-14 | 2023-01-09 | Log management device, log management method, computer program product, and security attack detection and analyzing system |
Publications (1)
| Publication Number | Publication Date |
|---|---|
| WO2022014193A1 true WO2022014193A1 (ja) | 2022-01-20 |
Family
ID=79555714
Family Applications (1)
| Application Number | Title | Priority Date | Filing Date |
|---|---|---|---|
| PCT/JP2021/021285 Ceased WO2022014193A1 (ja) | 2020-07-14 | 2021-06-03 | ログ管理装置及びセキュリティ攻撃検知・分析システム |
Country Status (5)
| Country | Link |
|---|---|
| US (1) | US12341798B2 (enExample) |
| JP (1) | JP7392598B2 (enExample) |
| CN (1) | CN115803737A (enExample) |
| DE (1) | DE112021003762T5 (enExample) |
| WO (1) | WO2022014193A1 (enExample) |
Cited By (1)
| Publication number | Priority date | Publication date | Assignee | Title |
|---|---|---|---|---|
| WO2024071120A1 (ja) * | 2022-09-30 | 2024-04-04 | 株式会社デンソー | 情報処理装置、情報処理システム、情報処理プログラム、情報処理方法 |
Families Citing this family (1)
| Publication number | Priority date | Publication date | Assignee | Title |
|---|---|---|---|---|
| JP7765872B2 (ja) * | 2022-04-15 | 2025-11-07 | 株式会社デンソー | ログ管理装置及びログ管理分析システム |
Citations (3)
| Publication number | Priority date | Publication date | Assignee | Title |
|---|---|---|---|---|
| JP2018032254A (ja) * | 2016-08-25 | 2018-03-01 | クラリオン株式会社 | 車載装置、ログ収集システム |
| JP2019087277A (ja) * | 2016-12-06 | 2019-06-06 | パナソニック インテレクチュアル プロパティ コーポレーション オブ アメリカPanasonic Intellectual Property Corporation of America | 情報処理装置及び情報処理方法 |
| WO2019193786A1 (ja) * | 2018-04-06 | 2019-10-10 | パナソニック インテレクチュアル プロパティ コーポレーション オブ アメリカ | ログ出力方法、ログ出力装置及びプログラム |
Family Cites Families (9)
| Publication number | Priority date | Publication date | Assignee | Title |
|---|---|---|---|---|
| US20060217116A1 (en) * | 2005-03-18 | 2006-09-28 | Cassett Tia M | Apparatus and methods for providing performance statistics on a wireless communication device |
| JP2010039878A (ja) * | 2008-08-07 | 2010-02-18 | Hitachi Ltd | ログ管理システムおよびログ表示システム |
| US8839435B1 (en) * | 2011-11-04 | 2014-09-16 | Cisco Technology, Inc. | Event-based attack detection |
| JP6665503B2 (ja) * | 2015-12-04 | 2020-03-13 | 株式会社Ihi | データ収集システム、データ収集装置及びデータ収集方法 |
| JP6490879B2 (ja) | 2016-12-06 | 2019-03-27 | パナソニック インテレクチュアル プロパティ コーポレーション オブ アメリカPanasonic Intellectual Property Corporation of America | 情報処理装置及び情報処理方法 |
| CN107547740A (zh) * | 2017-08-28 | 2018-01-05 | 江西博瑞彤芸科技有限公司 | 电台列表的管理方法及系统 |
| US12101338B2 (en) * | 2018-06-08 | 2024-09-24 | Nvidia Corporation | Protecting vehicle buses from cyber-attacks |
| JP7156869B2 (ja) | 2018-09-03 | 2022-10-19 | パナソニックホールディングス株式会社 | ログ出力装置、ログ出力方法およびログ出力システム |
| JP2020120721A (ja) | 2019-01-29 | 2020-08-13 | 株式会社三共 | 遊技機 |
-
2020
- 2020-07-14 JP JP2020120721A patent/JP7392598B2/ja active Active
-
2021
- 2021-06-03 DE DE112021003762.5T patent/DE112021003762T5/de active Pending
- 2021-06-03 WO PCT/JP2021/021285 patent/WO2022014193A1/ja not_active Ceased
- 2021-06-03 CN CN202180048919.6A patent/CN115803737A/zh active Pending
-
2023
- 2023-01-09 US US18/151,680 patent/US12341798B2/en active Active
Patent Citations (3)
| Publication number | Priority date | Publication date | Assignee | Title |
|---|---|---|---|---|
| JP2018032254A (ja) * | 2016-08-25 | 2018-03-01 | クラリオン株式会社 | 車載装置、ログ収集システム |
| JP2019087277A (ja) * | 2016-12-06 | 2019-06-06 | パナソニック インテレクチュアル プロパティ コーポレーション オブ アメリカPanasonic Intellectual Property Corporation of America | 情報処理装置及び情報処理方法 |
| WO2019193786A1 (ja) * | 2018-04-06 | 2019-10-10 | パナソニック インテレクチュアル プロパティ コーポレーション オブ アメリカ | ログ出力方法、ログ出力装置及びプログラム |
Cited By (2)
| Publication number | Priority date | Publication date | Assignee | Title |
|---|---|---|---|---|
| WO2024071120A1 (ja) * | 2022-09-30 | 2024-04-04 | 株式会社デンソー | 情報処理装置、情報処理システム、情報処理プログラム、情報処理方法 |
| JP2024051738A (ja) * | 2022-09-30 | 2024-04-11 | 株式会社デンソー | 情報処理装置、情報処理システム、情報処理プログラム、情報処理方法 |
Also Published As
| Publication number | Publication date |
|---|---|
| US20230156027A1 (en) | 2023-05-18 |
| US12341798B2 (en) | 2025-06-24 |
| JP2022017889A (ja) | 2022-01-26 |
| CN115803737A (zh) | 2023-03-14 |
| JP7392598B2 (ja) | 2023-12-06 |
| DE112021003762T5 (de) | 2023-04-27 |
Similar Documents
| Publication | Publication Date | Title |
|---|---|---|
| JP7255710B2 (ja) | 攻撃監視用センター装置、及び攻撃監視用端末装置 | |
| US11711387B2 (en) | Security management device, security management method, and computer program executed by security management device | |
| JP7571844B2 (ja) | ログ管理装置及びセンタ装置 | |
| US12177239B2 (en) | Attack analyzer, attack analysis method and attack analysis program | |
| WO2022014193A1 (ja) | ログ管理装置及びセキュリティ攻撃検知・分析システム | |
| US11667264B2 (en) | Unauthorized intrusion prevention device, unauthorized intrusion prevention method, and unauthorized intrusion prevention program | |
| US20240039949A1 (en) | Attack estimation verification device, attack estimation verification method, and storage medium storing attack estimation verification program | |
| US12166781B2 (en) | Attack analyzer for accurate estimation of attack route | |
| JP7380473B2 (ja) | セキュリティ監視システム | |
| US20250350618A1 (en) | Log management device, log management system, method and storage medium thereof | |
| JP7728063B2 (ja) | ログ管理装置、ログ管理方法、及びログ管理プログラム | |
| US20240089281A1 (en) | Attack analysis device, attack analysis method, and storage medium | |
| JP7765872B2 (ja) | ログ管理装置及びログ管理分析システム | |
| JP2024169239A (ja) | ログ収集装置、ログ収集方法、ログ収集プログラム、及びログ送信装置 | |
| US20250323793A1 (en) | Log generation device, sensor module, log generation module, and electronic control system | |
| US20250077651A1 (en) | Abnormality monitoring device, center device, abnormality monitoring method, and abnormality monitoring program | |
| US20250286902A1 (en) | Log determination method, log determination device, and storage medium storing log determination program | |
| US20240208441A1 (en) | Electronic control unit, electronic control system, log processing method, and non-transitory computer-readable storage medium storing log processing program | |
| JP2020184120A (ja) | 通信電子制御装置、管理電子制御装置、及びアプリケーションインストール方法 | |
| JP2025170686A (ja) | ログ管理システム、ログ管理方法、ログ管理装置、及びログ管理プログラム | |
| JP2024168283A (ja) | 不正基地局検知装置、不正基地局検知方法、及び不正基地局検知プログラム | |
| JP2024100472A (ja) | 電子制御装置、セキュリティログ処理方法、及びセキュリティログ処理プログラム |
Legal Events
| Date | Code | Title | Description |
|---|---|---|---|
| 121 | Ep: the epo has been informed by wipo that ep was designated in this application |
Ref document number: 21842703 Country of ref document: EP Kind code of ref document: A1 |
|
| 122 | Ep: pct application non-entry in european phase |
Ref document number: 21842703 Country of ref document: EP Kind code of ref document: A1 |