WO2016184380A1 - Processing method and device for network access - Google Patents
Processing method and device for network access Download PDFInfo
- Publication number
- WO2016184380A1 WO2016184380A1 PCT/CN2016/082354 CN2016082354W WO2016184380A1 WO 2016184380 A1 WO2016184380 A1 WO 2016184380A1 CN 2016082354 W CN2016082354 W CN 2016082354W WO 2016184380 A1 WO2016184380 A1 WO 2016184380A1
- Authority
- WO
- WIPO (PCT)
- Prior art keywords
- terminal
- access
- information
- network
- predetermined
- Prior art date
Links
Images
Classifications
-
- H—ELECTRICITY
- H04—ELECTRIC COMMUNICATION TECHNIQUE
- H04W—WIRELESS COMMUNICATION NETWORKS
- H04W48/00—Access restriction; Network selection; Access point selection
- H04W48/02—Access restriction performed under specific conditions
- H04W48/04—Access restriction performed under specific conditions based on user or terminal location or mobility data, e.g. moving direction, speed
-
- H—ELECTRICITY
- H04—ELECTRIC COMMUNICATION TECHNIQUE
- H04W—WIRELESS COMMUNICATION NETWORKS
- H04W4/00—Services specially adapted for wireless communication networks; Facilities therefor
- H04W4/02—Services making use of location information
-
- H—ELECTRICITY
- H04—ELECTRIC COMMUNICATION TECHNIQUE
- H04W—WIRELESS COMMUNICATION NETWORKS
- H04W24/00—Supervisory, monitoring or testing arrangements
- H04W24/02—Arrangements for optimising operational condition
-
- H—ELECTRICITY
- H04—ELECTRIC COMMUNICATION TECHNIQUE
- H04W—WIRELESS COMMUNICATION NETWORKS
- H04W48/00—Access restriction; Network selection; Access point selection
- H04W48/16—Discovering, processing access restriction or access information
Definitions
- Wi-Fi wireless network such as the wireless network provided by a hotel
- invading the Wi-Fi wireless network and stealing the bandwidth of other Internet-enabled terminals not only increases the network security risk, but also affects the network experience of the guests and reduces the network speed. It can be seen that there is a network in the related art. The problem of low access control efficiency.
- the location information includes at least one of the following: a media access control MAC address of a Wi-Fi signal transmitting end carried by the Wi-Fi signal detected by the terminal, and a Wi-Fi signal detected by the terminal.
- a media access control MAC address of a Wi-Fi signal transmitting end carried by the Wi-Fi signal detected by the terminal and a Wi-Fi signal detected by the terminal.
- a method for processing an access network including: receiving location information of a terminal; determining, according to the location information, whether the terminal is within a target range of a predetermined network; and controlling the location according to the determination result The terminal accesses the predetermined network.
- the processing method further includes: receiving, by the router, Determining token information, wherein the predetermined token information is sent by the router after receiving the predetermined token information sent by the terminal; verifying the predetermined token information and token information sent to the terminal Whether the agreement is consistent; if the verification result is consistent, the terminal allows access information of the predetermined network to be sent to the router.
- the location information includes at least one of the following: a media access control MAC address of a Wi-Fi signal transmitting end carried by the Wi-Fi signal detected by the terminal, and a Wi-Fi signal detected by the terminal.
- a media access control MAC address of a Wi-Fi signal transmitting end carried by the Wi-Fi signal detected by the terminal and a Wi-Fi signal detected by the terminal.
- the location information of the terminal is sent to the authentication server, and the determination result returned by the authentication server according to the location information is received, where the determination result is used to identify whether the terminal is within the target range of the predetermined network. And determining, according to the determination result, whether the terminal is allowed to access the predetermined network, and solving the problem that the network access control efficiency in the related art is low, thereby achieving an effect of improving network access control efficiency.
- FIG. 2 is a flowchart of a method for processing a second access network according to an embodiment of the present invention
- the step of determining, according to the determination result, whether the terminal is allowed to access the predetermined network includes: acquiring token information carried in the determination result; The token information is accessed by the router to the predetermined network.
- the step of accessing the predetermined network by using the router according to the token information may include: after acquiring the token information, the terminal sends the token information to the router, and the router sends the received token information to the authentication server, and the authentication server The host is allowed to access the predetermined network by comparing the token information sent by the router with the token information sent to the terminal in advance.
- the terminal When the comparison result is consistent, it is determined that the terminal is in the target range, and the terminal is allowed to access the predetermined network, so that the terminal accesses the predetermined network through the router. If the comparison result is inconsistent, the terminal is not allowed to access the predetermined network. In addition, it intercepts illegal users to access the network and protects the interests of legitimate users. Improve the safety factor of the access network.
- FIG. 2 is a flowchart of a method for processing a second access network according to an embodiment of the present invention. As shown in FIG. 2, the processing method includes the following steps:
- Step S202 receiving location information of the terminal
- the step of controlling the terminal to access the predetermined network according to the foregoing judgment result comprises: sending the token information to the terminal when the determining result is that the terminal is located in the target range, wherein the token information is used for The terminal accesses the predetermined network through the router.
- the terminal sends information indicating that the terminal accesses the predetermined network. Thereby, the terminal is controlled to access the predetermined network according to the specific location of the terminal.
- a processing device for accessing the network is further provided, and the device is used to implement the foregoing embodiments and optional implementations, and details are not described herein.
- the term "module” may implement a combination of software and/or hardware of a predetermined function.
- the apparatus described in the following embodiments is preferably implemented in software, hardware, or a combination of software and hardware, is also possible and contemplated.
- the terminal device takes the most popular Android mobile phone as an example.
- the Android system provides an off-the-shelf interface for obtaining the Wi-Fi signal, the Bluetooth signal, and the base station signal of the terminal at the location.
- the location information that can be used to describe the terminal is very large.
- the location information of the terminal provided by the Wi-Fi signal is taken as an example in this embodiment, and the actual implementation is not limited thereto.
- Initial configuration of the AC controller save a list of MAC addresses, the MAC address list is set to allow the terminal to access the network if the source MAC address of the message is received from the terminal, and the source of the message is received from the terminal.
- the MAC address is not in the MAC address list, and the packet is redirected to the authentication server.
- the implementation method can first use the iptables rule to perform the destination network address translation (DNAT) to the local processing process. , the local processing process redirects the request to the authentication server, and The redirected link carries information about the Access Controller (AC). Set the validity period for the MAC address in the MAC address list.
- DNAT destination network address translation
- Step S802 the terminal sends an arbitrary HTTP request after connecting to the Wi-Fi network.
- Step S816 After receiving the redirection request from the terminal, the AC controller sends the MAC address, the AC controller identifier, and the token token of the terminal to the authentication server for verification, and is described in the JSON format as follows:
- Interface 1 used to receive the authentication home page http://auth-server/index that is redirected after the unauthenticated terminal goes online.
- the heartbeat interface is used to receive a request from the AC controller to query whether the MAC address of the terminal has expired: http://auth-server/alive.
- the network can be accessed through Wi-Fi or the like.
- the mobile terminal travels inside and outside the set area, and collects identification and information of Wi-Fi signals/Bluetooth signals, etc. at each position during the process of traveling, and each position will be marked as inside or outside the area, in order to ensure positioning.
- the effect is to mark and information such as Wi-Fi signals/Bluetooth signals intensively at the edge of the area, and mark and information such as Wi-Fi signals/Bluetooth signals at a slightly larger distance in and outside the area.
- 9 is a schematic diagram of a sample library and verified points located within and outside a region, respectively, in accordance with an embodiment of the present invention.
- both the AC controller and the authentication server are implemented in the router, two interfaces are required between the terminal and the router: one is a redirected address that is redirected to when the unauthenticated terminal accesses; The second is to verify the interface.
- the same address can be used, the entry uses the get instruction action, and the verification uses the post instruction action to distinguish.
- Embodiments of the present invention also provide a storage medium.
- the foregoing storage medium may be configured to store program code for performing the following steps:
- each module/unit in the above embodiment may be implemented in the form of hardware, for example, by implementing an integrated circuit to implement its corresponding function, or may be implemented in the form of a software function module, for example, executing a program stored in the memory by a processor. / instruction to achieve its corresponding function.
- Embodiments of the invention are not limited to any specific form of combination of hardware and software.
Landscapes
- Engineering & Computer Science (AREA)
- Computer Networks & Wireless Communication (AREA)
- Signal Processing (AREA)
- Computer Security & Cryptography (AREA)
- Mobile Radio Communication Systems (AREA)
Abstract
A processing method and device for network access. The method comprises: transmitting position information of a terminal to an authentication server; receiving a judgment result returned by the authentication server according to the position information, wherein the judgment result is used for marking whether the terminal is positioned within a target range of a scheduled network or not; and determining, according to the judgment result, whether to allow the terminal to access the scheduled network or not. The solution solves the problem of low control efficiency of network access existing in the related art, thereby realizing an effect of improving the control efficiency of network access.
Description
本申请涉及但不限于通信领域,尤其是一种接入网络的处理方法及装置。The present application relates to, but is not limited to, the field of communications, and in particular, to a method and apparatus for processing an access network.
随着移动互联网的飞速发展,各种智能终端以及Wi-Fi无线网络已经遍布人们活动的各个场所。然而入侵Wi-Fi无线网络并盗用其他可上网终端的带宽的现象却一直未能被有效禁止,其不仅仅影响网络体验,拖慢网速,更大的危害是让不可信的设备连入局域网络之中,带来更大的网络安全风险。Wi-Fi无线网络虽有多种加密方案,如有线等效保密(Wired Equivalent Privacy,简称为WEP)、Wi-Fi网络安全接入(Wi-Fi Protected Access,简称为WPA)、以及更高级的WPA2等等,其中WEP已被淘汰,WPA/WPA2以及其他方式在密码足够复杂的情况下是比较安全的,但是由于大量的类似于wifi万能钥匙的软件收集各Wi-Fi无线网络的密码信息并共享给其他使用者,尽管使用者不一定能看到明文的密码,但事实上密码已泄露;更加安全的方法是在防火墙上设置媒体接入控制(Media Access Control,简称为MAC)地址白名单,但这一种方法配置繁琐,且仅适合网络使用者较少且固定的情况。With the rapid development of the mobile Internet, various smart terminals and Wi-Fi wireless networks have spread all over the place where people are active. However, the phenomenon of invading Wi-Fi wireless networks and stealing the bandwidth of other Internet-enabled terminals has not been effectively banned. It not only affects the network experience, but also slows down the network speed. The greater harm is to connect untrusted devices to the LAN. In the network, it brings greater cyber security risks. Wi-Fi wireless networks have multiple encryption schemes, such as Wired Equivalent Privacy (WEP), Wi-Fi Protected Access (WPA), and more advanced. WPA2 and so on, where WEP has been eliminated, WPA/WPA2 and other methods are safer when the password is complicated enough, but the password information of each Wi-Fi wireless network is collected due to a large number of software similar to the wifi master key. Share to other users, although the user may not be able to see the plaintext password, but the password is actually leaked; a more secure method is to set the media access control (MAC) address whitelist on the firewall. However, this method is cumbersome to configure and is only suitable for a small and fixed network user.
而在商业/公共区域,通常将Wi-Fi无线网络的密码写在墙上,或者由店员提供,这种方法没有安全性;更安全的方法是无密码接入,通过短信验证码或者微信关注等方式认证,这一类方法需要在路由器上进行配置,未认证的客户端发起的请求将会被重定向到指定的认证网页,验证通过后才可使用Wi-Fi无线网络,现在一般的智能路由器都可以支持这样的认证方式,主流的开源插件wifidog可很好的实现该功能。In commercial/public areas, the password of the Wi-Fi wireless network is usually written on the wall or provided by the clerk. This method has no security; the safer method is no password access, via SMS authentication code or WeChat attention. In the other way, the method needs to be configured on the router. The request initiated by the unauthenticated client will be redirected to the specified authentication page. After the authentication is passed, the Wi-Fi wireless network can be used. Now the general intelligence Routers can support such authentication methods, and the mainstream open source plug-in wifidog can achieve this function very well.
通过短信/微信认证,商家可以收集到更精确的客户信息,精准地推送相关信息,但是仍然不能控制非目标群体使用Wi-Fi无线网络,比如某宾馆提供的无线网络,自然是仅希望员工和入住的客人可以使用,入侵Wi-Fi无线网络并盗用其他可上网终端的带宽的行为不仅加大网络安全风险,也很可能影响入住客人的网络体验,降低网速。由此可知,在相关技术中存在着网络
接入控制效率低的问题。Through SMS/WeCell authentication, merchants can collect more accurate customer information and accurately push relevant information, but still can't control non-target groups to use Wi-Fi wireless network, such as the wireless network provided by a hotel, naturally only hope employees and Guests who stay can use it, invading the Wi-Fi wireless network and stealing the bandwidth of other Internet-enabled terminals not only increases the network security risk, but also affects the network experience of the guests and reduces the network speed. It can be seen that there is a network in the related art.
The problem of low access control efficiency.
针对相关技术中存在的网络接入控制效率低的问题,目前尚未提出有效的解决方案。In view of the low efficiency of network access control existing in the related art, an effective solution has not been proposed yet.
发明内容Summary of the invention
以下是对本文详细描述的主题的概述。本概述并非是为了限制权利要求的保护范围。The following is an overview of the topics detailed in this document. This Summary is not intended to limit the scope of the claims.
本申请提供了一种接入网络的处理方法及装置,以至少解决相关技术中存在的网络接入控制效率低的问题。The present application provides a method and an apparatus for processing an access network, so as to at least solve the problem of low efficiency of network access control existing in the related art.
根据本申请的一个方面,提供了一种接入网络的处理方法,包括:向认证服务器发送终端的位置信息;接收所述认证服务器根据所述位置信息返回的判断结果,其中所述判断结果用于标识所述终端是否处于预定网络的目标范围内;根据所述判断结果确定是否允许所述终端接入所述预定网络。According to an aspect of the present application, a method for processing an access network is provided, including: transmitting location information of a terminal to an authentication server; and receiving a determination result returned by the authentication server according to the location information, where the determining result is used by And determining whether the terminal is within a target range of the predetermined network; determining, according to the determination result, whether the terminal is allowed to access the predetermined network.
可选地,所述位置信息包括以下信息至少之一:所述终端检测到的Wi-Fi信号携带的Wi-Fi信号发射端的媒体接入控制MAC地址和所述终端检测到的Wi-Fi信号的信号强度、所述终端检测到的蓝牙信号携带的蓝牙信号发射端的地址和所述终端检测到的蓝牙信号的信号强度。Optionally, the location information includes at least one of the following: a media access control MAC address of a Wi-Fi signal transmitting end carried by the Wi-Fi signal detected by the terminal, and a Wi-Fi signal detected by the terminal. The signal strength, the address of the Bluetooth signal transmitting end carried by the Bluetooth signal detected by the terminal, and the signal strength of the Bluetooth signal detected by the terminal.
可选地,当所述判断结果为所述终端处于所述目标范围内时,所述根据所述判断结果确定是否允许所述终端接入所述预定网络的步骤包括:获取所述判断结果中携带的令牌信息;依据所述令牌信息通过路由器接入所述预定网络。Optionally, when the determining result is that the terminal is in the target range, the step of determining, according to the determining result, whether to allow the terminal to access the predetermined network, includes: acquiring the determination result Carrying token information; accessing the predetermined network through a router according to the token information.
根据本申请的另一方面,提供了一种接入网络的处理方法,包括:接收终端的位置信息;根据所述位置信息判断所述终端是否处于预定网络的目标范围内;根据判断结果控制所述终端接入所述预定网络。According to another aspect of the present application, a method for processing an access network is provided, including: receiving location information of a terminal; determining, according to the location information, whether the terminal is within a target range of a predetermined network; and controlling the location according to the determination result The terminal accesses the predetermined network.
可选地,所述根据所述判断结果控制所述终端接入所述预定网络的步骤包括:当所述判断结果为所述终端位于所述目标范围内时,向所述终端发送令牌信息,其中,所述令牌信息用于所述终端通过路由器接入所述预定网络;当所述判断结果为所述终端位于所述目标范围外时,向所述终端发送拒绝所
述终端接入所述预定网络的信息。Optionally, the step of controlling the terminal to access the predetermined network according to the determining result includes: sending the token information to the terminal when the determining result is that the terminal is located in the target range The token information is used by the terminal to access the predetermined network through a router; when the determination result is that the terminal is outside the target range, sending a rejection to the terminal
The information that the terminal accesses the predetermined network.
可选地,所述当所述判断结果为所述终端位于所述目标范围内时,向所述终端发送所述令牌信息的步骤之后,所述处理方法还包括:接收所述路由器发送的预定令牌信息,其中,所述预定令牌信息为所述路由器在接收到终端发送的所述预定令牌信息后发送的;验证所述预定令牌信息与发送给所述终端的令牌信息是否一致;若验证结果为一致,将允许所述终端接入所述预定网络的允许信息发送给所述路由器。Optionally, after the step of sending the token information to the terminal when the determining result is that the terminal is located in the target range, the processing method further includes: receiving, by the router, Determining token information, wherein the predetermined token information is sent by the router after receiving the predetermined token information sent by the terminal; verifying the predetermined token information and token information sent to the terminal Whether the agreement is consistent; if the verification result is consistent, the terminal allows access information of the predetermined network to be sent to the router.
本申请另外提供一种计算机可读存储介质,存储有计算机可执行指令,所述计算机可执行指令被执行时实现上述方法。The application further provides a computer readable storage medium storing computer executable instructions that are implemented when the computer executable instructions are executed.
根据本申请的另一方面,提供了一种接入网络的处理装置,包括:发送模块,设置成向认证服务器发送终端的位置信息;第一接收模块,设置成接收所述认证服务器根据所述位置信息返回的判断结果,其中所述判断结果用于标识所述终端是否处于预定网络的目标范围内;处理模块,设置成根据所述判断结果确定是否允许所述终端接入所述预定网络。According to another aspect of the present application, a processing apparatus for accessing a network includes: a sending module configured to send location information of a terminal to an authentication server; and a first receiving module configured to receive the authentication server according to the And a determination result returned by the location information, where the determination result is used to identify whether the terminal is within a target range of the predetermined network; and the processing module is configured to determine, according to the determination result, whether the terminal is allowed to access the predetermined network.
可选地,所述位置信息包括以下信息至少之一:所述终端检测到的Wi-Fi信号携带的Wi-Fi信号发射端的媒体接入控制MAC地址和所述终端检测到的Wi-Fi信号的信号强度、所述终端检测到的蓝牙信号携带的蓝牙信号发射端的地址和所述终端检测到的蓝牙信号的信号强度。Optionally, the location information includes at least one of the following: a media access control MAC address of a Wi-Fi signal transmitting end carried by the Wi-Fi signal detected by the terminal, and a Wi-Fi signal detected by the terminal. The signal strength, the address of the Bluetooth signal transmitting end carried by the Bluetooth signal detected by the terminal, and the signal strength of the Bluetooth signal detected by the terminal.
可选地,所述处理模块包括:获取单元,设置成当所述判断结果为所述终端处于所述目标范围内时,获取所述判断结果中携带的令牌信息;接入单元,设置成依据所述令牌信息通过路由器接入所述预定网络。Optionally, the processing module includes: an acquiring unit, configured to acquire token information carried in the determining result when the determining result is that the terminal is in the target range; and the access unit is configured to Accessing the predetermined network through a router according to the token information.
根据本申请的另一方面,提供了一种接入网络的处理装置,包括:第二接收模块,设置成接收终端的位置信息;判断模块,设置成根据所述位置信息判断所述终端是否处于预定网络的目标范围内;控制模块,设置成根据判断结果控制所述终端接入所述预定网络。According to another aspect of the present application, a processing apparatus for accessing a network is provided, including: a second receiving module configured to receive location information of the terminal; and a determining module configured to determine, according to the location information, whether the terminal is in Within the target range of the predetermined network; the control module is configured to control the terminal to access the predetermined network according to the judgment result.
可选地,所述控制模块包括:第一发送单元,设置成当所述判断结果为所述终端位于所述目标范围内时,向所述终端发送令牌信息,其中,所述令牌信息用于所述终端通过路由器接入所述预定网络;第二发送单元,设置成当所述判断结果为所述终端位于所述目标范围外时,向所述终端发送拒绝所
述终端接入所述预定网络的信息。Optionally, the control module includes: a first sending unit, configured to send token information to the terminal when the determining result is that the terminal is located in the target range, where the token information The second sending unit is configured to: when the determining result is that the terminal is outside the target range, send a rejection to the terminal;
The information that the terminal accesses the predetermined network.
可选地,所述装置还包括:接收单元,设置成接收所述路由器发送的预定令牌信息,其中,所述预定令牌信息为所述路由器在接收到终端发送的所述预定令牌信息后发送的;验证单元,设置成验证所述预定令牌信息与发送给所述终端的令牌信息是否一致;第三发送单元,设置成若所述验证单元的验证结果为一致,将允许所述终端接入所述预定网络的允许信息发送给所述路由器。Optionally, the device further includes: a receiving unit, configured to receive predetermined token information sent by the router, where the predetermined token information is the predetermined token information that is sent by the router after receiving the terminal And a verification unit, configured to verify whether the predetermined token information is consistent with the token information sent to the terminal; and the third sending unit is configured to allow the verification if the verification result of the verification unit is consistent The permission information that the terminal accesses the predetermined network is sent to the router.
通过本申请的方案,采用向认证服务器发送终端的位置信息;接收所述认证服务器根据所述位置信息返回的判断结果,其中所述判断结果用于标识所述终端是否处于预定网络的目标范围内;根据所述判断结果确定是否允许所述终端接入所述预定网络,解决了相关技术中存在的网络接入控制效率低的问题,进而达到了提高网络接入控制效率的效果。Through the solution of the present application, the location information of the terminal is sent to the authentication server, and the determination result returned by the authentication server according to the location information is received, where the determination result is used to identify whether the terminal is within the target range of the predetermined network. And determining, according to the determination result, whether the terminal is allowed to access the predetermined network, and solving the problem that the network access control efficiency in the related art is low, thereby achieving an effect of improving network access control efficiency.
在阅读并理解了附图和详细描述后,可以明白其他方面。Other aspects will be apparent upon reading and understanding the drawings and detailed description.
附图概述BRIEF abstract
此处所说明的附图用来提供对本申请的进一步理解,构成本申请的一部分,本申请的示意性实施例及其说明用于解释本申请,并不构成对本申请的不当限定。在附图中:The drawings described herein are intended to provide a further understanding of the present application, and are intended to be a part of this application. In the drawing:
图1是根据本发明实施例的第一种接入网络的处理方法的流程图;1 is a flowchart of a processing method of a first access network according to an embodiment of the present invention;
图2是根据本发明实施例的第二种接入网络的处理方法的流程图;2 is a flowchart of a method for processing a second access network according to an embodiment of the present invention;
图3是根据本发明实施例的第一种接入网络的处理装置的结构框图;3 is a structural block diagram of a processing apparatus of a first access network according to an embodiment of the present invention;
图4是根据本发明实施例的第一种接入网络的处理装置的一种可选实施例的结构框图;4 is a structural block diagram of an alternative embodiment of a processing apparatus for a first access network according to an embodiment of the present invention;
图5是根据本发明实施例的第二种接入网络的处理装置的结构框图;FIG. 5 is a structural block diagram of a processing apparatus of a second access network according to an embodiment of the present invention; FIG.
图6是根据本发明实施例的第二种接入网络的处理装置的一种可选实施例的结构框图;6 is a structural block diagram of an alternative embodiment of a processing apparatus for a second access network according to an embodiment of the present invention;
图7是根据本发明实施例的第二种接入网络的处理装置的另一种可选实施例的结构框图;
FIG. 7 is a structural block diagram of another alternative embodiment of a processing apparatus for a second access network according to an embodiment of the present invention; FIG.
图8是根据本发明实施例一的路由器/AC控制器与认证服务器分离情况下的交互流程图;8 is a flow chart of interaction between a router/AC controller and an authentication server according to Embodiment 1 of the present invention;
图9是根据本发明实施例的样本库和被验证点分别位于区域内和区域外的示意图;9 is a schematic diagram of a sample library and verified points located within and outside a region, respectively, according to an embodiment of the present invention;
图10是根据本发明实施例二的路由器/AC控制器与认证服务器在同一个设备中的情况下的交互流程图。FIG. 10 is a flow chart showing the interaction of a router/AC controller and an authentication server in the same device according to Embodiment 2 of the present invention.
本发明的较佳实施方式Preferred embodiment of the invention
下文中将参考附图并结合实施例来详细说明本申请。需要说明的是,在不冲突的情况下,本申请中的实施例及实施例中的特征可以相互组合。The present application will be described in detail below with reference to the drawings in conjunction with the embodiments. It should be noted that the embodiments in the present application and the features in the embodiments may be combined with each other without conflict.
需要说明的是,本申请的说明书和权利要求书及上述附图中的术语“第一”、“第二”等是用于区别类似的对象,而不必用于描述特定的顺序或先后次序。It should be noted that the terms "first", "second" and the like in the specification and claims of the present application and the above-mentioned drawings are used to distinguish similar objects, and are not necessarily used to describe a specific order or order.
随着室内定位技术逐渐成熟,利用Wi-Fi/蓝牙指纹定位技术、惯导传感等技术,定位精度已能达到米级。基于相关技术中存在的上述问题,本发明实施例中,将室内定位技术与无线网络认证结合,提出了一种将终端的位置作为Wi-Fi无线网络的认证参数的方案,实现根据终端的位置决定终端是否可以访问网络。With the gradual maturity of indoor positioning technology, using Wi-Fi/Bluetooth fingerprint positioning technology, inertial sensing technology and other technologies, the positioning accuracy has reached the meter level. Based on the above problems in the related art, in the embodiment of the present invention, the indoor positioning technology is combined with the wireless network authentication, and a scheme of using the location of the terminal as the authentication parameter of the Wi-Fi wireless network is proposed, and the location according to the terminal is implemented. Determine if the terminal can access the network.
在本实施例中提供了一种接入网络的处理方法,图1是根据本发明实施例的第一种接入网络的处理方法的流程图,如图1所示,该处理方法包括如下步骤:In this embodiment, a processing method of an access network is provided. FIG. 1 is a flowchart of a processing method of a first access network according to an embodiment of the present invention. As shown in FIG. 1, the processing method includes the following steps. :
步骤S102,向认证服务器发送终端的位置信息;Step S102: Send location information of the terminal to the authentication server.
步骤S104,接收该认证服务器根据位置信息返回的判断结果,其中该判断结果用于标识终端是否处于预定网络的目标范围内;Step S104, receiving a determination result returned by the authentication server according to the location information, where the determination result is used to identify whether the terminal is within a target range of the predetermined network;
步骤S106,根据判断结果确定是否允许终端接入上述预定网络。Step S106: Determine, according to the determination result, whether the terminal is allowed to access the predetermined network.
通过上述步骤,在对终端进行接入网络的控制时,通过判断终端的位置信息来确定是否允许终端接入预定网络,从而使得处于预定网络的目标范围内的终端才可以接入预定网络,提高了网络连接的安全系数,也保障了合法
使用者的利益。解决了相关技术中存在的网络接入控制效率低的问题,进而达到了提高网络接入控制效率的效果。Through the above steps, when the terminal is controlled by the access network, it is determined whether the terminal is allowed to access the predetermined network by determining the location information of the terminal, so that the terminal within the target range of the predetermined network can access the predetermined network, thereby improving The safety factor of the network connection also ensures legality
User's interest. The problem that the network access control efficiency in the related art is low is solved, and the effect of improving the network access control efficiency is achieved.
其中,上述的位置信息可以通过多种方式进行确定,在一个可选的实施例中,上述位置信息可以包括以下信息至少之一:上述终端检测到的Wi-Fi信号携带的Wi-Fi信号发射端的媒体接入控制MAC地址和上述终端检测到的Wi-Fi信号的信号强度、上述终端检测到的蓝牙信号携带的蓝牙信号发射端的地址和上述终端检测到的蓝牙信号的信号强度;还可以通过终端的定位功能确定终端的具体位置,并将所确定的位置信息上报给认证服务器;或通过其他的方式确定终端的位置信息。The foregoing location information may be determined in multiple manners. In an optional embodiment, the location information may include at least one of the following information: a Wi-Fi signal transmission carried by the Wi-Fi signal detected by the terminal. The media access control MAC address of the terminal and the signal strength of the Wi-Fi signal detected by the terminal, the address of the Bluetooth signal transmitting end carried by the Bluetooth signal detected by the terminal, and the signal strength of the Bluetooth signal detected by the terminal; The location function of the terminal determines the specific location of the terminal, and reports the determined location information to the authentication server; or determines the location information of the terminal by other means.
在一个可选的实施例中,当上述判断结果为终端处于目标范围内时,所述根据判断结果确定是否允许终端接入上述预定网络的步骤包括:获取判断结果中携带的令牌信息;依据该令牌信息通过路由器接入上述预定网络。所述依据令牌信息通过路由器接入上述预定网络的步骤可以包括,当终端获取到令牌信息后,将该令牌信息发送给路由器,路由器将接收的令牌信息发送给认证服务器,认证服务器通过对比路由器发送过来的令牌信息和预先发送给终端的令牌信息来确定是否允许终端接入预定网络。当对比结果为一致时,确定该终端处于目标范围内,则允许该终端接入预定网络,从而使得终端通过路由器接入预定网络。若对比结果为不一致,则不允许上述终端接入预定网络。进而拦截了非法用户接入网络,保障了合法用户的利益。提高了接入网络的安全系数。In an optional embodiment, when the determining result is that the terminal is in the target range, the step of determining, according to the determination result, whether the terminal is allowed to access the predetermined network, includes: acquiring token information carried in the determination result; The token information is accessed by the router to the predetermined network. The step of accessing the predetermined network by using the router according to the token information may include: after acquiring the token information, the terminal sends the token information to the router, and the router sends the received token information to the authentication server, and the authentication server The host is allowed to access the predetermined network by comparing the token information sent by the router with the token information sent to the terminal in advance. When the comparison result is consistent, it is determined that the terminal is in the target range, and the terminal is allowed to access the predetermined network, so that the terminal accesses the predetermined network through the router. If the comparison result is inconsistent, the terminal is not allowed to access the predetermined network. In addition, it intercepts illegal users to access the network and protects the interests of legitimate users. Improve the safety factor of the access network.
图2是根据本发明实施例的第二种接入网络的处理方法的流程图,如图2所示,该处理方法包括如下步骤:FIG. 2 is a flowchart of a method for processing a second access network according to an embodiment of the present invention. As shown in FIG. 2, the processing method includes the following steps:
步骤S202,接收终端的位置信息;Step S202, receiving location information of the terminal;
步骤S204,根据该位置信息判断终端是否处于预定网络的目标范围内;Step S204, determining, according to the location information, whether the terminal is within a target range of the predetermined network;
步骤S206,根据判断结果控制终端接入上述预定网络。Step S206, controlling the terminal to access the predetermined network according to the determination result.
通过上述步骤,在控制终端接入网络时,通过验证终端的位置信息来确定是否允许终端接入预定网络,从而使得处于预定位置范围内的终端才可以接入预定网络,提高了网络连接的安全系数,也保障了合法使用者的利益。解决了相关技术中存在的网络接入控制效率低的问题,进而达到了提高网络
接入控制效率的效果。Through the above steps, when the control terminal accesses the network, it is determined whether the terminal is allowed to access the predetermined network by verifying the location information of the terminal, so that the terminal in the predetermined location range can access the predetermined network, thereby improving the security of the network connection. The coefficient also protects the interests of legitimate users. The invention solves the problem that the network access control efficiency in the related technology is low, thereby achieving the improvement of the network.
The effect of access control efficiency.
在一个可选的实施例中,根据上述判断结果控制终端接入预定网络的步骤包括:当上述判断结果为终端位于目标范围内时,向终端发送令牌信息,其中,该令牌信息用于终端通过路由器接入上述预定网络;当上述判断结果为终端位于目标范围外时,向上述终端发送拒绝终端接入上述预定网络的信息。从而实现了依据终端的具体位置控制终端接入预定网络。In an optional embodiment, the step of controlling the terminal to access the predetermined network according to the foregoing judgment result comprises: sending the token information to the terminal when the determining result is that the terminal is located in the target range, wherein the token information is used for The terminal accesses the predetermined network through the router. When the result of the foregoing determination is that the terminal is outside the target range, the terminal sends information indicating that the terminal accesses the predetermined network. Thereby, the terminal is controlled to access the predetermined network according to the specific location of the terminal.
在一个可选的实施例中,在所述向上述终端发送令牌信息的步骤之后,所述第二种接入网络的处理方法还包括:接收路由器发送的预定令牌信息,其中,该预定令牌信息为路由器在接收到终端发送的预定令牌信息后发送的;验证该预定令牌信息与发送给终端的令牌信息是否一致;若验证结果为一致,将允许上述终端接入预定网络的允许信息发送给路由器。In an optional embodiment, after the step of sending the token information to the terminal, the processing method of the second access network further includes: receiving predetermined token information sent by the router, where the predetermined The token information is sent by the router after receiving the predetermined token information sent by the terminal; verifying whether the predetermined token information is consistent with the token information sent to the terminal; if the verification result is consistent, the terminal is allowed to access the predetermined network. The allowed information is sent to the router.
通过以上的实施方式的描述,本领域的技术人员可以清楚地了解到根据上述实施例的方法可借助软件加必需的通用硬件平台的方式来实现,当然也可以通过硬件,但很多情况下前者是更佳的实施方式。基于这样的理解,本申请的技术方案本质上或者说对相关技术做出贡献的部分可以以软件产品的形式体现出来,该计算机软件产品存储在一个存储介质(如ROM/RAM、磁碟、光盘)中,包括若干指令用以使得一台终端设备(可以是手机,计算机,服务器,或者网络设备等)执行本申请各个实施例的方法。Through the description of the above embodiments, those skilled in the art can clearly understand that the method according to the above embodiment can be implemented by means of software plus a necessary general hardware platform, and of course, by hardware, but in many cases, the former is A better implementation. Based on such understanding, the technical solution of the present application, which is essential or contributes to the related art, may be embodied in the form of a software product stored in a storage medium (such as ROM/RAM, disk, CD-ROM). The instructions include a number of instructions for causing a terminal device (which may be a cell phone, computer, server, or network device, etc.) to perform the methods of various embodiments of the present application.
本发明实施例另外提供一种计算机可读存储介质,存储有计算机可执行指令,所述计算机可执行指令被执行时实现上述方法。Embodiments of the present invention further provide a computer readable storage medium storing computer executable instructions that are implemented when the computer executable instructions are executed.
在本实施例中还提供了一种接入网络的处理装置,该装置用于实现上述实施例及可选实施方式,已经进行过说明的不再赘述。如以下所使用的,术语“模块”可以实现预定功能的软件和/或硬件的组合。尽管以下实施例所描述的装置较佳地以软件来实现,但是硬件,或者软件和硬件的组合的实现也是可能并被构想的。In the embodiment, a processing device for accessing the network is further provided, and the device is used to implement the foregoing embodiments and optional implementations, and details are not described herein. As used below, the term "module" may implement a combination of software and/or hardware of a predetermined function. Although the apparatus described in the following embodiments is preferably implemented in software, hardware, or a combination of software and hardware, is also possible and contemplated.
图3是根据本发明实施例的第一种接入网络的处理装置的结构框图,如图3所示,该装置包括发送模块32、第一接收模块34和处理模块36,下面对该装置进行说明:3 is a structural block diagram of a processing apparatus of a first access network according to an embodiment of the present invention. As shown in FIG. 3, the apparatus includes a transmitting module 32, a first receiving module 34, and a processing module 36. Be explained:
发送模块32,设置成向认证服务器发送终端的位置信息;第一接收模块
34,连接至上述发送模块32,设置成接收认证服务器根据位置信息返回的判断结果,其中该判断结果用于标识终端是否处于预定网络的目标范围内;处理模块36,连接至上述第一接收模块34,设置成根据判断结果确定是否允许终端接入上述预定网络。The sending module 32 is configured to send location information of the terminal to the authentication server; the first receiving module
34, connected to the foregoing sending module 32, configured to receive a determination result returned by the authentication server according to the location information, wherein the determination result is used to identify whether the terminal is within a target range of the predetermined network; and the processing module 36 is connected to the first receiving module 34. Set to determine, according to the determination result, whether the terminal is allowed to access the predetermined network.
在一个可选的实施例中,上述的位置信息包括以下信息至少之一:终端检测到的Wi-Fi信号携带的Wi-Fi信号发射端的媒体接入控制MAC地址和终端检测到的Wi-Fi信号的信号强度、终端检测到的蓝牙信号携带的蓝牙信号发射端的地址和终端检测到的蓝牙信号的信号强度。In an optional embodiment, the foregoing location information includes at least one of the following: a media access control MAC address of the Wi-Fi signal transmitting end carried by the Wi-Fi signal detected by the terminal, and a Wi-Fi detected by the terminal. The signal strength of the signal, the address of the Bluetooth signal transmitter carried by the Bluetooth signal detected by the terminal, and the signal strength of the Bluetooth signal detected by the terminal.
图4是根据本发明实施例的第一种接入网络的处理装置的一种可选实施例的结构框图,如图4所示,该处理模块36包括获取单元42和接入单元44,下面对该处理模块36进行说明。FIG. 4 is a structural block diagram of an optional embodiment of a processing apparatus for a first access network according to an embodiment of the present invention. As shown in FIG. 4, the processing module 36 includes an obtaining unit 42 and an access unit 44. The processing module 36 will be described.
获取单元42,设置成当上述判断结果为终端处于目标范围内时,获取判断结果中携带的令牌信息;接入单元44,连接至上述获取单元42,设置成依据上述令牌信息通过路由器接入预定网络。The obtaining unit 42 is configured to acquire the token information carried in the determination result when the terminal is in the target range, and the access unit 44 is connected to the acquiring unit 42 and configured to be connected through the router according to the token information. Enter the scheduled network.
图5是根据本发明实施例的第二种接入网络的处理装置的结构框图,如图5所示,该装置包括第二接收模块52、判断模块54和控制模块56,下面对该装置进行说明。FIG. 5 is a structural block diagram of a processing apparatus for a second access network according to an embodiment of the present invention. As shown in FIG. 5, the apparatus includes a second receiving module 52, a determining module 54, and a control module 56. Be explained.
第二接收模块52,设置成接收终端的位置信息;判断模块54,连接至第二接收模块52,设置成根据上述位置信息判断终端是否处于预定网络的目标范围内;控制模块56,连接至判断单元54,设置成根据判断结果控制上述终端接入预定网络。The second receiving module 52 is configured to receive the location information of the terminal; the determining module 54 is connected to the second receiving module 52, and is configured to determine whether the terminal is within the target range of the predetermined network according to the location information; and the control module 56 is connected to the determining The unit 54 is configured to control the terminal to access the predetermined network according to the determination result.
图6是根据本发明实施例的第二种接入网络的处理装置的一种可选实施例的结构框图,如图6所示,该控制模块56包括第一发送单元62和/或第二发送单元64,下面对该控制模块56进行说明。FIG. 6 is a structural block diagram of an optional embodiment of a processing apparatus for a second access network according to an embodiment of the present invention. As shown in FIG. 6, the control module 56 includes a first sending unit 62 and/or a second. The transmitting unit 64 will be described below with respect to the control module 56.
第一发送单元62,设置成当上述判断结果为终端位于目标范围内时,向终端发送令牌信息,其中,该令牌信息用于终端通过路由器接入预定网络;第二发送单元64,设置成当上述判断结果为终端位于目标范围外时,向终端发送拒绝该终端接入预定网络的信息。
The first sending unit 62 is configured to send token information to the terminal when the determining result is that the terminal is located in the target range, wherein the token information is used by the terminal to access the predetermined network through the router; and the second sending unit 64 sets When the result of the above judgment is that the terminal is outside the target range, the terminal is sent information rejecting the terminal accessing the predetermined network.
图7是根据本发明实施例的第二种接入网络的处理装置的另一种的可选实施例的结构框图,如图7所示,该装置除包括图6所示的所有单元外,还包括接收单元72、验证单元74和第三发送单元76,下面对该控制模块56进行说明。FIG. 7 is a structural block diagram of another alternative embodiment of a processing apparatus for a second access network according to an embodiment of the present invention. As shown in FIG. 7, the apparatus includes all the units shown in FIG. The receiving unit 72, the verifying unit 74 and the third transmitting unit 76 are also included, and the control module 56 will be described below.
接收单元72,连接至第一发送单元62,设置成接收路由器发送的预定令牌信息,其中,该预定令牌信息为路由器在接收到终端发送的预定令牌信息后发送的;验证单元74,连接至接收单元72,设置成验证上述预定令牌信息与发送给终端的令牌信息是否一致;第三发送单元76,连接至验证单元74,设置成若上述验证单元的验证结果为一致,将允许终端接入预定网络的允许信息发送给路由器。The receiving unit 72 is connected to the first sending unit 62, and is configured to receive predetermined token information sent by the router, where the predetermined token information is sent by the router after receiving the predetermined token information sent by the terminal; the verifying unit 74, Connected to the receiving unit 72, configured to verify whether the predetermined token information is consistent with the token information sent to the terminal; the third sending unit 76 is connected to the verification unit 74, and is configured to: if the verification result of the verification unit is consistent, The permission information for allowing the terminal to access the predetermined network is sent to the router.
下面对整体流程进行说明。该整体流程涉及三种设备:终端设备,无线路由器和/或无线AC控制器(以下简称为无线路由器/无线AC控制器,或者简称为路由器/AC控制器),认证服务器。The overall process is described below. The overall process involves three types of devices: a terminal device, a wireless router and/or a wireless AC controller (hereinafter referred to as a wireless router/wireless AC controller, or simply a router/AC controller), and an authentication server.
其中终端设备以目前最为普遍的安卓手机为例,安卓系统提供了现成的用于获取终端在所处位置的Wi-Fi信号、蓝牙信号、基站信号的接口。可用于描述终端的位置信息非常多,为简化描述,本实施例仅以Wi-Fi信号提供的终端的位置信息为例,实际实施时并不局限于此。The terminal device takes the most popular Android mobile phone as an example. The Android system provides an off-the-shelf interface for obtaining the Wi-Fi signal, the Bluetooth signal, and the base station signal of the terminal at the location. The location information that can be used to describe the terminal is very large. To simplify the description, the location information of the terminal provided by the Wi-Fi signal is taken as an example in this embodiment, and the actual implementation is not limited thereto.
无线路由器/无线AC控制器(Wireless Access Point Controller):对于家庭用户,AC控制器即为无线路由器,一般采用常见的linux系统,内核版本2.4以上,其自带的iptables程序可以快捷地实现本申请方案。Wireless Access Point Controller: For home users, the AC controller is a wireless router. It is usually a common Linux system with a kernel version of 2.4 or higher. Its own iptables program can quickly implement this application. Program.
认证服务器:存储位置样本库,并提供接口用于验证位置是否满足条件。在AC控制器性能较强的情况下,AC控制器可以与认证服务器合一。Authentication Server: Stores a location sample library and provides an interface to verify that the location satisfies the condition. In the case of strong AC controller performance, the AC controller can be integrated with the authentication server.
该流程包括如下步骤:The process includes the following steps:
a终端通过Wi-Fi接入网络并发出访问任意某个地址的请求;a terminal accesses the network through Wi-Fi and issues a request to access any address;
b路由器根据从终端收到的请求中的报文源MAC地址(即终端的MAC地址),判断所述终端是否已认证,若未认证,则将该请求重定向至认证服务器,并且在重定向的地址中附加上路由器的标识,用于接收令牌token的接口地址等信息。
The router determines whether the terminal is authenticated according to the source MAC address of the packet received by the terminal (ie, the MAC address of the terminal). If not, the router redirects the request to the authentication server, and is redirected. The identifier of the router is attached to the address, and is used to receive information such as the interface address of the token token.
c认证服务器向终端返回一个认证页面,该认证页面用于终端向认证服务器发送位置指纹信息。The authentication server returns an authentication page to the terminal, where the authentication page is used by the terminal to send the location fingerprint information to the authentication server.
d终端向认证服务器发送收集到的相关位置指纹信息:位置指纹信息可以包含多个Wi-Fi信号携带的Wi-Fi信号发射端的MAC地址和多个Wi-Fi信号的信号强度,或者也可以包含蓝牙信号携带的蓝牙信号发射端的地址以及蓝牙信号的信号强度,当然,该位置指纹信息也可以是其他的信息或信息之间的组合。The terminal sends the collected location fingerprint information to the authentication server: the location fingerprint information may include the MAC address of the Wi-Fi signal transmitting end carried by the multiple Wi-Fi signals and the signal strength of the multiple Wi-Fi signals, or may also include The address of the Bluetooth signal transmitting end carried by the Bluetooth signal and the signal strength of the Bluetooth signal. Of course, the location fingerprint information may also be a combination of other information or information.
e认证服务器根据终端发送的位置指纹信息判断终端是否在网络提供者限定的目标范围内,若终端在限定的目标范围内,则向终端发送令牌token,并将该终端的请求重定向至路由器。The e-authentication server determines whether the terminal is within the target range defined by the network provider according to the location fingerprint information sent by the terminal, and if the terminal is within the limited target range, sends a token token to the terminal, and redirects the request of the terminal to the router. .
f路由器将收到的令牌token以及路由器的标识发送到认证服务器进行验证,如验证成功,则将该终端的MAC地址加入允许访问网络的列表,允许该终端通过路由器访问网络;The f router sends the received token token and the identifier of the router to the authentication server for verification. If the verification succeeds, the MAC address of the terminal is added to the list of allowed access networks, and the terminal is allowed to access the network through the router;
g客户端(即,终端)定期向认证服务器反馈其收集到的位置指纹信息、令牌token、以及终端的MAC地址等信息,认证服务器根据这些信息判断该终端是否可继续访问网络,同时路由器定期向认证服务器询问MAC是否处于可用状态,若不可用,将该MAC重新设置为一旦访问网络就重定向至认证页面。The g client (ie, the terminal) periodically feeds back to the authentication server the information such as the location fingerprint information, the token token, and the MAC address of the terminal, and the authentication server determines whether the terminal can continue to access the network according to the information, and the router periodically Ask the authentication server if the MAC is available. If not, reset the MAC to redirect to the authentication page once the network is accessed.
实施例一:Embodiment 1:
本实施例将描述AC控制器与认证服务器分离,即处于不同设备的情况。This embodiment will describe the case where the AC controller is separated from the authentication server, that is, in the case of different devices.
本实施例假定实施的环境下已有既有的室内地图及其位置指纹样本库。This embodiment assumes that there is an existing indoor map and its location fingerprint sample library in the implemented environment.
AC控制器的初始配置:保存一个MAC地址列表,该MAC地址列表设置成若从终端收到报文源MAC地址在MAC地址列表中,允许该终端访问网络;而若从终端收到报文源MAC地址不在MAC地址列表中,将报文重定向至认证服务器,实现方法可首先利用iptables规则,将该报文做目的网络地址转换(Destination Network Address Translation,简称为DNAT)跳转至本地处理进程,再由本地处理进程将该请求重定向至认证服务器,并且在
重定向的链接中携带接入控制器(Access Controller,简称为AC)的相关信息。为MAC地址列表中的MAC地址设置有效期,为了方便管理,对网络管理员或常用客户的终端的MAC地址,可设置为无限期永久访问,即不参与基于位置的认证;对于普通的MAC地址,设置生命周期为相对较短的时间,比如5分钟。Initial configuration of the AC controller: save a list of MAC addresses, the MAC address list is set to allow the terminal to access the network if the source MAC address of the message is received from the terminal, and the source of the message is received from the terminal. The MAC address is not in the MAC address list, and the packet is redirected to the authentication server. The implementation method can first use the iptables rule to perform the destination network address translation (DNAT) to the local processing process. , the local processing process redirects the request to the authentication server, and
The redirected link carries information about the Access Controller (AC). Set the validity period for the MAC address in the MAC address list. For the convenience of management, the MAC address of the network administrator or the terminal of the common customer can be set to be indefinitely permanent access, that is, not participating in location-based authentication; for ordinary MAC addresses, Set the life cycle to a relatively short time, such as 5 minutes.
图8是根据本发明实施例一的路由器/AC控制器与认证服务器分离情况下的交互流程图,如图8所示,该流程包括如下步骤:FIG. 8 is a flowchart of interaction between a router/AC controller and an authentication server according to the first embodiment of the present invention. As shown in FIG. 8, the process includes the following steps:
步骤S802,终端连入Wi-Fi网络后发出任意的一个HTTP请求。Step S802, the terminal sends an arbitrary HTTP request after connecting to the Wi-Fi network.
步骤S804,AC控制器判断报文源MAC是否在允许访问网络的MAC地址列表中,若该MAC不在允许访问网络的MAC地址列表之中,即未经过认证,则向终端返回包括重定向的地址的响应,所述包括重定向的地址的响应可为:超文本传输协议(Hyper Text Transfer Protocol,简称为HTTP)状态码,以及AC控制器的相关信息:包括AC控制器的标识(本实施例中以AC控制器的MAC地址作为标识),AC控制器接收令牌的地址(端口的IP地址和端口)、终端的MAC地址信息等,例如,最终终端将访问的目的地址为:http://auth-server/index&&gwid=00:d0:d0:00:00:01&&gwip=192.168.1.1&&gwport=8080&&client=00:d0:d0:00:00:0A。Step S804, the AC controller determines whether the source MAC address of the packet is in the MAC address list of the network that is allowed to access, and if the MAC address is not in the MAC address list of the network that is allowed to access, that is, if the MAC address is not authenticated, the address including the redirected address is returned to the terminal. The response of the address including the redirected address may be: Hypertext Transfer Protocol (HTTP) status code, and related information of the AC controller: including the identifier of the AC controller (this embodiment) The AC controller receives the MAC address of the AC controller as the identifier. The AC controller receives the address of the token (the IP address and port of the port) and the MAC address information of the terminal. For example, the destination address that the terminal will access is: http:/ /auth-server/index&&gwid=00:d0:d0:00:00:01&&gwip=192.168.1.1&&gwport=8080&&client=00:d0:d0:00:00:0A.
步骤S806,终端向认证服务器发送请求。Step S806, the terminal sends a request to the authentication server.
步骤S808,认证服务器收到终端的请求后,提取步骤S804中终端传来的参数并存储终端MAC与AC控制器信息的对应关系,向终端返回包含一个隐含的form表单的页面,该form表单的目的地址例如:http://auth-server/auth,用于终端向认证服务器发送其当前Wi-Fi信号携带的位置指纹信息,类似于基于短信的上网认证时被输入短信验证码的form表单,而本方案基于位置认证,无需用户手工输入数据,由终端自行采集数据。Step S808, after receiving the request of the terminal, the authentication server extracts the parameter transmitted by the terminal in step S804 and stores the correspondence between the terminal MAC and the AC controller information, and returns a page containing an implicit form form to the terminal, the form form The destination address is, for example, http://auth-server/auth, which is used by the terminal to send the location fingerprint information carried by the current Wi-Fi signal to the authentication server, similar to the form form that is input with the SMS verification code when the short message is authenticated based on the short message. The solution is based on location authentication, and the user does not need to manually input data, and the terminal collects data by itself.
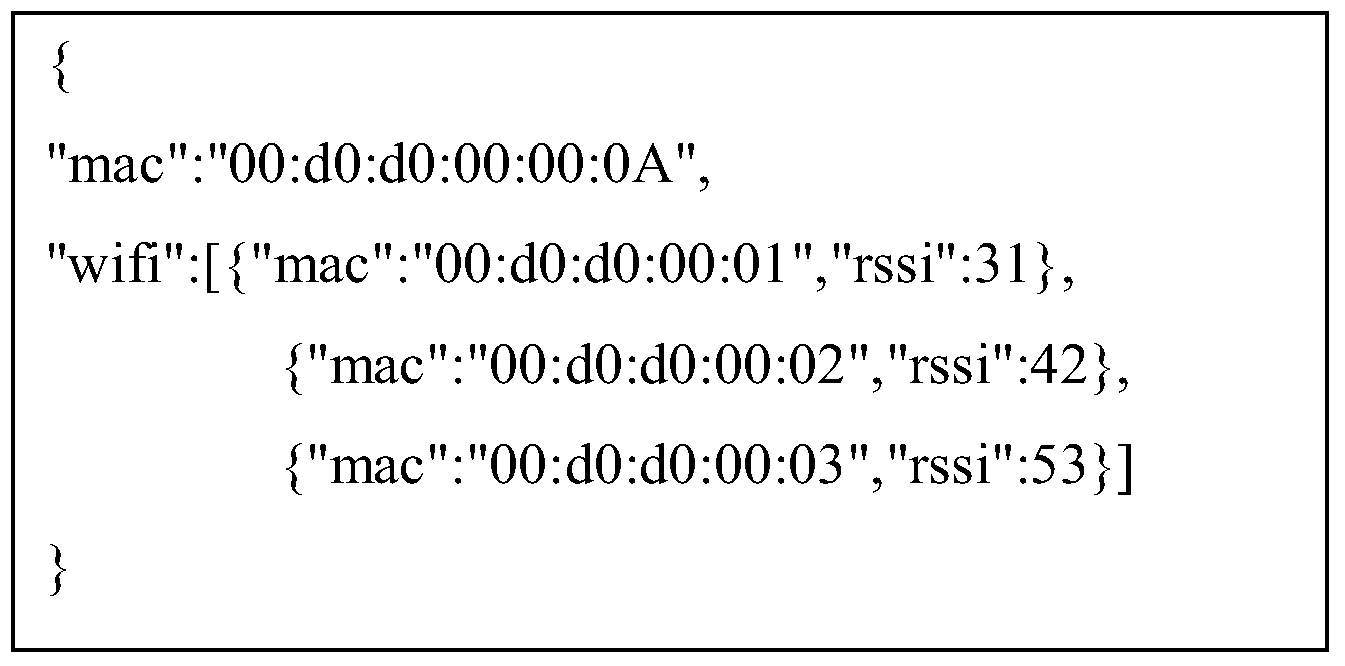
步骤S810,客户端(即,上述的终端)加载认证服务器返回的web页面后,将收集到的Wi-Fi信号携带的位置指纹信息发送到步骤S804中向终端返回的包括重定向的地址的响应中的地址http://auth-server/auth:用JSON格式(JavaScript Object Notation,是一种轻量级的数据交换格式)描述如下:
Step S810, after the client (ie, the terminal) loads the web page returned by the authentication server, the location fingerprint information carried by the collected Wi-Fi signal is sent to the response including the redirected address returned to the terminal in step S804. The address in http://auth-server/auth: is described in JSON format (JavaScript Object Notation, a lightweight data exchange format) as follows:
其中rssi为Wi-Fi信号的信号强度,一般表示为负值,单位为dbm,值越小代表信号强度越大,为了简洁,此处用正数表示,省略了单位。Where rssi is the signal strength of the Wi-Fi signal, generally expressed as a negative value, the unit is dbm. The smaller the value, the greater the signal strength. For the sake of brevity, the positive number is used here, and the unit is omitted.
步骤S812,认证服务器对收到的Wi-Fi信号携带的位置指纹信息进行判断,若满足预设约束条件,则根据终端的MAC查询出其对应的网关信息,生成重定向地址发送到客户端,在重定向的地址中包含有用于表示验证成功的令牌token以及生命周期,如http://192.168.1.1:8080&&token=ezak102s&&lifetime=300,其中300为该令牌token的生命周期,AC控制器应在300秒之后向服务器询问是否仍然有效。判断Wi-Fi等信号携带的位置指纹信息表征的位置是否在区域内的方法:首先根据Wi-Fi信号携带的位置指纹信息查找到最匹配的位置,然后可通过射线法判断是否在预设的多边形(区域边缘形成的点连线形成一个多边形):从被判断的点向x轴发射一条射线,如果射线与多边形的边有偶数次相交,那么点不在多边形内;奇数次相交,那么点在多边形内。Step S812: The authentication server determines the location fingerprint information carried by the received Wi-Fi signal. If the preset constraint condition is met, the gateway information of the terminal is used to query the corresponding gateway information, and a redirect address is generated and sent to the client. The redirected address contains a token token and a life cycle for indicating successful authentication, such as http://192.168.1.1:8080&&token=ezak102s&&lifetime=300, where 300 is the lifetime of the token token, and the AC controller should After 300 seconds, ask the server if it is still valid. A method for determining whether a location represented by a location fingerprint information carried by a signal such as Wi-Fi is in an area: first, finding a location that matches the location according to the location fingerprint information carried by the Wi-Fi signal, and then determining whether it is preset by a ray method Polygon (the line formed by the edge of the area forms a polygon): emits a ray from the point being judged to the x-axis. If the ray intersects the edge of the polygon an even number of times, then the point is not in the polygon; if the odd number intersects, then the point is Inside the polygon.
步骤S814,终端将收到的令牌token发送给AC控制器。Step S814, the terminal sends the received token token to the AC controller.
步骤S816,AC控制器从终端收到重定向的请求后,将终端的MAC地址、AC控制器标识、令牌token发送至认证服务器验证进行验证,用JSON格式描述如下:
Step S816: After receiving the redirection request from the terminal, the AC controller sends the MAC address, the AC controller identifier, and the token token of the terminal to the authentication server for verification, and is described in the JSON format as follows:
步骤S818,认证服务器检查终端的MAC地址和令牌token、AC控制器标识等是否匹配。认证服务器向AC控制器返回认证结果:0为匹配,-1为匹配失败。Step S818, the authentication server checks whether the MAC address of the terminal matches the token token, the AC controller identifier, and the like. The authentication server returns the authentication result to the AC controller: 0 is a match and -1 is a match failure.
步骤S820,如果验证匹配,AC控制器将终端的MAC地址加入允许访问网络的列表,且将步骤S816的重定向的请求重定向至认证服务器的心跳页面,例如http://auth-server/alive。Step S820, if the verification matches, the AC controller adds the MAC address of the terminal to the list of allowed access networks, and redirects the redirected request of step S816 to the heartbeat page of the authentication server, for example, http://auth-server/alive .
步骤S822,终端在使用网络过程中,一直保持心跳页面开启,定期向认证服务器反馈其当前Wi-Fi信号携带的位置指纹信息,以及令牌token。In step S822, the terminal keeps the heartbeat page open during the use of the network, and periodically feeds back to the authentication server the location fingerprint information carried by the current Wi-Fi signal and the token token.
心跳页面处理:若Wi-Fi信号携带的位置指纹信息表征的位置不在区域内,则认证服务器将该MAC地址对应的记录置为非法状态;若Wi-Fi信号携带的位置指纹信息表征的位置在区域内,则更新其生命周期。由于终端很可能处于移动状态,所以当发现其在区域外,并不立即停止,而是等待AC控制器去查询某MAC地址是否可以继续使用网络。
Heartbeat page processing: if the location of the location fingerprint information carried by the Wi-Fi signal is not in the area, the authentication server sets the record corresponding to the MAC address to an illegal state; if the location fingerprint information carried by the Wi-Fi signal is represented by the location Within the region, its life cycle is updated. Since the terminal is likely to be in a mobile state, when it is found that it is outside the area, it does not stop immediately, but waits for the AC controller to query whether a MAC address can continue to use the network.
步骤S824,AC控制器定期向认证服务器询问MAC列表中的MAC是否到期,若到期,则将其从MAC列表中删除。Step S824, the AC controller periodically queries the authentication server whether the MAC in the MAC list expires, and if it expires, deletes it from the MAC list.
步骤S826,认证服务器向AC控制器返回查询结果。Step S826, the authentication server returns a query result to the AC controller.
在整个认证过程中,终端总是客户端的角色,无需提供对外的服务接口;In the entire authentication process, the terminal is always the role of the client, and there is no need to provide an external service interface;
AC控制器需要提供一个接口,用于接收终端发送的令牌token验证请求;The AC controller needs to provide an interface for receiving a token token verification request sent by the terminal;
认证服务器需要提供三个接口:The authentication server needs to provide three interfaces:
接口1:用于接收未经认证的终端上线后被重定向的认证首页http://auth-server/index;Interface 1: used to receive the authentication home page http://auth-server/index that is redirected after the unauthenticated terminal goes online.
接口2:接收终端发起的验证请求:http://auth-server/auth;Interface 2: Receive the authentication request initiated by the terminal: http://auth-server/auth;
接口3:心跳接口用于接收AC控制器发起的、查询终端的MAC地址是否已经失效的请求:http://auth-server/alive。Interface 3: The heartbeat interface is used to receive a request from the AC controller to query whether the MAC address of the terminal has expired: http://auth-server/alive.
实施例二:Embodiment 2:
本实施例描述AC控制器与认证服务器在同一个设备中的方案,即在处理性能较强且具备一定存储能力的无线路由器上实现,操作系统可以Linux系统,或者基于openwrt(一种Linux系统)进行修改,这种方案中AC控制器与认证服务器之间的交互会更加简单,下面描述中统称为路由器。This embodiment describes a scheme in which an AC controller and an authentication server are in the same device, that is, implemented on a wireless router with strong processing performance and certain storage capability, and the operating system can be a Linux system or based on openwrt (a Linux system). To modify, the interaction between the AC controller and the authentication server in this scheme is simpler, and the following description is collectively referred to as a router.
在本实施例中假定没有既有的室内定位系统,也即没有室内地图,也就没有既有的位置指纹库,需要重新建立简化的位置样本库:通过携带能够通过Wi-Fi等方式访问网络的移动终端在设定的区域内外行进,在行进的过程中收集各位置的Wi-Fi信号/蓝牙信号等的标识和信息,每个位置都将会被标注为区域内或外,为了保证定位的效果,在区域边缘进行密集覆盖地标注Wi-Fi信号/蓝牙信号等的标记和信息,并且在区域内和区域外以距离稍大的间隔标注Wi-Fi信号/蓝牙信号等的标记和信息,以保证匹配效果。图9是根据本发明实施例的样本库和被验证点分别位于区域内和区域外的示意图。In this embodiment, it is assumed that there is no existing indoor positioning system, that is, there is no indoor map, and there is no existing location fingerprint database, and a simplified location sample library needs to be re-established: by carrying, the network can be accessed through Wi-Fi or the like. The mobile terminal travels inside and outside the set area, and collects identification and information of Wi-Fi signals/Bluetooth signals, etc. at each position during the process of traveling, and each position will be marked as inside or outside the area, in order to ensure positioning. The effect is to mark and information such as Wi-Fi signals/Bluetooth signals intensively at the edge of the area, and mark and information such as Wi-Fi signals/Bluetooth signals at a slightly larger distance in and outside the area. To ensure a matching effect. 9 is a schematic diagram of a sample library and verified points located within and outside a region, respectively, in accordance with an embodiment of the present invention.
图10是根据本发明实施例二的路由器/AC控制器与认证服务器在同一个设备中的情况下的交互流程图,如图10所示,该流程包括如下步骤:
10 is a flow chart of interaction between a router/AC controller and an authentication server in the same device according to Embodiment 2 of the present invention. As shown in FIG. 10, the process includes the following steps:
在路由器上通过iptables程序初始设置访问规则:保存一个MAC地址列表,若从终端收到的报文源MAC地址在MAC地址列表中,则可以正常访问网络,而若从终端收到的报文源MAC地址不在MAC地址列表中,将报文重定向至认证服务器,运行认证进程,本实施例中,因认证服务器和AC控制器是同一个设备,所以认证服务器的地址可用本地环回地址:127.0.0.1:8080.与实施例一相同的是,为方便管理,为MAC地址列表中的MAC地址分别设置生命周期,允许特殊地址可以不经过认证就能一直访问网络。Initially set the access rule on the router through the iptables program: save a list of MAC addresses. If the source MAC address of the packet received from the terminal is in the MAC address list, the network can be accessed normally, and if the source is received from the terminal. The MAC address is not in the MAC address list, and the packet is redirected to the authentication server to run the authentication process. In this embodiment, because the authentication server and the AC controller are the same device, the address of the authentication server can be used as the local loopback address: 127.0 .0.1:8080. As in the first embodiment, for the convenience of management, the life cycle is set for the MAC address in the MAC address list, allowing the special address to access the network without authentication.
步骤S1002,终端连接网络后发出任意的HTTP请求,例如,访问网址为www.xxx.com的网页。In step S1002, the terminal sends an arbitrary HTTP request after connecting to the network, for example, accessing a webpage with a website address of www.xxx.com.
步骤S1004,路由器根据终端MAC地址判断其是否已经过认证,若判断终端没有经过认证,则将报文重定向至本地进程127.0.0.1:8080以进行处理,在该进程中向终端返回包含一个隐含的form表单的页面,该form表单的目的地址为http://127.0.0.1:8080/auth,用于终端向认证服务器发送其当前位置,该页面将一直处于活动状态,并且定期自动向认证服务器发送位置信息。In step S1004, the router determines whether it has been authenticated according to the terminal MAC address. If it is determined that the terminal is not authenticated, the packet is redirected to the local process 127.0.0.1:8080 for processing, and the terminal returns a hidden in the process. The page containing the form form, the destination address of the form is http://127.0.0.1:8080/auth, which is used by the terminal to send its current location to the authentication server, the page will remain active, and the authentication will be automatically performed periodically. The server sends location information.
步骤S1006,客户端将收集到的Wi-Fi信号携带的指纹信息发送到步骤S1004中的目的地址,用JSON格式描述如下:In step S1006, the client sends the fingerprint information carried by the collected Wi-Fi signal to the destination address in step S1004, which is described in the JSON format as follows:
路由器将收到的MAC地址和信号强度等与样本库进行比较,以进行判断,判断的方法有多种,比如欧式距离方法,极大似然概率法,支持向量机算法等等,如果在样本库中查找到的最为匹配的条目属于区域内,则认为该
位置满足预设约束条件,将该MAC地址加入前述MAC地址列表,更新其生命周期;如果不满足预设约束条件,则从MAC地址列表中将该MAC地址去除。The router compares the received MAC address and signal strength with the sample library to make judgments. There are various methods for judging, such as the Euclidean distance method, the maximum likelihood probability method, the support vector machine algorithm, etc., if the sample is in the sample. If the most matching entry found in the library belongs to the zone, then the
The location meets the preset constraint condition, and the MAC address is added to the foregoing MAC address list to update its life cycle; if the preset constraint is not met, the MAC address is removed from the MAC address list.
步骤S1008,路由器定期扫描MAC地址列表,将生命周期已经结束的MAC地址删除,使其下一次访问网络时,继续被重定向至认证页面。In step S1008, the router periodically scans the MAC address list, and deletes the MAC address whose lifetime has been completed, so that when the next time the network is accessed, the router continues to be redirected to the authentication page.
在上述实施例中,由于AC控制器和认证服务器都在路由器中实现,终端和路由器之间需要两个接口:一是当未经过认证的终端接入后被跳转到的重定向的地址;二是验证接口,在具体实施过程中,可以使用同一个地址,入口使用get指令动作,验证则使用post指令动作进行区分。In the above embodiment, since both the AC controller and the authentication server are implemented in the router, two interfaces are required between the terminal and the router: one is a redirected address that is redirected to when the unauthenticated terminal accesses; The second is to verify the interface. In the specific implementation process, the same address can be used, the entry uses the get instruction action, and the verification uses the post instruction action to distinguish.
需要说明的是,上述各个模块是可以通过软件或硬件来实现的,对于后者,可以通过以下方式实现,但不限于此:上述模块均位于同一处理器中;或者,上述模块分别位于多个处理器中。It should be noted that each of the above modules may be implemented by software or hardware. For the latter, the foregoing may be implemented by, but not limited to, the foregoing modules are all located in the same processor; or, the modules are located in multiple In the processor.
本发明的实施例还提供了一种存储介质。可选地,在本实施例中,上述存储介质可以被设置为存储用于执行以下步骤的程序代码:Embodiments of the present invention also provide a storage medium. Optionally, in the embodiment, the foregoing storage medium may be configured to store program code for performing the following steps:
S1,向认证服务器发送终端的位置信息;S1. Send location information of the terminal to the authentication server.
S2,接收该认证服务器根据位置信息返回的判断结果,其中该判断结果用于标识终端是否处于预定网络的目标范围内;S2, receiving a determination result returned by the authentication server according to the location information, where the determination result is used to identify whether the terminal is within a target range of the predetermined network;
S3,根据判断结果确定是否允许终端接入上述预定网络。S3. Determine, according to the determination result, whether the terminal is allowed to access the predetermined network.
可选地,存储介质还被设置为存储用于执行以下步骤的程序代码:Optionally, the storage medium is further arranged to store program code for performing the following steps:
S1,接收终端的位置信息;S1. Receive location information of the terminal.
S2,根据该位置信息判断终端是否处于预定网络的目标范围内;S2, determining, according to the location information, whether the terminal is within a target range of the predetermined network;
S3,根据判断结果控制终端接入上述预定网络。S3. Control the terminal to access the predetermined network according to the judgment result.
可选地,在本实施例中,上述存储介质可以包括但不限于:U盘、只读存储器(Read-Only Memory,简称为ROM)、随机存取存储器(Random Access Memory,简称为RAM)、移动硬盘、磁碟或者光盘等各种可以存储程序代码的介质。Optionally, in the embodiment, the foregoing storage medium may include, but is not limited to, a USB flash drive, a Read-Only Memory (ROM), and a Random Access Memory (RAM). A variety of media that can store program code, such as a hard disk, a disk, or an optical disk.
可选地,本实施例中的具体示例可以参考上述实施例及可选实施方式中
所描述的示例,本实施例在此不再赘述。Optionally, specific examples in this embodiment may refer to the foregoing embodiment and the optional implementation manner.
The described examples are not described herein again.
显然,本领域的技术人员应该明白,上述的本申请的各模块或各步骤可以用通用的计算装置来实现,它们可以集中在单个的计算装置上,或者分布在多个计算装置所组成的网络上,可选地,它们可以用计算装置可执行的程序代码来实现,从而,可以将它们存储在存储装置中由计算装置来执行,并且在某些情况下,可以以不同于此处的顺序执行所示出或描述的步骤,或者将它们分别制作成各个集成电路模块,或者将它们中的多个模块或步骤制作成单个集成电路模块来实现。这样,本申请不限制于任何特定的硬件和软件结合。Obviously, those skilled in the art should understand that the above modules or steps of the present application can be implemented by a general computing device, which can be concentrated on a single computing device or distributed in a network composed of multiple computing devices. Alternatively, they may be implemented by program code executable by the computing device such that they may be stored in the storage device by the computing device and, in some cases, may be different from the order herein. The steps shown or described are performed, or they are separately fabricated into individual integrated circuit modules, or a plurality of modules or steps thereof are fabricated as a single integrated circuit module. Thus, the application is not limited to any particular combination of hardware and software.
以上所述仅为本申请的可选实施例而已,并不用于限制本申请,对于本领域的技术人员来说,本申请可以有各种更改和变化。凡在本申请的精神和原则之内,所作的任何修改、等同替换、改进等,均应包含在本申请的保护范围之内。The above description is only an optional embodiment of the present application, and is not intended to limit the present application, and various changes and modifications may be made to the present application. Any modifications, equivalent substitutions, improvements, etc. made within the spirit and principles of this application are intended to be included within the scope of the present application.
本领域普通技术人员可以理解上述方法中的全部或部分步骤可通过程序来指令相关硬件(例如处理器)完成,所述程序可以存储于计算机可读存储介质中,如只读存储器、磁盘或光盘等。可选地,上述实施例的全部或部分步骤也可以使用一个或多个集成电路来实现。相应地,上述实施例中的各模块/单元可以采用硬件的形式实现,例如通过集成电路来实现其相应功能,也可以采用软件功能模块的形式实现,例如通过处理器执行存储于存储器中的程序/指令来实现其相应功能。本发明实施例不限制于任何特定形式的硬件和软件的结合。One of ordinary skill in the art will appreciate that all or a portion of the above steps may be performed by a program to instruct related hardware, such as a processor, which may be stored in a computer readable storage medium, such as a read only memory, disk or optical disk. Wait. Alternatively, all or part of the steps of the above embodiments may also be implemented using one or more integrated circuits. Correspondingly, each module/unit in the above embodiment may be implemented in the form of hardware, for example, by implementing an integrated circuit to implement its corresponding function, or may be implemented in the form of a software function module, for example, executing a program stored in the memory by a processor. / instruction to achieve its corresponding function. Embodiments of the invention are not limited to any specific form of combination of hardware and software.
通过本申请的方案,采用向认证服务器发送终端的位置信息;接收所述认证服务器根据所述位置信息返回的判断结果,其中所述判断结果用于标识所述终端是否处于预定网络的目标范围内;根据所述判断结果确定是否允许所述终端接入所述预定网络,解决了相关技术中存在的网络接入控制效率低的问题,进而达到了提高网络接入控制效率的效果。
Through the solution of the present application, the location information of the terminal is sent to the authentication server, and the determination result returned by the authentication server according to the location information is received, where the determination result is used to identify whether the terminal is within the target range of the predetermined network. And determining, according to the determination result, whether the terminal is allowed to access the predetermined network, and solving the problem that the network access control efficiency in the related art is low, thereby achieving an effect of improving network access control efficiency.
Claims (12)
- 一种接入网络的处理方法,包括:A method for processing an access network, comprising:向认证服务器发送终端的位置信息;Sending location information of the terminal to the authentication server;接收所述认证服务器根据所述位置信息返回的判断结果,其中,所述判断结果用于标识所述终端是否处于预定网络的目标范围内;Receiving a determination result returned by the authentication server according to the location information, where the determination result is used to identify whether the terminal is within a target range of a predetermined network;根据所述判断结果确定是否允许所述终端接入所述预定网络。Determining whether the terminal is allowed to access the predetermined network according to the judgment result.
- 根据权利要求1所述的方法,其中,所述位置信息包括以下信息至少之一:The method of claim 1, wherein the location information comprises at least one of the following information:所述终端检测到的Wi-Fi信号携带的Wi-Fi信号发射端的媒体接入控制MAC地址和所述终端检测到的Wi-Fi信号的信号强度、所述终端检测到的蓝牙信号携带的蓝牙信号发射端的地址和所述终端检测到的蓝牙信号的信号强度。The media access control MAC address of the Wi-Fi signal transmitting end carried by the Wi-Fi signal detected by the terminal, the signal strength of the Wi-Fi signal detected by the terminal, and the Bluetooth carried by the terminal detecting the Bluetooth signal The address of the signal transmitting end and the signal strength of the Bluetooth signal detected by the terminal.
- 根据权利要求1所述的方法,其中,当所述判断结果为所述终端处于所述目标范围内时,所述根据所述判断结果确定是否允许所述终端接入所述预定网络的步骤包括:The method according to claim 1, wherein when the determination result is that the terminal is in the target range, the step of determining whether to allow the terminal to access the predetermined network according to the determination result comprises: :获取所述判断结果中携带的令牌信息;Obtaining token information carried in the judgment result;依据所述令牌信息通过路由器接入所述预定网络。Accessing the predetermined network through a router according to the token information.
- 一种接入网络的处理方法,包括:A method for processing an access network, comprising:接收终端的位置信息;Receiving location information of the terminal;根据所述位置信息判断所述终端是否处于预定网络的目标范围内;Determining, according to the location information, whether the terminal is within a target range of a predetermined network;根据判断结果控制所述终端接入所述预定网络。Controlling, by the determination result, the terminal accessing the predetermined network.
- 根据权利要求4所述的方法,其中,所述根据所述判断结果控制所述终端接入所述预定网络的步骤包括:The method according to claim 4, wherein the step of controlling the terminal to access the predetermined network according to the determination result comprises:当所述判断结果为所述终端位于所述目标范围内时,向所述终端发送令牌信息,其中,所述令牌信息用于所述终端通过路由器接入所述预定网络;When the result of the determination is that the terminal is located in the target range, sending token information to the terminal, where the token information is used by the terminal to access the predetermined network through a router;当所述判断结果为所述终端位于所述目标范围外时,向所述终端发送拒绝所述终端接入所述预定网络的信息。 And when the determining result is that the terminal is located outside the target range, sending, to the terminal, information that denies the terminal accessing the predetermined network.
- 根据权利要求5所述的方法,所述当所述判断结果为所述终端位于所述目标范围内时,向所述终端发送所述令牌信息的步骤之后,所述处理方法还包括:The method according to claim 5, after the step of transmitting the token information to the terminal when the determining result is that the terminal is located in the target range, the processing method further includes:接收所述路由器发送的预定令牌信息,其中,所述预定令牌信息为所述路由器在接收到终端发送的所述预定令牌信息后发送的;Receiving predetermined token information sent by the router, where the predetermined token information is sent by the router after receiving the predetermined token information sent by the terminal;验证所述预定令牌信息与发送给所述终端的令牌信息是否一致;Verifying whether the predetermined token information is consistent with the token information sent to the terminal;若验证结果为一致,将允许所述终端接入所述预定网络的允许信息发送给所述路由器。If the verification result is consistent, the terminal allows access information of the predetermined network to be sent to the router.
- 一种接入网络的处理装置,包括:A processing device for accessing a network, comprising:发送模块,设置成向认证服务器发送终端的位置信息;a sending module, configured to send location information of the terminal to the authentication server;第一接收模块,设置成接收所述认证服务器根据所述位置信息返回的判断结果,其中所述判断结果用于标识所述终端是否处于预定网络的目标范围内;a first receiving module, configured to receive a determination result returned by the authentication server according to the location information, where the determining result is used to identify whether the terminal is within a target range of a predetermined network;处理模块,设置成根据所述判断结果确定是否允许所述终端接入所述预定网络。And a processing module, configured to determine, according to the determination result, whether the terminal is allowed to access the predetermined network.
- 根据权利要求7所述的装置,其中,所述位置信息包括以下信息至少之一:The apparatus of claim 7, wherein the location information comprises at least one of the following information:所述终端检测到的Wi-Fi信号携带的Wi-Fi信号发射端的媒体接入控制MAC地址和所述终端检测到的Wi-Fi信号的信号强度、所述终端检测到的蓝牙信号携带的蓝牙信号发射端的地址和所述终端检测到的蓝牙信号的信号强度。The media access control MAC address of the Wi-Fi signal transmitting end carried by the Wi-Fi signal detected by the terminal, the signal strength of the Wi-Fi signal detected by the terminal, and the Bluetooth carried by the terminal detecting the Bluetooth signal The address of the signal transmitting end and the signal strength of the Bluetooth signal detected by the terminal.
- 根据权利要求7所述的装置,其中,所述处理模块包括:The apparatus of claim 7 wherein said processing module comprises:获取单元,设置成当所述判断结果为所述终端处于所述目标范围内时,获取所述判断结果中携带的令牌信息;An acquiring unit, configured to acquire token information carried in the determination result when the determining result is that the terminal is in the target range;接入单元,设置成依据所述令牌信息通过路由器接入所述预定网络。The access unit is configured to access the predetermined network through the router according to the token information.
- 一种接入网络的处理装置,包括:A processing device for accessing a network, comprising:第二接收模块,设置成接收终端的位置信息; a second receiving module, configured to receive location information of the terminal;判断模块,设置成根据所述位置信息判断所述终端是否处于预定网络的目标范围内;a determining module, configured to determine, according to the location information, whether the terminal is within a target range of a predetermined network;控制模块,设置成根据判断结果控制所述终端接入所述预定网络。And a control module, configured to control the terminal to access the predetermined network according to the determination result.
- 根据权利要求10所述的装置,其中,所述控制模块包括:The apparatus of claim 10 wherein said control module comprises:第一发送单元,设置成当所述判断结果为所述终端位于所述目标范围内时,向所述终端发送令牌信息,其中,所述令牌信息用于所述终端通过路由器接入所述预定网络;a first sending unit, configured to send token information to the terminal when the determining result is that the terminal is located in the target range, where the token information is used by the terminal to access through a router Predetermined network;第二发送单元,设置成当所述判断结果为所述终端位于所述目标范围外时,向所述终端发送拒绝所述终端接入所述预定网络的信息。And a second sending unit, configured to send, to the terminal, information that denies the terminal accessing the predetermined network when the determining result is that the terminal is located outside the target range.
- 根据权利要求11所述的装置,所述处理装置还包括:The apparatus of claim 11 further comprising:接收单元,设置成接收所述路由器发送的预定令牌信息,其中,所述预定令牌信息为所述路由器在接收到终端发送的所述预定令牌信息后发送的;a receiving unit, configured to receive predetermined token information sent by the router, where the predetermined token information is sent by the router after receiving the predetermined token information sent by the terminal;验证单元,设置成验证所述预定令牌信息与发送给所述终端的令牌信息是否一致;a verification unit, configured to verify whether the predetermined token information is consistent with token information sent to the terminal;第三发送单元,设置成若所述验证单元的验证结果为一致,将允许所述终端接入所述预定网络的允许信息发送给所述路由器。 And a third sending unit, configured to: if the verification result of the verification unit is consistent, allow permission information that the terminal accesses the predetermined network to be sent to the router.
Applications Claiming Priority (2)
| Application Number | Priority Date | Filing Date | Title |
|---|---|---|---|
| CN201510257791.0 | 2015-05-19 | ||
| CN201510257791.0A CN106162549A (en) | 2015-05-19 | 2015-05-19 | The processing method and processing device of access network |
Publications (1)
| Publication Number | Publication Date |
|---|---|
| WO2016184380A1 true WO2016184380A1 (en) | 2016-11-24 |
Family
ID=57319437
Family Applications (1)
| Application Number | Title | Priority Date | Filing Date |
|---|---|---|---|
| PCT/CN2016/082354 WO2016184380A1 (en) | 2015-05-19 | 2016-05-17 | Processing method and device for network access |
Country Status (2)
| Country | Link |
|---|---|
| CN (1) | CN106162549A (en) |
| WO (1) | WO2016184380A1 (en) |
Cited By (3)
| Publication number | Priority date | Publication date | Assignee | Title |
|---|---|---|---|---|
| CN112153645A (en) * | 2019-06-28 | 2020-12-29 | 北京奇虎科技有限公司 | Anti-network-rubbing method and device and router |
| CN114268955A (en) * | 2021-12-23 | 2022-04-01 | 智小途(上海)数字科技有限公司 | Cognitive matching method and system for wireless communication network node signals |
| CN115038082A (en) * | 2022-06-08 | 2022-09-09 | 上海百功半导体有限公司 | Safety internet access control system and method for optical communication equipment |
Families Citing this family (11)
| Publication number | Priority date | Publication date | Assignee | Title |
|---|---|---|---|---|
| CN106911565B (en) * | 2017-03-01 | 2021-03-16 | 常州三泰科技有限公司 | Method and system for safely processing information data |
| CN107241348A (en) * | 2017-07-13 | 2017-10-10 | 上海斐讯数据通信技术有限公司 | Alarming method and system that a kind of router is logged in |
| CN107613498A (en) * | 2017-10-26 | 2018-01-19 | 上海与德科技有限公司 | A kind of connection method of network communication and device |
| CN108566440B (en) * | 2018-06-26 | 2021-06-15 | 上海尚往网络科技有限公司 | Network connection method, equipment and storage medium |
| CN109246854A (en) * | 2018-09-12 | 2019-01-18 | 苏州汇恒网络科技有限公司 | A kind of method, apparatus and the network equipment of automatic replacement network equipment information |
| CN110213769B (en) * | 2019-06-10 | 2022-11-25 | 平安科技(深圳)有限公司 | Intranet access method and related device |
| CN112887968B (en) * | 2019-11-29 | 2023-11-17 | 中兴通讯股份有限公司 | Network equipment management method, device, network management equipment and medium |
| CN113068113A (en) * | 2019-12-31 | 2021-07-02 | 佛山市云米电器科技有限公司 | Network distribution method, network distribution equipment and computer readable storage medium |
| CN114339601B (en) * | 2020-10-09 | 2023-12-26 | 美的集团股份有限公司 | Automatic network distribution method and device based on UWB |
| CN113741330A (en) * | 2021-09-08 | 2021-12-03 | 珠海格力电器股份有限公司 | Networking safety verification system and method based on PLC power line communication technology |
| CN115396982B (en) * | 2022-07-13 | 2024-08-27 | 微网优联科技(成都)有限公司 | Method and device for preventing network from being rubbed based on WiFi6 router |
Citations (4)
| Publication number | Priority date | Publication date | Assignee | Title |
|---|---|---|---|---|
| CN1673925A (en) * | 2004-03-24 | 2005-09-28 | 美国博通公司 | Global positioning system (gps) based secure access |
| EP2648126A1 (en) * | 2012-04-05 | 2013-10-09 | LG CNS Co., Ltd. | Method of authenticating user, server and mobile terminal performing the same |
| CN104159271A (en) * | 2013-05-15 | 2014-11-19 | 华为技术有限公司 | Boundary control method and system, and access controller |
| CN104581830A (en) * | 2014-12-23 | 2015-04-29 | 大唐移动通信设备有限公司 | Access method and equipment of terminal equipment |
Family Cites Families (4)
| Publication number | Priority date | Publication date | Assignee | Title |
|---|---|---|---|---|
| US8620269B2 (en) * | 2007-12-31 | 2013-12-31 | Honeywell International Inc. | Defining a boundary for wireless network using physical access control systems |
| CN101296240B (en) * | 2008-06-20 | 2012-03-28 | 中国移动通信集团北京有限公司 | Authentication method and system for access to wireless network, and authentication server |
| CN101582769B (en) * | 2009-07-03 | 2012-07-04 | 杭州华三通信技术有限公司 | Authority setting method of user access network and equipment |
| CN101668293A (en) * | 2009-10-21 | 2010-03-10 | 杭州华三通信技术有限公司 | Control method and system of network access authority in WLAN |
-
2015
- 2015-05-19 CN CN201510257791.0A patent/CN106162549A/en not_active Withdrawn
-
2016
- 2016-05-17 WO PCT/CN2016/082354 patent/WO2016184380A1/en active Application Filing
Patent Citations (4)
| Publication number | Priority date | Publication date | Assignee | Title |
|---|---|---|---|---|
| CN1673925A (en) * | 2004-03-24 | 2005-09-28 | 美国博通公司 | Global positioning system (gps) based secure access |
| EP2648126A1 (en) * | 2012-04-05 | 2013-10-09 | LG CNS Co., Ltd. | Method of authenticating user, server and mobile terminal performing the same |
| CN104159271A (en) * | 2013-05-15 | 2014-11-19 | 华为技术有限公司 | Boundary control method and system, and access controller |
| CN104581830A (en) * | 2014-12-23 | 2015-04-29 | 大唐移动通信设备有限公司 | Access method and equipment of terminal equipment |
Cited By (3)
| Publication number | Priority date | Publication date | Assignee | Title |
|---|---|---|---|---|
| CN112153645A (en) * | 2019-06-28 | 2020-12-29 | 北京奇虎科技有限公司 | Anti-network-rubbing method and device and router |
| CN114268955A (en) * | 2021-12-23 | 2022-04-01 | 智小途(上海)数字科技有限公司 | Cognitive matching method and system for wireless communication network node signals |
| CN115038082A (en) * | 2022-06-08 | 2022-09-09 | 上海百功半导体有限公司 | Safety internet access control system and method for optical communication equipment |
Also Published As
| Publication number | Publication date |
|---|---|
| CN106162549A (en) | 2016-11-23 |
Similar Documents
| Publication | Publication Date | Title |
|---|---|---|
| WO2016184380A1 (en) | Processing method and device for network access | |
| US11552954B2 (en) | Private cloud control | |
| US10097546B2 (en) | Authentication of a user device using traffic flow information | |
| JP6506871B2 (en) | System and method for wireless access point security and quality assessment | |
| CN107005442B (en) | Method and apparatus for remote access | |
| KR102581559B1 (en) | Log access point detection using multi-path verification | |
| US9763099B2 (en) | System and method for security and quality assessment of wireless access points | |
| US8594632B1 (en) | Device to-device (D2D) discovery without authenticating through cloud | |
| US20180212970A1 (en) | Distributed authentication for internet-of-things resources | |
| CN104144163B (en) | Auth method, apparatus and system | |
| WO2014113882A1 (en) | Computer system and method for indoor geo-fencing and access control | |
| CN109167780B (en) | Method, device, system and medium for controlling resource access | |
| CN109937608B (en) | Method and system for collecting sensor data from a sensor device | |
| US20170034164A1 (en) | Multifactor authentication for mail server access | |
| US20150103678A1 (en) | Identification of user home system in a distributed environment | |
| US20170295167A1 (en) | Registering a smart device with a registration device using a multicast protocol | |
| WO2017219748A1 (en) | Method and device for access permission determination and page access | |
| US11632366B1 (en) | Multi-device authentication | |
| US9398002B2 (en) | Secure communication during provisioning of a mobile device to stream media content from a media client | |
| EP3910978B1 (en) | Method for detecting fake device and wireless device care apparatus | |
| JP7140845B2 (en) | Devices and methods for securing network connections | |
| WO2018014555A1 (en) | Data transmission control method and apparatus |
Legal Events
| Date | Code | Title | Description |
|---|---|---|---|
| 121 | Ep: the epo has been informed by wipo that ep was designated in this application |
Ref document number: 16795867 Country of ref document: EP Kind code of ref document: A1 |
|
| NENP | Non-entry into the national phase |
Ref country code: DE |
|
| 122 | Ep: pct application non-entry in european phase |
Ref document number: 16795867 Country of ref document: EP Kind code of ref document: A1 |