EP2436166B1 - Interface de service - Google Patents
Interface de service Download PDFInfo
- Publication number
- EP2436166B1 EP2436166B1 EP10736596.7A EP10736596A EP2436166B1 EP 2436166 B1 EP2436166 B1 EP 2436166B1 EP 10736596 A EP10736596 A EP 10736596A EP 2436166 B1 EP2436166 B1 EP 2436166B1
- Authority
- EP
- European Patent Office
- Prior art keywords
- firewall
- network
- server
- user
- access
- Prior art date
- Legal status (The legal status is an assumption and is not a legal conclusion. Google has not performed a legal analysis and makes no representation as to the accuracy of the status listed.)
- Active
Links
- 238000000034 method Methods 0.000 claims description 13
- 238000013459 approach Methods 0.000 description 9
- 238000004891 communication Methods 0.000 description 3
- 238000013475 authorization Methods 0.000 description 2
- 241001522296 Erithacus rubecula Species 0.000 description 1
- 244000035744 Hura crepitans Species 0.000 description 1
- 240000002853 Nelumbo nucifera Species 0.000 description 1
- 235000006508 Nelumbo nucifera Nutrition 0.000 description 1
- 235000006510 Nelumbo pentapetala Nutrition 0.000 description 1
- 238000010276 construction Methods 0.000 description 1
- 230000003993 interaction Effects 0.000 description 1
- 238000000926 separation method Methods 0.000 description 1
- 238000011144 upstream manufacturing Methods 0.000 description 1
Images
Classifications
-
- H—ELECTRICITY
- H04—ELECTRIC COMMUNICATION TECHNIQUE
- H04L—TRANSMISSION OF DIGITAL INFORMATION, e.g. TELEGRAPHIC COMMUNICATION
- H04L63/00—Network architectures or network communication protocols for network security
- H04L63/02—Network architectures or network communication protocols for network security for separating internal from external traffic, e.g. firewalls
- H04L63/0209—Architectural arrangements, e.g. perimeter networks or demilitarized zones
-
- H—ELECTRICITY
- H04—ELECTRIC COMMUNICATION TECHNIQUE
- H04L—TRANSMISSION OF DIGITAL INFORMATION, e.g. TELEGRAPHIC COMMUNICATION
- H04L63/00—Network architectures or network communication protocols for network security
- H04L63/02—Network architectures or network communication protocols for network security for separating internal from external traffic, e.g. firewalls
- H04L63/0227—Filtering policies
- H04L63/0236—Filtering by address, protocol, port number or service, e.g. IP-address or URL
-
- H—ELECTRICITY
- H04—ELECTRIC COMMUNICATION TECHNIQUE
- H04L—TRANSMISSION OF DIGITAL INFORMATION, e.g. TELEGRAPHIC COMMUNICATION
- H04L63/00—Network architectures or network communication protocols for network security
- H04L63/08—Network architectures or network communication protocols for network security for authentication of entities
- H04L63/0815—Network architectures or network communication protocols for network security for authentication of entities providing single-sign-on or federations
-
- H—ELECTRICITY
- H04—ELECTRIC COMMUNICATION TECHNIQUE
- H04L—TRANSMISSION OF DIGITAL INFORMATION, e.g. TELEGRAPHIC COMMUNICATION
- H04L63/00—Network architectures or network communication protocols for network security
- H04L63/10—Network architectures or network communication protocols for network security for controlling access to devices or network resources
- H04L63/102—Entity profiles
Definitions
- the invention relates to a system for allowing access to services or computers from a first local area network in a second local area network, both networks being connected via a common intermediate area network (DMZ).
- DMZ common intermediate area network
- VPN virtual private network
- the object of the present invention is an alternative provision of services for users who work in a first private network and who need the services in a second private network.
- a scenario may exist if an employee who works for company A but is employed by company B wants to retrieve his e-mails stored in company B. To do this, he would normally have to dial into the company's network via a VPN connection with his computer in order to then be able to read the e-mails on his computer. However, this presupposes that the computer on which he is currently working has also installed the necessary client software and has the necessary access rights with respect to the firewall in network A of company A. From the " Citrix Access Gateway Enterprise Edition Administrator's Guide "November 2008 is the configuration of an Access Gateway of the corresponding manufacturer known. Out " Firewalls for Dummies "2003 Wiley Publishing is the configuration of firewalls known. The US 2005 / 198380A1 also concerns the control of network access.
- the object of the present invention is to provide access to services in a first local area network A from a second local area network B, where both networks are secured via a firewall, and both networks are connected via a network located between the firewalls. Access authorizations should be clarified and the restriction to certain services should be achieved.
- a network A secured by a firewall Fa is connected via a network Nab, in one possible embodiment designed as a DMZ, to a network B, which in turn is secured by a firewall Fb.
- a network A in which a user U1 works with his computer C1. This wants to access the network B, so he can use services S1 there.
- a possible service S1 is z. For example, access to the mail server or the appointment server. Other services are conceivable, such as file servers, databases or the like.
- the user U1 / C1 logs on to the firewall Fa via a suitable authentication.
- Smart cards are used in the preferred embodiment.
- the authentication can be specified via a rule that the user can only access a specific server SNab, within the network Nab, ie within the DMZ.
- This server is also referred to as a jump server and manages applications.
- this is a terminal server or application streaming server, such as that offered by Citrix, or a Unix / Linux server that manages and provides applications.
- the applications such as mail programs operating on this server SNab in turn, mature via the firewall Fb on the network B to retrieve the data stored there. in case of a Mailservers, z.
- an Outlook ⁇ (R)> program or a Lotus Notes ⁇ (R)> client is made available to the user to access the applications.
- the personal mail data is located on a mail server working on network B.
- the server SNab can also access the network B. This is achieved by the server SNab being assigned a unique IP address to each user who has dialed in on the server SNab. This requires a large pool of IP addresses, which is preferably selected from the area of private IP addresses. It is also possible for a user to be assigned multiple IP addresses.
- the IP addresses are assigned to the user in a central directory (eg LDAP).
- the firewall Fb uses the IP address to identify which user it must be, and can use specific rules to determine which servers SNb the user on network B can access. So z. For example, a user who only wants to retrieve e-mail has access to an e-mail server on network B. Based on the IP address, the firewall Fb can now use the directory service to retrieve rules that determine which server SNb the user can access. It should be noted that in another embodiment, the user must also authenticate to the firewall Fb.
- the rules are managed in an LDAP. It is a directory that centrally manages users' rules and authentication.
- an approach with a single sign-on is chosen in a preferred embodiment.
- the user only logs in once or authenticates once and can then access different services without having to perform an authentication each time again. Rather, there is a query in the background by the services that check whether the person has already logged in correctly in another permissible system. If the approach of single-sign-on is not selected, it usually requires three authentications. The first authentication takes place at the Firewall Fa, the second at the server Sab and the third at the Firewall Fb.
- the network in HP is a DMZ.
- a demilitarized zone (DMZ, also demilitarized or demilitarized zone) refers to a computer network with security-controlled access to the connected server.
- the systems installed in the DMZ are shielded by one or more firewalls against other networks (eg Internet, LAN). This separation allows access to publicly accessible services (bastion hosts with eg e-mail, WWW or similar) while protecting the internal network (LAN) from unauthorized access.
- the servers in the DMZ access network B via a secure connection to the servers in network B.
- the connection between the computer of the user and the server Sab is also encrypted, as well as the connection of the server Sab in the network B. This can be done from the firewall Fa or already from the user's computer.
- firewall Fa Fal, .., fan redundant
- different DMZ can be addressed through the firewall, if one of the DMZ is not available or the servers are not reachable within the DMZ.
- the firewall Fa automatically switches to another DMZ, which usually also includes alternative servers (Jump server). It is also conceivable that within a DMZ several of the jump servers are arranged, which are addressed depending on the load.
- the load balancing which is a meaningful utilization of the server, is performed either by an upstream proxy system, which is located in front of the server, or by the firewall itself, the requests for a specific algorithm, for example, such as round robin Robin, forwards.
- a specific algorithm for example, such as round robin Robin, forwards.
- the load-balancing techniques provided by the manufacturer can be used.
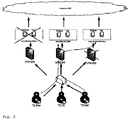
- the fig. 1 shows in front of a first firewall 7, also called Fb, a jump server 1, which allows users 2, 3 in the network B to access applications.
- the jump server then forwards the requests to the servers 16 or the server 15.
- the jump server is not located behind the firewall 7, but in front of the firewall. This is a fundamental exception to the present approach.
- the split tunnel can be active in individual cases in the case of a selective split tunnel.
- the jump server streams the application (transfers the program file plus some control files) to the user's computer. There it is executed within a protected environment (sandbox, a kind of virtual machine). Leave over with the transferred control files to limit the communication possibilities of the application. It controls whether the application is allowed to access the local storage media, whether an interaction with the clipboard is allowed, whether the applications may access other network resources, ...
- control files are transmitted individually for each application, it is possible to regulate the communication options for each individual application: the so-called selective split tunnel.
- a real split tunnel is different.
- the VPN client includes the option to disable the split tunnel when setting up the VPN tunnels. At the moment of tunnel setup, the VPN client stops communication with all networks except its own tunnel.
- This function of the VPN client is controlled by a control file which is located on the local hard drive of the user PC. This allows the Split Tunnel to be switched on or off.
- the VPN client offers the option of checking the configuration of the user PC for certain features at the moment of tunnel setup. These features can z. For example, the file date or the existence of a particular file or its contents. Similarly, the presence of certain processes or registry keys can be checked.
- the content of the control file for switching the split tunnel on / off is checked. If this file does not meet the requirements, the tunnel will not be successfully established. Thus even a user with administrative rights can not set up the tunnel with an active split tunnel. Although he could change the contents of the control file, the tunnel construction would then fail.
- the user in network B wants to access an application, such as a mail server 15, 16, for example.
- the jump server 1 is accessed, which has the same functionality as the jump servers 10 and 9, but which are arranged in the DMZ behind the firewall 7.
- the jump server then forwards the request via a virtual encrypted connection (VPN) to the servers 16, 15, 14, 13.
- VPN virtual encrypted connection
- the redirection takes place via a jump server, which is arranged between the firewalls 7 and 8, the information 18 is forwarded to the firewall 7, where authentication takes place.
- the request is forwarded to the Jump servers.
- Authentication at the jump server 10, 9 is then either again explicitly or by a single-sign-on approach.
- LDAP directory service
- the requests 19 are redirected via either the firewall 8 or 7 to corresponding servers 16, 15, 14 and 13, using unique IP addresses assigned to the user by the JumpServer .
- Each user has a unique, or one Group of unique IP addresses that allow conclusions about the identity of the user. These IP addresses are z. B. stored in the LDAP.
- Using these unique IP addresses on the Jump Server then accesses servers 13-16.
- the firewall must pass through 8 Fa, which recognizes which user it is based on the IP address and other authorization information.
- Based on a set of rules 20 it is now determined to which server 13 an access in the network A can take place.
- the same approach can also be taken from network A by users 11 and 12.
- the network A further has a local server 23, which is not integrated in the access.
- the fig. 2 shows a redundant approach. There are a number of firewalls, each allowing access to a jump server. If one of the servers or the firewall fails, the requests are redirected either via another firewall or to another Jump server in the respective countries, so that a redundancy is given.
Landscapes
- Engineering & Computer Science (AREA)
- Computer Hardware Design (AREA)
- Computer Security & Cryptography (AREA)
- Computing Systems (AREA)
- General Engineering & Computer Science (AREA)
- Computer Networks & Wireless Communication (AREA)
- Signal Processing (AREA)
- Data Exchanges In Wide-Area Networks (AREA)
- Computer And Data Communications (AREA)
Claims (9)
- Un procédé permettant à un utilisateur U1 d'accéder de façon sécurisée à son ordinateur C1 au sein d'un premier réseau local A, pour des services numériques (13, 15, 16) au sein d'un second réseau local B, dans lequel les deux réseaux sont sécurisés au moyen d'un pare-feu (7, 8), et dans lequel les deux réseaux sont connectés via un Nab de réseau disposés entre les pare-feux, comprenant les étapes :- authentification de l'utilisateur U1 au niveau du premier pare-feu (7, 8) ;- détermination, suite à l'authentification, au moyen d'une règle que l'utilisateur U1 est autorisé à accédé à un serveur de saut spécifique (13, 15, 16) au sein du Nab de réseau ;- accès au serveur de saut (9, 10) et authentification de l'utilisateur U1 au niveau du serveur de saut (9 10), et affectation d'une unique adresse IP dépendant de l'authentification ;- accès au service (13, 15, 16) au sein du second réseau B via le serveur de saut (9, 10), dans lequel intervient une authentification de l'adresse IP sur le second pare-feu (7, 8) ;- détermination d'une règle sur le second pare-feu (7, 8) sur la base de l'adresse IP pour vérifier que l'accès au service (13, 15, 16) peut être autorisé, si un accès est autorisé, la transmission de la requête du serveur de saut (9, 10) au service (13, 15, 16) au sein du second réseau B.
- Le procédé selon la revendication précédente, dans lequel une ou plusieurs adresses IP utilisées par le serveur de saut sont affectées de manière unique à un utilisateur.
- Le procédé selon une ou plusieurs des revendications précédentes, dans lequel les règles et/ou les adresses IP affectées à un utilisateur sont stockée au sein d'un répertoire central, tel que LPAD.
- Le procédé selon une ou plusieurs des revendications précédentes, dans lequel un procédé d'enregistrement unique est utilisé pour l'authentification au premier pare-feu et au second pare-feu et/ou au serveur de saut.
- Le procédé selon une ou plusieurs des revendications précédentes, dans lequel le réseau Nab est une zone démilitarisée, DMZ.
- Le procédé selon une ou plusieurs des revendications précédentes, dans lequel les connexions entre le pare-feu, le serveur de saut et les services sont chiffrées.
- Le procédé selon une ou plusieurs des revendications précédentes, dans lequel il y a une pluralité de pare-feux, qui sont conçus dans un esprit de redondance, de façon à ce que, à tout moment, l'accès peut être réalisé à un serveur de saut dans une ou plusieurs DMZ.
- Le procédé selon une ou plusieurs des revendications précédentes, dans lequel différentes DMZ sont adressées par le pare-feu, si l'une quelconque des DMZ n'est pas atteignable ou si les serveurs qui sont au sein de la DMZ ne peuvent être atteints.
- Le procédé selon une ou plusieurs des revendications précédentes, dans lequel un équilibrage de charge intervient pour une pluralité de serveur de saut, de façon à éviter que ne se produise une surcharge d'un seul côté des serveurs de saut.
Applications Claiming Priority (2)
| Application Number | Priority Date | Filing Date | Title |
|---|---|---|---|
| DE102009022977A DE102009022977A1 (de) | 2009-05-28 | 2009-05-28 | Service Interface |
| PCT/DE2010/000437 WO2010136003A1 (fr) | 2009-05-28 | 2010-05-05 | Interface de service |
Publications (2)
| Publication Number | Publication Date |
|---|---|
| EP2436166A1 EP2436166A1 (fr) | 2012-04-04 |
| EP2436166B1 true EP2436166B1 (fr) | 2016-03-23 |
Family
ID=42768130
Family Applications (1)
| Application Number | Title | Priority Date | Filing Date |
|---|---|---|---|
| EP10736596.7A Active EP2436166B1 (fr) | 2009-05-28 | 2010-05-05 | Interface de service |
Country Status (6)
| Country | Link |
|---|---|
| EP (1) | EP2436166B1 (fr) |
| DE (1) | DE102009022977A1 (fr) |
| ES (1) | ES2580677T3 (fr) |
| HU (1) | HUE029009T2 (fr) |
| PL (1) | PL2436166T3 (fr) |
| WO (1) | WO2010136003A1 (fr) |
Families Citing this family (2)
| Publication number | Priority date | Publication date | Assignee | Title |
|---|---|---|---|---|
| CN110661761B (zh) | 2018-06-29 | 2021-12-14 | 西门子股份公司 | 一种访问控制设备、方法、计算机程序产品和计算机可读介质 |
| WO2022026799A1 (fr) * | 2020-07-30 | 2022-02-03 | Open Text Holdings, Inc. | Systèmes de gestion d'agent de point d'extrémité et procédés de sécurité de point d'extrémité à distance |
Family Cites Families (9)
| Publication number | Priority date | Publication date | Assignee | Title |
|---|---|---|---|---|
| US7287271B1 (en) * | 1997-04-08 | 2007-10-23 | Visto Corporation | System and method for enabling secure access to services in a computer network |
| US7272625B1 (en) * | 1997-03-10 | 2007-09-18 | Sonicwall, Inc. | Generalized policy server |
| US20010042202A1 (en) * | 2000-04-14 | 2001-11-15 | Horvath Charles J. | Dynamically extendible firewall |
| US7984157B2 (en) * | 2002-02-26 | 2011-07-19 | Citrix Systems, Inc. | Persistent and reliable session securely traversing network components using an encapsulating protocol |
| US7263614B2 (en) * | 2002-12-31 | 2007-08-28 | Aol Llc | Implicit access for communications pathway |
| JP4119295B2 (ja) * | 2003-04-07 | 2008-07-16 | 東京エレクトロン株式会社 | 保守・診断データ蓄積サーバ、保守・診断データの蓄積・取得システム、保守・診断データの蓄積・提供システム |
| US20050251855A1 (en) * | 2004-05-04 | 2005-11-10 | Hob Gmbh & Co. Kg | Client-server-communication system |
| JP4492248B2 (ja) * | 2004-08-04 | 2010-06-30 | 富士ゼロックス株式会社 | ネットワークシステム、内部サーバ、端末装置、プログラム、およびパケット中継方法 |
| EP2061205A3 (fr) * | 2007-11-16 | 2009-06-17 | Hewlett-Packard Development Company, L.P. | Procédé et dispositif pour l'accès au réseau |
-
2009
- 2009-05-28 DE DE102009022977A patent/DE102009022977A1/de not_active Withdrawn
-
2010
- 2010-05-05 WO PCT/DE2010/000437 patent/WO2010136003A1/fr active Application Filing
- 2010-05-05 HU HUE10736596A patent/HUE029009T2/en unknown
- 2010-05-05 EP EP10736596.7A patent/EP2436166B1/fr active Active
- 2010-05-05 ES ES10736596.7T patent/ES2580677T3/es active Active
- 2010-05-05 PL PL10736596.7T patent/PL2436166T3/pl unknown
Also Published As
| Publication number | Publication date |
|---|---|
| HUE029009T2 (en) | 2017-02-28 |
| WO2010136003A1 (fr) | 2010-12-02 |
| EP2436166A1 (fr) | 2012-04-04 |
| DE102009022977A1 (de) | 2010-12-02 |
| ES2580677T3 (es) | 2016-08-25 |
| PL2436166T3 (pl) | 2016-10-31 |
Similar Documents
| Publication | Publication Date | Title |
|---|---|---|
| DE19740547B4 (de) | Vorrichtung und Verfahren zum Sicherstellen sicherer Kommunikation zwischen einer anfordernden Entität und einer bedienenden Entität | |
| EP2250598B1 (fr) | Système client/serveur de communication selon le protocole standard opc ua comportant des mécanismes d'authentification single sign-on et procédé d'exécution de single sign-on dans ce système | |
| DE19741239C2 (de) | Verallgemeinertes Sicherheitspolitik-Management-System und Verfahren | |
| DE60307652T2 (de) | Verfahren und System zur gesicherten Inhaltsüberlieferung | |
| DE112011102224B4 (de) | Identitätsvermittlung zwischen Client- und Server-Anwendungen | |
| WO2015185509A1 (fr) | Procédé de transfert de données entre des systèmes informatiques, infrastructure de réseau d'ordinateurs et produit-programme d'ordinateur | |
| WO2013017394A1 (fr) | Régulation d'accès pour des données ou des applications d'un réseau | |
| EP2436166B1 (fr) | Interface de service | |
| EP1298529A2 (fr) | Unité proxy et méthode pour protéger par ordinateur un programme de serveur d'applications | |
| EP3318033B1 (fr) | Procédé anti-cracking impiquant un ordinateur-relais | |
| DE112004000125T5 (de) | Gesichertes Client-Server-Datenübertragungssystem | |
| WO2004028107A2 (fr) | Controle de transmissions de donnees | |
| DE102012007217A1 (de) | IT-Verfahren für den sicheren Umgang mit Sensitiven Daten im Kontext des Cloud Computings | |
| WO2022128829A1 (fr) | Passerelle conçue spécifiquement pour des réseaux ot | |
| WO2016008889A1 (fr) | Procédé de libération de systèmes informatiques externes dans une infrastructure de réseau informatique, réseau informatique distribué ayant une telle infrastructure de réseau informatique, et un produit programme d'ordinateur | |
| WO2002067532A1 (fr) | Procede pour transmettre des donnees, serveur mandataire et systeme de transmission de donnees | |
| DE60031004T2 (de) | Elektronisches sicherheitssystem und verfahren für ein kommunikationsnetz | |
| DE19645006B4 (de) | Verfahren zur Kommunikation zwischen Prozessen | |
| DE102005050336B4 (de) | Verfahren und Anordnung zum Betreiben eines Sicherheitsgateways | |
| DE102009060904B4 (de) | Verfahren zum Steuern eines Verbindungsaufbaus sowie Netzwerksystem | |
| WO2020065476A1 (fr) | Système et procédé d'accès à des données dans une zone interne | |
| DE102007012750B3 (de) | Netzwerkadapter | |
| DE10234562B4 (de) | Sichere Netzwerkarchitektur | |
| WO2002056153A2 (fr) | Dispositif d'identification anti-falsification, de verification et d'autorisation d'applications sur reseau | |
| EP1903464A1 (fr) | Procédé et programme de commande destinés au traitement de droits d'accès utilisateur dans un réseau de communication |
Legal Events
| Date | Code | Title | Description |
|---|---|---|---|
| PUAI | Public reference made under article 153(3) epc to a published international application that has entered the european phase |
Free format text: ORIGINAL CODE: 0009012 |
|
| 17P | Request for examination filed |
Effective date: 20111228 |
|
| AK | Designated contracting states |
Kind code of ref document: A1 Designated state(s): AL AT BE BG CH CY CZ DE DK EE ES FI FR GB GR HR HU IE IS IT LI LT LU LV MC MK MT NL NO PL PT RO SE SI SK SM TR |
|
| DAX | Request for extension of the european patent (deleted) | ||
| GRAJ | Information related to disapproval of communication of intention to grant by the applicant or resumption of examination proceedings by the epo deleted |
Free format text: ORIGINAL CODE: EPIDOSDIGR1 |
|
| GRAP | Despatch of communication of intention to grant a patent |
Free format text: ORIGINAL CODE: EPIDOSNIGR1 |
|
| INTG | Intention to grant announced |
Effective date: 20150921 |
|
| GRAS | Grant fee paid |
Free format text: ORIGINAL CODE: EPIDOSNIGR3 |
|
| GRAA | (expected) grant |
Free format text: ORIGINAL CODE: 0009210 |
|
| AK | Designated contracting states |
Kind code of ref document: B1 Designated state(s): AL AT BE BG CH CY CZ DE DK EE ES FI FR GB GR HR HU IE IS IT LI LT LU LV MC MK MT NL NO PL PT RO SE SI SK SM TR |
|
| REG | Reference to a national code |
Ref country code: GB Ref legal event code: FG4D Free format text: NOT ENGLISH |
|
| REG | Reference to a national code |
Ref country code: CH Ref legal event code: EP |
|
| REG | Reference to a national code |
Ref country code: AT Ref legal event code: REF Ref document number: 784131 Country of ref document: AT Kind code of ref document: T Effective date: 20160415 |
|
| REG | Reference to a national code |
Ref country code: IE Ref legal event code: FG4D Free format text: LANGUAGE OF EP DOCUMENT: GERMAN |
|
| REG | Reference to a national code |
Ref country code: DE Ref legal event code: R096 Ref document number: 502010011269 Country of ref document: DE |
|
| REG | Reference to a national code |
Ref country code: FR Ref legal event code: PLFP Year of fee payment: 7 |
|
| REG | Reference to a national code |
Ref country code: NL Ref legal event code: FP |
|
| REG | Reference to a national code |
Ref country code: LT Ref legal event code: MG4D |
|
| PG25 | Lapsed in a contracting state [announced via postgrant information from national office to epo] |
Ref country code: FI Free format text: LAPSE BECAUSE OF FAILURE TO SUBMIT A TRANSLATION OF THE DESCRIPTION OR TO PAY THE FEE WITHIN THE PRESCRIBED TIME-LIMIT Effective date: 20160323 Ref country code: HR Free format text: LAPSE BECAUSE OF FAILURE TO SUBMIT A TRANSLATION OF THE DESCRIPTION OR TO PAY THE FEE WITHIN THE PRESCRIBED TIME-LIMIT Effective date: 20160323 Ref country code: NO Free format text: LAPSE BECAUSE OF FAILURE TO SUBMIT A TRANSLATION OF THE DESCRIPTION OR TO PAY THE FEE WITHIN THE PRESCRIBED TIME-LIMIT Effective date: 20160623 |
|
| REG | Reference to a national code |
Ref country code: ES Ref legal event code: FG2A Ref document number: 2580677 Country of ref document: ES Kind code of ref document: T3 Effective date: 20160825 |
|
| PG25 | Lapsed in a contracting state [announced via postgrant information from national office to epo] |
Ref country code: LT Free format text: LAPSE BECAUSE OF FAILURE TO SUBMIT A TRANSLATION OF THE DESCRIPTION OR TO PAY THE FEE WITHIN THE PRESCRIBED TIME-LIMIT Effective date: 20160323 Ref country code: BE Free format text: LAPSE BECAUSE OF NON-PAYMENT OF DUE FEES Effective date: 20160531 Ref country code: LV Free format text: LAPSE BECAUSE OF FAILURE TO SUBMIT A TRANSLATION OF THE DESCRIPTION OR TO PAY THE FEE WITHIN THE PRESCRIBED TIME-LIMIT Effective date: 20160323 Ref country code: SE Free format text: LAPSE BECAUSE OF FAILURE TO SUBMIT A TRANSLATION OF THE DESCRIPTION OR TO PAY THE FEE WITHIN THE PRESCRIBED TIME-LIMIT Effective date: 20160323 |
|
| REG | Reference to a national code |
Ref country code: GR Ref legal event code: EP Ref document number: 20160400770 Country of ref document: GR Effective date: 20160601 |
|
| PG25 | Lapsed in a contracting state [announced via postgrant information from national office to epo] |
Ref country code: EE Free format text: LAPSE BECAUSE OF FAILURE TO SUBMIT A TRANSLATION OF THE DESCRIPTION OR TO PAY THE FEE WITHIN THE PRESCRIBED TIME-LIMIT Effective date: 20160323 Ref country code: IS Free format text: LAPSE BECAUSE OF FAILURE TO SUBMIT A TRANSLATION OF THE DESCRIPTION OR TO PAY THE FEE WITHIN THE PRESCRIBED TIME-LIMIT Effective date: 20160723 |
|
| PG25 | Lapsed in a contracting state [announced via postgrant information from national office to epo] |
Ref country code: SM Free format text: LAPSE BECAUSE OF FAILURE TO SUBMIT A TRANSLATION OF THE DESCRIPTION OR TO PAY THE FEE WITHIN THE PRESCRIBED TIME-LIMIT Effective date: 20160323 Ref country code: SK Free format text: LAPSE BECAUSE OF FAILURE TO SUBMIT A TRANSLATION OF THE DESCRIPTION OR TO PAY THE FEE WITHIN THE PRESCRIBED TIME-LIMIT Effective date: 20160323 Ref country code: RO Free format text: LAPSE BECAUSE OF FAILURE TO SUBMIT A TRANSLATION OF THE DESCRIPTION OR TO PAY THE FEE WITHIN THE PRESCRIBED TIME-LIMIT Effective date: 20160323 Ref country code: PT Free format text: LAPSE BECAUSE OF FAILURE TO SUBMIT A TRANSLATION OF THE DESCRIPTION OR TO PAY THE FEE WITHIN THE PRESCRIBED TIME-LIMIT Effective date: 20160725 Ref country code: CZ Free format text: LAPSE BECAUSE OF FAILURE TO SUBMIT A TRANSLATION OF THE DESCRIPTION OR TO PAY THE FEE WITHIN THE PRESCRIBED TIME-LIMIT Effective date: 20160323 |
|
| PG25 | Lapsed in a contracting state [announced via postgrant information from national office to epo] |
Ref country code: LU Free format text: LAPSE BECAUSE OF FAILURE TO SUBMIT A TRANSLATION OF THE DESCRIPTION OR TO PAY THE FEE WITHIN THE PRESCRIBED TIME-LIMIT Effective date: 20160505 |
|
| REG | Reference to a national code |
Ref country code: CH Ref legal event code: PL |
|
| REG | Reference to a national code |
Ref country code: DE Ref legal event code: R097 Ref document number: 502010011269 Country of ref document: DE |
|
| PLBE | No opposition filed within time limit |
Free format text: ORIGINAL CODE: 0009261 |
|
| STAA | Information on the status of an ep patent application or granted ep patent |
Free format text: STATUS: NO OPPOSITION FILED WITHIN TIME LIMIT |
|
| PG25 | Lapsed in a contracting state [announced via postgrant information from national office to epo] |
Ref country code: LI Free format text: LAPSE BECAUSE OF NON-PAYMENT OF DUE FEES Effective date: 20160531 Ref country code: DK Free format text: LAPSE BECAUSE OF FAILURE TO SUBMIT A TRANSLATION OF THE DESCRIPTION OR TO PAY THE FEE WITHIN THE PRESCRIBED TIME-LIMIT Effective date: 20160323 Ref country code: CH Free format text: LAPSE BECAUSE OF NON-PAYMENT OF DUE FEES Effective date: 20160531 |
|
| REG | Reference to a national code |
Ref country code: IE Ref legal event code: MM4A |
|
| PG25 | Lapsed in a contracting state [announced via postgrant information from national office to epo] |
Ref country code: BG Free format text: LAPSE BECAUSE OF FAILURE TO SUBMIT A TRANSLATION OF THE DESCRIPTION OR TO PAY THE FEE WITHIN THE PRESCRIBED TIME-LIMIT Effective date: 20160623 |
|
| REG | Reference to a national code |
Ref country code: HU Ref legal event code: AG4A Ref document number: E029009 Country of ref document: HU |
|
| 26N | No opposition filed |
Effective date: 20170102 |
|
| REG | Reference to a national code |
Ref country code: FR Ref legal event code: PLFP Year of fee payment: 8 |
|
| PG25 | Lapsed in a contracting state [announced via postgrant information from national office to epo] |
Ref country code: SI Free format text: LAPSE BECAUSE OF FAILURE TO SUBMIT A TRANSLATION OF THE DESCRIPTION OR TO PAY THE FEE WITHIN THE PRESCRIBED TIME-LIMIT Effective date: 20160323 Ref country code: IE Free format text: LAPSE BECAUSE OF NON-PAYMENT OF DUE FEES Effective date: 20160505 |
|
| PGFP | Annual fee paid to national office [announced via postgrant information from national office to epo] |
Ref country code: NL Payment date: 20170522 Year of fee payment: 8 |
|
| PGFP | Annual fee paid to national office [announced via postgrant information from national office to epo] |
Ref country code: ES Payment date: 20170601 Year of fee payment: 8 Ref country code: AT Payment date: 20170519 Year of fee payment: 8 Ref country code: IT Payment date: 20170524 Year of fee payment: 8 |
|
| REG | Reference to a national code |
Ref country code: FR Ref legal event code: PLFP Year of fee payment: 9 |
|
| PG25 | Lapsed in a contracting state [announced via postgrant information from national office to epo] |
Ref country code: CY Free format text: LAPSE BECAUSE OF FAILURE TO SUBMIT A TRANSLATION OF THE DESCRIPTION OR TO PAY THE FEE WITHIN THE PRESCRIBED TIME-LIMIT Effective date: 20160323 |
|
| PG25 | Lapsed in a contracting state [announced via postgrant information from national office to epo] |
Ref country code: MC Free format text: LAPSE BECAUSE OF FAILURE TO SUBMIT A TRANSLATION OF THE DESCRIPTION OR TO PAY THE FEE WITHIN THE PRESCRIBED TIME-LIMIT Effective date: 20160323 Ref country code: MT Free format text: LAPSE BECAUSE OF FAILURE TO SUBMIT A TRANSLATION OF THE DESCRIPTION OR TO PAY THE FEE WITHIN THE PRESCRIBED TIME-LIMIT Effective date: 20160323 Ref country code: MK Free format text: LAPSE BECAUSE OF FAILURE TO SUBMIT A TRANSLATION OF THE DESCRIPTION OR TO PAY THE FEE WITHIN THE PRESCRIBED TIME-LIMIT Effective date: 20160323 Ref country code: TR Free format text: LAPSE BECAUSE OF FAILURE TO SUBMIT A TRANSLATION OF THE DESCRIPTION OR TO PAY THE FEE WITHIN THE PRESCRIBED TIME-LIMIT Effective date: 20160323 |
|
| PGFP | Annual fee paid to national office [announced via postgrant information from national office to epo] |
Ref country code: MC Payment date: 20180829 Year of fee payment: 9 |
|
| PGFP | Annual fee paid to national office [announced via postgrant information from national office to epo] |
Ref country code: HU Payment date: 20180421 Year of fee payment: 9 |
|
| PG25 | Lapsed in a contracting state [announced via postgrant information from national office to epo] |
Ref country code: AL Free format text: LAPSE BECAUSE OF FAILURE TO SUBMIT A TRANSLATION OF THE DESCRIPTION OR TO PAY THE FEE WITHIN THE PRESCRIBED TIME-LIMIT Effective date: 20160323 |
|
| REG | Reference to a national code |
Ref country code: NL Ref legal event code: MM Effective date: 20180601 |
|
| REG | Reference to a national code |
Ref country code: AT Ref legal event code: MM01 Ref document number: 784131 Country of ref document: AT Kind code of ref document: T Effective date: 20180505 |
|
| PG25 | Lapsed in a contracting state [announced via postgrant information from national office to epo] |
Ref country code: GR Free format text: LAPSE BECAUSE OF NON-PAYMENT OF DUE FEES Effective date: 20181204 Ref country code: AT Free format text: LAPSE BECAUSE OF NON-PAYMENT OF DUE FEES Effective date: 20180505 |
|
| PG25 | Lapsed in a contracting state [announced via postgrant information from national office to epo] |
Ref country code: IT Free format text: LAPSE BECAUSE OF NON-PAYMENT OF DUE FEES Effective date: 20180505 Ref country code: NL Free format text: LAPSE BECAUSE OF NON-PAYMENT OF DUE FEES Effective date: 20180601 |
|
| REG | Reference to a national code |
Ref country code: ES Ref legal event code: FD2A Effective date: 20190913 |
|
| PG25 | Lapsed in a contracting state [announced via postgrant information from national office to epo] |
Ref country code: ES Free format text: LAPSE BECAUSE OF NON-PAYMENT OF DUE FEES Effective date: 20180506 |
|
| PG25 | Lapsed in a contracting state [announced via postgrant information from national office to epo] |
Ref country code: HU Free format text: LAPSE BECAUSE OF NON-PAYMENT OF DUE FEES Effective date: 20190506 |
|
| REG | Reference to a national code |
Ref country code: DE Ref legal event code: R079 Ref document number: 502010011269 Country of ref document: DE Free format text: PREVIOUS MAIN CLASS: H04L0029060000 Ipc: H04L0065000000 |
|
| PG25 | Lapsed in a contracting state [announced via postgrant information from national office to epo] |
Ref country code: PL Free format text: LAPSE BECAUSE OF NON-PAYMENT OF DUE FEES Effective date: 20190505 |
|
| PGFP | Annual fee paid to national office [announced via postgrant information from national office to epo] |
Ref country code: GB Payment date: 20240522 Year of fee payment: 15 |
|
| PGFP | Annual fee paid to national office [announced via postgrant information from national office to epo] |
Ref country code: DE Payment date: 20240517 Year of fee payment: 15 |
|
| PGFP | Annual fee paid to national office [announced via postgrant information from national office to epo] |
Ref country code: FR Payment date: 20240522 Year of fee payment: 15 |