WO2020179707A1 - 通信制御装置および通信システム - Google Patents
通信制御装置および通信システム Download PDFInfo
- Publication number
- WO2020179707A1 WO2020179707A1 PCT/JP2020/008467 JP2020008467W WO2020179707A1 WO 2020179707 A1 WO2020179707 A1 WO 2020179707A1 JP 2020008467 W JP2020008467 W JP 2020008467W WO 2020179707 A1 WO2020179707 A1 WO 2020179707A1
- Authority
- WO
- WIPO (PCT)
- Prior art keywords
- communication
- communication control
- control device
- information
- client
- Prior art date
- Legal status (The legal status is an assumption and is not a legal conclusion. Google has not performed a legal analysis and makes no representation as to the accuracy of the status listed.)
- Ceased
Links
Images
Classifications
-
- H—ELECTRICITY
- H04—ELECTRIC COMMUNICATION TECHNIQUE
- H04L—TRANSMISSION OF DIGITAL INFORMATION, e.g. TELEGRAPHIC COMMUNICATION
- H04L9/00—Cryptographic mechanisms or cryptographic arrangements for secret or secure communications; Network security protocols
- H04L9/08—Key distribution or management, e.g. generation, sharing or updating, of cryptographic keys or passwords
- H04L9/0894—Escrow, recovery or storing of secret information, e.g. secret key escrow or cryptographic key storage
- H04L9/0897—Escrow, recovery or storing of secret information, e.g. secret key escrow or cryptographic key storage involving additional devices, e.g. trusted platform module [TPM], smartcard or USB
-
- G—PHYSICS
- G06—COMPUTING OR CALCULATING; COUNTING
- G06F—ELECTRIC DIGITAL DATA PROCESSING
- G06F21/00—Security arrangements for protecting computers, components thereof, programs or data against unauthorised activity
- G06F21/60—Protecting data
- G06F21/606—Protecting data by securing the transmission between two devices or processes
-
- H—ELECTRICITY
- H04—ELECTRIC COMMUNICATION TECHNIQUE
- H04L—TRANSMISSION OF DIGITAL INFORMATION, e.g. TELEGRAPHIC COMMUNICATION
- H04L63/00—Network architectures or network communication protocols for network security
- H04L63/04—Network architectures or network communication protocols for network security for providing a confidential data exchange among entities communicating through data packet networks
- H04L63/0428—Network architectures or network communication protocols for network security for providing a confidential data exchange among entities communicating through data packet networks wherein the data content is protected, e.g. by encrypting or encapsulating the payload
- H04L63/0435—Network architectures or network communication protocols for network security for providing a confidential data exchange among entities communicating through data packet networks wherein the data content is protected, e.g. by encrypting or encapsulating the payload wherein the sending and receiving network entities apply symmetric encryption, i.e. same key used for encryption and decryption
-
- H—ELECTRICITY
- H04—ELECTRIC COMMUNICATION TECHNIQUE
- H04L—TRANSMISSION OF DIGITAL INFORMATION, e.g. TELEGRAPHIC COMMUNICATION
- H04L63/00—Network architectures or network communication protocols for network security
- H04L63/04—Network architectures or network communication protocols for network security for providing a confidential data exchange among entities communicating through data packet networks
- H04L63/0428—Network architectures or network communication protocols for network security for providing a confidential data exchange among entities communicating through data packet networks wherein the data content is protected, e.g. by encrypting or encapsulating the payload
- H04L63/0492—Network architectures or network communication protocols for network security for providing a confidential data exchange among entities communicating through data packet networks wherein the data content is protected, e.g. by encrypting or encapsulating the payload by using a location-limited connection, e.g. near-field communication or limited proximity of entities
-
- H—ELECTRICITY
- H04—ELECTRIC COMMUNICATION TECHNIQUE
- H04L—TRANSMISSION OF DIGITAL INFORMATION, e.g. TELEGRAPHIC COMMUNICATION
- H04L63/00—Network architectures or network communication protocols for network security
- H04L63/08—Network architectures or network communication protocols for network security for authentication of entities
- H04L63/0823—Network architectures or network communication protocols for network security for authentication of entities using certificates
-
- H—ELECTRICITY
- H04—ELECTRIC COMMUNICATION TECHNIQUE
- H04L—TRANSMISSION OF DIGITAL INFORMATION, e.g. TELEGRAPHIC COMMUNICATION
- H04L63/00—Network architectures or network communication protocols for network security
- H04L63/08—Network architectures or network communication protocols for network security for authentication of entities
- H04L63/0869—Network architectures or network communication protocols for network security for authentication of entities for achieving mutual authentication
-
- H—ELECTRICITY
- H04—ELECTRIC COMMUNICATION TECHNIQUE
- H04L—TRANSMISSION OF DIGITAL INFORMATION, e.g. TELEGRAPHIC COMMUNICATION
- H04L9/00—Cryptographic mechanisms or cryptographic arrangements for secret or secure communications; Network security protocols
- H04L9/08—Key distribution or management, e.g. generation, sharing or updating, of cryptographic keys or passwords
- H04L9/0816—Key establishment, i.e. cryptographic processes or cryptographic protocols whereby a shared secret becomes available to two or more parties, for subsequent use
- H04L9/0838—Key agreement, i.e. key establishment technique in which a shared key is derived by parties as a function of information contributed by, or associated with, each of these
- H04L9/0841—Key agreement, i.e. key establishment technique in which a shared key is derived by parties as a function of information contributed by, or associated with, each of these involving Diffie-Hellman or related key agreement protocols
- H04L9/0844—Key agreement, i.e. key establishment technique in which a shared key is derived by parties as a function of information contributed by, or associated with, each of these involving Diffie-Hellman or related key agreement protocols with user authentication or key authentication, e.g. ElGamal, MTI, MQV-Menezes-Qu-Vanstone protocol or Diffie-Hellman protocols using implicitly-certified keys
-
- H—ELECTRICITY
- H04—ELECTRIC COMMUNICATION TECHNIQUE
- H04L—TRANSMISSION OF DIGITAL INFORMATION, e.g. TELEGRAPHIC COMMUNICATION
- H04L9/00—Cryptographic mechanisms or cryptographic arrangements for secret or secure communications; Network security protocols
- H04L9/14—Cryptographic mechanisms or cryptographic arrangements for secret or secure communications; Network security protocols using a plurality of keys or algorithms
-
- H—ELECTRICITY
- H04—ELECTRIC COMMUNICATION TECHNIQUE
- H04L—TRANSMISSION OF DIGITAL INFORMATION, e.g. TELEGRAPHIC COMMUNICATION
- H04L9/00—Cryptographic mechanisms or cryptographic arrangements for secret or secure communications; Network security protocols
- H04L9/32—Cryptographic mechanisms or cryptographic arrangements for secret or secure communications; Network security protocols including means for verifying the identity or authority of a user of the system or for message authentication, e.g. authorization, entity authentication, data integrity or data verification, non-repudiation, key authentication or verification of credentials
- H04L9/3263—Cryptographic mechanisms or cryptographic arrangements for secret or secure communications; Network security protocols including means for verifying the identity or authority of a user of the system or for message authentication, e.g. authorization, entity authentication, data integrity or data verification, non-repudiation, key authentication or verification of credentials involving certificates, e.g. public key certificate [PKC] or attribute certificate [AC]; Public key infrastructure [PKI] arrangements
-
- H—ELECTRICITY
- H04—ELECTRIC COMMUNICATION TECHNIQUE
- H04L—TRANSMISSION OF DIGITAL INFORMATION, e.g. TELEGRAPHIC COMMUNICATION
- H04L9/00—Cryptographic mechanisms or cryptographic arrangements for secret or secure communications; Network security protocols
- H04L9/32—Cryptographic mechanisms or cryptographic arrangements for secret or secure communications; Network security protocols including means for verifying the identity or authority of a user of the system or for message authentication, e.g. authorization, entity authentication, data integrity or data verification, non-repudiation, key authentication or verification of credentials
- H04L9/3263—Cryptographic mechanisms or cryptographic arrangements for secret or secure communications; Network security protocols including means for verifying the identity or authority of a user of the system or for message authentication, e.g. authorization, entity authentication, data integrity or data verification, non-repudiation, key authentication or verification of credentials involving certificates, e.g. public key certificate [PKC] or attribute certificate [AC]; Public key infrastructure [PKI] arrangements
- H04L9/3268—Cryptographic mechanisms or cryptographic arrangements for secret or secure communications; Network security protocols including means for verifying the identity or authority of a user of the system or for message authentication, e.g. authorization, entity authentication, data integrity or data verification, non-repudiation, key authentication or verification of credentials involving certificates, e.g. public key certificate [PKC] or attribute certificate [AC]; Public key infrastructure [PKI] arrangements using certificate validation, registration, distribution or revocation, e.g. certificate revocation list [CRL]
-
- H—ELECTRICITY
- H04—ELECTRIC COMMUNICATION TECHNIQUE
- H04L—TRANSMISSION OF DIGITAL INFORMATION, e.g. TELEGRAPHIC COMMUNICATION
- H04L9/00—Cryptographic mechanisms or cryptographic arrangements for secret or secure communications; Network security protocols
- H04L9/32—Cryptographic mechanisms or cryptographic arrangements for secret or secure communications; Network security protocols including means for verifying the identity or authority of a user of the system or for message authentication, e.g. authorization, entity authentication, data integrity or data verification, non-repudiation, key authentication or verification of credentials
- H04L9/3271—Cryptographic mechanisms or cryptographic arrangements for secret or secure communications; Network security protocols including means for verifying the identity or authority of a user of the system or for message authentication, e.g. authorization, entity authentication, data integrity or data verification, non-repudiation, key authentication or verification of credentials using challenge-response
- H04L9/3273—Cryptographic mechanisms or cryptographic arrangements for secret or secure communications; Network security protocols including means for verifying the identity or authority of a user of the system or for message authentication, e.g. authorization, entity authentication, data integrity or data verification, non-repudiation, key authentication or verification of credentials using challenge-response for mutual authentication
-
- G—PHYSICS
- G06—COMPUTING OR CALCULATING; COUNTING
- G06F—ELECTRIC DIGITAL DATA PROCESSING
- G06F2221/00—Indexing scheme relating to security arrangements for protecting computers, components thereof, programs or data against unauthorised activity
- G06F2221/21—Indexing scheme relating to G06F21/00 and subgroups addressing additional information or applications relating to security arrangements for protecting computers, components thereof, programs or data against unauthorised activity
- G06F2221/2115—Third party
-
- H—ELECTRICITY
- H04—ELECTRIC COMMUNICATION TECHNIQUE
- H04L—TRANSMISSION OF DIGITAL INFORMATION, e.g. TELEGRAPHIC COMMUNICATION
- H04L2209/00—Additional information or applications relating to cryptographic mechanisms or cryptographic arrangements for secret or secure communication H04L9/00
- H04L2209/76—Proxy, i.e. using intermediary entity to perform cryptographic operations
-
- H—ELECTRICITY
- H04—ELECTRIC COMMUNICATION TECHNIQUE
- H04L—TRANSMISSION OF DIGITAL INFORMATION, e.g. TELEGRAPHIC COMMUNICATION
- H04L47/00—Traffic control in data switching networks
- H04L47/10—Flow control; Congestion control
- H04L47/12—Avoiding congestion; Recovering from congestion
-
- H—ELECTRICITY
- H04—ELECTRIC COMMUNICATION TECHNIQUE
- H04L—TRANSMISSION OF DIGITAL INFORMATION, e.g. TELEGRAPHIC COMMUNICATION
- H04L63/00—Network architectures or network communication protocols for network security
- H04L63/14—Network architectures or network communication protocols for network security for detecting or protecting against malicious traffic
- H04L63/1408—Network architectures or network communication protocols for network security for detecting or protecting against malicious traffic by monitoring network traffic
- H04L63/1425—Traffic logging, e.g. anomaly detection
Definitions
- An embodiment of the present invention relates to a communication control device and a communication system.
- the communication system needs to protect the data it handles and the control information of the device from attacks such as malware.
- devices such as surveillance cameras installed as social infrastructure need to ensure the safety of data to be communicated.
- it is difficult to replace each device that builds social infrastructure, such as a surveillance camera, frequently, so there is a problem that safety measures become insufficient.
- the problem to be solved by the present invention is to provide a communication control device and a communication system capable of improving the safety of communication used in a social infrastructure system or the like.
- the communication control device has a communication interface, a controller, and a memory.
- the communication interface communicates with the device connected via the first device and the network communication network.
- the controller is determined by the mutual authentication process between the second device and the second communication control device connected between the second device and the network communication network, which uses the private key issued by the private certificate authority and the client certificate.
- Information transmitted from the second device to the first device by transmitting to the second communication control device, information obtained by encrypting the information transmitted from the first device to the second device using the common key
- the decrypted information is transmitted to the first device.
- the memory stores the analysis information of the communication volume of data communication via the communication interface.
- the controller sends the log information to the device management server at the execution time set based on the analysis information of the communication volume stored in the memory.
- FIG. 1 is a diagram illustrating a basic configuration example of a communication system according to each embodiment.
- FIG. 2 is a block diagram showing a functional configuration example of the client device and the server device according to each embodiment.
- FIG. 3 is a block diagram showing a functional configuration example of the communication control device on the client side and the communication control device on the server side according to each embodiment.
- FIG. 4 is a diagram showing a hardware configuration example of an IC card as a configuration example of an authentication unit in the communication control device according to each embodiment.
- FIG. 5 is a block diagram showing a functional configuration example of the C card as a configuration example of the authentication unit in the communication control device according to each embodiment.
- FIG. 6 is a block diagram showing a functional configuration example in the communication control management device according to each embodiment.
- FIG. 1 is a diagram illustrating a basic configuration example of a communication system according to each embodiment.
- FIG. 2 is a block diagram showing a functional configuration example of the client device and the server device according to each embodiment.
- FIG. 7 is a sequence showing an example of processing performed by the communication system shown in FIG.
- FIG. 8 is a diagram showing a first configuration example of the communication system according to the first embodiment.
- FIG. 9 is a block diagram showing a configuration example of the communication control device in the first configuration example of the communication system according to the first embodiment.
- FIG. 10 is a sequence for explaining an operation example of the communication system according to the first configuration example of the first embodiment.
- FIG. 11 is a diagram illustrating a second configuration example of the communication system according to the first embodiment.
- FIG. 12 is a block diagram showing a configuration example of a communication control device in a second configuration example of the communication system according to the first embodiment.
- FIG. 13 is a sequence for explaining an operation example of the communication system according to the second configuration example of the first embodiment.
- FIG. 14 is a diagram illustrating a configuration example of a communication system according to the second embodiment.
- FIG. 15 is a block diagram showing a configuration example of the communication control device in the configuration example of the communication system according to the second embodiment.
- FIG. 16 is a flowchart for explaining an operation example of the distributed controller in the communication system according to the second embodiment.
- FIG. 17 is a block diagram showing a configuration example of a communication system according to the third embodiment.
- FIG. 18 is a sequence for explaining a first operation example of the communication system according to the third embodiment.
- FIG. 19 is a sequence for explaining the second operation example of the communication system according to the third embodiment.
- FIG. 20 is a sequence for explaining the first operation example of the communication system according to the fourth embodiment.
- FIG. 21 is a sequence for explaining the second operation example of the communication system according to the fourth embodiment.
- FIG. 22 is a sequence for explaining the third operation example of the communication system according to the fourth embodiment.
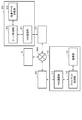
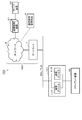
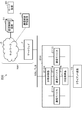
- FIG. 1 is a diagram showing a configuration example of a communication system 1 having a configuration that is a base of the communication system according to each embodiment.
- the communication system 1 includes a client device 10 (10-1 to 10-N), a server device 20, and a communication control device 30 (30-1 to 30-N) on the client side (“first communication control device”).
- first communication control device an example
- server-side communication control device 31 an example of a “first communication control device”
- communication control management device 5 an example of a “private certificate authority”
- network 6 and the gateway 7 that connects the network 6 to the client device 10 and the like are collectively referred to as “network NW”.
- the client device 10 connects to the network NW via the communication control device 30 on the client side.
- the server device 20 connects to the network NW via the communication control device 31 on the server side. The details of the configurations of the client device 10 and the server device 20 will be described later.
- the communication control device 30 on the client side is connected between the client device 10 and the network NW, and mediates communication between the client device 10 and the server device 20.
- the communication control device 30 on the client side acquires the data transmitted to the server device 20 by the client device 10, and outputs the acquired data to the server device 20.
- the communication control device 30 on the client side encrypts the data acquired from the client device 10 and transmits the encrypted data to the server device 20.
- the communication control device 30 on the client side acquires the data transmitted to the client device 10 by the server device 20, and outputs the acquired data to the client device 10.
- the data acquired by the communication control device 30 on the client side is encrypted data.
- the communication control device 30 on the client side outputs data to the client device 10, it decodes the data acquired from the server device 20 via the communication control device 31 on the server side, and outputs the decoded data to the client device 10. To do.
- the communication control device 31 on the server side is connected between the server device 20 and the network NW, and mediates communication between the client device 10 and the server device 20.
- the communication control device 31 on the server side acquires data transmitted to the client device 10 by the server device 20, and transmits the acquired data to the client device 10.
- the communication control device 31 on the server side encrypts the data acquired from the server device 20 and transmits the encrypted data to the client device 10.
- the communication control device 31 on the server side acquires the data transmitted to the server device 20 by the client device 10, and outputs the acquired data to the server device 20.
- the data acquired by the communication control device 31 on the server side is encrypted data.
- the communication control device 31 on the server side outputs data to the server device 20, it decodes the data acquired from the client device 10 via the communication control device 30 on the client side, and outputs the decoded data to the server device 20. To do.
- encryption is performed by the SSL (Secure Socket Layer) / TLS (Transport Layer Security) protocol.
- the communication control device 30 on the client side and the communication control device 31 on the server side for example, encrypt the data contained in HTTP by combining the SSL / TLS protocol with HTTP, and improve the security of HTTPS (HTTP Secure). ).
- the data encryption performed by the communication control device 30 on the client side and the communication control device 31 on the server side is not limited to using HTTP as HTTPS.
- the client-side communication control device 30 and the server-side communication control device 31 may be replaced with a secure communication protocol with improved safety by combining the SSL/TLS protocol with various communication protocols.
- the communication control device 30 on the client side and the communication control device 31 on the server side may replace FTP (File Transfer Protocol) with FTPS (FTP Secure).
- the data encrypted by the communication control device 30 on the client side or the communication control device 31 on the server side is output to the network NW.
- the data flowing through the network NW in the communication system 1 is encrypted data. Therefore, the risk that the data transmitted / received on the network NW is maliciously accessed from the outside and the data is eavesdropped is avoided, and the safety is improved.
- the data eavesdropping referred to here means an "act of eavesdropping on data" or an "act of extracting data”.
- the communication control management device 5 is a communication management server for managing communication using the communication control device on the client side and the communication control device on the server side. For example, the communication control management device 5 issues a client certificate and a private key to the communication control device 30 on the client side. In the configuration example shown in FIG. 1, the communication control management device 5 issues a client certificate and a private key stored in an IC card mounted on the communication control device 30 on the client side. Further, the communication control management device 5 transmits the client certificate stored in the IC card and the private key to the client-side communication control device 30 in which the IC card is mounted via the network NW.
- the communication control management device 5 issues a server certificate and a private key to the communication control device 31 on the server side.
- the communication control management device 5 issues the server certificate and the private key stored in the IC card.
- the communication control management device 5 transmits the server certificate and the private key stored in the IC card to the communication control device 31 on the server side in which the IC card is mounted via the network NW.
- the client certificate, the server certificate, and the private key are used to determine a common key (session key) used when the client-side communication control device 30 and the server-side communication control device 31 perform encrypted communication. Is the information necessary for.
- the client device 10 and the server device 20 are, for example, components that construct a social infrastructure system.
- Social infrastructure is equipment necessary for preparing social infrastructure such as road transportation network, power generation equipment, distribution power equipment, water treatment equipment, gas distribution equipment, and the like.
- the social infrastructure system is, for example, a mechanism for stably operating the social infrastructure by monitoring the social infrastructure, grasping changes in the situation, and responding to the changes.
- the client device 10 and the server device are components of a monitoring system that monitors roads and public facilities will be described as an example.
- the client device 10 is a device (network surveillance camera) that transmits image data in which the road conditions and the like are imaged via the network NW.
- the server device 20 is a device that receives the imaging data transmitted by the client device 10 via the network NW.
- the client device 10 and the server device 20 are not limited to the components of the monitoring system.
- the client device 10 and the server device may be components of a system that monitors the power status of power generation equipment or delivery power equipment, a system that acquires the delivery status at a distribution center, or equipment at a factory or research institute. It may be a component such as a system that acquires the operating status of.
- FIG. 2 is a block diagram showing a functional configuration example of the client device 10 and the server device 20 shown in FIG.
- the client device 10 includes a NW (network) communication unit 11, a client control unit 12, and an imaging unit 13.
- the NW communication unit 11 is, for example, an Ethernet (registered trademark) port of the client device 10.
- the NW communication unit 11 is connected to the communication control device 30 on the client side, and outputs the data transmitted from the client device 10 to the server device 20 to the communication control device 30 on the client side.
- the NW communication unit 11 corresponds to a functional unit that is connected to the network NW and communicates with the server device 20 via the network NW in a conventional system.
- the client control unit 12 is, for example, a processor including a CPU and the like, and controls the client device 10 in an integrated manner.
- the client control unit 12 causes the imaging unit 13 to start or stop imaging according to the control from the server device 20, and sets imaging conditions such as the direction of the camera to be imaged with respect to the imaging unit 13 and the magnification at the time of imaging. To set.
- the imaging unit 13 captures a landscape at a predetermined location according to the instructions of the client control unit 12.
- the imaging unit 13 outputs the captured data (imaging data) to the client control unit 12.
- the server device 20 includes a NW (network) communication unit 21, a server control unit 22, and an imaging data storage unit 23.
- the NW communication unit 21 is, for example, an Ethernet (registered trademark) port of the server device 20.
- the NW communication unit 21 is connected to the communication control device 31 on the server side, and outputs data transmitted from the server device 20 to the client device 10 to the communication control device 31 on the server side.
- the NW communication unit 21 corresponds to a functional unit that is connected to the network NW and communicates with the client device 10 via the network NW in the case of a conventional system.
- the server control unit 22 is, for example, a processor including a CPU and controls the server device 20 in a centralized manner.
- the server control unit 22 stores, for example, the imaged data captured by the client device 10 in the imaged data storage unit 23.
- the imaging data storage unit 23 stores the imaging data according to the instruction of the server control unit 22.
- unencrypted information (so-called plain text) output to the network NW by the client device 10 or the server device 20 flows through the network NW.
- the client device 10 encrypts the imaged data and outputs it to the network NW.
- the client control unit 12 of the client device 10 encrypts the imaging data and outputs the encrypted imaging data to the network NW.
- a processor such as a CPU provided in a surveillance camera is generally used for the purpose of compressing or encoding image data, it is further subjected to processing for encryption. In many cases, it does not have enough resources. In such a case, the CPU originally possessed by the client control unit 12 cannot encrypt the captured data.
- the client control unit 12 encrypts the imaging data, it is necessary to change or replace the hardware configuration of the client control unit 12, such as mounting a processor for encrypting the imaging data on the client control unit 12. It is conceivable that Since the client device 10 is a component that constitutes social infrastructure such as a surveillance camera, it is not easy to change or replace the hardware configuration. In view of these circumstances, it is desirable that the captured data is encrypted and output to the network NW without changing the client device 10.
- the client-side communication control device 30 connected between the client device 10 and the network NW encrypts the data transmitted by the client device 10 and outputs the encrypted data to the network NW.
- the communication control device 31 on the server side connected between the server device 20 and the network NW encrypts the control data transmitted by the server device 20 and outputs the control data to the network NW.
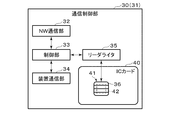
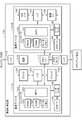
- FIG. 3 is a block diagram showing a functional configuration example of the communication control device 30 on the client side and the communication control device 31 on the server side shown in FIG.
- the functional configurations of the communication control device 30 on the client side and the communication control device 31 on the server side are the same. Therefore, in the following, the configuration of one (for example, the communication control device 30 on the client side) will be described, and the configuration of the other (for example, the communication control device 31 on the server side) will not be described. Further, hereinafter, when the communication control device 30 on the client side and the communication control device 31 on the server side are not distinguished, they are simply referred to as the communication control device 30 (31) and the like.
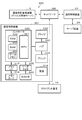
- the communication control device 30 (31) includes a NW (network) communication unit 32, a control unit 33, a device communication unit 34, a reader / writer 35, and an IC card 40.
- the IC card 40 is an example of the "authentication unit".
- the authentication unit is not limited to that realized by the reader / writer 35 and the IC card 40.
- the authentication unit may be realized by the control unit 33 or may be realized by a processing circuit for authentication processing.
- the NW communication unit 32 is connected to the network NW and communicates with the other communication control device 30 (31) via the network NW.
- the control unit 33 is, for example, a processor including a CPU and the like, and controls the communication control device 30 (31) in an integrated manner.
- the control unit 33 transmits a command to the IC card 40 and receives a response from the IC card 40 via the reader/writer 35, for example.
- the control unit 33 also transmits information based on the response received from the IC card 40 to the other communication control device 30 (31) via the NW communication unit 32. Further, the control unit 33 transmits a command to the IC card 40 based on the information received from the other communication control device 30 (31) via the NW communication unit 32.
- the device communication unit 34 is connected to the device (client device 10 or server device 20) and communicates with the device. Specifically, the device communication unit 34 of the communication control device 30 on the client side is connected to the client device 10, acquires imaging data from the client device 10, and outputs the decrypted control data to the client device 10. .. Further, the device communication unit 34 of the communication control device 31 on the server side is connected to the server device 20, acquires the control data from the server device 20, and outputs the decoded imaging data to the server device 20.
- the reader / writer 35 connects to the IC card 40 via the contact unit 36 and communicates with the IC card 40.
- the IC card 40 is formed by mounting the IC module 41 on, for example, a plastic card base material. That is, the IC card 40 includes an IC module 41 and a card base material in which the IC module 41 is embedded.
- the IC card 40 is detachably attached to the communication control device 30 (31) and can communicate with the communication control device 30 (31) via the contact portion 36.
- the IC card 40 receives, for example, a command (processing request) transmitted by the communication control device 30 (31) via the contact unit 36, and executes processing (command processing) according to the received command. Then, the IC card 40 transmits a response (processing response), which is the execution result of the command processing, to the communication control device 30 (31) via the contact unit 36.
- a command processing request
- processing response processing response
- the IC module 41 includes a contact portion 36 and an IC chip 42.
- the contact portion 36 has terminals for various signals necessary for the IC card 40 to operate.
- the terminals of various signals are terminals that receive power supply voltage, clock signal, reset signal, etc. from the communication control device 30 (31), and serial data input for communicating with the communication control device 30 (31). It has an output terminal (SIO terminal).
- the IC chip 42 is, for example, an LSI (Large Scale Integration) such as a one-chip microprocessor.
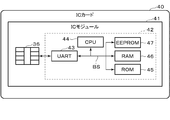
- FIG. 4 is a diagram showing a hardware configuration example of the IC card 40 shown in FIG.
- the IC card 40 includes an IC module 41 including a contact portion 36 and an IC chip 42.
- the IC chip 42 includes a UART (Universal Asynchronous Receiver Transmitter) 43, a CPU 44, a ROM (Read Only Memory) 45, a RAM (Random Access Memory) 46, and an EEPROM (registered trademark) (Electrically Erasable Programmable ROM) 47.
- UART Universal Asynchronous Receiver Transmitter
- CPU 44 central processing unit
- ROM Read Only Memory
- RAM Random Access Memory
- EEPROM registered trademark
- each configuration (43 to 47) is connected via an internal bus BS.
- the UART 43 performs serial data communication with the communication control device 30 (31) via the SIO terminal described above.
- the UART 43 outputs data (for example, 1-byte data) obtained by parallel conversion of the serial data signal received via the SIO terminal to the internal bus BS. Further, the UART 43 serially converts the data acquired via the internal bus BS and outputs the data to the communication control device 30 (31) via the SIO terminal.
- the UART 43 receives a command from the communication control device 30 (31) via the SIO terminal, for example. Further, the UART 43 transmits a response to the communication control device 30 (31) via the SIO terminal.
- the CPU 44 executes a program stored in the ROM 45 or the EEPROM 47 to perform various processes on the IC card 40.
- the CPU 44 executes command processing according to the command received by the UART 43, for example, via the contact unit 36.
- the ROM 45 is, for example, a non-volatile memory such as a mask ROM, and stores data such as a program for executing various processes of the IC card 40 and a command table.
- the RAM 46 is, for example, a volatile memory such as an SRAM (Static RAM), and temporarily stores data used when performing various processes of the IC card 40.
- the EEPROM 47 is, for example, an electrically rewritable non-volatile memory.
- the EEPROM 47 stores various data used by the IC card 40.
- the EEPROM 47 stores information used for various services (applications) using the IC card 40, for example.
- FIG. 5 is a block diagram showing a functional configuration example of the IC card 40 shown in FIG.
- the IC card 40 includes a communication unit 50, a control unit 51, and a storage unit 54.
- each unit of the IC card 40 shown in FIG. 5 is realized by using the hardware of the IC card 40 shown in FIG.
- the communication unit 50 is realized by, for example, a UART 43, a CPU 44, and a program stored in the ROM 45, and sends and receives commands and responses between, for example, the communication control device 30 (31) via the contact unit 36. I do. That is, the communication unit 50 receives a command (processing request) requesting a predetermined process from the communication control device 30 (31), and transmits a response (processing response) to the command to the communication control device 30 (31). The communication unit 50 stores the received data received from the communication control device 30 (31) via the UART 43 in the RAM 46. The communication unit 50 also transmits the transmission data stored in the RAM 46 to the communication control device 30 (31) via the UART 43.
- the control unit 51 is realized by, for example, the CPU 44, the RAM 45, the ROM 46, or the EEPROM 47, and integrally controls the IC card 40.
- the control unit 51 includes a command processing unit 52 and an encryption/decryption unit 53.
- the process performed by the command processing unit 52 is an example of “authentication process”.
- the process performed by the encryption / decryption unit 53 is an example of the “encryption / decryption process”.
- the command processing unit 52 executes various command processing.
- the command processing unit 52 performs an SSL/TLS handshake, for example, as command processing for requesting an HTTPS request described later.
- SSL / TLS handshake key information and the like necessary for encrypted communication are exchanged, and mutual authentication with the communication destination device is performed.
- mutual authentication is an authentication process for mutually confirming that the communication control device 30 on the client side and the communication control device 31 on the server side are devices that have been properly authenticated with each other before performing communication. is there.
- the encryption / decryption unit 53 executes a process of encrypting data and a process of decrypting encrypted data.
- the encryption / decryption unit 53 encrypts the data output by the device (client device 10 or server device 20) acquired via the communication unit 50. Further, the encryption / decryption unit 53 decrypts the encrypted data from the network NW acquired via the communication unit 50.
- the storage unit 54 is, for example, a storage unit composed of an EEPROM 47, and includes a certificate information storage unit 55 and a secret information storage unit 56.
- the certificate information storage unit 55 stores the certificate issued by the communication control management device 5 for the device (the client device 10 or the server device 20).
- the certificate information storage unit 55 of the IC card 40 mounted on the client-side communication control device 30 stores information indicating the client certificate.
- information indicating the server certificate is stored in the certificate information storage unit 55 of the IC card 40 attached to the communication control device 31 on the server side.
- the secret information storage unit 56 stores a secret key for the device (client device 10 or server device 20) issued by the communication control management device 5. Specifically, the secret information storage unit 56 of the IC card 40 mounted on the communication control device 30 on the client side stores information indicating the secret key issued to the communication control device 30 on the client side. .. Further, the certificate information storage unit 55 of the IC card 40 mounted on the communication control device 31 on the server side stores information indicating the private key issued to the communication control device 31 on the server side.
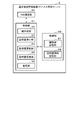
- FIG. 6 is a block diagram showing a configuration example of the communication control management device 5 shown in FIG.
- the communication control management device 5 includes, for example, a NW (network) communication unit 60, a control unit 61, and a storage unit 66.
- the NW communication unit 60 is connected to the network NW and communicates with the communication control device 30 (31) via the network NW.
- the control unit 61 includes a processor such as a CPU, for example.
- the control unit 61 realizes various processes by the processor executing programs.
- the control unit 61 comprehensively controls the communication control management device 5. Further, the control unit 61 mainly operates as a private certificate authority that recognizes the validity of the communication control device 30 (31).
- the control unit 61 functions as a key generation unit 62, a certificate issuing unit 63, a certificate updating unit 64, a certificate management unit 65, and a management unit 69 by the processor executing a program. Execute the process to realize.
- the key generation unit 62 issues a private key corresponding to the public key included in the certificate described later, based on, for example, an authentication application from the communication control device 30 (31).
- the certificate issuing unit 63 issues a certificate that recognizes the validity of the communication control device 30 (31), for example, based on the certification application from the communication control device 30 (31).
- the certificate includes a public key and information indicating the owner of the communication control device 30 (31).
- the certificate renewal unit 64 renews the certificate by setting a new expiration date for the certificate whose expiration date has passed.
- the certificate update unit 64 issues a certificate in which the validity period of the certificate issued to the communication control device 30 (31) is extended, for example, based on an update application from the communication control device 30 (31). Then, the issued certificate is transmitted to the communication control device 30 (31). Information indicating the issued certificate is received by the communication control device 30 (31) and is stored in the certificate information storage unit 405 of the IC card 40 of the communication control device 30 (31). ) Certificate expiration date is extended.
- the certificate management unit 65 manages the certificates that have already been issued. When the certificate management unit 65 does not prove the validity of each other in mutual authentication due to, for example, falsification or theft of the IC card 40 mounted on the communication control device 30 (31), the communication control device 30 (31) Performs the process of invalidating the certificate issued to. In addition, the certificate management unit 65 uses the certificate management unit 65 to issue a certificate issued to the communication control device 30 (31) and other communication devices based on an inquiry from the communication control device 30 (31 ). You may respond whether it was issued or not. Further, the certificate management unit 65 may periodically check whether the issued certificate is used in the legitimate communication control device 30 (31).
- the management unit 69 manages the communication control device 30 (31). For example, the management unit 69 remotely controls the mutual authentication performed by the communication control device 30 (31) via the network NW.
- the storage unit 66 includes, for example, a key information storage area 67 and a certificate information storage area 68.
- the key information storage area 67 stores, for example, information indicating an already issued public key or a private key.
- the certificate information storage area 68 stores, for example, information indicating a certificate that has already been issued.
- the key information storage area 67 and the certificate information storage area 68 are referred to, for example, when the key generation unit 62 issues a private key and when the certificate issuing unit 63 issues a certificate. Further, in the key information storage area 67, information indicating a private key issued by the key generation unit 62 is stored. Further, in the certificate information storage area 68, information indicating a certificate issued by the certificate issuing unit 63 is stored.
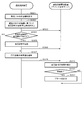
- FIG. 7 is a sequence chart showing an example of processing performed by the communication system 1.
- the client device 10 When transmitting the imaging data to the server device 20, the client device 10 first transmits an HTTP request to the server device 20 (step S1).
- the HTTP request transmitted by the client device 10 is acquired by the communication control device 30 on the client side (step S2).
- step S3 When the communication control device 30 on the client side acquires the HTTPS request transmitted by the client device 10, it transmits an HTTPS request (Client Hello) to the communication control device 31 on the server side (step S3). As a result, a handshake between the communication control device 30 on the client side and the communication control device 31 on the server side is started (step S4).
- the Client Hello transmitted by the communication control device 30 on the client side includes, for example, the TLS version and information indicating a list of encryption methods and algorithms used for communication.
- the server-side communication control device 31 transmits an HTTPS response (Server Hello) to the client-side communication control device 30 as a response to the Client Hello.
- the server hello transmitted by the communication control device 31 on the server side includes, for example, information selected by the server device 20 from the options presented by the client hello. In other words, the communication control device 31 on the server side selects a presentation from the communication control device 30 on the client side, thereby determining a specific encryption algorithm in communication.
- the communication control device 31 on the server side sends information necessary for the common key used for encrypted communication.
- the information required for the common key includes, for example, information indicating the public key issued to the server device 20 and its certificate, and information requesting to send the public key of the client device 10 and its certificate. Is done.
- the client-side communication control device 30 sends the server-side communication control device 31 the information necessary for the public key issued to itself and its certificate, and the common key used for encrypted communication.
- Mutual authentication between the communication control device 30 on the client side and the communication control device 31 on the server side is performed, for example, as follows.
- the communication control device 30 on the client side generates a signature from the Server Hello or the like received so far and transmits it to the communication control device 31 on the server side.
- the communication control device 31 on the server side verifies the signature received from the communication control device 30 on the client side based on the certificate received from the communication control device 30 on the client side. If the verification is successful, the server-side communication control device 31 determines that the certificate definitely belongs to the client-side communication control device 30. Further, the communication control device 31 on the server side generates a signature from the Client Hello or the like received so far and transmits it to the communication control device 30 on the client side.
- the communication control device 30 on the client side verifies the signature received from the communication control device 31 on the server side based on the certificate received from the communication control device 31 on the server side. When the verification is successful, the client-side communication control device 30 determines that the certificate definitely belongs to the server-side communication control device 31.
- the client-side communication control device 30 and the server-side communication control device 31 are used for encryption, respectively. Generate and exchange a common key.
- the communication control on the server side ends the handshake if the public key and its certificate sent from the communication control device 30 on the client side are certificates allowed by the communication control device 31 on the server side.
- the server-side communication control device 31 transmits an HTTP request to the server device 20 (step S5).
- the HTTP request is an HTTP request transmitted from the client device 10 in step S1.
- the HTTP request transmitted by the communication control device 31 on the server side is received by the server device 20 (step S6).
- the server device 20 recognizes that the client device 10 has requested the HTTP request. Therefore, the server device 20 responds to the HTTP response to the client device 10 (step S7).
- the HTTP response transmitted by the server device 20 is acquired by the communication control device 31 on the server side (step S8).
- the communication control device 31 on the server side encrypts the acquired HTTP response from the server device 20 using the common key determined in the handshake of step S4 (step S9).
- the HTTP response encrypted by the server-side communication control device 31 is received by the client-side communication control device 30 via the network NW (step S10).
- the communication control device 30 on the client side decodes the received HTTP response using the common key (step S11).
- the HTTP response decoded by the communication control device 30 on the client side is acquired by the client device 10 (step S12).
- the client device 10 receives the decrypted HTTP response (step S13). At this time, the client device 10 recognizes that the HTTP response is returned from the server device 20. Therefore, the client device 10 transmits the imaging data to the server device 20 (step S14).
- the imaging data transmitted by the client device 10 is acquired by the communication control device 30 on the client side (step S15).
- the communication control device 30 on the client side encrypts the imaged data transmitted by the client device 10 using a common key (step S16).
- the imaged data encrypted by the communication control device 30 on the client side is received by the communication control device 31 on the server side via the network NW (step S17).
- the communication control device 31 on the server side decrypts the received imaging data using the common key (step S18).
- the image pickup data decrypted by the communication control device 31 on the server side is acquired by the server device 20 (step S19).
- the server device 20 receives the decrypted imaging data (step S20). At this time, the server device 20 recognizes that the imaging data from the client device 10 has been received.
- the communication control device 30 on the client side communicates with the communication destination. Do not allow communication. Specifically, the communication control device 30 on the client side does not output the information transmitted from the communication destination to the client device 10. This is because if the mutual authentication is not performed correctly, the communication destination may be an unauthorized communication device disguised as the communication control device 31 on the server side. In this case, the communication control device 30 on the client side may transmit, for example, a communication record when mutual authentication is not correctly performed to the communication control management device 5. As a result, the communication control management device 5 can acquire a communication record when mutual authentication is not correctly performed, and grasp the pattern or frequency of unauthorized communication with the client-side communication control device 30 under management. This makes it possible to monitor network abnormalities.
- the communication control device 30 on the client side is a communication destination based on a destination list indicating information of a communication device that allows communication to the client device 10 instead of mutual authentication in the handshake performed in step S4 of the above flowchart. It may be determined whether or not to allow communication with.
- the information of the communication device shown in the destination list is, for example, a URL (Uniform Resource Locator).
- URL Uniform Resource Locator
- control unit 33 may update the destination list.
- the control unit 33 stores, for example, the URL of the communication destination that is permitted to communicate with the client device 10 and the URL of the communication destination that is not permitted to communicate with the client device 10 for a certain period of time. Then, the control unit 33 updates the transmission destination list by, for example, re-registering the URL of the communication destination that has been communicated for a certain period of time among the URLs registered in the transmission destination list.
- the communication control device 30 on the client side may transmit the communication destination URL that is permitted to communicate and the communication destination URL that is not permitted to communicate to the communication control management device 5 for a certain period of time.
- the communication control management device 5 may update the destination list based on the communication destination URL that has communicated with the communication control device 30 on the client side.
- the communication control management device 5 By updating the transmission destination list by the communication control management device 5, it is possible to collectively manage the communication devices that communicate with the client-side communication control device 30 under the control of the communication control management device 5.
- the client-side communication control device 30 verifies whether or not the content of the information (for example, the firmware update program) transmitted to the client device 10 after the handshake performed in step S4 is established is correct. You may do it.
- the control unit 33 of the communication control device 30 on the client side verifies using the verification key (verification key).
- the communication control management device 5 may transmit the verification key to, for example, the communication control device 30 on the client side and the communication control device 31 on the server side.
- the communication control device 31 on the server side generates a hash value from the information (plain text) transmitted to the client device 10, and encrypts the generated hash value with the verification key. Then, the communication control device 31 on the server side further encrypts the plaintext and the encrypted hash value with a secret key, and sends the encrypted hash value to the client device 10. Further, the communication control device 30 on the client side decrypts the information using the common key, and acquires the plaintext and the encrypted hash value.
- the communication control device 30 on the client side generates a hash value from the acquired plaintext and decrypts the encrypted hash value with the verification key.
- the communication control device 30 on the client side determines that the information transmitted to the client device 10 has the correct content when the hash value generated from the plain text and the decrypted hash value have the same value. In this case, the communication control device 30 on the client side outputs the decoded information (plain text) to the client device 10.
- the communication control device 30 on the client side determines that the information transmitted to the client device 10 is the server device 20 or the communication control on the server side. It is determined that the information may be illegal information transmitted from an unauthorized communication device disguised as the device 31. In this case, the communication control device 30 on the client side does not output the decoded information (plain text) to the client device 10.
- the client device 10 can receive only the information that has been verified and has been verified to be correct. Further, normally, it is considered that the client device 10 determines whether or not the content of the update program is correct when the firmware is updated. However, instead of the client device 10, the communication control device 31 on the server side instructs the client device 10 to do so. By verifying the content of the transmitted information, it is possible to reduce the processing load of the client device 10.
- the communication system 1 includes the client-side communication control device 30 connected between the client device 10 and the network NW, and the server-side communication connected between the server device 20 and the network NW.
- a control device 31 is provided.
- the communication control device 30 on the client side encrypts the information from the client device 10 and transmits it to the communication control device 31 on the server side via the network NW, and the information from the network NW (the server encrypted by the communication control device 31).
- Information from the device 20) is decoded and transmitted to the client device 10.
- the communication control device 31 on the server side encrypts the information from the server device 20 and transmits it to the communication control device 30 on the client side via the network NW, and the information from the network NW (the client encrypted by the communication control device 30). Information from the device) is decrypted and transmitted to the server device 20.
- the communication system 1 can improve the safety of the social infrastructure system without changing the social infrastructure system.
- the image data (so-called plain text) of the HTTP protocol transmitted from the client device 10 to the server device 20 is combined with, for example, the SSL / TLS protocol by the communication control device 30 on the client side to improve the safety. This is because it is replaced by HTTPS.
- the control data transmitted to the server device 20 or the client device 10 is encrypted, but is decrypted by the communication control device 30 on the client side and received by the client device 10, so the client device 10 It is not necessary to perform the process of decrypting the existing device, and the existing device can be used as it is without being changed.
- the communication control device 30 on the client side and the communication control device 31 on the server side perform mutual authentication, it is possible to improve safety as compared with the case of performing authentication in only one direction. ..
- a valid client certificate is issued and managed for the unspecified number of client terminals. It is not realistic to continue.
- the communication control device 30 on the client side and the communication control device 31 on the server side can perform mutual authentication, and the security can be improved.
- a client terminal that does not have a client certificate may be required to enter an ID and password issued by the server device in order to communicate with the server device.
- password authentication in order to maintain security, a long character string combining letters and numbers may be required for the password, or the password may be changed regularly.
- management becomes troublesome, and there are cases where passwords are leaked, such as when the password is written in a memo or recorded in a web browser.
- the communication control device 30 on the client side since the communication control device 30 on the client side has the client certificate, mutual authentication can be reliably performed with the server device 20. Therefore, password authentication is unnecessary. Therefore, the trouble of entering the password and the trouble of periodically changing and managing the password are eliminated, and the convenience of the user is improved. That is, safety can be maintained without imposing a burden on the user.
- the client device 10 and the server device 20 are illegal because mutual authentication is performed between the client device 10 and the server device 20 via the communication control device 30 (31). None be taken over by. That is, in the communication system 1, it is possible to take measures against ransomware.
- the terminal also called a stray device
- the terminal will be illegally hijacked and used as an illegal terminal that attacks malware etc.
- the communication control device 30 31
- mutual authentication is performed between the client device 10 and the server device 20 via the communication control device 30 (31), so that the administrator inside the network NW can perform the mutual authentication. Even when an absent terminal is illegally hijacked and used for an attack, it is possible to prevent infection with malware or the like.
- the server device 20 is connected to the communication control device 31 on the server side, and the authentication process is not performed inside the server device 20. Therefore, it is not necessary to hold a certificate or the like inside the server device 20, and it becomes clear that the server device 20 connected to the server-side communication control device 31 is under the control of the communication control management device 5.
- the server device 20 already has a functional unit corresponding to the communication control device 31 on the server side, the communication control device 31 on the server side is not necessarily physically connected between the server device 20 and the network NW. You don't have to.
- the functional unit corresponding to the communication control device 31 on the server side originally possessed by the server device 20 performs the authentication process with the communication control device 30 on the client side.
- control unit 401 of the IC card 40 is made to perform at least one of mutual authentication and encryption / decryption processing. Therefore, the device cost of the communication control device 30 (31) can be suppressed.
- the IC card 40 mounted on the communication control device 30 (31) performs at least one of mutual authentication and encryption / decryption processing.
- the configuration for performing mutual authentication and encryption / decryption processing is not limited to the IC card.
- the IC card 40 described above has a storage function for storing a private key and a client certificate (or a server certificate), and a processing function for performing at least one of mutual authentication and encryption / decryption processing. Any functional unit may be used, for example, a SIM card on which an IC chip is mounted, or a card form may not be adopted.
- the IC card 40 of the communication control device 30 on the client side is detachably attached to the communication control device 30 on the client side.
- the IC card 40 and the communication control device 30 on the client side can be separated. Therefore, when exchanging either one, the one device may be exchanged.
- the IC card 40 and the communication control device 30 on the client side are integrated, when the part corresponding to the IC card 40 is replaced, the entire communication control device 30 on the client side must be replaced.
- the maintenance cost when replacing a specific part such as the IC card 40 of the communication control device 30 on the client side can be suppressed.
- the communication system 1 further includes a communication control management device 5, and the communication control management device 5 stores a private key and a client certificate stored in an IC card 40 mounted on the communication control device 30 on the client side on the client side.
- the secret key stored in the IC card 40 mounted on the communication control device 31 on the server side and the server certificate are transmitted to the communication control device 31 on the server side.
- the communication system 1 can perform a handshake and determine the common key using the legitimate private key and certificate issued by the communication control management device 5, and in addition to achieving the above-mentioned effects, the society The safety of the infrastructure system can be further improved.
- the configuration of the communication system 1 is not limited to the above-mentioned example.
- the communication control device 30 (31) may use an HSM (Hardware Security Module) that realizes the functions of the communication control device 30 (31) by hardware based on the processing load. That is, the communication control device 30 (31) is not limited to the configuration in which an IC card is mounted as long as secure processing is possible, and an IC chip or an IC module that can realize the function of the communication control device 30 (31) is used. The configuration may be different.
- HSM Hardware Security Module
- secure communication using the SSL/TLS protocol may be constantly performed, or whether communication using the SSL/TLS protocol may be selectable. Further, only the communication in one direction of the bidirectional communication between the client device 10 and the server device 20 may be the communication using the SSL / HTTPS protocol. Further, secure communication using the SSL / HTTPS protocol may be performed at all times, or it may be possible to select whether or not to perform communication using the SSL / HTTPS protocol.
- communication using the SSL/TLS protocol may be constantly performed to store unauthorized access to the client device 10 and the server device 20.
- a record of unauthorized access may be transmitted to the communication control management device 5.
- the communication control management device 5 can recognize whether or not there is an unauthorized access, and can detect a warning sign before a large-scale attack on the entire system is started and take countermeasures.
- the communication control device 30 (31) periodically confirms whether or not the connection with the client device 10 or the server device 20 to which the own device is connected is maintained. May be. In this case, information indicating the connection state may be transmitted to the communication control management device 5.
- the communication control management device 5 determines that the communication control device 30 (31) is disconnected from the client device 10 or the server device 20 when the information indicating the connection state cannot be received from the communication control device 30 (31), The disconnected communication control device 30 (31) is invalidated. By doing so, the communication control management device 5 prevents the disconnected communication control device 30 (31) from being connected to an unauthorized device and being misused for spoofing.
- the IC card 40 mounted on the communication control device 30 (31) may be equipped with a highly tamper-resistant chip called a secure element that has acquired CC (Common Criteria/ISO15408) certification. .. By using this chip to store a certificate containing a private key and a public key, extremely high security can be maintained.
- CC Common Criteria/ISO15408
- the program of the client device 10 may be updated from the server device 20, the communication control management device 5, or the like via the communication control device 30 (31).
- the function of the client device 10 can be safely updated.
- the firmware transmitted from the server device 20 is, for example, signed by the server device 20 encrypted by the communication control device 31 on the server side. Granted.
- the client device 10 can determine that the transmitted firmware is definitely the firmware transmitted from the server device 20 by decoding the signature by the communication control device 30 on the client side.
- the client device 10 is erroneously based on the unauthorized firmware. It is possible to exclude that updates are made.
- the firmware can be safely updated from the server device 20, the communication control management device 5, and the like to the client device 10. It is also possible to reduce the work cost as compared with the case where the firmware is updated by physically moving the plurality of client devices 10 to the place where each client device 10 is installed.
- the client device 10 may be started or stopped from the server device 20, the communication control management device 5, or the like via the communication control device 30 (31). By starting or stopping (remote activation) via the communication control device 30 (31), the function of the client device 10 can be safely updated, and secure remote control can be realized.
- At least one of the client device 10 and the server device 20 may be a device that performs wireless communication via a wireless LAN or the like.
- the communication control device 30 on the client side has a wireless communication function and encrypts the data transmitted by the client device 10 and encrypts the data.
- the data is transmitted to the server device 20 by wireless communication.
- the communication control device 30 on the client side communicates with the communication control device 31 on the server side
- the communication destination of the communication control device 30 on the client side is limited to this.
- the communication control device 30-1 on the client side may communicate with the communication control device 30-2 on the client side.
- the communication control device 30-1 on the client side receives a signal to start communication from the communication control device 30-2 on the client side, it first performs mutual authentication with the communication control device 30-2 on the client side, and the client Confirm that the communication control device 30-2 on the side is a legitimate communication terminal.
- the communication control device 30-1 on the client side outputs the information received from the communication control device 30-2 on the client side to the client device 10.
- an authenticator to the transmitted data using encryption, it is possible to detect falsification of communication information and identify the sender. Therefore, in the communication system 1, in the communication between the communication control device 30 on the client side and the communication control device 31 on the server side and the communication between the communication control devices 30 on the client side, "from the correct partner" and "tampering" are performed. You can be assured that you will not "receive data.”
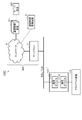
- FIG. 8 is a diagram showing a first configuration example of the communication system 100 according to the first embodiment.
- the communication control device 30 is replaced with the communication control device 101 in the system configuration shown in FIG.
- the communication control device 101 has a plurality of communication devices 111A and 111B provided in parallel between the network NW and the client device 10.
- each device other than the communication control device 101 in the communication system 100 can be realized by the same configuration as the device shown in FIG. Therefore, detailed description of configurations other than the communication control device 101 will be omitted below.
- the communication control device 31 may be configured to include a plurality of communication devices provided in parallel between the network NW and the server device 20 as in the communication control device 101.
- FIG. 9 is a block diagram showing a configuration example of the communication control apparatus 101 in the first configuration example of the communication system 100 according to the first embodiment.
- the communication control apparatus 101 has a first communication device 111A and a second communication device 111B arranged in parallel as a plurality of communication devices 111.
- the first communication device 111A and the second communication device 111B are connected in parallel between the hub 114 connected to the network NW side and the hub 115 connected to the client side in the communication control device 101.
- Each of the first communication device 111A and the second communication device 111B has a configuration that executes the same communication process as the communication control device 30 shown in FIG. 1 described above.
- the communication control apparatus 101 has a power supply 116 and a memory I/F 117 shared by the first communication device 111A and the second communication device 111B.
- the power supply 116 is connected to an external power supply and supplies the power from the external power supply to the communication devices 111A and 111B.
- the memory I / F 117 is an interface for setting a memory device 118 such as a memory card.
- the memory I / F 117 is set with a memory device 118 that stores information applied to the communication devices 111A and 111B such as initial setting information.
- the memory device 118 set in the memory I / F 117 may store data (for example, log data) supplied from the communication devices 111A and 111B.
- the communication control device 101 may be realized as a system in which a plurality of communication devices having the same configuration as the communication control device 30 are arranged in parallel.
- each communication device may include a power supply and a memory I/F.
- the first communication device 111A and the second communication device 111B may be arranged in parallel between the network NW and the client device 10.
- the communication control apparatus 101 may have a configuration in which the first communication device 111A and the second communication device 111B include interfaces for connecting to the network NW and the client apparatus 10, respectively, without providing the hubs 114 and 115. good.
- each communication control device 101 the first communication device 111A and the second communication device 111B are arranged in parallel between the network NW and the client device 10, and one of them is in the normal communication mode (first communication mode). Executes communication processing.
- the communication control device 101 realizes communication control between the network NW and the client device 10 by switching the communication devices 111A and 111B that communicate in the normal communication mode.
- the normal communication mode is assumed to be an operation mode in which communication involving encryption and decryption of transmission/reception data using a common key based on mutual authentication with the server-side communication control device 31 as described above is performed. .. Further, in the present embodiment, the communication control device 101 executes communication in the normal communication mode in the whitelist operation mode that allows communication with the destinations listed in the whitelist described later.
- the first communication device 111A and the second communication device 111B provided in parallel in the communication control device 101 may be realized by two independent software for communication processing.
- one communication device may be operated as two communication devices arranged in parallel, which are realized by two software.
- Each communication device 111 has a function of detecting its own failure, unauthorized access, malware infection, or the like. For example, the communication device 111 transmits information indicating a failure such as a failure, an unauthorized access, or malware infection, or a failure such as a communication failure to the communication control management device (device management server) 5. Further, each communication device 111 switches the operation mode according to an instruction from the communication control management device 5. For example, each communication device 111 switches from the non-communication state to the normal communication mode or switches from the normal communication mode to the non-communication state in response to an instruction from the communication control management device 5.
- each communication device 111 (111A, 111B) has a controller 120, a bridge 132, a hub 133, a bridge 134, a reader/writer 135, and an IC card 140.
- the controller 120 controls the communication device 111.
- the controller 120 includes an MPU 121, a RAM 122, a SAM 123, a data memory 124, and the like.
- the MPU 121 is an example of a processor that controls the controller 120.
- the MPU 121 implements various processes by executing a program stored in the data memory 124 or the like.
- the controller 120 executes processes such as communication control, failure detection, communication failure detection, self-diagnosis, and log information collection when the MPU 121 executes a program.
- the controller 120 causes the MPU 121 to execute a program, thereby performing mutual authentication processing with the server-side communication control device 31, encryption processing of data transmitted from the client device 10 to the network NW, and client processing via the network NW. Decryption processing of the encrypted data transmitted to the device may be performed. Further, the controller 120 may request the IC card 140 connected via the reader / writer 135 to perform at least one of mutual authentication processing, encryption processing, and decryption processing.
- the RAM 122 is a random access memory.
- the RAM 122 functions as a working memory for holding work data.
- the SAM 123 is a serial access memory.
- the data memory 124 is a rewritable nonvolatile memory.
- the data memory 124 stores programs and setting information.
- the data memory 124 stores a white list showing a list of destinations that are allowed to communicate.
- the controller 120 refers to the whitelist stored in the data memory 124 for communication. Execute. Further, the controller 120 may rewrite the white list in the data memory 124 in response to an instruction from the communication control management device 5.
- the communication device 111 may be put into a non-communication state by deleting all the destinations on the white list.
- the data memory 124 may store log information indicating the operating state of the communication device. The log information accumulated in the data memory 124 is sent to the communication control management device (device management server) 5 or used for self-diagnosis processing.
- the bridges 132 and 134 function as a communication interface (communication unit). Bridges 132 and 134 are connected to controller 120 via hub 133. The bridge 132 executes communication on the network NW side in the communication device 111. The bridge 132 realizes communication as the NW communication unit 32 shown in FIG. The bridge 132 supplies the data received from the network NW to the controller 120 via the hub 133. Further, the bridge 134 sends the data encrypted by the controller 120 or the IC card 140 to the network NW.
- the bridge 134 executes communication on the client device 10 side in the communication device 111.
- the bridge 134 realizes communication as the device communication unit 34 shown in FIG.
- the bridge 134 supplies the data from the client device 10 to the controller 120 via the hub 133.
- the bridge 134 transmits the data obtained by decrypting the encrypted data from the network NW with the controller 110 or the IC card 140 to the client device 10.
- the reader/writer 135 and the IC card 140 correspond to the reader/writer 35 and the IC card 40 shown in FIG. 3 described above.
- the IC card 140 can be realized by having the same configuration as the IC card 40 shown in FIG. 4 described above. Further, the IC card 140 has the same processing function as the IC card 40 shown in FIG. 5 described above, and functions as an example of the authentication unit in the communication control apparatus 101.
- FIG. 10 is a sequence for explaining an operation example in the communication system 100 having the configuration shown in FIG. 8 according to the first embodiment.
- the first communication device 111A executes communication in a normal operation mode (normal communication mode, first communication mode) based on the whitelist (step S101), and the second communication device 111B has not yet been executed. It is assumed that the communication state is set (step S102).
- the controller 120 of the first communication device 111A monitors the operation state such as the communication data amount, the communication speed, the communication time, the error detection frequency, and the like to determine whether there is a failure or a communication failure in the first communication device. It is detected (step S103). Further, the controller 120 may detect the presence or absence of a defect in the communication device 111A by executing the self-diagnosis at the set timing. Further, each communication device 111 may be provided with a detector for detecting a defect, and the controller 120 may acquire the detection result by the detector.
- step S103 If the controller 120 of the first communication device 111A does not detect a defect (step S103, NO), it continuously executes communication in the normal communication mode. Further, when the controller 120 of the first communication device 111A detects a defect during execution of communication in the normal communication mode (step S103, YES), the controller 120 transmits information indicating the defect to the communication control management device 5.
- Step S105 Information indicating a defect transmitted by the first communication device 111A of the communication control device 101 is acquired by the communication control management device 5 (step S105).
- the control unit 61 of the communication control management device 5 sets the second communication device 111B of the communication control device 101 to the normal communication mode according to the information indicating the failure from the first communication device 111A of the communication control device 101,
- the communication device 111A is controlled so as not to communicate.
- step S106 when the information indicating the defect is received from the first communication device 111A, the control unit 61 of the communication control management device 5 notifies the second communication device 111B of the communication control device 101 that is the source of the information indicating the defect.
- An instruction to switch to the normal communication mode is given (step S106).
- the instruction to switch from the communication control management device 5 to the normal communication mode is acquired by the second communication device 111B of the communication control device 101, which is the source of the information indicating the defect (step S107).
- the controller 120 of the second communication device 111B switches the operation mode to the normal communication mode in response to the switching instruction from the communication control management device 5 to the normal communication mode (step S108).
- the control unit 61 of the communication control management device 5 instructs the first communication device 111A of the communication control device 101, which is the source of the information indicating the defect, to the first communication device 111A. It is instructed to be in the non-communication state (step S109).
- the instruction to switch to the non-communication state from the communication control management device 5 is acquired by the first communication device 111B, which is the source of the information indicating the failure (step S110).
- the controller 120 of the first communication device 111A switches the operation mode to the non-communication state in response to the switching instruction from the communication control management device 5 to the non-communication state (step S111).
- the operation mode of the first communication device and the second communication device can be switched so that the communication as the communication control device 101 is not interrupted.
- the communication control management device (device management server) 5 sets the first communication device 111A in a non-communication state after the switching to the normal communication mode of the second communication device 111B is completed. Thereby, the communication control management device 5 can reliably ensure the availability of communication in the communication control device 101.
- the communication control apparatus 101 performs communication control in which, when a failure occurs in one communication device that is performing communication in the normal communication mode, the other communication device switches to perform communication in the normal communication mode. It may be realized in the device 101. For example, when the first communication device performing communication in the normal communication mode detects a defect, the controller 120 of the first communication device 111A requests the second communication device 111B to switch to the normal communication mode. May be. As a result, the second communication device 111B can be started in the normal communication mode in response to the request, and the first communication device 111A can be made to transition to the non-communication state. In this case, the first communication device and the second communication device can communicate with each other by their addresses.
- FIG. 11 is a diagram showing a second configuration example of the communication system 100 ′ according to the first embodiment.
- the communication system 100'shown in FIG. 11 replaces the communication control device 30 with the communication control device 101'in the system configuration shown in FIG.
- the communication control apparatus 101′ has a plurality of communication devices 111C and 111D arranged in series between the network NW and the client apparatus 10.
- each device other than the communication control device 101′ in the communication system 100′ can be realized by the same configuration as the device shown in FIG. Therefore, detailed description of the configuration of each device other than the communication control device 101'will be omitted below.
- the communication control device 31 is also configured to include a plurality of communication devices arranged in series between the network NW and the server device 20 as in the communication control device 101'. good.
- FIG. 12 is a block diagram showing a configuration example of the communication control device 101′ in the second configuration example of the communication system 100′ according to the first embodiment. In the configuration example illustrated in FIG.
- the communication control apparatus 101′ includes, as the plurality of communication devices 111, a first communication device 111C and a second communication device 111D that are arranged in series.
- the first communication device 111C connected to the network NW and the second communication device 111D connected to the client device 10 are connected in series.
- the communication control apparatus 101′ is assumed to have a power supply 116 and a memory I/F 117 shared by the first communication device 111C and the second communication device 111D.
- the power supply 116 is connected to an external power supply and supplies the power from the external power supply to the communication devices 111C and 111D, as in FIG.
- the memory I / F 117 is an interface for setting a memory device 118 such as a memory card, as in FIG.
- the communication control device 101′ may be realized as a system in which a plurality of communication devices having the same configuration as the communication control device 30 are arranged in series. In such a system, the plurality of communication devices 111'may each have a configuration such as a power supply and a memory I / F.
- the first communication device 111C and the second communication device 111D each have a configuration for executing the same communication processing as the communication control device 30 shown in FIG. 1 described above. That is, in each communication control device 101, one of the first communication device 111C and the second communication device 111D arranged in series between the network NW and the client device 10 is in the normal communication mode (first communication device). Mode), and the other communicates in the pass-through mode (second communication mode).
- the pass-through mode (second communication mode) is a communication mode in which input information is passed as it is and output.
- the normal communication mode is an operation mode in which communication is performed with encryption and decryption of transmitted / received data using a common key based on mutual authentication with the communication control device 31 on the server side as described above.
- the communication control device 101' is assumed to execute the communication in the whitelist operation mode which allows the communication with the destination in the whitelist as described above in the normal operation mode.
- first communication device 111C and the second communication device 111D provided in series in the communication control device 101' may be realized by two independent software for communication processing.
- one communication device may be operated as two communication devices arranged in parallel, which are realized by two software.
- Each communication device 111' has a function of detecting its own failure, unauthorized access, malware infection, or the like.
- the communication device 111' notifies the communication control management device (device management server) 5 of information indicating a failure such as a failure, an unauthorized access, or a malware infection, or a communication failure.
- each communication device 111's switches an operation mode according to an instruction from the communication control management device 5. For example, each communication device 111'switches from the pass-through mode to the normal communication mode or switches from the normal communication mode to the pass-through mode in response to an instruction from the communication control management device 5.
- each communication device 111′ (111C, 111D) has a controller 120, a bridge 132, a hub 133, a bridge 134, a reader/writer 135, an IC card 140, and the like, as in the configuration shown in FIG. I shall. Further, it is assumed that the controller 120 has an MPU 121, a RAM 122, a SAM 123, a data memory 124, and the like. Since each of these configurations can be realized with the same configuration as each configuration shown in FIG. 9, detailed description will be omitted.
- FIG. 13 is a sequence for explaining an operation example in the communication system 100'with the configuration shown in FIG.
- the first communication device 111C executes communication in a normal operation mode (normal communication mode) based on the whitelist (step S121), and the second communication device 111D operates in the pass-through mode. (Step S122).
- the controller 120 of the first communication device 111C monitors the operation state such as the communication data amount, the communication speed, the communication time, the error detection frequency, and the like to check whether there is a failure or a communication failure in the first communication device. Detect (step S123). Further, the controller 120 may detect the presence or absence of a defect in the communication device 111A by executing the self-diagnosis at the set timing. Further, each communication device 111 may be provided with a detector for detecting a defect, and the controller 120 may acquire the detection result by the detector.
- step S123 If the controller 120 of the first communication device 111C does not detect any malfunction (NO in step S123), the controller 120 continues to execute communication in the normal communication mode. Further, when the controller 120 of the first communication device 111C detects a defect during communication in the normal communication mode (YES in step S123), the controller 120 notifies the communication control management device 5 of information indicating the defect (step S124).
- step S125 Information indicating a defect notified by the first communication device 111C of the communication control device 101' is acquired by the communication control management device 5 (step S125).
- the control unit 61 of the communication control management device 5 sets the second communication device 111D of the communication control device 101′ to the normal communication mode according to the information indicating the failure from the first communication device 111C of the communication control device 101′,
- the first communication device 111C is controlled to be in the pass-through mode.
- the control unit 61 of the communication control management device 5 notifies the second communication device 111D of the communication control device 101′ that is the source of the information indicating the defect. Instructs the switch to the normal communication mode (step S126).
- the instruction to switch to the normal communication mode from the communication control management device 5 is acquired by the second communication device 111D in the communication control device 101'which is the source of the information indicating the defect (step S127).
- the controller 120 of the second communication device 111D switches the operation mode to the normal communication mode in response to the instruction to switch to the normal communication mode from the communication control management device 5 (step S128).
- the control unit 61 of the communication control management device 5 when receiving the information indicating the defect from the first communication device 111C, notifies the first communication device 111C of the communication control device 101′ that is the source of the information indicating the defect. Instructs that the pass-through mode is set (step S129).
- the instruction to switch to the pass-through mode from the communication control management device 5 is acquired by the first communication device 111C, which is the source of the information indicating the defect (step S130).
- the controller 120 of the first communication device 111C switches the operation mode to the pass-through mode in response to the instruction to switch to the pass-through mode from the communication control management device 5 (step S131).
- the communication control device has a redundant configuration in which a plurality of communication devices are provided.
- the communication control device even if a failure or a communication failure occurs in the communication control device for ensuring the security in data communication via the network, the communication can be continued without interruption. It is possible to realize communication operation with reliable availability.
- FIG. 14 is a diagram illustrating a configuration example of the communication system 200 according to the second embodiment.
- the communication control device 30 on the client side is replaced with the communication control device 201 in the system configuration shown in FIG.
- the communication control apparatus 201 includes a plurality of communication devices 211A, 211B, and 211C arranged in parallel between the network NW and the client apparatus 10 via the distributed controllers 212A and 212B. Have.
- each device other than the communication control device 201 in the communication system 200 can be realized by the same configuration as the device shown in FIG. Therefore, detailed description of configurations other than the communication control device 200 will be omitted.
- the communication control device 31 on the server side also has a plurality of communications arranged in parallel between the network NW and the server device 20 via a distributed controller, similarly to the communication control device 201. It may be configured to include a device.
- FIG. 15 is a block diagram showing a configuration example of the communication control device 201 in the configuration example of the communication system 200 according to the second embodiment.
- the communication control device 201 has three communication devices 211A, 211B, 211C arranged in parallel as a plurality of communication devices 211.
- the plurality of communication devices 211A to 211C are connected in parallel between the distributed controller 212A connected to the network NW and the distributed controller 212B connected to the client device 10 in the communication control device 201.
- Each of the plurality of communication devices 211A to 211C has a configuration that executes the same communication processing as the communication control device 30 shown in FIG. 1 described above.
- the distribution controllers 212A and 212B perform control for distributing the load of communication processing to the plurality of communication devices 211A to 211C. Therefore, the encryption/decryption processing and the mutual authentication processing by the certificate can be processed by the controllers of the respective communication devices 211A to 211C.
- the communication control device 201 has a power supply 216 shared by a plurality of communication devices 211A to 211C and the distributed controllers 212A and 212B.
- the communication control device 201 also has a memory I / F 217 shared by a plurality of communication devices 211A to 211C.
- the power supply 216 is connected to an external power supply and supplies the power from the external power supply to each of the communication devices 211A to 211C and the distributed controllers 212A and 212B.
- the memory I / F 217 is an interface for setting a memory device 218 such as a memory card. For example, a memory device 218 that stores setting information for each communication device 211 is set in the memory I / F 217.
- the number of communication devices 211 arranged in parallel is not limited to three, and may be a plurality. Further, in the communication control device 201, the communication devices 211 arranged in parallel may be those that perform the same communication processing, and may have different processing capacities. Further, in the communication control device 201, the communication devices 211 arranged in parallel may be replaced with those having different processing capacities.
- the communication control device 201 is realized as a distributed device system in which a plurality of communication devices having the same configuration as the communication control device 30 are arranged in parallel between two distributed controllers 212A and 212B. You may.
- each communication device constituting the distributed device system may be configured as a device that has a power supply, a memory I / F, and the like and can operate independently.
- each communication device 211 (211A to 211C) has a controller 220, a bridge 232, a hub 233, a bridge 234, a reader / writer 235, and an IC card 240.
- the controller 220 controls the communication device 211.
- the controller 220 has an MPU 221, a RAM 222, a SAM 223, a data memory 224, and the like.
- the MPU 221 is an example of a processor that controls the controller 220.
- the MPU 221 implements various processes by executing a program stored in the data memory 224 or the like.
- the controller 220 executes processes such as communication control, failure detection, communication failure detection, communication state monitoring, self-diagnosis, and log information collection by the MPU 221 executing a program.
- the controller 220 causes the MPU 221 to execute a program, thereby performing mutual authentication processing with the server-side communication control device 31, encryption processing of data transmitted from the client device 10 to the network NW, and client processing via the network NW. You may make it perform the decoding process etc. of the encrypted data transmitted to an apparatus.
- the controller 220 may request the IC card 240 to perform at least one of mutual authentication processing, encryption processing, and decryption processing.
- the RAM 222 is a random access memory.
- the RAM 222 functions as a working memory that holds work data.
- the SAM 223 is a serial access memory.
- the data memory 224 is a rewritable nonvolatile memory.
- the data memory 224 stores programs and setting information.
- the data memory 224 stores a white list showing a list of destinations that are allowed to communicate.
- the controller 220 refers to the white list stored in the data memory 224 and executes communication in the normal communication mode (first communication mode).
- the data memory 224 may store log information indicating the operating state of the communication device.
- the data memory 224 may store information indicating the amount of communication in the communication device.
- the data memory 224 executes self-diagnosis processing such as analysis of log data.
- the bridges 232 and 234 function as communication interfaces (communication units). Bridges 232 and 234 are connected to controller 220 via hub 233. The bridge 232 executes communication on the network NW side in the communication device 211. The bridge 232 realizes communication as the NW communication unit 32 shown in FIG. The bridge 232 supplies the data received from the network NW to the controller 220 via the hub 233. Further, the bridge 234 sends the data encrypted by the controller 220 or the IC card 240 to the network NW.
- the bridge 234 executes communication on the client device 10 side in the communication device 211.
- the bridge 234 realizes communication as the device communication unit 34 shown in FIG.
- the bridge 234 supplies data from the client device 10 to the controller 220 via the hub 233. Further, the bridge 234 sends the data obtained by decrypting the encrypted data from the network NW by the controller 220 or the IC card 240 to the client device 10.
- the reader/writer 235 and the IC card 240 correspond to the reader/writer 35 and the IC card 40 shown in FIG. 3 described above.
- the IC card 240 can be realized by having the same configuration as the IC card 40 shown in FIG. 4 described above. Further, the IC card 240 has a processing function similar to that of the IC card 40 shown in FIG. 5 described above, and functions as an example of an authentication unit in the communication control device 201.
- Each distributed controller 212 (212A, 212B) has a controller 251 and a memory 252, a hub 253 and an interface (I / F) 254, as shown in FIG.
- the controller 251 controls the distributed controller 212.
- the controller 251 has a processor and various memories. In the controller 251, various processes are realized by the processor executing the program. For example, the controller 251 controls the distribution of the communication load to the communication devices 211A to 211C by the processor executing the program.
- the memory 252 stores setting information and the like.
- the memory 252 stores a threshold value for determining the distribution of the communication load.
- the controller 251 determines a communication device to execute communication processing from a plurality of communication devices according to the communication load based on setting information such as a threshold value stored in the memory 252.
- the hub 253 is an interface for connecting the network NW or the client device 10 and the plurality of communication devices 211A to 211C.
- the hub 253 is controlled by the controller 251 as a communication device to be connected.
- Interface 254 is an interface for acquiring setting information and the like.
- the interface 254 is configured as a communication unit for communicating with the communication control management device 5.
- the interface 254 may be configured by a memory reader that reads information from a memory device such as a memory card that stores setting information such as a threshold value.
- the interface 254 may be an interface for connecting an external device that supplies setting information such as a threshold value.
- FIG. 16 is a flowchart for explaining an operation example of the distributed controller 212 (212A, 212B) in the communication system 200 having the configuration shown in FIGS. 14 and 15.
- the distribution controller 212 receives setting information input by the interface 254 or the like for distributed processing by the plurality of communication devices 211A to 211C (S201).
- the controller 251 of the distribution controller 212 (212A or 212B) performs the distributed processing by the plurality of communication devices 211A to 211C based on the input setting information.
- a threshold value for determining the above is set (step S202).
- the first threshold value is a determination reference value for the processing load of the entire communication control device 201 for determining whether or not the communication processing is performed by one communication device.
- the controller 251 of the distributed controller 212 executes communication processing by one communication device if the processing load of the entire communication control device 201 is less than the first threshold value, and by a plurality of communication devices if the processing load is equal to or more than the first threshold value. Communication processing shall be executed in a distributed manner.
- the second threshold value is a determination reference value for the processing load of the entire communication control device 201 for determining whether or not the communication processing is executed by the three communication devices. If the processing load of the entire communication control device 201 is equal to or greater than the second threshold value, the controller 252 of the distributed controller 212 distributes the communication processing among the three communication devices to execute the communication processing, and is equal to or greater than the first threshold value and less than the second threshold value. If so, it is assumed that the communication process is executed by dividing the two communication devices.
- the threshold as the setting information for carrying out the distributed processing may be set appropriately.
- the controllers 251 of the distributed controllers 212A and 212B monitor the processing load on the communication device based on the amount of communication and the like (step S203). For example, since the communication device 211 executes the decoding process on the information input from the network NW side, the controller 251 of the distributed controller 212A monitors the amount of data input from the network NW side as a processing load. Further, since the communication device 211 executes the encryption process on the information input from the client device 10, the controller 251 of the distributed controller 212B monitors the amount of data input from the client device 10 as a processing load.
- the controller 251 of the distributed controller 212 causes one communication device 211 to execute the communication process (step S205). For example, in a state where a plurality of communication devices are operating, the controller 251 executes communication with only one communication device when the load of the monitored process becomes less than the first threshold value, and performs communication. Transition the communication device that does not execute to the non-communication state (sleep state). As a result, when the processing load is less than the first threshold value, the distributed controller 212 executes the communication process with only one communication device and puts the other communication devices in the non-communication state, which wastes power consumption. Can be suppressed.
- step S204 determines whether the processing load is less than the second threshold value (step S206). ).
- step S206 determines whether the processing load is less than the second threshold value (step S206).
- step S207 the controller 251 distributes the processing load to the two communication devices to execute the communication processing.
- the controller 251 determines that the load of the process being monitored is equal to or more than the first threshold value and less than the second threshold value, and the second communication device The 211B is in a communicable state.
- the controller 251 distributes the information output from the hub 253 to the communication device 211A and the communication device 211B.
- the distributed controller 212 can perform the processing in a distributed manner by the two communication devices when the processing load is equal to or more than the first threshold value and less than the second threshold value.
- the distributed controller 212 can perform communication processing in a distributed manner among a plurality of communication devices whose processing is operated according to the load, and can prevent data delay and the like from occurring due to insufficient processing capacity.
- the controller 251 of the distributed controller 212 distributes the three communication devices to execute the communication processing (step S208). ..
- the controller 251 can communicate with the third communication device 211A when the load of the monitored process exceeds the second threshold value. State.
- the controller 251 distributes the information output from the hub 253 to the communication device 211A, the communication device 211B, and the communication device 211C.
- the distributed controller 212 can execute distributed processing among three communication devices (the maximum number of communication devices) when the processing load is equal to or higher than the second threshold. As a result, the distributed controller 212 can perform communication processing in a distributed manner among a plurality of communication devices whose processing is operated according to the load, and can prevent data delay and the like from occurring due to insufficient processing capacity.
- the above-mentioned operation example has been described on the assumption that a plurality of communication devices operate normally, but the distributed controller detects a failure such as a failure or a communication failure in each communication device and causes a failure.
- the above-mentioned distributed control may be performed on a communication device other than the communication device in which the above occurs. Further, when a failure occurs in all the communication devices, the distributed controller may operate any one of the communication devices in the pass-through mode to surely continue the data communication.
- the communication control device described above has a plurality of equivalent communication devices arranged in parallel, but a plurality of communication devices having different processing capabilities may be arranged in parallel. Further, one communication device may be used as the main processing device, and the other communication device may be used as the slave processing device to assist the processing of the main communication device. Furthermore, the processing content performed by the communication device may be performed separately.
- the communication system has a communication control device in which a plurality of communication devices are arranged in parallel between the network and the client device via a distributed controller.
- the distributed controller monitors the processing load on the communication control device and distributes and executes the communication processing by the number of communication devices according to the processing load.
- FIG. 17 is a diagram showing a configuration example of the communication system 300 and the communication control device 301 according to the third embodiment.
- a communication system 300 shown in FIG. 17 is obtained by replacing the client side communication control device 30 with a communication control device 301 in the system configuration shown in FIG.
- the server-side communication control device 31 arranged between the network NW and the server device 20 may have the same configuration as the communication control device 301.
- each device other than the communication control device 301 in the communication system 300 can be realized with the same configuration as the device shown in FIG. 1, and therefore detailed description thereof will be omitted.
- the communication control device 301 includes a power supply 316, a memory I/F 317, a controller 320, a bridge 332, a hub 333, a bridge 334, a reader/writer 335, an IC card 340, and the like.
- the controller 320 controls the communication device 211.
- the controller 320 has an MPU 321, a RAM 322, a SAM 323, a data memory 324, and the like.
- the MPU 321 is an example of a processor that controls the controller 320.
- the MPU 321 realizes various processes by executing a program stored in the data memory 324 or the like.
- the controller 320 executes processes such as communication control, failure detection, communication failure detection, communication amount analysis, self-diagnosis, log information storage, and log information transmission by the MPU 321 executing a program.
- the controller 320 causes the MPU 321 to execute the program, thereby performing mutual authentication processing with the server-side communication control device 31, encryption processing of data transmitted from the client device 10 to the network NW, and client processing via the network NW. Decryption processing of the encrypted data transmitted to the device 10 may be performed. Further, the controller 320 may request the IC card 340 to perform at least one of mutual authentication processing, encryption processing, and decryption processing.
- the RAM 322 is a random access memory.
- the RAM 322 functions as a working memory that holds work data.
- the SAM 323 is a serial access memory.
- the data memory 324 is a rewritable nonvolatile memory.
- the data memory 324 stores programs and setting information. For example, the data memory 324 stores a white list showing a list of destinations that are allowed to communicate.
- the controller 320 executes communication in the normal communication mode (first communication mode) with reference to the white list stored in the data memory 324. Further, the data memory 324 may store log information indicating the operating state of the communication control device. Further, the data memory 324 stores the analysis information of the communication amount in the communication control device by the controller 320.
- the bridges 332 and 334 function as a communication interface (communication unit).
- the bridges 332 and 334 are connected to the controller 320 via the hub 333.
- the bridge 332 executes communication on the network NW side in the communication control device 301.
- the bridge 332 realizes communication as the NW communication unit 32 shown in FIG.
- the bridge 332 supplies the data received from the network NW to the controller 320 via the hub 333. Further, the bridge 334 sends the data encrypted by the controller 320 or the IC card 340 to the network NW.
- the bridge 334 executes communication on the client device 10 side in the communication control device 301.
- the bridge 334 realizes communication as the device communication unit 34 shown in FIG.
- the bridge 334 supplies the data from the client device 10 to the controller 320 via the hub 333. Further, the bridge 334 sends the data obtained by decrypting the encrypted data from the network NW with the controller 320 or the IC card 340 to the client device 10.
- the reader/writer 335 and the IC card 340 correspond to the reader/writer 35 and the IC card 40 shown in FIG. 3 described above.
- the IC card 340 can be realized by having the same configuration as the IC card 40 shown in FIG. 4 described above. Further, the IC card 340 has the same processing function as the IC card 40 shown in FIG. 5 described above, and functions as an example of the authentication unit in the communication control device 301.
- the power source 316 is connected to an external power source and supplies the power from the external power source to each unit in the communication control device 301.
- the memory I / F 317 is an interface for setting a memory device 318 such as a memory card.
- a memory device 318 that stores setting information for the communication control device 301 is set in the memory I / F 317.
- FIG. 18 is a sequence for explaining a first operation example in the communication system 300 shown in FIG.
- the communication control device 301 accumulates log information including the amount of communication in normal operation.
- the controller 320 of the communication control device 301 monitors the data passing through the bridges 332 and 334 as the communication interface to store the information indicating the communication amount of the communication control device 301 in the data memory 324.
- the controller 320 of the communication control device 301 analyzes the information indicating the communication amount accumulated as log information in the data memory 324, and stores the analysis information of the communication amount as the analysis result in the data memory 324 (step S301). For example, the controller 320 analyzes the communication amount in a predetermined cycle and records the analysis information of the communication amount in the data memory 324.
- the communication amount analysis information may indicate, for example, the communication amount per hour, the communication amount for each time period and the increasing/decreasing trend of the communication amount, or the communication amount
- the information may be information indicating a time period in which the traffic amount is less than the predetermined threshold value or a communication amount is minimum.
- the communication amount analysis information may be information for determining the time at which the communication control device 301 executes the self-diagnosis.
- the controller 320 of the communication control device 301 transmits the analysis information of the communication amount stored in the data memory 324 to the communication control management device (device management server) 5 (step S302).
- the controller 320 may transmit the analysis information of the communication amount at a predetermined timing, or may transmit the analysis information in response to the request from the communication control management device 5.
- the controller 320 self-determines the time zone in which the communication amount is low in the communication control management device 5, and transmits the analysis information of the communication amount to the communication control management device 5 in the time zone when it is determined that the communication amount is low. You may.
- the communication amount analysis information transmitted from the communication control device 301 is acquired by the communication control management device 5 (step S303).
- the control unit 61 of the communication control management device 5 stores the analysis information of the communication amount received by the NW communication unit 60 in the storage unit 66 in association with the identification information indicating the communication control device 301 of the transmission source.
- the control unit 61 determines the time or time zone in which the communication control device 301 should execute the self-diagnosis based on the analysis information of the received communication amount (step S304).
- the control unit 301 specifies the time required for the self-diagnosis process as the self-diagnosis execution time (scheduled execution time) in the time zone when the communication volume is less than the predetermined threshold value based on the communication volume analysis information. To do.
- the time at which the self-diagnosis process can be secured is set to the time when the self-diagnosis is performed (scheduled It may be specified as time).
- the control unit 61 After determining the implementation time of the self-diagnosis, when the implementation time of the self-diagnosis arrives, the control unit 61 transmits a life-and-death confirmation query to the communication control device 301 (step S305).
- the life-and-death confirmation query requests a response regarding whether or not it is operating normally.
- the controller 320 of the communication control device 301 receives the life / death confirmation query from the communication control management device 5 (step S306), the controller 320 transmits a response indicating that it is normal if it is operating normally (step S307). Further, the communication control device 301 may respond to the life-and-death confirmation query with the date and time when the previous self-diagnosis was performed.
- the control unit 61 of the communication control management device 5 determines whether or not to perform the self-diagnosis based on the response from the communication control device 301 (step S308). For example, the control unit 61 causes the communication control device 301 to perform the self-diagnosis when there is no response from the communication control device or when a predetermined period or more has passed from the date and time when the previous self-diagnosis was performed. to decide. In addition, the control unit 61 may perform self-diagnosis regardless of the response content from the communication control device 301. When performing the self-diagnosis, the control unit 61 of the communication control management device 5 requests the communication control device 301 to perform the self-diagnosis (step S309).
- the controller 320 of the communication control management device 5 determines whether or not the self-diagnosis is possible at present (step S311). For example, the controller 320 performs self-diagnosis if the current communication amount is less than a predetermined threshold.
- the system according to the third embodiment controls the communication control device and the entire communication system to execute the self-diagnosis with as little load as possible. Therefore, it is determined that the controller of the communication control device does not perform (postpone) the self-diagnosis when the actual communication volume is large.
- the controller 320 When carrying out the self-diagnosis (step S311, YES), the controller 320 carries out the self-diagnosis (step S312) and transmits information indicating the execution result of the self-diagnosis to the communication control management device 5. In this case, the information indicating the execution result of the self-diagnosis is transmitted from the communication control device 301 and is acquired by the communication control management device 5 (step S313).
- the controller 320 transmits a notification indicating that the self-diagnosis is not performed to the communication control management device 5 (step S314). In this case, the notification indicating that the self-diagnosis is not performed is acquired by the communication control management device 5 as a response to the self-diagnosis execution request (step S315).
- the control unit 61 of the communication control management device 5 saves the self-diagnosis result in the storage unit 66 (step 316). For example, when the self-diagnosis is performed by the communication control device 30, the control unit 61 stores the information indicating the execution result of the self-diagnosis in the storage unit 66 in association with the identification information of the communication control device 301 together with the implementation date and time. .. When the communication control device 30 has not performed the self-diagnosis, the control unit 61 stores information indicating that the self-diagnosis cannot be performed in the storage unit 66 in association with the identification information of the communication control device 301. ..
- control unit 61 of the communication control management device 5 verifies whether or not there is an abnormality in the acquired execution result of the self-diagnosis.
- the control unit 61 notifies an alert indicating that the communication control device 301 or the communication system 300 has an abnormality (step S318).
- the control unit 61 may notify that there is an abnormality in the communication control device 301 or the communication system 300.
- the communication control management device acquires the communication amount analysis information in the communication control device, and the communication control management device performs the communication control based on the communication amount analysis information.
- the communication control management device can cause the communication control device to perform the self-diagnosis at a time when the communication amount is small and the self-diagnosis does not affect the normal communication processing.
- FIG. 19 is a sequence for explaining a second operation example in the communication system 300 shown in FIG.
- the controller 320 of the communication control device 301 analyzes the information indicating the communication amount to be stored as log information in the data memory 324, and analyzes the analysis information of the communication amount as the analysis result, as in the first operation example described above. It is stored in 324 (step S321).
- the controller 320 of the communication control device 301 determines the scheduled execution time at which the self-diagnosis is scheduled to be executed based on the analysis information of the communication amount stored in the data memory 324 at a predetermined timing (step S322). For example, the controller 320 specifies as a self-diagnosis execution time (scheduled execution time) a time during which the time required for the self-diagnosis process can be secured in the time zone when the communication volume is less than a predetermined threshold value based on the communication volume analysis information. ..
- the controller 320 When the scheduled execution time of the self-diagnosis is determined, the controller 320 notifies the communication control management device 5 of the scheduled execution time of the self-diagnosis (S323). In this case, the control unit 61 of the communication control management device 5 stores the information indicating the scheduled execution time of the self-diagnosis notified from the communication control device 301 in association with the identification information of the communication control device 301. You may. However, the controller 320 does not have to notify the communication control management device 5 of the scheduled execution time of the self-diagnosis.
- the control unit 61 determines whether or not the self-diagnosis can be performed at the scheduled time for performing the self-diagnosis (step S324). For example, the controller 320 performs a self-diagnosis if the current traffic is less than a predetermined threshold.
- the controller 320 carries out the self-diagnosis (step S325) and transmits information indicating the execution result of the self-diagnosis to the communication control management device 5.
- the information indicating the execution result of the self-diagnosis is transmitted from the communication control device 301 and is acquired by the communication control management device 5 (step S326).
- step S324 the controller 320 transmits a notification indicating that the self-diagnosis is not performed to the communication control management device 5 (step S327).
- the notification indicating that the self-diagnosis is not executed is acquired by the communication control management device 5 as a response to the self-diagnosis execution request (step S328).
- the control unit 61 of the communication control management device 5 saves the self-diagnosis result in the storage unit 66 (step 329). Further, when the self-diagnosis is not performed by the communication control device 30, the control unit 61 stores the information indicating that the self-diagnosis could not be performed in the storage unit 66 in association with the identification information of the communication control device 301. ..
- control unit 61 of the communication control management device 5 verifies whether or not there is an abnormality in the acquired execution result of the self-diagnosis (step S330).
- the control unit 61 notifies an alert indicating that the communication control device 301 or the communication system 300 is abnormal (step S331). ..
- the communication control device itself sets the scheduled time for performing the self-diagnosis based on the analysis information of the communication amount.
- the communication control device can be planned to perform the self-diagnosis at a time when the amount of communication is small and the self-diagnosis does not affect the normal communication processing.
- the communication control management device can efficiently perform self-diagnosis for confirming the state of the communication control device and detecting a failure or communication failure at an early stage without imposing a load on the communication system. ..
- the communication system according to the fourth embodiment has the same configuration as the communication system 300 according to the third embodiment described above. Therefore, the fourth embodiment will be described as an example of application to the communication system 300 shown in FIG. 17 described in the third embodiment.
- FIG. 20 is a sequence for explaining a first operation example in the communication system 300 according to the fourth embodiment.
- the communication control device 301 stores log information indicating an operating state in the data memory 324.
- the log information stored in the data memory 324 is information indicating the operation history of the communication control device 301.
- information that should be urgently notified to the communication control management device 5 such as unauthorized access may be stored as log information, but is immediately notified to the communication control management device 5.
- Information indicating the communication volume in normal operation may be stored in the data memory 324 as log information.
- the controller 320 of the communication control device 301 monitors the data passing through the bridges 332 and 334 as the communication interface to store the information indicating the communication amount of the communication control device 301 in the data memory 324.
- the controller 320 of the communication control device 301 analyzes the information indicating the communication amount accumulated as log information in the data memory 324, and stores the analysis information of the communication amount as the analysis result in the data memory 324 (step S401). For example, the controller 320 analyzes the communication amount in a predetermined cycle and records the analysis information of the communication amount in the data memory 324.
- the communication amount analysis information may indicate, for example, the communication amount per hour, the communication amount for each time period and the increasing/decreasing trend of the communication amount, or the communication amount
- the information may be information indicating a time period in which the traffic amount is less than the predetermined threshold value or a communication amount is minimum.
- the communication amount analysis information may be information for determining the time when the communication control device 301 transmits the log information to the communication control management device (device management server) 5.
- the controller 320 of the communication control device 301 transmits the analysis information of the communication amount stored in the data memory 324 to the communication control management device (device management server) 5 (step S402).
- the controller 320 may transmit the analysis information of the communication amount at a predetermined timing, or may transmit the analysis information in response to the request from the communication control management device 5.
- the controller 320 self-determines the time zone in which the communication amount is low in the communication control management device 5, and transmits the analysis information of the communication amount to the communication control management device 5 in the time zone when it is determined that the communication amount is low. You may.
- the communication amount analysis information transmitted from the communication control device 301 is acquired by the communication control management device 5 (step S403).
- the control unit 61 of the communication control management device 5 stores the analysis information of the communication amount received by the NW communication unit 60 in the storage unit 66 in association with the identification information indicating the communication control device 301 of the transmission source (step S404).
- the control unit 61 determines a schedule (log collection schedule) at which each communication control device 301 transmits log information, based on the analysis information of the communication amount from each communication control device 301 stored in the storage unit 66 ( Step S405).
- control unit 301 causes each communication control device 301 to output log information based on the analysis information of the communication amount from each communication control device in the communication system so that the communication amount in the entire network NW becomes less than a predetermined threshold value. Schedule the time (time zone) that can be sent.
- the control unit 61 notifies each communication control device 301 of the time (transmission time) for transmitting the log information (step S406).
- the controller 320 of the communication control device 301 receives the notification of the log information transmission time from the communication control management device 5 (step S407), the controller 320 stores the log information transmission time in the data memory 324 (step S408).
- the controller 320 transmits the log information accumulated in the data memory 324 to the communication control management device 5 at the transmission time of the log information instructed by the communication control management device 5 (step S409).
- the log information transmitted from the communication control device 301 is transmitted to the communication control management device 5 via the network NW and received by the communication control management device 5 (step S410).
- the control unit 61 of the communication control management device 5 saves the log information received from the communication control device 301 in the storage unit 66 (step 411). For example, the control unit 61 stores the received log information together with the implementation date and time in the storage unit 66 in association with the identification information of the communication control device 301.
- the communication control device connected to the client device transmits the analysis information of its own communication amount to the communication control management device, and the communication control management device is in the communication system.
- the time when each communication control device transmits the log information is scheduled based on the analysis information of the communication amount from each communication control device.
- each communication control device 301 determines the time when the log information is transmitted based on the analysis information of the communication amount, and the communication control management device considers the communication amount in each communication control device of the entire communication system.
- Each communication control device can decide to send log information. As a result, it is possible to control the time at which each communication control device sends out log information in consideration of not only the individual communication control devices but also the load expected to occur in the entire network.
- FIG. 21 is a sequence for explaining a second operation example in the communication system 300 according to the fourth embodiment.
- the controller 320 of the communication control device 301 analyzes the information indicating the communication amount to be accumulated as log information in the data memory 324, and analyzes the communication amount analysis information as the analysis result, as in the first operation example described above.
- the data is stored in the data memory 324 (step S421).
- the controller 320 of the communication control device 301 selects a candidate for the transmission time at which the communication control device 301 transmits the log information, based on the analysis information of the communication amount stored in the data memory 324 (step S422).
- the candidate for the transmission time may be one, may be a plurality, or may be indicated by a time zone.
- the controller 320 selects a time at which the communication control device 301 can transmit the log information as a candidate for the transmission time, based on the analysis information of the communication amount at the communication control device, in the time zone with the smallest communication amount. Further, the control unit 301 selects a time (transmission time) at which the communication control device 301 can transmit log information from a time zone in which the communication volume is less than a predetermined threshold value, based on the analysis information of the communication volume in the communication control device. You may.
- the controller 3210 transmits the selected log information transmission time candidate to the communication control management device 5 (step S424).
- the communication control management device 5 acquires the candidate of the transmission time of the log information selected by the communication control device 301.
- the control unit 61 of the communication control management device 5 stores the information indicating the transmission time candidates of the log information received by the NW communication unit 60 in the storage unit 66 in association with the identification information indicating the communication control device 301 of the transmission source. (Step S425). As a result, the storage unit 66 stores the information indicating the candidates for the transmission time of the log information from each communication control device 301 in the communication system.
- the control unit 61 of the communication control management device 5 schedules the time when each communication control device 31 of the entire system sends the logo information based on the candidate of the transmission time of the log information of each communication control device 301 stored in the storage unit 66. (Schedule of log collection) is created (step S426). For example, the control unit 301 schedules candidates for transmission time of log information from each communication control device so that the communication volume in the entire network NW is less than a predetermined threshold value.
- the control unit 61 When the schedule of the transmission time of the log information is created, the control unit 61 notifies each communication control device 301 of the transmission time for transmitting the log information (step S427).
- the controller 320 of the communication control device 301 receives the notification of the log information transmission time from the communication control management device 5 (step S428), the controller 320 stores the log information transmission time in the data memory 324 (step S429).
- the controller 320 transmits the log information accumulated in the data memory 324 to the communication control management device 5 at the transmission time of the log information instructed by the communication control management device 5 (step S430).
- the log information transmitted from the communication control device 301 is transmitted to the communication control management device 5 via the network NW and received by the communication control management device 5 (step S431).
- the control unit 61 of the communication control management device 5 saves the log information received from the communication control device 301 in the storage unit 66 (step 432). For example, the control unit 61 stores the received log information together with the implementation date and time in the storage unit 66 in association with the identification information of the communication control device 301.
- the communication control device 301 selects a candidate for the transmission time of the log information based on the analysis information of its own communication amount.
- the communication control management device 5 schedules candidates for transmission time of log information acquired from each communication control device 301 in the communication system 300 so as to reduce the load on the network NW.
- each communication control device 301 can reduce the load on the entire network when transmitting log information to the communication control management device. Further, since each communication control device selects a candidate for the transmission time of the log information, the processing load on the communication control management device 5 can be reduced. As a result, for example, even in a communication system in which the number of communication control devices is large, the time at which each communication control device transmits log information can be efficiently controlled.
- FIG. 22 is a sequence for explaining a third operation example in the communication system 300 according to the fourth embodiment.
- the controller 320 of the communication control device 301 analyzes the information indicating the communication amount to be accumulated as log information in the data memory 324, and analyzes the communication amount analysis information as the analysis result, as in the first operation example described above.
- the data is stored in the data memory 324 (step S441).
- the controller 320 of the communication control device 301 determines the scheduled transmission time at which the communication control device 301 transmits the log information based on the analysis information of the communication amount stored in the data memory 324 (step S442). For example, the controller 320 selects, as the scheduled transmission time, the time when the communication control device 301 can transmit the log information in the time zone when the communication amount is the least, based on the analysis information of the communication amount in the communication control device.
- the controller 320 estimates the degree of network congestion at the scheduled transmission time of the selected log information (step S443). For example, the controller 320 estimates the network congestion degree from the time from the transmission of the inquiry for confirming the network congestion degree to the communication control management apparatus 5 to the reception of the response from the communication control management apparatus 5.
- the inquiry transmitted to the communication control management device 5 is data for estimating the congestion of the network, the inquiry has a small size so as not to load the network itself.
- step S444, NO the controller 320 stops transmission of log information.
- the controller 320 selects the scheduled transmission time for transmitting the logo information again from the analysis information of the communication amount.
- step S444 determines that the log information can be transmitted, and controls the communication of the log information stored in the data memory 324. It is transmitted to the management device 5 (step S445).
- the log information transmitted from the communication control device 301 is transmitted to the communication control management device 5 via the network NW and received by the communication control management device 5 (step S446).
- the control unit 61 of the communication control management device 5 saves the log information received from the communication control device 301 in the storage unit 66 (step 457).
- the communication control device sets the scheduled transmission time of log information based on the analysis information of its own communication volume.
- the communication control device estimates the network congestion degree at the scheduled transmission time set by the time, and if the network congestion degree is less than the threshold value, the communication control device shall transmit the log information to the communication control management device.
- each communication control device can transmit log information to the communication control management device after confirming the actual network congestion degree at the scheduled transmission time set by the individual communication control device.
- Log information can be collected.
Landscapes
- Engineering & Computer Science (AREA)
- Computer Security & Cryptography (AREA)
- Computer Networks & Wireless Communication (AREA)
- Signal Processing (AREA)
- General Engineering & Computer Science (AREA)
- Computer Hardware Design (AREA)
- Computing Systems (AREA)
- Theoretical Computer Science (AREA)
- Health & Medical Sciences (AREA)
- Bioethics (AREA)
- General Health & Medical Sciences (AREA)
- Software Systems (AREA)
- Physics & Mathematics (AREA)
- General Physics & Mathematics (AREA)
- Data Exchanges In Wide-Area Networks (AREA)
Priority Applications (3)
| Application Number | Priority Date | Filing Date | Title |
|---|---|---|---|
| EP20765990.5A EP3913851B1 (en) | 2019-03-04 | 2020-02-28 | Communication control device and communication system |
| SG11202109223VA SG11202109223VA (en) | 2019-03-04 | 2020-02-28 | Communication control device and communication system |
| US17/446,637 US20210400040A1 (en) | 2019-03-04 | 2021-09-01 | Communication control device and communication system |
Applications Claiming Priority (2)
| Application Number | Priority Date | Filing Date | Title |
|---|---|---|---|
| JP2019-038377 | 2019-03-04 | ||
| JP2019038377A JP7191726B2 (ja) | 2019-03-04 | 2019-03-04 | 通信制御装置および通信システム |
Related Child Applications (1)
| Application Number | Title | Priority Date | Filing Date |
|---|---|---|---|
| US17/446,637 Continuation US20210400040A1 (en) | 2019-03-04 | 2021-09-01 | Communication control device and communication system |
Publications (1)
| Publication Number | Publication Date |
|---|---|
| WO2020179707A1 true WO2020179707A1 (ja) | 2020-09-10 |
Family
ID=72338709
Family Applications (1)
| Application Number | Title | Priority Date | Filing Date |
|---|---|---|---|
| PCT/JP2020/008467 Ceased WO2020179707A1 (ja) | 2019-03-04 | 2020-02-28 | 通信制御装置および通信システム |
Country Status (5)
| Country | Link |
|---|---|
| US (1) | US20210400040A1 (enExample) |
| EP (1) | EP3913851B1 (enExample) |
| JP (1) | JP7191726B2 (enExample) |
| SG (1) | SG11202109223VA (enExample) |
| WO (1) | WO2020179707A1 (enExample) |
Cited By (1)
| Publication number | Priority date | Publication date | Assignee | Title |
|---|---|---|---|---|
| WO2023176431A1 (ja) * | 2022-03-15 | 2023-09-21 | 株式会社 東芝 | 情報処理装置および通信システム |
Families Citing this family (4)
| Publication number | Priority date | Publication date | Assignee | Title |
|---|---|---|---|---|
| US12052282B2 (en) * | 2021-08-25 | 2024-07-30 | Paypal, Inc. | Automatic detection of proxy-based phishing sites |
| US11843619B1 (en) | 2022-10-07 | 2023-12-12 | Uab 360 It | Stateless system to enable data breach notification |
| WO2025090020A1 (en) * | 2023-10-25 | 2025-05-01 | Etymology Pte. Ltd. | Security system and method for ev charger |
| WO2025090019A1 (en) * | 2023-10-25 | 2025-05-01 | Etymology Pte. Ltd. | Cctv security system and method therefor |
Citations (4)
| Publication number | Priority date | Publication date | Assignee | Title |
|---|---|---|---|---|
| JP2005223892A (ja) * | 2004-01-09 | 2005-08-18 | Ricoh Co Ltd | デジタル証明書無効化方法、デジタル証明書無効化装置、デジタル証明書無効化システム、プログラム及び記録媒体 |
| JP2009117887A (ja) | 2007-11-01 | 2009-05-28 | Meidensha Corp | 電子認証装置、電子認証システム、電子認証方法およびこの方法のプログラム |
| JP2013016041A (ja) * | 2011-07-04 | 2013-01-24 | Fujitsu Ltd | 振分制御装置、振分制御方法および振分制御プログラム |
| JP2018037888A (ja) * | 2016-08-31 | 2018-03-08 | 株式会社東芝 | 通信装置、通信方法および通信システム |
Family Cites Families (30)
| Publication number | Priority date | Publication date | Assignee | Title |
|---|---|---|---|---|
| JPS63146630A (ja) * | 1986-12-10 | 1988-06-18 | Fujitsu Ltd | 暗号装置間の公開鍵交換方式 |
| JP3950596B2 (ja) | 1999-10-22 | 2007-08-01 | 株式会社日立製作所 | Isdn暗号アダプタおよびisdn暗号通信方法 |
| EP1299989A2 (en) * | 2000-07-07 | 2003-04-09 | Science Applications International Corporation | A system or method for calling a vanity number using speech recognition |
| DE10107883B4 (de) * | 2001-02-19 | 2006-02-09 | Deutsche Post Ag | Verfahren zur Übertragung von Daten, Proxy-Server und Datenübertragungssystem |
| US7441119B2 (en) * | 2001-12-05 | 2008-10-21 | International Business Machines Corporation | Offload processing for secure data transfer |
| US20050193103A1 (en) * | 2002-06-18 | 2005-09-01 | John Drabik | Method and apparatus for automatic configuration and management of a virtual private network |
| US7069438B2 (en) * | 2002-08-19 | 2006-06-27 | Sowl Associates, Inc. | Establishing authenticated network connections |
| JP2004328563A (ja) | 2003-04-28 | 2004-11-18 | Hitachi Ltd | 暗号通信装置および暗号通信システム |
| US7590074B1 (en) * | 2004-12-02 | 2009-09-15 | Nortel Networks Limited | Method and apparatus for obtaining routing information on demand in a virtual private network |
| US8250214B2 (en) * | 2004-12-20 | 2012-08-21 | Vmware, Inc. | System, method and computer program product for communicating with a private network |
| US7930365B2 (en) * | 2005-02-16 | 2011-04-19 | Cisco Technology, Inc. | Method and apparatus to modify network identifiers at data servers |
| JP2007049455A (ja) * | 2005-08-10 | 2007-02-22 | Toshiba Corp | 暗号鍵管理サーバ、暗号鍵管理方法および暗号鍵管理プログラム |
| JP2008028867A (ja) * | 2006-07-24 | 2008-02-07 | Nomura Research Institute Ltd | 通信代理システムおよび通信代理装置 |
| US8886934B2 (en) * | 2006-07-26 | 2014-11-11 | Cisco Technology, Inc. | Authorizing physical access-links for secure network connections |
| US9392462B2 (en) * | 2009-01-28 | 2016-07-12 | Headwater Partners I Llc | Mobile end-user device with agent limiting wireless data communication for specified background applications based on a stored policy |
| US8892720B2 (en) * | 2009-02-12 | 2014-11-18 | Arcsoft, Inc. | System and method for network optimization through predictive downloading |
| US9479480B2 (en) * | 2010-01-29 | 2016-10-25 | Citrix Systems, Inc. | Systems and methods of using SSL pools for WAN acceleration |
| US8700892B2 (en) * | 2010-03-19 | 2014-04-15 | F5 Networks, Inc. | Proxy SSL authentication in split SSL for client-side proxy agent resources with content insertion |
| CN103731407B (zh) | 2012-10-12 | 2017-08-11 | 华为技术有限公司 | Ike报文协商的方法及系统 |
| US9106557B2 (en) * | 2013-03-13 | 2015-08-11 | Comcast Cable Communications, Llc | Scheduled transmission of data |
| US9674316B2 (en) * | 2014-03-27 | 2017-06-06 | Pismo Labs Technology Limited | Methods and systems for identifying data sessions at a VPN gateway |
| US10623285B1 (en) * | 2014-05-09 | 2020-04-14 | Amazon Technologies, Inc. | Multi-mode health monitoring service |
| US9680918B2 (en) * | 2014-06-30 | 2017-06-13 | Fortinet, Inc. | Socket application program interface (API) for efficient data transactions |
| US9722906B2 (en) * | 2015-01-23 | 2017-08-01 | Cisco Technology, Inc. | Information reporting for anomaly detection |
| US9686081B2 (en) * | 2015-07-01 | 2017-06-20 | Cisco Technology, Inc. | Detecting compromised certificate authority |
| US20170054770A1 (en) * | 2015-08-23 | 2017-02-23 | Tornaditech Llc | Multimedia teleconference streaming architecture between heterogeneous computer systems |
| JP2017135461A (ja) | 2016-01-25 | 2017-08-03 | 三菱電機株式会社 | 加入者終端装置、局側終端装置、光信号伝送装置および通信システム |
| US10469268B2 (en) * | 2016-05-06 | 2019-11-05 | Pacific Star Communications, Inc. | Unified encryption configuration management and setup system |
| EP3364607A1 (en) * | 2017-02-16 | 2018-08-22 | Telia Company AB | Methods and apparatuses for providing security in a roaming environment |
| US10721097B2 (en) * | 2018-04-24 | 2020-07-21 | Microsoft Technology Licensing, Llc | Dynamic scaling of virtual private network connections |
-
2019
- 2019-03-04 JP JP2019038377A patent/JP7191726B2/ja active Active
-
2020
- 2020-02-28 EP EP20765990.5A patent/EP3913851B1/en active Active
- 2020-02-28 SG SG11202109223VA patent/SG11202109223VA/en unknown
- 2020-02-28 WO PCT/JP2020/008467 patent/WO2020179707A1/ja not_active Ceased
-
2021
- 2021-09-01 US US17/446,637 patent/US20210400040A1/en not_active Abandoned
Patent Citations (4)
| Publication number | Priority date | Publication date | Assignee | Title |
|---|---|---|---|---|
| JP2005223892A (ja) * | 2004-01-09 | 2005-08-18 | Ricoh Co Ltd | デジタル証明書無効化方法、デジタル証明書無効化装置、デジタル証明書無効化システム、プログラム及び記録媒体 |
| JP2009117887A (ja) | 2007-11-01 | 2009-05-28 | Meidensha Corp | 電子認証装置、電子認証システム、電子認証方法およびこの方法のプログラム |
| JP2013016041A (ja) * | 2011-07-04 | 2013-01-24 | Fujitsu Ltd | 振分制御装置、振分制御方法および振分制御プログラム |
| JP2018037888A (ja) * | 2016-08-31 | 2018-03-08 | 株式会社東芝 | 通信装置、通信方法および通信システム |
Non-Patent Citations (2)
| Title |
|---|
| KITAMIKADO, YASUHIRO; OYA, TAKAFUMI; TAKAHASHI, RYO; ICHIKAWA, YASUYUKI; MIYOSHI, JUN: "B-6-27 IPsecGW Redundancy Architecture Using MOBIKE", LECTURE PROCEEDINGS 2 OF THE 2009 COMMUNICATION SOCIETY CONFERENCE OF IEICE, 1 September 2009 (2009-09-01), JP, pages 27, XP009529611 * |
| See also references of EP3913851A4 |
Cited By (1)
| Publication number | Priority date | Publication date | Assignee | Title |
|---|---|---|---|---|
| WO2023176431A1 (ja) * | 2022-03-15 | 2023-09-21 | 株式会社 東芝 | 情報処理装置および通信システム |
Also Published As
| Publication number | Publication date |
|---|---|
| JP7191726B2 (ja) | 2022-12-19 |
| SG11202109223VA (en) | 2021-09-29 |
| EP3913851A1 (en) | 2021-11-24 |
| EP3913851A4 (en) | 2022-10-12 |
| US20210400040A1 (en) | 2021-12-23 |
| JP2020145497A (ja) | 2020-09-10 |
| EP3913851B1 (en) | 2024-02-28 |
Similar Documents
| Publication | Publication Date | Title |
|---|---|---|
| US20220385655A1 (en) | Communication control system and communication control device | |
| WO2020179707A1 (ja) | 通信制御装置および通信システム | |
| JP7278806B2 (ja) | 通信制御装置および通信システム | |
| JP2022040299A (ja) | クライアント側通信制御装置 | |
| JP7278807B2 (ja) | 通信制御装置および通信システム | |
| JP7458470B2 (ja) | 通信制御装置 | |
| JP7191727B2 (ja) | 通信制御装置および通信システム | |
| US20210345106A1 (en) | Communication control device and communication control system | |
| EP3866033B1 (en) | Information processing device and information processing system | |
| JP7163206B2 (ja) | 通信制御装置 | |
| US20250344081A1 (en) | Communication system, information processing apparatus, and monitoring method | |
| US20240380760A1 (en) | Information processing apparatus and communication system | |
| JP2025037147A (ja) | 情報処理装置および通信システム |
Legal Events
| Date | Code | Title | Description |
|---|---|---|---|
| 121 | Ep: the epo has been informed by wipo that ep was designated in this application |
Ref document number: 20765990 Country of ref document: EP Kind code of ref document: A1 |
|
| ENP | Entry into the national phase |
Ref document number: 2020765990 Country of ref document: EP Effective date: 20210820 |
|
| NENP | Non-entry into the national phase |
Ref country code: DE |