WO2019012952A1 - 電子制御装置、プログラム改ざん検知方法、プログラム改ざん検知方法のプログラム、およびコンピュータ読み出し可能持続的有形記録媒体 - Google Patents
電子制御装置、プログラム改ざん検知方法、プログラム改ざん検知方法のプログラム、およびコンピュータ読み出し可能持続的有形記録媒体 Download PDFInfo
- Publication number
- WO2019012952A1 WO2019012952A1 PCT/JP2018/023808 JP2018023808W WO2019012952A1 WO 2019012952 A1 WO2019012952 A1 WO 2019012952A1 JP 2018023808 W JP2018023808 W JP 2018023808W WO 2019012952 A1 WO2019012952 A1 WO 2019012952A1
- Authority
- WO
- WIPO (PCT)
- Prior art keywords
- program
- authenticator
- partial
- electronic control
- verification
- Prior art date
- Legal status (The legal status is an assumption and is not a legal conclusion. Google has not performed a legal analysis and makes no representation as to the accuracy of the status listed.)
- Ceased
Links
Images
Classifications
-
- H—ELECTRICITY
- H04—ELECTRIC COMMUNICATION TECHNIQUE
- H04L—TRANSMISSION OF DIGITAL INFORMATION, e.g. TELEGRAPHIC COMMUNICATION
- H04L9/00—Cryptographic mechanisms or cryptographic arrangements for secret or secure communications; Network security protocols
- H04L9/32—Cryptographic mechanisms or cryptographic arrangements for secret or secure communications; Network security protocols including means for verifying the identity or authority of a user of the system or for message authentication, e.g. authorization, entity authentication, data integrity or data verification, non-repudiation, key authentication or verification of credentials
- H04L9/3236—Cryptographic mechanisms or cryptographic arrangements for secret or secure communications; Network security protocols including means for verifying the identity or authority of a user of the system or for message authentication, e.g. authorization, entity authentication, data integrity or data verification, non-repudiation, key authentication or verification of credentials using cryptographic hash functions
- H04L9/3242—Cryptographic mechanisms or cryptographic arrangements for secret or secure communications; Network security protocols including means for verifying the identity or authority of a user of the system or for message authentication, e.g. authorization, entity authentication, data integrity or data verification, non-repudiation, key authentication or verification of credentials using cryptographic hash functions involving keyed hash functions, e.g. message authentication codes [MACs], CBC-MAC or HMAC
-
- G—PHYSICS
- G06—COMPUTING OR CALCULATING; COUNTING
- G06F—ELECTRIC DIGITAL DATA PROCESSING
- G06F21/00—Security arrangements for protecting computers, components thereof, programs or data against unauthorised activity
- G06F21/60—Protecting data
- G06F21/64—Protecting data integrity, e.g. using checksums, certificates or signatures
-
- G—PHYSICS
- G06—COMPUTING OR CALCULATING; COUNTING
- G06F—ELECTRIC DIGITAL DATA PROCESSING
- G06F1/00—Details not covered by groups G06F3/00 - G06F13/00 and G06F21/00
- G06F1/26—Power supply means, e.g. regulation thereof
- G06F1/32—Means for saving power
- G06F1/3203—Power management, i.e. event-based initiation of a power-saving mode
-
- G—PHYSICS
- G06—COMPUTING OR CALCULATING; COUNTING
- G06F—ELECTRIC DIGITAL DATA PROCESSING
- G06F21/00—Security arrangements for protecting computers, components thereof, programs or data against unauthorised activity
- G06F21/30—Authentication, i.e. establishing the identity or authorisation of security principals
- G06F21/44—Program or device authentication
-
- G—PHYSICS
- G06—COMPUTING OR CALCULATING; COUNTING
- G06F—ELECTRIC DIGITAL DATA PROCESSING
- G06F21/00—Security arrangements for protecting computers, components thereof, programs or data against unauthorised activity
- G06F21/50—Monitoring users, programs or devices to maintain the integrity of platforms, e.g. of processors, firmware or operating systems
- G06F21/57—Certifying or maintaining trusted computer platforms, e.g. secure boots or power-downs, version controls, system software checks, secure updates or assessing vulnerabilities
-
- G—PHYSICS
- G09—EDUCATION; CRYPTOGRAPHY; DISPLAY; ADVERTISING; SEALS
- G09C—CIPHERING OR DECIPHERING APPARATUS FOR CRYPTOGRAPHIC OR OTHER PURPOSES INVOLVING THE NEED FOR SECRECY
- G09C1/00—Apparatus or methods whereby a given sequence of signs, e.g. an intelligible text, is transformed into an unintelligible sequence of signs by transposing the signs or groups of signs or by replacing them by others according to a predetermined system
-
- H—ELECTRICITY
- H04—ELECTRIC COMMUNICATION TECHNIQUE
- H04L—TRANSMISSION OF DIGITAL INFORMATION, e.g. TELEGRAPHIC COMMUNICATION
- H04L9/00—Cryptographic mechanisms or cryptographic arrangements for secret or secure communications; Network security protocols
- H04L9/32—Cryptographic mechanisms or cryptographic arrangements for secret or secure communications; Network security protocols including means for verifying the identity or authority of a user of the system or for message authentication, e.g. authorization, entity authentication, data integrity or data verification, non-repudiation, key authentication or verification of credentials
- H04L9/3247—Cryptographic mechanisms or cryptographic arrangements for secret or secure communications; Network security protocols including means for verifying the identity or authority of a user of the system or for message authentication, e.g. authorization, entity authentication, data integrity or data verification, non-repudiation, key authentication or verification of credentials involving digital signatures
-
- H—ELECTRICITY
- H04—ELECTRIC COMMUNICATION TECHNIQUE
- H04L—TRANSMISSION OF DIGITAL INFORMATION, e.g. TELEGRAPHIC COMMUNICATION
- H04L2209/00—Additional information or applications relating to cryptographic mechanisms or cryptographic arrangements for secret or secure communication H04L9/00
- H04L2209/84—Vehicles
Definitions
- the present disclosure relates to an electronic control unit that detects program tampering, a program tampering detection method, a program of the program tampering detection method, and a computer-readable sustainable tangible recording medium.
- a control system ECU Electronic Control Unit
- a body system ECU that controls a meter, a power window, etc.
- an information system ECU such as a navigation device Etc.
- the programs of the on-board ECUs mounted on the vehicle include, for example, those in which strict time restrictions are imposed on the start-up time in order to ensure safety.
- Patent Document 1 describes the disclosure of a secure boot method in which only an intended OS or the like is operated with respect to a risk that an OS (Operating System) or the like is falsified by a third party in an embedded device such as a car.
- a computer is to be verified among partial programs in which a program is divided into a plurality of programs for each program activation of the system for the purpose of activating the system quickly and safely. It is determined whether the selection step of selecting the partial program, the calculation step of calculating the hash value of the selected partial program, and whether the calculated hash value and the correct hash value match, and if they match, start processing is continued. And a verification step of interrupting the start-up process if they do not match.
- the program area to be verified is divided into a plurality of divisions, and verification of the presence or absence of program tampering is sequentially performed in each division to satisfy the restriction of the activation time. It is stated that all program areas to be verified can be verified.
- wake-up wake-up time constraints from sleep are more stringent than normal wake-up time constraints. For this reason, in order to satisfy the time constraint at the time of wake-up activation from sleep, it is necessary to finely divide the area of the program to be verified into multiple partial programs.
- An object of the present invention is to provide an electronic control device, a program tampering detection method, a program of the program tampering detection method, and a computer-readable sustainable tangible recording medium.
- the electronic control unit generates a plurality of divided programs obtained by dividing the program and a storage unit for storing a verification authenticator, and generates a partial authenticator of each of the plurality of divided programs by cryptographic operation. And a logical operation using a plurality of partial authenticators to generate an operation authenticator, and falsification of the program depending on whether the authentication authenticator and the operation authenticator match or not. And a verification unit to be verified.
- the electronic control device described above matches the operation authenticator generated by the logical operation using a plurality of partial authenticators generated from the divided programs and the verification authenticator generated by performing the same logical operation in advance Whether the program has been tampered with or not is verified.
- the number of verification authenticators stored in advance in the storage unit can be smaller than the number of divided programs. Therefore, even if the number of divisions of the program is increased in order to satisfy the restriction of the activation time, the electronic control unit consumes a small amount of memory (memory) required for storing the verification authenticator.
- a program tampering detection method comprises: generating, by cryptographic operation, a partial authenticator of each of a plurality of divided programs obtained by dividing a program; and performing a logical operation using the plurality of partial authenticators And generating the operation certifier, and determining whether or not the operation certifier matches the previously-obtained verification certifier.
- the operation authentication code generated by the logical operation using a plurality of partial authentication codes generated from the divided programs matches the verification authentication code generated by performing the same logical operation in advance Whether the program is tampered or not is verified.
- the number of verification authenticators stored in advance can be smaller than the number of divided programs. Therefore, even if the number of divisions of the program is increased in order to satisfy the start time constraint, the consumption of the storage unit (memory) required for storing the verification authenticator decreases.
- the program generates a partial authenticator of each of a plurality of divided programs obtained by dividing the program by cryptographic operation, and performs a logical operation using the plurality of partial authenticators to perform arithmetic authentication.
- a computer is caused to execute a program tampering detection method including generation of a child, and determination as to whether or not the operation authenticator matches a previously-obtained authentication authenticator.
- the operation authentication code generated by the logical operation using a plurality of partial authentication codes generated from the divided programs matches the verification authentication code generated by performing the same logical operation in advance Whether the program is tampered or not is verified.
- the number of verification authenticators stored in advance can be smaller than the number of divided programs. Therefore, even if the number of divisions of the program is increased in order to satisfy the start time constraint, the consumption of the storage unit (memory) required for storing the verification authenticator decreases.
- the program generates a partial authenticator of each of a plurality of divided programs obtained by dividing the program by cryptographic operation, and performs a logical operation using the plurality of partial authenticators to perform arithmetic authentication.
- the program control method includes: generating a child; and determining whether the operation authenticator matches the authentication authenticator obtained in advance. Run it.
- the operation authentication code generated by the logical operation using a plurality of partial authentication codes generated from the divided programs matches the verification authentication code generated by performing the same logical operation in advance Whether the program is tampered or not is verified.
- the number of verification authenticators stored in advance can be smaller than the number of divided programs. Therefore, even if the number of divisions of the program is increased in order to satisfy the start time constraint, the consumption of the storage unit (memory) required for storing the verification authenticator decreases.
- a program generates, by cryptographic operation, a partial authenticator of each of a plurality of divided programs obtained by dividing a program, and performs logical operation using the plurality of partial authenticators to perform arithmetic authentication.
- a program tampering detection method comprising generation of a child, and determination as to whether or not the operation authenticator and the authentication authenticator obtained in advance coincide with each other is generally selected from the low power consumption mode of the electronic control device. Make it run on your computer when transitioning to mode.
- the operation authentication code generated by the logical operation using a plurality of partial authentication codes generated from the divided programs matches the verification authentication code generated by performing the same logical operation in advance Whether the program is tampered or not is verified.
- the number of verification authenticators stored in advance can be smaller than the number of divided programs. Therefore, even if the number of divisions of the program is increased in order to satisfy the start time constraint, the consumption of the storage unit (memory) required for storing the verification authenticator decreases.
- the instructions in a computer-readable non-transitory tangible storage medium including computer-executable instructions, the instructions generate a partial authenticator of each of a plurality of divided programs obtained by dividing a program by cryptographic operation. And performing a logical operation using a plurality of the partial authenticators to generate an operational authenticator, and determining whether the operational authenticator matches a verification authenticator obtained in advance. And.
- the above-described computer-readable persistent tangible recording medium is a verification authenticator generated by performing the same logical operation in advance as an operation authenticator generated by a logical operation using a plurality of partial authenticators generated from divided programs. Whether the program is tampered or not is verified by whether or not the two match.
- the number of verification authenticators stored in advance can be smaller than the number of divided programs. Therefore, even if the number of divisions of the program is increased in order to satisfy the start time constraint, the consumption of the storage unit (memory) required for storing the verification authenticator decreases.
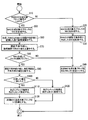
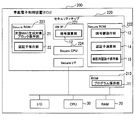
- FIG. 8 is an explanatory view schematically showing an outline of program falsification check processing by the electronic control unit of FIG. 1; 6 is a flowchart for explaining the operation of the electronic control unit of FIG. 1; It is a block diagram explaining the composition of the electronic control unit concerning Embodiment 2 of this indication.
- the electronic control unit 100 includes a ROM (Read Only Memory) 10, a RAM (Random Access Memory) 20, a CPU (Central Processing Unit) 30, an I / O (Input / Output), and a configuration of these. Are composed of bus lines etc.
- ROM Read Only Memory
- RAM Random Access Memory
- CPU Central Processing Unit
- I / O Input / Output
- the main object is to use an encryption operation using a message authentication code (MAC), but in the present disclosure, an operation (SHA-) using a hash function (Hash function) is described. Including 256) and other operations.
- MAC message authentication code
- SHA- hash function
- the ROM 10 includes a program storage unit 11 for tampering check, an encryption operation unit 12, an encryption key storage unit 13, an authenticator operation unit 14, and a verification authenticator storage unit 15.
- the program storage unit 11 (corresponding to the “storage unit” of the present disclosure) stores a program subjected to tampering check as a divided program divided into a plurality of blocks.
- the number of divisions of the program may be determined in consideration of the application of the electronic control unit 100, the activation time, and the like.
- vision is sufficient if the start point of the part of the program is specified by dividing the storage area or the like, and it is not necessary to divide the program itself.
- the encryption operation unit 12 (corresponding to the “encryption operation unit” in the present disclosure) is an area in which an encryption operation program is stored.
- the encryption operation is performed by the CPU (encryption operation unit) 30 which has read the program of the encryption operation unit 12.
- an encryption operation program using a message authentication code such as Cipher-based MAC (CMAC) is stored in the encryption operation unit 12.
- MAC message Authentication Code
- CMAC Cipher-based MAC
- cryptographic operations other than MAC include operations (such as SHA-256) using a HASH function (Hash function).
- a partial authenticator for each of a plurality of divided programs is generated by cryptographic operation.
- the encryption key storage unit 13 is an area in which an encryption key for MAC operation, which is required when the encryption operation unit 12 performs the encryption operation, is stored.
- the encryption key storage unit 13 is not necessary because the encryption key is unnecessary.
- the authenticator operation unit 14 (corresponding to the “verification unit” in the present disclosure) is a logic that generates an operation authenticator using a plurality of partial authenticators generated for each divided program of the program storage unit 11 for tampering check. It is an area in which an arithmetic program is stored.
- the logical operation is performed by the CPU (verification unit) 30 which has read the program of the authenticator operation unit 14.
- the logical operation used in the authenticator operation unit 14 will be described later with reference to FIGS. 2 and 3. In addition, verification of the presence or absence of program falsification will be described later with reference to FIGS. 2 and 3.
- the verification authenticator storage unit 15 (corresponding to the “storage unit” of the present disclosure) is an area in which the verification authenticator of the program to be verified stored in the program storage unit 11 which is the target of tampering verification is stored. is there.
- the verification authenticator is generated by performing predetermined cryptographic computation and logical computation on the program of the program storage unit 11 in advance.
- the electronic control unit 100 may have a function (reprogram function) capable of rewriting the program storage unit 11 stored in the ROM 10.
- a function reprogram function
- the verification authenticator storage unit 15 since the verification authenticator changes as the program storage unit 11 is rewritten, the verification authenticator storage unit 15 also needs to be rewritten.
- the reprogramming function is provided, there is a high possibility of being connected from the outside, so the number of divisions of the program storage unit 11 can be increased without increasing the area required for storing the verification authenticator.
- Device 100 is useful.
- the RAM 20 is provided with a next MAC generation target block storage unit 21 and an authentication code storage unit 22.
- the next MAC generation target block storage unit 21 stores information such as a block number and an address in the ROM 10 that can specify a divided program to be a target of MAC generation next.
- a new authenticator is overwritten and stored in the authenticator storage unit 22 each time an authenticator is generated.
- the CPU 30 is a device that executes a program, and executes each program of the cryptographic computation unit 12 and the authenticator computation unit 14 when verifying program tampering of the program storage unit 11. 2. Tamper Check Process The program tamper check process by the electronic control unit 100 having the above-described configuration will be described with reference to FIG.
- MAC operation is an encryption operation using a message authentication code (MAC), and using the encryption key of the encryption key storage unit 13 as execution of the program of the encryption operation unit 12, blocks of the tamper check area 10A of the ROM 10. It is performed for each of the divided programs of 1 to n. As a result of the MAC operation, MAC1 to MACn (partial authenticators) are generated for each of the divided programs of block 1 to block n.
- MAC1 to MACn partial authenticators
- the generated MAC is, for example, 128 bits in the case of an operation using an encryption algorithm of AES (Advanced Encryption Standard) 128.
- AES Advanced Encryption Standard
- the generated HASH value is 256 bits.
- the ROM 10 is divided into a tampering check area 10A in which the program storage unit 11 in which n partial programs are stored is placed, and a non-tampering check area 10B other than that.
- partial programs divided into blocks 1 to n are stored.
- partial programs of block 1 to block n may be referred to as block 1 to block n as appropriate.
- a verification authenticator is stored in the non-falsification check area 10B.
- the verifier for verification is generated in advance by calculation, and it is compared with the verifier [1-n] (verifier for calculation) whether the blocks 1 to n are tampered or not This data is highly important because it is used to determine Therefore, the non-tamper check area 10B of the ROM 10 is configured as a secure area.
- the secure area is an area where access to stored information is difficult and the function of protecting information is high.
- FIG. 2 shows an example in which the entire non-tamper check area 10B is configured as a secure area.
- the non-falsification check area 10B may not be a secure area but may be an area of an information protection function similar to that of the falsification check area 10A, or a part may be a secure area.
- an encryption operation unit 12 an encryption key storage unit 13, and an authentication code operation unit 14 (see FIG. 1) are also placed.
- 2.2. Logical operation When MACx is calculated by the cryptographic operation of block x (x is an integer of 2 to n), the logical operation of the authenticator and MACx stored in the authenticator storage unit 22 of the RAM 20 is performed to perform authentication The child [1-x] is generated and overwritten on the authenticator storage unit 22. At the same time, the block number x + 1 specifying the block x + 1 is stored in the next MAC generation target block storage unit 21.
- Logical operations include AND (AND operation), NOT of AND (NAND operation), OR (OR operation), NOT of OR (NOR operation), exclusive OR (XOR operation), and exclusive logic
- exclusive OR and negation of exclusive OR do not converge to either 0 or 1 by repetition of logical operation because the number of 0 and 1 in the truth table is the same. Preferred in point. 2.3. Relationship between MAC Operation and Logic Operation MAC operation and logic operation are implemented as described in 2.1 and 2.2, respectively. In the following, when the MACs are generated in order of block numbers, the partial authenticators generated by the MAC operation and the operation authenticators generated by the logical operation are sequentially implemented as to how they are used. The process will be described in order along the processing of blocks 1 to n.
- MAC1 of block 1 is a partial authenticator generated first. Therefore, at the time when MAC1 is generated, it is not possible to perform the logical operation using a plurality of partial authenticators. Therefore, the MAC 1 of the block 1 is stored in the authenticator storage unit 22 of the RAM 20 as the authenticator [1] (arithmetic authenticator). At the same time, the next MAC generation target block of the next MAC generation target block storage unit 21 is set to 2.
- the authentication code [1-2] (operation authentication code) generated by performing the logical operation of the authentication code [1] of the authentication code storage unit 22 and MAC 2 is authenticated. It is overwritten and stored in the child storage unit 22.
- the next MAC generation target block of the next MAC generation target block storage unit 21 is set to 3.
- the authenticator [1] is the same as MAC1, the logical operation of MAC2 and the authenticator [1] is performed using two partial authenticators.
- the authentication code [1-3] (operation authentication code) generated by performing the logical operation of the authentication code [1-2] of the authentication code storage unit 22 and MAC3 is generated. It is overwritten and stored in the authentication code storage unit 22.
- the next MAC generation target block of the next MAC generation target block storage unit 21 is set to 4.
- the authenticator [1-2] is generated by the logical operation using MAC1 and MAC2, the logical operation of the authenticator [1-2] and the MAC3 is performed by three partial authenticators MAC1 and MAC2 And MAC3.
- the “plurality of partial authenticators” used in the logical operation includes the partial authenticator used in the previous logical operation.
- an authentication code [1-n] (operational authentication generated by performing logical operation of the authentication code [1-n-1] of the authentication code storage unit 22 and MACn The child is overwritten and stored in the authenticator storage unit 22.
- the next MAC generation target block of the next MAC generation target block storage unit 21 is initialized to 1.
- the authenticator [1-n-1] is generated by the logical operation using MAC1 to MACn-1
- the logical operation between the authenticator [1-n-1] and the MACn is a partial authenticator. It is performed using all of MAC1 to MACn.
- the authentication code [1-n] is an operation authentication code generated as a result of a logical operation performed using all of MAC1 to MACn (partial authentication code) of block 1 to block n. Therefore, when one of the blocks 1 to n is falsified, the falsification is reflected on the authenticator [1-n] via any one of MAC1 to MACn. Therefore, if there is tampering, the certifier [1-n] does not match the certifier for verification obtained by the operation in advance.
- the electronic control unit 100 performs an operation using all of MAC1 to MACn to generate an authenticator [1-n] (arithmetic authenticator), compares it with the authenticator for verification, and generates the program storage unit 11 (FIG. See if there is any falsification. Therefore, it is sufficient to store one verification authenticator in the verification authenticator storage unit 15 of the ROM 10.
- the number n of blocks is n minus one, which is equal to the number of blocks required for verification for verifying that the program has been tampered with for each divided block.
- the storage capacity of the verification authenticator of can be reduced.
- the storage capacity of (n-1) ⁇ 128 bits can be reduced.
- the effect of reducing the storage capacity of the ROM 10 increases as the number of divisions of the program to be subjected to the tampering verification increases.
- the increase in the number of divided programs is effective to prevent the processing from being wasted when the start processing is interrupted, and to shorten the start time of the electronic control unit 100.
- FIG. 2 the case where there is one verification authenticator is described. As described above, it is preferable to use one verification authenticator from the viewpoint of reducing the storage capacity of the verification authenticator storage unit 15 of the ROM 10.
- the number of verification authenticators stored in the verification authenticator storage unit 15 is not limited to one, and may be plural.
- plural verification authenticators are used, a plurality of blocks 1 to n are used.
- the group is divided into groups, and a verification authenticator for each group is stored in advance in the ROM 10. Then, a verifier for verification by logical operation using all partial verifiers of each group is generated, and compared with the verifier for verification, it is determined whether or not the divided programs included in the group are tampered.
- the authenticator storage unit 22 stores an authenticator (arithmetic authenticator) obtained by the tampering check process until cancellation. Further, in the next MAC generation target block storage unit 21, a block to be a MAC generation target is stored next to the logical operation for which the certifier is obtained. Therefore, it is possible to resume from the next cryptographic operation of the logical operation that has generated the certifier in the falsification check process of the to be aborted. Then, in the logical operation following the resumed cryptographic operation, the certifier of the certifier storage unit 22 can be used, so that the result of the cryptographic processing and the logical operation on the block completed before interruption can be used effectively. .
- the RAM 20 includes a non-initialization region 20A which is not initialized and an initial region 20B which is initialized at the time of startup from the low power consumption mode to the normal mode (Wake Up startup).
- the next MAC generation target block storage unit 21 and the authentication code storage unit 22 are placed in the non-initialization area 20A. Therefore, the information written to the next MAC generation block storage unit 21 and the authentication unit storage unit 22 rewritten each time the authentication unit 1 to the authentication unit [1-n] are calculated is maintained when Wake Up is activated. Be done. Therefore, if a restart occurs during the computation of authenticator 1 to authenticator [1-n], based on the information of the next MAC generation target block storage unit 21 and authenticator storage unit 22 recorded before the restart. And the tamper check process can be resumed.
- the next-to-next MAC generation target block storage unit 21 and the authentication code storage unit 22 may be stored in rewritable non-volatile memory such as EEPROM or Data Flash.
- EEPROM electrically erasable programmable read-only memory
- the non-volatile memory in the above-mentioned example can be used only when the time constraint at the time of starting the electronic control device 100 can be satisfied.
- the present disclosure can also be implemented as an electronic control unit unit including a plurality of electronic control units.
- an electronic control unit having a plurality of electronic control units is used in combination with electronic control units having different time restrictions at the time of start-up. Therefore, it is preferable to make the number of divisions of the division program stored in the storage unit different depending on applications of a plurality of electronic control devices and time restrictions at the time of movement. As a result, it is possible to suppress the consumption of the memory as the entire storage unit in the electronic control unit unit while satisfying the restrictions of the activation times of the electronic control unit. 3.
- Program Tampering Detection Method With reference to FIG. 3, a program tampering detection method by the electronic control unit 100 described above will be described.
- the CPU 30 reads and executes the programs of the cryptographic operation unit 12 and the authenticator operation unit 14 (see FIG. 1), and changes from the low power consumption mode to the normal mode when the electronic control device 100 is started. It is called when migrating.
- the low power consumption mode is a state in which the electronic control unit 100 does not perform part of the processing performed in the normal mode, and the power consumption is smaller than that in the normal mode.
- the sleep mode in which a program being executed is stored in memory and temporarily stopped is an example of the low power consumption mode.
- S10 it is determined whether or not the block number is other than 1 with reference to the block number recorded in the next MAC generation target block storage unit 21 of the RAM 20. Then, if the block number of the next MAC generation target block storage unit 21 is not 1 (if it is 1) (S10: NO), the process proceeds to S20 (encryption operation step), and stores the next MAC generation target block If the block number of the unit 21 is other than 1 (S10: YES), the process proceeds to S50 (encryption operation step).
- the MAC 1 generated in S20 is stored in the authenticator storage unit 22 of the RAM 20 as an authenticator, and the process proceeds to S40 (authenticator operation step).
- the block number obtained by adding 1 to the block number of the partial program for which MAC was generated in S20 is written (set) in the next MAC generation block storage unit 21 of the RAM 20 as the next MAC generation target block. End the process.
- MACx of a divided program of block number x (x is an integer of 2 to n), which is a MAC generation target block, is generated, and the process proceeds to S60 (authenticator operation step).
- the authenticator operation unit 14 performs a logical operation on the MAC generated in S50 and the authenticator [1- (x-1)] stored in the authenticator storage unit 22 of the RAM 20, and the authenticator [ Calculate 1 ⁇ (x)], and shift to S70.
- the authenticator [1-n] stored in the authenticator storage unit 22 in S70 is obtained as a result of logical operation using partial authenticators of all divided programs. It is It can be used as a verification authenticator for verifying whether or not a tampered program is included in all divided programs. Therefore, the process proceeds to S90 (verification step).
- the certifier [1-n] stored in the certifier storage unit 22 is compared with the certifier for verification stored in the certifier storage unit 15 for verification.
- S100 verification step
- S100: YES the process proceeds to S110; if they do not match (S100: YES), the process proceeds to S120.
- the falsification check result is set to no falsification, and the process proceeds to S130.
- the present disclosure can also be implemented as a program that causes a computer to execute the program tampering detection method described above.
- the program is executed when the electronic control device is activated or when transitioning from the low power consumption mode to the normal mode.
- the electronic control unit of the present embodiment it can be obtained by performing logical operation using a plurality of partial authenticators rather than each partial authenticator itself required for each divided program into which the program is divided.
- the operation certifier is compared with the certifier for verification to detect whether the program has been tampered with. This makes it possible to reduce the number of verification authenticators to be stored and to suppress the large consumption of ROM.
- Second Embodiment An embodiment in which the present disclosure is applied to an electronic control unit (ECU) using a security chip will be described.
- the electronic control unit 200 of the present embodiment includes a ROM 210, a security chip 220, a RAM 20, a CPU 30, and I / O and a bus line connecting these components.
- the electronic control unit 200 is different from the electronic control unit 100 in that the configuration includes a ROM 210 and a security chip 220 instead of the ROM 10.
- the configuration includes a ROM 210 and a security chip 220 instead of the ROM 10.
- the program storage unit 11 is disposed in the ROM 210.
- the components other than the program storage unit 11 are placed on the security chip 220 which is highly resistant to tampering (difficulty of analyzing stored data).
- the security chip 220 includes a secure CPU 224, a secure RAM 223, a secure interface (Secure I / F), a hardware IP module (HWIP) 221, and a secure ROM 222.
- the hardware IP module 221 has a cryptographic operation unit 12.
- the secure ROM 222 has an encryption key storage unit 13, an authentication code calculation unit 14, and a verification authentication code storage unit 15.
- the secure (secure) RAM 223 includes a block storage unit for MAC generation next time 21 and an authentication unit storage unit 22.
- the CPU 30 executes the various cryptographic computations of FIG. 2 and the process of the flow of FIG. 3. However, in the present embodiment, the secure CPU 224 executes this.
- the security chip 220 stores the program (and temporary data such as the operation certifier and the next MAC generation target block), the encryption key, and the certifier for verification, which are used for processing for verifying the presence or absence of program tampering.
- the program and temporary data such as the operation certifier and the next MAC generation target block
- the encryption key and the certifier for verification, which are used for processing for verifying the presence or absence of program tampering.
- access to the program (and the temporary data), the encryption key, and the verifier for verification can be prevented.
- Examples of forms of the electronic control device of the present disclosure include semiconductors, electronic circuits, modules, and microcomputers.
- necessary functions such as an antenna and a communication interface may be added to these.
- it is also possible to take a form such as a car navigation system, a smartphone, a personal computer, and a portable information terminal.
- the present disclosure can not only be realized by the above-described dedicated hardware, but also a program recorded in a recording medium such as a memory or a hard disk, and general-purpose hardware having a dedicated or general-purpose CPU, memory, etc. It can be realized as a combination with
- Programs stored in dedicated or general-purpose hardware storage areas can be recorded via recording media or without recording media.
- the electronic control unit according to the present disclosure can be used as an on-vehicle electronic control unit (ECU).
- ECU electronic control unit
- electronic control devices other than those for use in vehicles are also included in the present disclosure.
- each section is expressed as, for example, S10.
- each section can be divided into multiple subsections, while multiple sections can be combined into one section.
- each section configured in this way can be referred to as a device, a module, or a means.
Landscapes
- Engineering & Computer Science (AREA)
- Computer Security & Cryptography (AREA)
- Theoretical Computer Science (AREA)
- General Physics & Mathematics (AREA)
- General Engineering & Computer Science (AREA)
- Physics & Mathematics (AREA)
- Software Systems (AREA)
- Computer Hardware Design (AREA)
- Computer Networks & Wireless Communication (AREA)
- Signal Processing (AREA)
- General Health & Medical Sciences (AREA)
- Bioethics (AREA)
- Health & Medical Sciences (AREA)
- Power Engineering (AREA)
- Storage Device Security (AREA)
Priority Applications (1)
| Application Number | Priority Date | Filing Date | Title |
|---|---|---|---|
| US16/738,927 US11392722B2 (en) | 2017-07-13 | 2020-01-09 | Electronic control device, program falsification detection method, and computer readable non- transitory tangible storage medium |
Applications Claiming Priority (2)
| Application Number | Priority Date | Filing Date | Title |
|---|---|---|---|
| JP2017-136725 | 2017-07-13 | ||
| JP2017136725A JP6949416B2 (ja) | 2017-07-13 | 2017-07-13 | 電子制御装置、プログラム改ざん検知方法 |
Related Child Applications (1)
| Application Number | Title | Priority Date | Filing Date |
|---|---|---|---|
| US16/738,927 Continuation US11392722B2 (en) | 2017-07-13 | 2020-01-09 | Electronic control device, program falsification detection method, and computer readable non- transitory tangible storage medium |
Publications (1)
| Publication Number | Publication Date |
|---|---|
| WO2019012952A1 true WO2019012952A1 (ja) | 2019-01-17 |
Family
ID=65002583
Family Applications (1)
| Application Number | Title | Priority Date | Filing Date |
|---|---|---|---|
| PCT/JP2018/023808 Ceased WO2019012952A1 (ja) | 2017-07-13 | 2018-06-22 | 電子制御装置、プログラム改ざん検知方法、プログラム改ざん検知方法のプログラム、およびコンピュータ読み出し可能持続的有形記録媒体 |
Country Status (3)
| Country | Link |
|---|---|
| US (1) | US11392722B2 (enExample) |
| JP (1) | JP6949416B2 (enExample) |
| WO (1) | WO2019012952A1 (enExample) |
Cited By (2)
| Publication number | Priority date | Publication date | Assignee | Title |
|---|---|---|---|---|
| CN113646760A (zh) * | 2019-04-16 | 2021-11-12 | 华为技术有限公司 | 一种软件程序运行检查方法、电子设备及存储介质 |
| DE112020005818T5 (de) | 2020-01-28 | 2022-09-08 | Mitsubishi Electric Corporation | Authentifikatorverwaltungsvorrichtung, authentifikatorverwaltungsprogramm und authentifikatorverwaltungsverfahren |
Families Citing this family (4)
| Publication number | Priority date | Publication date | Assignee | Title |
|---|---|---|---|---|
| WO2021015204A1 (ja) * | 2019-07-23 | 2021-01-28 | 株式会社ソニー・インタラクティブエンタテインメント | アクセス制御装置、アクセス制御方法及びプログラム |
| US11080387B1 (en) * | 2020-03-16 | 2021-08-03 | Integrity Security Services Llc | Validation of software residing on remote computing devices |
| JP7613174B2 (ja) | 2021-03-16 | 2025-01-15 | 富士フイルムビジネスイノベーション株式会社 | 情報処理装置及び情報処理プログラム |
| JP7427697B2 (ja) * | 2022-02-08 | 2024-02-05 | 本田技研工業株式会社 | 電子機器監視装置、移動体、及び電子機器監視方法 |
Citations (3)
| Publication number | Priority date | Publication date | Assignee | Title |
|---|---|---|---|---|
| JP2015090682A (ja) * | 2013-11-07 | 2015-05-11 | キヤノン株式会社 | 画像形成装置、その制御方法及びプログラム |
| WO2016185577A1 (ja) * | 2015-05-20 | 2016-11-24 | 富士通株式会社 | プログラム検証方法、検証プログラム、及び情報処理装置 |
| JP2017509082A (ja) * | 2014-03-25 | 2017-03-30 | オベルトゥル テクノロジOberthur Technologies | 不揮発性メモリ又はセキュア素子へのデータの読み込みを安全に行うこと |
Family Cites Families (14)
| Publication number | Priority date | Publication date | Assignee | Title |
|---|---|---|---|---|
| US3763477A (en) * | 1971-08-02 | 1973-10-02 | Bell Telephone Labor Inc | Magnetic domain logic control arrangement |
| US20040199516A1 (en) * | 2001-10-31 | 2004-10-07 | Metacyber.Net | Source information adapter and method for use in generating a computer memory-resident hierarchical structure for original source information |
| JP4732921B2 (ja) * | 2006-02-24 | 2011-07-27 | アルパイン株式会社 | プログラム正当性検証装置 |
| US8949600B2 (en) * | 2006-10-27 | 2015-02-03 | Qualcomm Incorporated | Composed message authentication code |
| US8453206B2 (en) * | 2006-11-09 | 2013-05-28 | Panasonic Corporation | Detecting unauthorized tampering of a program |
| WO2010110605A2 (ko) * | 2009-03-25 | 2010-09-30 | 엘지전자 주식회사 | Iptv 수신기 및 그의 컨텐트 다운로드 방법 |
| JP2012078953A (ja) | 2010-09-30 | 2012-04-19 | Kyocera Mita Corp | 改ざん検知装置及び改ざん検知方法 |
| US8780635B2 (en) * | 2012-11-09 | 2014-07-15 | Sandisk Technologies Inc. | Use of bloom filter and improved program algorithm for increased data protection in CAM NAND memory |
| JP2015022521A (ja) | 2013-07-19 | 2015-02-02 | スパンション エルエルシー | セキュアブート方法、組み込み機器、セキュアブート装置およびセキュアブートプログラム |
| WO2015013440A1 (en) * | 2013-07-23 | 2015-01-29 | Battelle Memorial Institute | Systems and methods for securing real-time messages |
| JP6244759B2 (ja) * | 2013-09-10 | 2017-12-13 | 株式会社ソシオネクスト | セキュアブート方法、半導体装置、及び、セキュアブートプログラム |
| KR102509594B1 (ko) * | 2016-06-28 | 2023-03-14 | 삼성전자주식회사 | 어플리케이션 코드의 위변조 여부 탐지 방법 및 이를 지원하는 전자 장치 |
| US10075425B1 (en) * | 2016-08-26 | 2018-09-11 | Amazon Technologies, Inc. | Verifiable log service |
| US10558812B2 (en) * | 2017-06-21 | 2020-02-11 | Microsoft Technology Licensing, Llc | Mutual authentication with integrity attestation |
-
2017
- 2017-07-13 JP JP2017136725A patent/JP6949416B2/ja not_active Expired - Fee Related
-
2018
- 2018-06-22 WO PCT/JP2018/023808 patent/WO2019012952A1/ja not_active Ceased
-
2020
- 2020-01-09 US US16/738,927 patent/US11392722B2/en active Active
Patent Citations (3)
| Publication number | Priority date | Publication date | Assignee | Title |
|---|---|---|---|---|
| JP2015090682A (ja) * | 2013-11-07 | 2015-05-11 | キヤノン株式会社 | 画像形成装置、その制御方法及びプログラム |
| JP2017509082A (ja) * | 2014-03-25 | 2017-03-30 | オベルトゥル テクノロジOberthur Technologies | 不揮発性メモリ又はセキュア素子へのデータの読み込みを安全に行うこと |
| WO2016185577A1 (ja) * | 2015-05-20 | 2016-11-24 | 富士通株式会社 | プログラム検証方法、検証プログラム、及び情報処理装置 |
Cited By (2)
| Publication number | Priority date | Publication date | Assignee | Title |
|---|---|---|---|---|
| CN113646760A (zh) * | 2019-04-16 | 2021-11-12 | 华为技术有限公司 | 一种软件程序运行检查方法、电子设备及存储介质 |
| DE112020005818T5 (de) | 2020-01-28 | 2022-09-08 | Mitsubishi Electric Corporation | Authentifikatorverwaltungsvorrichtung, authentifikatorverwaltungsprogramm und authentifikatorverwaltungsverfahren |
Also Published As
| Publication number | Publication date |
|---|---|
| JP2019020872A (ja) | 2019-02-07 |
| JP6949416B2 (ja) | 2021-10-13 |
| US20200151361A1 (en) | 2020-05-14 |
| US11392722B2 (en) | 2022-07-19 |
Similar Documents
| Publication | Publication Date | Title |
|---|---|---|
| WO2019012952A1 (ja) | 電子制御装置、プログラム改ざん検知方法、プログラム改ざん検知方法のプログラム、およびコンピュータ読み出し可能持続的有形記録媒体 | |
| JP6373888B2 (ja) | 情報処理装置及び制御方法 | |
| JP6422059B2 (ja) | 処理装置、車載端末装置、処理装置の起動方法、及び処理装置の起動プログラム | |
| CN113177201A (zh) | 程序校验、签名方法及装置、soc芯片 | |
| EP3522049B1 (en) | Data protection method for chip rewriting equipment, electronic equipment and storage medium | |
| CN109753788B (zh) | 内核运行时的完整性校验方法及计算机可读存储介质 | |
| CN112511306A (zh) | 一种基于混合信任模型的安全运行环境构建方法 | |
| JP5718373B2 (ja) | 不揮発性メモリのメモリブロックを検査する方法 | |
| CN114547618B (zh) | 基于Linux系统的安全启动方法、装置、电子设备及存储介质 | |
| JP6659180B2 (ja) | 制御装置および制御方法 | |
| US11620385B2 (en) | Vehicle control device, vehicle control device start-up method, and recording medium | |
| JP6622360B2 (ja) | 情報処理装置 | |
| JP5776480B2 (ja) | 情報処理装置、正当性検証方法、正当性検証プログラム | |
| JP7619253B2 (ja) | 電子制御装置 | |
| JP7635494B2 (ja) | トラストアンカコンピューティング装置を備える処理システムおよび対応する方法 | |
| JP2015049785A (ja) | プログラム処理装置 | |
| JP2019532402A (ja) | セキュア・ブート更新にわたる保護済みの機密情報の維持 | |
| CN109150534B (zh) | 终端设备及数据处理方法 | |
| CN114253576B (zh) | 双bios镜像刷新验证的方法、装置、存储介质及设备 | |
| US11509640B2 (en) | Method for protecting an electronic control unit | |
| KR20240122518A (ko) | 차량의 전자 제어 유닛의 비휘발성 메모리에 저장된 데이터의 무결성을 확인하는 방법 및 디바이스 | |
| CN118353698A (zh) | 一种车载数据的处理方法、装置及电子设备 | |
| CN120277675A (zh) | 处理装置的安全启动方法、装置、设备及可读存储介质 | |
| CN119227077A (zh) | 座舱域控制器系统的安全启动方法、装置、设备及车辆 | |
| CN120807140A (zh) | 基于区块链的交易方法、装置、电子设备和存储介质 |
Legal Events
| Date | Code | Title | Description |
|---|---|---|---|
| 121 | Ep: the epo has been informed by wipo that ep was designated in this application |
Ref document number: 18832027 Country of ref document: EP Kind code of ref document: A1 |
|
| NENP | Non-entry into the national phase |
Ref country code: DE |
|
| 122 | Ep: pct application non-entry in european phase |
Ref document number: 18832027 Country of ref document: EP Kind code of ref document: A1 |