WO2022270228A1 - Ipネットワークにアクセスするための通信サービスを提供するための装置、方法及びそのためのプログラム - Google Patents
Ipネットワークにアクセスするための通信サービスを提供するための装置、方法及びそのためのプログラム Download PDFInfo
- Publication number
- WO2022270228A1 WO2022270228A1 PCT/JP2022/021655 JP2022021655W WO2022270228A1 WO 2022270228 A1 WO2022270228 A1 WO 2022270228A1 JP 2022021655 W JP2022021655 W JP 2022021655W WO 2022270228 A1 WO2022270228 A1 WO 2022270228A1
- Authority
- WO
- WIPO (PCT)
- Prior art keywords
- instance
- gtp
- credential
- packet
- iot device
- Prior art date
- Legal status (The legal status is an assumption and is not a legal conclusion. Google has not performed a legal analysis and makes no representation as to the accuracy of the status listed.)
- Ceased
Links
Images
Classifications
-
- H—ELECTRICITY
- H04—ELECTRIC COMMUNICATION TECHNIQUE
- H04W—WIRELESS COMMUNICATION NETWORKS
- H04W12/00—Security arrangements; Authentication; Protecting privacy or anonymity
- H04W12/03—Protecting confidentiality, e.g. by encryption
- H04W12/033—Protecting confidentiality, e.g. by encryption of the user plane, e.g. user's traffic
-
- H—ELECTRICITY
- H04—ELECTRIC COMMUNICATION TECHNIQUE
- H04W—WIRELESS COMMUNICATION NETWORKS
- H04W76/00—Connection management
- H04W76/10—Connection setup
- H04W76/12—Setup of transport tunnels
-
- H—ELECTRICITY
- H04—ELECTRIC COMMUNICATION TECHNIQUE
- H04W—WIRELESS COMMUNICATION NETWORKS
- H04W12/00—Security arrangements; Authentication; Protecting privacy or anonymity
- H04W12/03—Protecting confidentiality, e.g. by encryption
-
- H—ELECTRICITY
- H04—ELECTRIC COMMUNICATION TECHNIQUE
- H04W—WIRELESS COMMUNICATION NETWORKS
- H04W12/00—Security arrangements; Authentication; Protecting privacy or anonymity
- H04W12/04—Key management, e.g. using generic bootstrapping architecture [GBA]
-
- H—ELECTRICITY
- H04—ELECTRIC COMMUNICATION TECHNIQUE
- H04W—WIRELESS COMMUNICATION NETWORKS
- H04W12/00—Security arrangements; Authentication; Protecting privacy or anonymity
- H04W12/04—Key management, e.g. using generic bootstrapping architecture [GBA]
- H04W12/041—Key generation or derivation
-
- H—ELECTRICITY
- H04—ELECTRIC COMMUNICATION TECHNIQUE
- H04W—WIRELESS COMMUNICATION NETWORKS
- H04W12/00—Security arrangements; Authentication; Protecting privacy or anonymity
- H04W12/04—Key management, e.g. using generic bootstrapping architecture [GBA]
- H04W12/043—Key management, e.g. using generic bootstrapping architecture [GBA] using a trusted network node as an anchor
- H04W12/0431—Key distribution or pre-distribution; Key agreement
-
- H—ELECTRICITY
- H04—ELECTRIC COMMUNICATION TECHNIQUE
- H04W—WIRELESS COMMUNICATION NETWORKS
- H04W12/00—Security arrangements; Authentication; Protecting privacy or anonymity
- H04W12/06—Authentication
-
- H—ELECTRICITY
- H04—ELECTRIC COMMUNICATION TECHNIQUE
- H04W—WIRELESS COMMUNICATION NETWORKS
- H04W12/00—Security arrangements; Authentication; Protecting privacy or anonymity
- H04W12/06—Authentication
- H04W12/068—Authentication using credential vaults, e.g. password manager applications or one time password [OTP] applications
-
- H—ELECTRICITY
- H04—ELECTRIC COMMUNICATION TECHNIQUE
- H04W—WIRELESS COMMUNICATION NETWORKS
- H04W12/00—Security arrangements; Authentication; Protecting privacy or anonymity
- H04W12/08—Access security
- H04W12/086—Access security using security domains
-
- H—ELECTRICITY
- H04—ELECTRIC COMMUNICATION TECHNIQUE
- H04W—WIRELESS COMMUNICATION NETWORKS
- H04W12/00—Security arrangements; Authentication; Protecting privacy or anonymity
- H04W12/30—Security of mobile devices; Security of mobile applications
- H04W12/35—Protecting application or service provisioning, e.g. securing SIM application provisioning
-
- H—ELECTRICITY
- H04—ELECTRIC COMMUNICATION TECHNIQUE
- H04W—WIRELESS COMMUNICATION NETWORKS
- H04W8/00—Network data management
- H04W8/18—Processing of user or subscriber data, e.g. subscribed services, user preferences or user profiles; Transfer of user or subscriber data
- H04W8/183—Processing at user equipment or user record carrier
-
- H—ELECTRICITY
- H04—ELECTRIC COMMUNICATION TECHNIQUE
- H04W—WIRELESS COMMUNICATION NETWORKS
- H04W8/00—Network data management
- H04W8/26—Network addressing or numbering for mobility support
Definitions
- the present invention relates to a device, method, and program for providing communication services for accessing IP networks.
- Wireless communication services using cellular networks have traditionally been provided by mobile network operators (MNOs). Users make a contract with an MNO, receive a SIM card from the MNO, and install it in their device to start using it. can do.
- MNOs mobile network operators
- MVNOs mobile virtual network operators
- MNOs mobile virtual network operators
- MVNOs can be broadly divided into forms that do not have any communication infrastructure themselves, and forms that have their own communication infrastructure and connect that communication infrastructure to the MNO's communication infrastructure to provide wireless communication services.
- the latter (see Fig. 1) has its own communication infrastructure, so as an example, it is possible to set prices according to communication quality such as communication speed and communication capacity, and it is possible to meet various needs. is being attempted.
- IoT devices A notable increase in demand for wireless communication services in recent years is the movement of IoT, which adds communication functions to all kinds of things and connects them to the Internet.
- IoT devices Devices that can be connected to computer networks including the Internet are hereinafter referred to as “IoT devices”. By installing a SIM card, IoT devices can access IP networks using cellular communication.
- MVNE mobile virtual network service provider
- MNO mobile virtual network service provider
- MVNEs may also be provided to MVNOs.
- the MVNE's communication infrastructure is connected to the MNO's communication infrastructure to realize wireless communication services, and the MVNO, which does not have its own communication infrastructure, is responsible for retail.
- MVNOs such as those described above
- the present invention has been made in view of such problems, and its purpose is to provide IoT devices with a communication service for accessing an IP network using a communication infrastructure connected to the communication infrastructure of an MNO.
- a more general object of the present invention is to provide a communication service for IoT devices to access an IP network, using a communication infrastructure connected to the communication infrastructure of an MNO, via a radio access network for cellular communication.
- the purpose is to enable the access without requiring
- MNO Mobility Management Entity
- MVNO Mobility Management Entity
- MVNE Mobility Management Entity
- MNO has 3G SGSN and LTE S-GW as communication infrastructure
- MVNO or MVNE is not distinguished, and is comprehensively defined as a business operator having communication infrastructure connected to MNO communication infrastructure. may be called.
- Examples of the communication infrastructure owned by the operator include 3G GGSN and LTE P-GW.
- SIM card is attached to the IoT device as an example, but it is not limited to the physical SIM card. It may be implemented by installed software or the like, and is hereinafter collectively referred to as "SIM".
- SIM stores a SIM identifier that identifies the SIM. Examples of SIM identifiers include IMSI, ICCID, MSISDN, and the like.
- the present invention has been made in view of such problems, and its purpose is to access IoT devices and IP networks using equipment provided by communication infrastructure on the cloud connected to the communication infrastructure of MNO.
- a method for providing a communication service for providing a communication service to a subscriber comprising: receiving a create session request including a subscriber identifier for identifying a subscriber of said communication service; and storing an ID in association with said subscriber identifier. and a first provisioning call to a first instance and a second instance included in the equipment to create a GTP-U session between the first instance and the second instance. sending a first provisioning call including the identity; and from the first instance or the second instance, in response to the first provisioning call, the source of the GTP-U session.
- the source address is and sending a second provisioning call including a first credential; and to the IoT device storing the first credential or a second credential corresponding to the first credential, the source address and sending connection information including a destination address of the first instance.
- a second aspect of the present invention is the method of the first aspect, wherein the connection information includes a port number of the first instance.
- a third aspect of the present invention is the method of the first aspect, wherein the first credential is a public key and the second credential is a private key corresponding to the public key. .
- a fourth aspect of the present invention is the method of the first aspect, wherein the session creation request is received from the IoT device.
- a fifth aspect of the present invention is the method according to any one of the first to fourth aspects, wherein the first instance and the second instance are instances on a cloud or a public cloud.
- a sixth aspect of the present invention provides a communication service for accessing an IP network to an IoT device using equipment provided in a communication infrastructure on a cloud connected to the communication infrastructure of an MNO. said method comprising: receiving a create session request including a subscriber identifier for identifying a subscriber of said communication service; and a first provisioning to a first instance and a second instance included in said equipment for creating a GTP-U session between said first instance and said second instance. sending a first provisioning call including said identity; and sending said GTP-U session from said first instance or said second instance in response to said first provisioning call.
- a seventh aspect of the present invention is a device for providing a communication service for accessing an IP network to an IoT device using equipment included in a communication infrastructure on a cloud connected to the communication infrastructure of an MNO.
- receiving a create session request including a subscriber identifier for identifying a subscriber of said communication service, storing an ID in association with said subscriber identifier, and a first instance included in said equipment;
- the second instance as a response to the first provisioning call, receives a source address that is the source of the GTP-U session, and to the first instance, sending a second provisioning call to create a VPN session between the IoT device and the first instance, the second provisioning call including the source address and a first credential; Send connection information including the source address and the destination address of the first instance to the IoT device that stores the first credential or a second credential corresponding to the first credential.
- an IoT device accesses an IP network using a communication infrastructure on the cloud having a first instance and a second instance between which a GTP-U session is generated.
- the first instance transmits, from the IoT device, a VPN packet encapsulating an IP packet encrypted by a credential stored in the IoT device or a temporary credential receiving, wherein said first instance obtains a credential or temporary credential corresponding to a source address or temporary key included in said VPN packet to decrypt said encrypted IP packet; and said first instance determining one or more source addresses and each transmission held in said first instance based on the source address contained in the header of said decrypted IP packet.
- Determining the second instance by referring to an association with the destination of the GTP session to which the original address is assigned; transmitting a GTP packet having the IP packet as a GTP payload; and removing the GTP header from the GTP packet and sending the IP packet, which is the GTP payload, outside or inside the communication infrastructure. and transmitting to an IP network.
- a ninth aspect of the present invention provides a method for causing a communication infrastructure on a cloud during which a GTP-U session is generated to perform a method of providing a communication service for an IoT device to access an IP network.
- a VPN program wherein a first instance of the communication infrastructure encapsulates an IP packet encrypted by a credential stored in the IoT device or a temporary credential from the IoT device.
- the first instance obtains a credential or temporary credential corresponding to a source address or temporary key contained in said VPN packet and converts said encrypted IP packet to one or more source addresses held in the first instance, based on the source address contained in the header of the decrypted IP packet;
- the second instance of the communication infrastructure sending the IP packet to an IP network outside or inside the communication infrastructure determining a possible second instance; and sending, by the first instance, a GTP packet to the second instance with the decrypted IP packet as the GTP payload.
- a tenth aspect of the present invention is a communication infrastructure on a cloud for providing a communication service for an IoT device to access an IP network, wherein a GTP-U session is generated between the first and a second instance, wherein the first instance receives from the IoT device a VPN packet encapsulating an IP packet encrypted with a credential stored in the IoT device or a temporary credential. and obtaining a credential or temporary credential corresponding to a source address or temporary key included in the VPN packet to decrypt the encrypted IP packet, wherein the first instance decrypts one or more source addresses and destinations of GTP sessions to which each source address is assigned, held in the first instance, based on the source addresses contained in the headers of the IP packets that have been generated.
- determining the second instance by referring to the association, transmitting a GTP packet having the decrypted IP packet as a GTP payload to the second instance, and removing the GTP header from the GTP packet and transmitting the IP packet, which is the GTP payload, to an IP network outside or inside the communication infrastructure;
- a confidential line is provided on an IP network such as the Internet by a VPN tunnel
- the IoT device is a communication infrastructure connected to the communication infrastructure of the MNO through the confidential line, and is a GTP tunnel. It becomes possible to connect to a communication infrastructure that can transmit data to and receive data from an IP network without going through a radio access network.
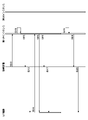
- FIG. 1 is a diagram schematically showing an MVNO that provides wireless communication services by connecting its own communication infrastructure to the MNO's communication infrastructure;
- FIG. Fig. 3 illustrates an apparatus for providing communication services for accessing an IP network according to an embodiment of the present invention;
- Fig. 3 shows a flow diagram of a method for providing communication services for accessing an IP network according to an embodiment of the present invention;
- Fig. 3 shows a flow diagram of a method for providing communication services for accessing an IP network according to an embodiment of the present invention;
- FIG. 4 is a diagram showing the flow of data transmission in a communication service for accessing an IP network by an IoT device according to an embodiment of the present invention;
- FIG. 2 shows an apparatus for providing communication services for accessing an IP network according to one embodiment of the present invention.
- the device 200 communicates with an MVNO communication infrastructure 220 and an IoT device 230 connected to an MNO communication infrastructure 210 over an IP network.
- the device 200 is also called a connection device because it establishes a connection for the IoT device 230 to access the IP network.
- the MVNO's communication infrastructure 220 is composed of multiple instances on the cloud or public cloud.
- cloud refers to a system that can dynamically provision and provide computing resources such as CPU, memory, storage, and network bandwidth on a network according to demand.
- a cloud can be used by AWS or the like.
- public cloud refers to a cloud in which multiple tenants can receive provision of computing resources.
- the device 200 includes a communication unit 201 such as a communication interface, a processing unit 202 such as a processor and a CPU, and a storage unit 203 including a storage device or storage medium such as a memory or hard disk. It can be configured by running Device 200 may include one or more devices, computers or servers. Also, the program may include one or more programs, and may be recorded on a computer-readable storage medium to be a non-transitory program product. The program can be stored in a storage device or storage medium such as the database 204 accessible from the storage unit 203 or the device 200 via the IP network, and can be executed by the processing unit 202 . Data described below as being stored in storage 203 may be stored in database 204, and vice versa.
- the device 200 can be one or more instances on the cloud or public cloud, and may be one or more instances on the same cloud as the communication infrastructure 220 of the MVNO. Each instance of the MVNO communication infrastructure 220 can have the same hardware configuration as the connection device 200, although not shown.
- Generate session 3A and 3B show a method flow for providing communication services for accessing an IP network according to one embodiment of the present invention.
- the device 200 receives a session creation request including a subscriber identifier for identifying a subscriber of the communication service from the IoT device 230 (S301).
- the session creation request can be transmitted through an Internet communication line other than a cellular line, and as an example, it may be transmitted through a fixed Internet line or through a cellular line.
- the IoT device 230 has a SIM identifier 231 that identifies a SIM for using a communication service for accessing an IP network provided via a radio access network using the communication infrastructure 220 of the MVNO.
- a subscriber identifier 232 is stored for using communication services for accessing the IP network provided without going through the radio access network.
- the subscriber identifier 232 is indicated as "V-SIM (Virtual SIM)" for convenience because it can be considered as a virtual SIM identifier when a connection is established using this.
- the IoT device 230 may store a token for validating the session creation request. The IoT device 230 does not necessarily have to store the SIM identifier 231 .
- connection device 200 After verifying the token included in the received session creation request as necessary, the connection device 200 generates and stores an ID in association with the subscriber identifier 232 included in the session creation request (S302). It is conceivable that the session creation request is transmitted to the connection device 200 for the IoT device 230 from a device other than the IoT device 230 that can legitimately access the subscriber identifier 232 .
- An example of a device other than the IoT device 230 is a computer used by an administrator who manages the IoT device 230.
- the administrator can access the subscriber identifier 232, and if the token necessary for making a session creation request to the connection device 200 is granted, the administrator can use the token to include the subscriber identifier 232.
- a session creation request can be made for the IoT device 230 .
- the IoT device 230 is authenticated using the SIM identifier 231 stored in the IoT device 230, and an authentication device capable of establishing a secure line with the IoT device 230 is used. server.
- the authentication server that has received the subscriber identifier 232 from the IoT device 230 through the established secure line accesses the subscriber identifier 232 legitimately.
- the SIM identified by the SIM identifier 231 is issued by an operator having the communication infrastructure 220 connected to the communication infrastructure 210 of the MNO, the authentication server is one or more of the equipment included in the communication infrastructure 220. can be an instance.
- connection adapter 200 adopts the first instance and the second instance of the communication infrastructure 220 (S303), and for the second instance, the first instance and the second instance.
- This provisioning call may include the ID stored in the connection device 200 and the first destination address such as the IP address, host name, etc. of the first instance adopted by the connection device 200 .
- the first instance can be adopted from the first node group, and the second instance can be adopted from the second node group.
- Each instance may include multiple servers, and the server from which each instance receives data may be different from the server from which it sends data.
- the MVNO communication infrastructure 220 provides the IoT device 230 with access to the IP network via the radio access network
- the first server selected from the first server group connected to the MNO communication infrastructure 210 Then, a second server selected from a second server group connected to the first server is used.
- At least some of the second group of nodes can be identical to at least some of the second group of servers.
- the second instance transmits a provisioning call response to the second instance to the connection device 200 (S305). Then, the second instance enters a waiting state for the GTP-U session (S306).
- the response may include the ID and a source address, such as a source IP address for the GTP-U session, which may be adopted by the second instance. Also, although it has been described here that it enters the standby state after sending a response, the order may be reversed.
- the source address may be assigned at the connection device 200 instead of the second instance.
- the provisioning call to the second instance may include the source address.
- the second instance can store the source address in association with the ID. Also, in the device 200, the source address can be stored in association with the subscriber identifier 232.
- connection adapter 200 then transmits a provisioning call to the first instance to create a GTP-U session between the first instance and the second instance (S307).
- This provisioning call may include the ID stored in the connected device 200, the source address, and the second destination address of the second instance that the connected device 200 has adopted.
- the first instance After that, the first instance enters a waiting state for a GTP-U session (S308).
- a GTP-U session is generated between the first instance and the second instance, and a so-called GTP tunnel is established.
- the connection adapter 200 receives the provisioning call response to the first instance (S309).
- the first instance may enter a standby state after transmitting a response, it is preferable to transmit a response after entering a standby state so as not to cause a period of time during which connection cannot be established.
- connection device 200 transmits a provisioning call for generating a VPN session between the IoT device 230 and the first instance to the first instance (S310).
- This provisioning call includes the source address and the credentials associated with IoT device 230 .
- the credential may be stored in database 204 in association with subscriber identifier 232 or included in the session creation request from IoT device 230 .
- This credential can be, for example, a public key.
- the IoT device 230 stores a private key corresponding to the public key. Encryption methods other than public key encryption methods may be used for VPN sessions, and more generally, a first credential required for the encryption method is sent to the first instance, and the first credential is sent to the first instance. One credential or a corresponding second credential may be stored in the IoT device 230 .
- the first instance After receiving the provisioning call for creating the VPN session, the first instance stores the source address and the credential, and enters a VPN session waiting state (S311). Also, the connection adapter 200 receives a response to the provisioning call from the first instance (S312). The response can include, in one example, the source address and the first destination address of the first instance.
- the first instance may enter a standby state after transmitting a response, it is preferable to transmit a response after entering a standby state so as not to cause a period of time during which connection cannot be established.
- the connection adapter 200 that has received the response transmits connection information to the IoT device 230 by adding a port number to the source address and the first destination address included in the response as necessary (S313). If the response from the first instance includes the port number, the received connection information should be sent to the IoT device 230 . In the IoT device 230, device provisioning is performed based on the connection information, and connection to the first instance is attempted (S314). Here, there may be an intervening device between the IoT device 230 and the first instance. If the first instance transmits a success response to the IoT device 230 (S315), the handshake is successful and the VPN tunnel is established. In response to receiving the attempt, in response to sending a successful response to the attempt, or more generally after receiving the attempt, the first instance listens for a GTP-U session and establishes a GTP tunnel. may be established.
- the first instance may notify the connection device 200 that it has come online, that is, that a connection has been established for communication using the subscriber identifier 232. (S316).
- the connection device 200 that has received such a notification for example, sends online display information to the IoT device 230 or a computer used by an administrator who manages the IoT device 230 to indicate that communication using the subscriber identifier 232 is possible. may be transmitted to a device other than the IoT device 230 (S317).
- the connection device 200 may self-determine and store that the subscriber identifier 232 has come online upon receiving a response that the attempt was successful.
- the first instance determines whether or not a predetermined period of time has passed (S318).
- the connection device 200 that has received such a notification, for example, displays offline display information indicating that communication using the subscriber identifier 232 is not possible, or displays the IoT device 230 such as a computer used by an administrator who manages the IoT device 230. It may be transmitted to other devices (S320). How to define the start point of the predetermined period and the period for confirming the existence of the VPN tunnel may be determined according to the individual specifications of the VPN technology. An example of the starting point of time is when the VPN tunnel is disconnected.
- connection device 200 When a session creation request is sent to the connection device 200 from a device other than the IoT device 230, the response to the request is sent to the device other than the IoT device 230. If a secure line is established between a device other than the IoT device 230 and the IoT device 230, the connection information can be sent to the IoT device 230 through the secure line and device provisioning can be performed. It can be said that the data is transmitted from the connection device 200 to the IoT device 230 .
- a temporary credential may be generated using the credential stored in the first instance or a credential corresponding thereto and stored in the first instance.
- the temporary credential is associated with the source address in the first instance.
- the IoT device 230 also stores temporary credentials.
- a temporary key may be generated, and in the first instance, in addition to associating the key with the source address, the temporary associated credentials.
- FIG. 4 shows the data transmission flow in the communication service for accessing the IP network according to the first embodiment of the present invention.
- the IoT device 230 encapsulates an IP packet encrypted by a credential or temporary credential stored in the IoT device 230 into a VPN packet and transmits it to the first instance (S401).
- the VPN packet includes an encrypted IP packet and VPN session information regarding the VPN session.
- the VPN session information includes a source address or a temporary key associated therewith.
- the first instance that receives the VPN packet obtains a credential or a temporary credential corresponding to the source address included in the VPN session information or a temporary key associated therewith, and encrypts An attempt is made to decrypt the IP packet (S402).
- Routing information may be set in the IoT device 230 during device provisioning in the session generation process. More specifically, the IoT device 230 may determine whether or not to pass through the VPN tunnel according to the destination address after the GTP tunnel termination of the encrypted IP packet sent from the IoT device 230. good.
- the first instance determines, based on the source address contained in the header of the decrypted IP packet, one or more source addresses held in the first instance and each source address
- the second instance to be the destination is determined by referring to the correspondence with the destination of the allocated GTP session (S403).
- the first instance transmits a GTP packet having the decrypted IP packet as the GTP payload to the determined second instance (S404). This terminates the VPN tunnel.
- Each instance may include multiple servers, and the server from which each instance receives data may be different from the server from which it sends data.
- the GTP header is removed from the received GTP packet, and the IP packet, which is the GTP payload, is sent to the IP network outside or inside the MVNO communication infrastructure 220 (S405).
- the GTP header includes an ID, and the second instance can identify the source address by referring to the correspondence between the ID and the source address stored by the second instance.
- the subscriber identifier can be identified transitively by referring to the source address-to-subscriber identifier association stored by 200 .
- the VPN tunnel provides a secure line on an IP network such as the Internet, and the IoT device 230 connects to the MVNO communication infrastructure 220, which performs data communication using the GTP protocol, not via the radio access network, but via the IP network. connection is possible.
- the MVNO communication infrastructure 220 is as follows when receiving data from the IP network.
- the GTP-U session corresponding to the address of the IoT device 230 that is the destination is specified, and the GTP header is added to the IP packet.
- the GTP header is removed from the received GTP packet to obtain the IP packet addressed to the IoT device 230 .
- Identify the corresponding VPN session from the destination address of the IP packet encapsulate the IP packet into a VPN packet using the credential corresponding to the temporary key associated with the VPN session or the temporary credential, and It transmits to the IoT device 230 via the tunnel.
- the IoT device 230 obtains a credential corresponding to the temporary key associated with the received VPN packet based on the VPN session information or a temporary credential, decrypts the encrypted IP packet, and converts the IP process the packet.
- the transmission source address associated with the subscriber identifier 232 or corresponding to the connection device 200 may send a request to disable the VPN session determined by the key to be used.
- the connection adapter 200 that received the invalidation request discards or invalidates the credential or temporary credential corresponding to the source address or the key associated with it for the first instance. and updates the stored billing state associated with the subscriber identifier 232 in response to the revocation of the VPN session.
Landscapes
- Engineering & Computer Science (AREA)
- Computer Security & Cryptography (AREA)
- Computer Networks & Wireless Communication (AREA)
- Signal Processing (AREA)
- Databases & Information Systems (AREA)
- Mobile Radio Communication Systems (AREA)
- Data Exchanges In Wide-Area Networks (AREA)
Priority Applications (5)
| Application Number | Priority Date | Filing Date | Title |
|---|---|---|---|
| JP2023529742A JP7637773B2 (ja) | 2021-06-22 | 2022-05-26 | Ipネットワークにアクセスするための通信サービスを提供するための装置、方法及びそのためのプログラム |
| EP22828147.3A EP4362601A4 (en) | 2021-06-22 | 2022-05-26 | DEVICE AND METHOD FOR PROVIDING A COMMUNICATION SERVICE FOR ACCESSING AN IP NETWORK AND ASSOCIATED PROGRAM |
| CN202280043914.9A CN117546598A (zh) | 2021-06-22 | 2022-05-26 | 用于提供向ip网络接入用的通信服务的装置、方法及所用的程序 |
| US18/542,471 US20240121835A1 (en) | 2021-06-22 | 2023-12-15 | Apparatus and method for providing communication service for accessing ip network, and storage medium |
| JP2025022437A JP2025072636A (ja) | 2021-06-22 | 2025-02-14 | Ipネットワークにアクセスするための通信サービスを提供するための装置、方法及びそのためのプログラム |
Applications Claiming Priority (2)
| Application Number | Priority Date | Filing Date | Title |
|---|---|---|---|
| JP2021-103687 | 2021-06-22 | ||
| JP2021103687 | 2021-06-22 |
Related Child Applications (1)
| Application Number | Title | Priority Date | Filing Date |
|---|---|---|---|
| US18/542,471 Continuation US20240121835A1 (en) | 2021-06-22 | 2023-12-15 | Apparatus and method for providing communication service for accessing ip network, and storage medium |
Publications (1)
| Publication Number | Publication Date |
|---|---|
| WO2022270228A1 true WO2022270228A1 (ja) | 2022-12-29 |
Family
ID=84543829
Family Applications (1)
| Application Number | Title | Priority Date | Filing Date |
|---|---|---|---|
| PCT/JP2022/021655 Ceased WO2022270228A1 (ja) | 2021-06-22 | 2022-05-26 | Ipネットワークにアクセスするための通信サービスを提供するための装置、方法及びそのためのプログラム |
Country Status (5)
| Country | Link |
|---|---|
| US (1) | US20240121835A1 (enExample) |
| EP (1) | EP4362601A4 (enExample) |
| JP (2) | JP7637773B2 (enExample) |
| CN (1) | CN117546598A (enExample) |
| WO (1) | WO2022270228A1 (enExample) |
Citations (3)
| Publication number | Priority date | Publication date | Assignee | Title |
|---|---|---|---|---|
| WO2008017709A1 (en) * | 2006-08-09 | 2008-02-14 | Alcatel Lucent | Method of managing interworking for transferring multiple service sessions between a mobile network and a wireless local area network, and corresponding equipment |
| CN102149133A (zh) * | 2010-02-10 | 2011-08-10 | 广州科讯技术有限公司 | 一种移动通信网络业务接入系统及方法 |
| WO2017022791A1 (ja) * | 2015-08-04 | 2017-02-09 | 日本電気株式会社 | 通信システム、通信装置、通信方法、端末、プログラム |
Family Cites Families (4)
| Publication number | Priority date | Publication date | Assignee | Title |
|---|---|---|---|---|
| CN114205926B (zh) * | 2015-09-29 | 2024-01-16 | 株式会社宙连 | 控制装置和存储介质 |
| US10897507B2 (en) * | 2016-04-01 | 2021-01-19 | Qualcomm Incorporated | Mechanism to enable connectivity sessions and IP session establishment |
| US11190547B2 (en) * | 2019-09-30 | 2021-11-30 | Palo Alto Networks, Inc. | Cellular internet of things battery drain prevention in mobile networks |
| JP7076050B1 (ja) | 2021-06-22 | 2022-05-26 | 株式会社ソラコム | Ipネットワークにアクセスするための通信サービスを提供するための装置、方法及びそのためのプログラム |
-
2022
- 2022-05-26 EP EP22828147.3A patent/EP4362601A4/en active Pending
- 2022-05-26 JP JP2023529742A patent/JP7637773B2/ja active Active
- 2022-05-26 CN CN202280043914.9A patent/CN117546598A/zh active Pending
- 2022-05-26 WO PCT/JP2022/021655 patent/WO2022270228A1/ja not_active Ceased
-
2023
- 2023-12-15 US US18/542,471 patent/US20240121835A1/en active Pending
-
2025
- 2025-02-14 JP JP2025022437A patent/JP2025072636A/ja active Pending
Patent Citations (3)
| Publication number | Priority date | Publication date | Assignee | Title |
|---|---|---|---|---|
| WO2008017709A1 (en) * | 2006-08-09 | 2008-02-14 | Alcatel Lucent | Method of managing interworking for transferring multiple service sessions between a mobile network and a wireless local area network, and corresponding equipment |
| CN102149133A (zh) * | 2010-02-10 | 2011-08-10 | 广州科讯技术有限公司 | 一种移动通信网络业务接入系统及方法 |
| WO2017022791A1 (ja) * | 2015-08-04 | 2017-02-09 | 日本電気株式会社 | 通信システム、通信装置、通信方法、端末、プログラム |
Non-Patent Citations (1)
| Title |
|---|
| See also references of EP4362601A4 * |
Also Published As
| Publication number | Publication date |
|---|---|
| CN117546598A (zh) | 2024-02-09 |
| JP2025072636A (ja) | 2025-05-09 |
| EP4362601A1 (en) | 2024-05-01 |
| US20240121835A1 (en) | 2024-04-11 |
| JPWO2022270228A1 (enExample) | 2022-12-29 |
| JP7637773B2 (ja) | 2025-02-28 |
| EP4362601A4 (en) | 2025-07-16 |
Similar Documents
| Publication | Publication Date | Title |
|---|---|---|
| US9967738B2 (en) | Methods and arrangements for enabling data transmission between a mobile device and a static destination address | |
| CN110800331A (zh) | 网络验证方法、相关设备及系统 | |
| JP5536628B2 (ja) | 無線lan接続方法、無線lanクライアント、および無線lanアクセスポイント | |
| JP7535022B2 (ja) | 機器をリモートで管理するための装置、方法及びそのためのプログラム | |
| US20200329360A1 (en) | Method and system for discovering user equipment in a network | |
| CN110944319B (zh) | 5g通信身份验证方法、设备及存储介质 | |
| CN109495594B (zh) | 一种数据传输方法、pnf sdn控制器、vnf sdn控制器及系统 | |
| WO2017167249A1 (zh) | 一种专网接入方法、装置及系统 | |
| CN111132305B (zh) | 5g用户终端接入5g网络的方法、用户终端设备及介质 | |
| CN113973098B (zh) | 一种域名系统请求的发送方法及装置 | |
| CN103428697A (zh) | 基于capwap协议的网络接入方法、装置和系统 | |
| TW201706893A (zh) | 實現雲端身份認證的網路系統、方法及移動設備 | |
| CN104168564A (zh) | 基于gprs网络和一体化标识网络的认证方法和装置 | |
| JP7076050B1 (ja) | Ipネットワークにアクセスするための通信サービスを提供するための装置、方法及びそのためのプログラム | |
| CN111093196A (zh) | 5g用户终端接入5g网络的方法、用户终端设备及介质 | |
| WO2014205703A1 (zh) | 一种共享接入的检测方法、设备和终端设备 | |
| JP5326815B2 (ja) | パケット送受信装置およびパケット送受信方法 | |
| WO2014201783A1 (zh) | 一种自组网的加密鉴权方法、系统及终端 | |
| JP7637773B2 (ja) | Ipネットワークにアクセスするための通信サービスを提供するための装置、方法及びそのためのプログラム | |
| JP7076051B1 (ja) | Ipネットワークにアクセスするための通信サービスを提供するための装置、方法及びそのためのプログラム | |
| CN118317308A (zh) | 网络地址分配方法、设备、存储介质及程序产品 | |
| JP7161108B2 (ja) | 通信方法、通信システム、中継装置および中継プログラム | |
| CN113543119B (zh) | 标识符的获取方法和统一数据管理实体、终端 | |
| JP2015041970A (ja) | 通信システム、通信方法、および、通信プログラム | |
| CN115811751A (zh) | 一种配置信息的获取、配置方法及终端设备、接入点设备 |
Legal Events
| Date | Code | Title | Description |
|---|---|---|---|
| 121 | Ep: the epo has been informed by wipo that ep was designated in this application |
Ref document number: 22828147 Country of ref document: EP Kind code of ref document: A1 |
|
| WWE | Wipo information: entry into national phase |
Ref document number: 2023529742 Country of ref document: JP |
|
| WWE | Wipo information: entry into national phase |
Ref document number: 202280043914.9 Country of ref document: CN |
|
| WWE | Wipo information: entry into national phase |
Ref document number: 2022828147 Country of ref document: EP |
|
| NENP | Non-entry into the national phase |
Ref country code: DE |
|
| ENP | Entry into the national phase |
Ref document number: 2022828147 Country of ref document: EP Effective date: 20240122 |