US8090763B2 - Method and apparatus for cross-domain communication using designated response processing page - Google Patents
Method and apparatus for cross-domain communication using designated response processing page Download PDFInfo
- Publication number
- US8090763B2 US8090763B2 US12/583,362 US58336209A US8090763B2 US 8090763 B2 US8090763 B2 US 8090763B2 US 58336209 A US58336209 A US 58336209A US 8090763 B2 US8090763 B2 US 8090763B2
- Authority
- US
- United States
- Prior art keywords
- domain
- request
- page
- data
- response
- Prior art date
- Legal status (The legal status is an assumption and is not a legal conclusion. Google has not performed a legal analysis and makes no representation as to the accuracy of the status listed.)
- Ceased, expires
Links
Images
Classifications
-
- H—ELECTRICITY
- H04—ELECTRIC COMMUNICATION TECHNIQUE
- H04L—TRANSMISSION OF DIGITAL INFORMATION, e.g. TELEGRAPHIC COMMUNICATION
- H04L63/00—Network architectures or network communication protocols for network security
- H04L63/20—Network architectures or network communication protocols for network security for managing network security; network security policies in general
-
- G—PHYSICS
- G06—COMPUTING; CALCULATING OR COUNTING
- G06F—ELECTRIC DIGITAL DATA PROCESSING
- G06F16/00—Information retrieval; Database structures therefor; File system structures therefor
- G06F16/90—Details of database functions independent of the retrieved data types
- G06F16/95—Retrieval from the web
- G06F16/958—Organisation or management of web site content, e.g. publishing, maintaining pages or automatic linking
- G06F16/972—Access to data in other repository systems, e.g. legacy data or dynamic Web page generation
-
- H—ELECTRICITY
- H04—ELECTRIC COMMUNICATION TECHNIQUE
- H04L—TRANSMISSION OF DIGITAL INFORMATION, e.g. TELEGRAPHIC COMMUNICATION
- H04L67/00—Network arrangements or protocols for supporting network services or applications
- H04L67/01—Protocols
- H04L67/02—Protocols based on web technology, e.g. hypertext transfer protocol [HTTP]
-
- H—ELECTRICITY
- H04—ELECTRIC COMMUNICATION TECHNIQUE
- H04L—TRANSMISSION OF DIGITAL INFORMATION, e.g. TELEGRAPHIC COMMUNICATION
- H04L67/00—Network arrangements or protocols for supporting network services or applications
- H04L67/01—Protocols
- H04L67/10—Protocols in which an application is distributed across nodes in the network
Definitions
- the present invention relates generally to the field of network technology and more particularly to method, system and device for cross-domain communication.
- Existing browser software such as Internet Explorer or Firefox provides a security isolation mechanism based on network domains to prevent programs from different websites from accessing each other's data and causing visitor's private data to be misappropriated from one website to another.
- Some large web platforms can include many different domain names or different websites that are in trust relationships with each other and often need to exchange data and service among different websites.
- Another technique for cross-domain communication involves decreasing the client browser security setting to allow for cross-domain visits. Decreasing the security standard, however, makes the client more vulnerable to exploits by malicious websites.
- Another technique involves URL jumping between different websites, where one website requests a page in another domain and sends information in the form of URL parameters and the other domain returns information by redirecting the browser to the web page in the requester's domain and sending information in the form of URL parameters.
- URL jumping is used to communicate between different websites, the servers must deal with greatly increased load and efficiency is decreased.
- the technique also leads to security problems since the data information transferred via the URL is in plain view in the address bar of browser. Further, the technique cannot transfer large amounts of data because of the limit on the URL length.
- Another technique uses cross-domain scripting citation.
- a web page in a domain uses the ⁇ script> label to reference Javascript (JS) file contents of another domain and transfers the data in the form of URL parameters.
- the JS file of the other domain can compile script freely to send the data directly to the current web page.
- This technique tends to be complex since new script needs to be generated in each communication. Further, the data of one domain would be completely exposed to the script of another and can be easily misappropriated.
- FIG. 1 is a block diagram illustrating an embodiment of a system that supports cross-domain communication.
- FIG. 2A is a flowchart illustrating an embodiment of a process for cross-domain communication.
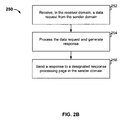
- FIG. 2B is a flowchart illustrating an embodiment of a process for cross-domain communication.
- FIG. 3 is a flowchart illustrating another embodiment of a process for cross-domain communication.
- FIG. 4 is a system diagram illustrating an embodiment of a cross-domain communication system.
- FIG. 5 is a block diagram illustrating an embodiment of a sender device.
- FIG. 6 is a block diagram illustrating an embodiment of a receiver device.
- the invention can be implemented in numerous ways, including as a process; an apparatus; a system; a composition of matter; a computer program product embodied on a computer readable storage medium; and/or a processor, such as a processor configured to execute instructions stored on and/or provided by a memory coupled to the processor.
- these implementations, or any other form that the invention may take, may be referred to as techniques.
- the order of the steps of disclosed processes may be altered within the scope of the invention.
- a component such as a processor or a memory described as being configured to perform a task may be implemented as a general component that is temporarily configured to perform the task at a given time or a specific component that is manufactured to perform the task.
- the term ‘processor’ refers to one or more devices, circuits, and/or processing cores configured to process data, such as computer program instructions.
- a domain refers to a collection of network devices organized under a common network name, such as www.example.com.
- the techniques can be used for implementing safe communication among different domains while guaranteeing security isolation of domains with respect to browser software.
- FIG. 1 is a block diagram illustrating an embodiment of a system that supports cross-domain communication.
- system 100 includes a first domain 104 and a second domain 106 , which in this example are shown to be isv.com and alisoft.com, respectively.
- domain 104 is presumed to be the domain from which a data request is sent and is referred to as the first domain or the sender domain
- domain 106 is presumed to be the domain to which a data request is received and is referred to as the second domain or the receiver domain.
- Communication in the reverse direction where domain 106 is the sender domain and domain 104 is the receiver domain is possible.
- One or more servers are included in the domains to provide web services such as displaying web pages and responding to client requests.
- different physical servers are included in different domains.
- a physical server device is virtualized to operate as multiple virtual servers that separately service different domains.
- domain 104 there are one or more web pages that can be accessed by client devices such as 102 via client software such as a web browser.
- a designated response processing page also referred to as the ACK page
- URL Universal Resource Locator
- ASK page in this case with the URL of alisoft.com/ask.htm
- ASK page is configured to handle cross-domain transfer requests from outside domains such as domain 104 . Details of the page configurations and operations are described below.
- FIG. 2A is a flowchart illustrating an embodiment of a process for cross-domain communication.
- Process 200 may be implemented on a device such as a server implementing services for domain 104 .
- a data request is sent from the sender domain to the receiver domain.
- the request may be evoked in response to a client action that is made on a webpage that is not specifically designated for cross-domain communication.
- a webpage is referred to as an originating page.
- the data request is sent to a designated request processing page in the receiver domain.
- the designated request processing page is specifically configured to respond to cross-domain data request.
- a response is received from the receiver domain. If the communication session is successful, the response would include requested data. The response is directed to a designated response processing page in the sender domain. The response is processed by the response processing page and information is passed to the originating page as appropriate.
- the response is processed and can be passed on to the originating page as appropriate.
- FIG. 2B is a flowchart illustrating an embodiment of a process for cross-domain communication.
- Process 250 may be implemented on a device such as a server implementing services for domain 106 .
- a data request from the sender domain is received in the receiver domain.
- the data request is directed to a designated request processing page in the receiver domain.
- the data request is processed.
- Information relating to the response is gathered and a response is generated.
- the response is sent to a designated response processing page in the sender domain to be processed and passed on to the originating page as appropriate.
- the above cross-domain communication technique observes the security isolation mechanisms of browser domains, without requiring decreased browser security standards, URL page jumping, or substantially increased server load. It guarantees fair and symmetrical security protection for both sides for communication.
- the server of the sender domain deploys a designated response processing page and the server of the receiver domain deploys a designated request processing page.
- the browser opens the designated pages to transfer data for cross-domain communication.
- deployment refers to placing these page files on the appropriate server and “open” refers to sending a request to a page file by a client browser.
- the client browser loads the originating page, which is a page that initiates cross domain communication.
- the originating page may be a login page for the sender domain that requires certain information from the receiver domain (e.g., user account in the receiver domain) to complete the login process in the sender domain.
- the originating page locates the name of the sender domain, such as isv.com.
- the browser that loaded the originating page will open a hidden page on the server in the sender domain, use the hidden page to open a ASK page deployed on the server of the receiver domain and transfer the command and the data associated with the communication request using an URL fragment identifier of the request and the name property of a window object of the page.
- the receiver domain receives the request command and data at the designated request processing page, also referred to as the ASK page. Data pertaining to the response of the request is extracted. Since the ASK page is located in the receiver domain, such as alisoft.com, it can acquire related data in the domain according to the request that is received.
- the ASK page opens the designated response processing page (i.e., the ACK page) on the sender domain or opens another hidden page and uses the hidden page to open the ACK page and sends the returning position and the response data using an URL fragment identifier and the name property of window object of the page. Since the ACK page is located in the sender domain, such as isv.com, it can return the response data to the originating page in the same domain.
- the ASK page is used for receiving request command for cross-domain transfer and extracting response data according to the command.
- the ACK page is used for receiving the response data sent by the ASK page and returning the response data to the originating page in the sender domain.
- the sender and receiver domains only need to exchange data via their respective servers the first time a specific cross-domain communication is made. In subsequent cross-domain transfers, the browser will use its cache function to cache the parameters sent the first time and the receiver of communication extracts the resulting data from the browser directly when receiving a cross-domain transfer request.
- FIG. 3 is a flowchart illustrating another embodiment of a process for cross-domain communication.
- the servers on the sender and receiver domains deploy the designated response processing ACK page and the designated request processing ASK page, respectively.
- Bi-direction communications can be achieved by each domain deploying both an ACK page and an ASK page.
- the designated request processing ASK page is a static page in some embodiments and a dynamic page in some embodiments where additional Hypertext Transfer Protocol (HTTP) header information is added.
- the response processing ACK page is a static page in some embodiments.
- ASK pages and ACK pages are basic pages for communication between two domains. They are collectively referred to as communication pages.
- the communication pages agree on the same request format and follow the same communication protocol.
- the HTTP GET request can be used for requesting page and command, and communication commands and data are not transferred as URL parameters.
- opening the hidden page includes opening an invisible new window or an invisible iframe.
- the hidden page opens the ASK page deployed on the server of the receiver domain and request command and parameters are transferred.
- the request command is transferred in the form of a fragment identifier attached to the URL and the data can be transferred in the form of the name property of window object.
- the fragment identifier is attached to the URL by appending a “#” identifier to the URL and appending a string to “#”.
- a fragment identifier can be used for locating a designated anchor node (reading position) in a page and is processed by the client rather than the server.
- URLs with or without a fragment identifier or with different fragment identifiers are considered to be the same URL for the server and are cached the same way by the browser. Therefore, data is exchanged the first time the URL is requested and is cached in the browser and available for subsequent requests without requiring further data exchange between the servers and the browser.
- the ASK page in the receiver domain implements corresponding service and acquires response data.
- the ASK page in the receiver domain opens a hidden new page or uses the ASK page itself to open the ACK page in the sender domain and transfers the response data to the ACK page in the sender domain.
- the security isolation mechanism built into the browser forbids a program of a page in one domain to operate the content and data of another page directly. But when a page in one domain can open a page in another domain, transferring data to a page in the other domain is permitted in the form of URL or the name property of window object.
- the ACK page in the original domain website returns the response data received to the originating page.
- a typical response to the ASK page is as follows:
- the ACK page and the originating page are located in the same domain, the ACK page can visit the originating page and thus transfer the resulting data to the originating page.
- request and response data are transferred in form of strings in JSON format.
- JSON format is native data expression form for JavaScript language and has the advantages of simple form, compact format and convenient conversion. Data can be transferred by the name property of window object, by which large amount data can be transferred. Data also can be transferred all by fragment identifiers.
- the data above can be packaged into a series of JavaScript functions to developers.
- function envoy domainName, serviceName, on Success, on Error
- domainName is the domain name for communication
- serviceName is the service name being requested
- on Success indicates the return function upon success
- on Error indicates the return function upon failure.
- FIG. 4 is a system diagram illustrating an embodiment of a cross-domain communication system.
- the system includes a sender device 100 and a receiver device 200 that belong to different domains.
- the sender 100 is implemented in some embodiments as a server configured to send a request to the designated request processing page on the receiver 200 and to receive a response sent by the designated request processing page on the receiver, at a designated local response processing page on the sender.
- the receiver 200 is implemented in some embodiments as a server configured to receive the request sent by the sender 100 via the designated request processing page, processing the request sent by the sender 100 and acquiring response data and sending the response to the response processing page on receiver 100 .
- FIG. 5 is a block diagram illustrating an embodiment of a sender device.
- the device includes a request sending module 10 , a response receiving module 20 and a data acquiring module 30 .
- the request sending module 10 is configured to a request to the designated request processing page in the receiver. It further includes an originating page configured to send data such as the request command and associated data.
- the response receiving module 20 is configured to process a response sent by the receiver. It further includes a designated response processing page configured to receive the response.
- the data acquiring module 30 is configured to acquire the response from the page for receiving data in the sender.
- FIG. 6 is a block diagram illustrating an embodiment of a receiver device for cross-domain communication.
- the device in this example includes a request receiving module 40 , a processing module 50 and a response sending module 60 .
- the request receiving module 40 is configured to receive a request from a sender. It further includes a designated request processing page configured to receive the request command and associated data.
- the processing module 50 is configured to process the request sent by the sender and to acquire response data.
- the response sending module 60 is used for sending the response to designated response processing page on the sender.
- a device may be configured both as a sender and a receiver and includes all the modules shown in FIGS. 5 and 6 .
- the designated request processing page and the designated response processing page can be different pages or the same page.
- the page(s) can be configured as dynamic pages or static pages.
- the modules described above can be implemented as software components executing on one or more general purpose processors, as hardware such as programmable logic devices and/or Application Specific Integrated Circuits designed to perform certain functions or a combination thereof.
- the modules can be embodied by a form of software products which can be stored in a nonvolatile storage medium (such as CD-ROM, U disk, mobile hard disk, etc.), including a number of instructions for making a computer device (such as personal computers, servers, network equipments, etc.) implement the methods described in the embodiments of the present invention.
- the modules may be implemented on a single device or distributed across multiple devices. The functions of the modules may be merged into one another or further split into multiple sub-modules.
- the technical personnel in this field can understand clearly that the present invention can be implemented by hardware or software and necessary current hardware platform.
- the technical program of the present invention can be embodied by a form of software products which can be stored in a nonvolatile storage medium (such as CD-ROM, U disk, mobile hard disk, etc.), including a number of instructions for making a computer device (such as personal computers, servers, or network equipments, etc.) implement the methods described in the embodiments of the present invention.
Landscapes
- Engineering & Computer Science (AREA)
- Computer Networks & Wireless Communication (AREA)
- Signal Processing (AREA)
- Databases & Information Systems (AREA)
- Computer Security & Cryptography (AREA)
- Theoretical Computer Science (AREA)
- General Engineering & Computer Science (AREA)
- Computing Systems (AREA)
- Data Mining & Analysis (AREA)
- Physics & Mathematics (AREA)
- General Physics & Mathematics (AREA)
- Computer Hardware Design (AREA)
- Information Transfer Between Computers (AREA)
Priority Applications (4)
| Application Number | Priority Date | Filing Date | Title |
|---|---|---|---|
| EP09810347.6A EP2318941A4 (en) | 2008-08-25 | 2009-08-20 | METHOD AND DEVICE FOR COMMUNICATING BETWEEN DOMAINS |
| PCT/US2009/004751 WO2010024863A1 (en) | 2008-08-25 | 2009-08-20 | Method and apparatus for cross-domain communication |
| JP2011524974A JP5689799B2 (ja) | 2008-08-25 | 2009-08-20 | クロスドメイン通信のための方法及び装置 |
| US14/139,426 USRE45139E1 (en) | 2008-08-25 | 2013-12-23 | Method and apparatus for cross-domain communication using designated response processing page |
Applications Claiming Priority (3)
| Application Number | Priority Date | Filing Date | Title |
|---|---|---|---|
| CN200810147259.3A CN101662460B (zh) | 2008-08-25 | 2008-08-25 | 一种跨域通讯的方法、系统和装置 |
| CN200810147259 | 2008-08-25 | ||
| CN200810147259.3 | 2008-08-25 |
Related Child Applications (1)
| Application Number | Title | Priority Date | Filing Date |
|---|---|---|---|
| US14/139,426 Reissue USRE45139E1 (en) | 2008-08-25 | 2013-12-23 | Method and apparatus for cross-domain communication using designated response processing page |
Publications (2)
| Publication Number | Publication Date |
|---|---|
| US20100049782A1 US20100049782A1 (en) | 2010-02-25 |
| US8090763B2 true US8090763B2 (en) | 2012-01-03 |
Family
ID=41697321
Family Applications (2)
| Application Number | Title | Priority Date | Filing Date |
|---|---|---|---|
| US12/583,362 Ceased US8090763B2 (en) | 2008-08-25 | 2009-08-18 | Method and apparatus for cross-domain communication using designated response processing page |
| US14/139,426 Active 2029-11-28 USRE45139E1 (en) | 2008-08-25 | 2013-12-23 | Method and apparatus for cross-domain communication using designated response processing page |
Family Applications After (1)
| Application Number | Title | Priority Date | Filing Date |
|---|---|---|---|
| US14/139,426 Active 2029-11-28 USRE45139E1 (en) | 2008-08-25 | 2013-12-23 | Method and apparatus for cross-domain communication using designated response processing page |
Country Status (6)
| Country | Link |
|---|---|
| US (2) | US8090763B2 (zh) |
| EP (1) | EP2318941A4 (zh) |
| JP (1) | JP5689799B2 (zh) |
| CN (1) | CN101662460B (zh) |
| HK (1) | HK1141170A1 (zh) |
| WO (1) | WO2010024863A1 (zh) |
Cited By (4)
| Publication number | Priority date | Publication date | Assignee | Title |
|---|---|---|---|---|
| US20110225495A1 (en) * | 2010-03-12 | 2011-09-15 | Salesforce.Com, Inc. | Service Cloud Console |
| US20130262977A1 (en) * | 2012-03-30 | 2013-10-03 | International Business Machines Corporation | Controlling Browser Preferences with a Rich Internet Application |
| US9154470B2 (en) | 2012-05-25 | 2015-10-06 | Canon U.S.A., Inc. | System and method for processing transactions |
| US9215096B2 (en) | 2011-08-26 | 2015-12-15 | Salesforce.Com, Inc. | Computer implemented methods and apparatus for providing communication between network domains in a service cloud |
Families Citing this family (37)
| Publication number | Priority date | Publication date | Assignee | Title |
|---|---|---|---|---|
| US8539234B2 (en) * | 2010-03-30 | 2013-09-17 | Salesforce.Com, Inc. | Secure client-side communication between multiple domains |
| CN102486780A (zh) * | 2010-12-01 | 2012-06-06 | 腾讯科技(深圳)有限公司 | 异步跨域传输xml数据的方法、客户端和服务端 |
| CN102571851B (zh) * | 2010-12-27 | 2015-03-25 | 阿里巴巴集团控股有限公司 | 一种数据通信方法和系统 |
| CN102307220B (zh) * | 2011-03-18 | 2014-04-02 | 北京思特奇信息技术股份有限公司 | 一种跨域网页信息交互方法 |
| CN102184220A (zh) * | 2011-05-06 | 2011-09-14 | 中兴通讯股份有限公司 | 跨域页面显示控制方法及装置 |
| US20120303453A1 (en) * | 2011-05-26 | 2012-11-29 | Yahoo! Inc. | Methods and systems for securely targeting advertisements on login pages |
| CN102984179A (zh) * | 2011-09-02 | 2013-03-20 | 广东电子工业研究院有限公司 | 一种面向云计算操作系统进行Web服务跨域访问的方法 |
| US8898780B2 (en) * | 2011-11-07 | 2014-11-25 | Qualcomm Incorporated | Encoding labels in values to capture information flows |
| CN104012050A (zh) * | 2012-01-02 | 2014-08-27 | 诺基亚通信公司 | 用于跨至少两个域传递数据的方法和装置 |
| CN103246667A (zh) * | 2012-02-08 | 2013-08-14 | 腾讯科技(深圳)有限公司 | 数据跨域传递的方法及装置 |
| CN103294672B (zh) * | 2012-02-23 | 2017-05-10 | 腾讯科技(深圳)有限公司 | 一种用于实现跨域拖动的方法、系统和装置 |
| CN103309861B (zh) * | 2012-03-07 | 2018-04-10 | 阿里巴巴集团控股有限公司 | 跨域数据获取的方法与装置 |
| CN103309877B (zh) * | 2012-03-12 | 2017-04-05 | 腾讯科技(深圳)有限公司 | 跨域通讯及全双工通讯的方法、装置 |
| CN102662600B (zh) * | 2012-04-28 | 2013-11-27 | 北京亿中邮信息技术有限公司 | 一种不同域名下文件相互拖拽的方法 |
| CN103634338B (zh) * | 2012-08-21 | 2017-04-12 | 北京亿赞普网络技术有限公司 | 在线修改网页主域标题的方法、数据处理装置和系统 |
| CN103152445B (zh) * | 2013-04-03 | 2016-02-03 | 晶赞广告(上海)有限公司 | 一种互联网安全的异步跨域身份标识映射方法 |
| CN104426864B (zh) * | 2013-08-28 | 2019-01-08 | 腾讯科技(深圳)有限公司 | 跨域远程命令的实现方法及系统 |
| CN103546570A (zh) * | 2013-10-29 | 2014-01-29 | 小米科技有限责任公司 | 网络客户端跨域请求数据的实现方法、装置及终端 |
| CN103870551B (zh) * | 2014-02-28 | 2018-02-23 | 小米科技有限责任公司 | 一种跨域数据获取的方法和装置 |
| CN104301379A (zh) * | 2014-08-28 | 2015-01-21 | 北京奇虎科技有限公司 | 一种网页跨域通信方法和装置 |
| CN105471824A (zh) * | 2014-09-03 | 2016-04-06 | 阿里巴巴集团控股有限公司 | 实现浏览器调用本地业务组件的方法、装置及系统 |
| CN104572263B (zh) * | 2014-12-30 | 2017-11-07 | 腾讯科技(深圳)有限公司 | 一种页面数据交互方法、相关装置及系统 |
| CN105491116B (zh) * | 2015-11-26 | 2019-04-26 | 广州华多网络科技有限公司 | 一种跨窗口提交数据的方法及系统 |
| GB2548405B (en) * | 2016-03-18 | 2019-08-14 | Advanced Risc Mach Ltd | Combination of control interfaces for multiple communicating domains |
| CN107220260B (zh) | 2016-03-22 | 2020-07-24 | 阿里巴巴集团控股有限公司 | 一种页面显示的方法及装置 |
| CN107070870B (zh) * | 2017-01-09 | 2020-04-14 | 阿里巴巴集团控股有限公司 | 一种数据获取方法和装置 |
| US11165825B2 (en) | 2017-02-16 | 2021-11-02 | Emerald Cactus Ventures, Inc. | System and method for creating encrypted virtual private network hotspot |
| US11122013B2 (en) * | 2017-02-16 | 2021-09-14 | Emerald Cactus Ventures, Inc. | System and method for encrypting data interactions delineated by zones |
| US11165751B2 (en) | 2017-02-16 | 2021-11-02 | Emerald Cactus Ventures, Inc. | System and method for establishing simultaneous encrypted virtual private networks from a single computing device |
| US10733376B2 (en) * | 2017-03-01 | 2020-08-04 | Google Llc | Delivering auto-play media content element from cross origin resources |
| CN107749858A (zh) * | 2017-11-06 | 2018-03-02 | 郑州云海信息技术有限公司 | 一种端点之间切换方法及装置 |
| CN110209959B (zh) * | 2018-02-11 | 2024-01-12 | 北京京东尚科信息技术有限公司 | 信息处理方法和装置 |
| CN110928699A (zh) * | 2018-09-20 | 2020-03-27 | 北京京东尚科信息技术有限公司 | 一种前端跨域事件处理方法和装置 |
| CN109450973A (zh) * | 2018-09-29 | 2019-03-08 | 福建威盾科技有限公司 | 一种跨域浏览器数据共享的方法 |
| CN111049851B (zh) * | 2019-12-24 | 2021-10-01 | 中国电子科技集团公司第五十四研究所 | 一种跨域传输业务多级多维联动管控系统 |
| CN112905940A (zh) * | 2021-02-25 | 2021-06-04 | 平安普惠企业管理有限公司 | 页面通讯方法、装置、计算机设备以及存储介质 |
| CN118449886A (zh) * | 2024-06-04 | 2024-08-06 | 国网江苏省电力有限公司信息通信分公司 | 一种跨域性能检测方法和装置 |
Citations (25)
| Publication number | Priority date | Publication date | Assignee | Title |
|---|---|---|---|---|
| US5142622A (en) | 1989-01-31 | 1992-08-25 | International Business Machines Corporation | System for interconnecting applications across different networks of data processing systems by mapping protocols across different network domains |
| US5802590A (en) | 1994-12-13 | 1998-09-01 | Microsoft Corporation | Method and system for providing secure access to computer resources |
| US5895499A (en) | 1995-07-03 | 1999-04-20 | Sun Microsystems, Inc. | Cross-domain data transfer using deferred page remapping |
| US5961593A (en) | 1997-01-22 | 1999-10-05 | Lucent Technologies, Inc. | System and method for providing anonymous personalized browsing by a proxy system in a network |
| US6125384A (en) | 1996-12-23 | 2000-09-26 | International Business Machines Corporation | Computer apparatus and method for communicating between software applications and computers on the world-wide web |
| US6934757B1 (en) | 2000-01-06 | 2005-08-23 | International Business Machines Corporation | Method and system for cross-domain service invocation using a single data handle associated with the stored common data and invocation-specific data |
| US20070113237A1 (en) | 2005-11-17 | 2007-05-17 | Ian Hickson | Method and device for event communication between documents |
| US20070256003A1 (en) * | 2006-04-24 | 2007-11-01 | Seth Wagoner | Platform for the interactive contextual augmentation of the web |
| US20070299735A1 (en) | 2006-06-27 | 2007-12-27 | Piyush Mangalick | Cross domain customer interface updates |
| US20070300064A1 (en) | 2006-06-23 | 2007-12-27 | Microsoft Corporation | Communication across domains |
| US20070299857A1 (en) * | 2006-06-23 | 2007-12-27 | Microsoft Corporation | Cross Domain Communication |
| US20080010359A1 (en) * | 2006-07-10 | 2008-01-10 | Jeffrey Mark Achtermann | Computer implemented method and system for managing server-based rendering of messages in a heterogeneous environment |
| US20080033956A1 (en) * | 2006-08-07 | 2008-02-07 | Shoumen Saha | Distribution of Content Document to Varying Users With Security Customization and Scalability |
| US20080034441A1 (en) * | 2006-08-07 | 2008-02-07 | Shoumen Saha | Updating content within a container document for user groups |
| US20080046562A1 (en) * | 2006-08-21 | 2008-02-21 | Crazy Egg, Inc. | Visual web page analytics |
| US20080281944A1 (en) * | 2007-05-07 | 2008-11-13 | Vorne Industries, Inc. | Method and system for extending the capabilities of embedded devices through network clients |
| US20080298342A1 (en) * | 2007-05-28 | 2008-12-04 | Benjamin Charles Appleton | Inter-Domain Communication |
| US20090006996A1 (en) * | 2006-08-07 | 2009-01-01 | Shoumen Saha | Updating Content Within A Container Document For User Groups |
| US20090037806A1 (en) * | 2007-07-30 | 2009-02-05 | Jun Yang | Cross-Domain Communication |
| US20090199083A1 (en) * | 2008-01-17 | 2009-08-06 | Can Sar | Method of enabling the modification and annotation of a webpage from a web browser |
| US20090248494A1 (en) * | 2008-04-01 | 2009-10-01 | Certona Corporation | System and method for collecting and targeting visitor behavior |
| US20090293018A1 (en) * | 2008-05-23 | 2009-11-26 | Jeffrey Wilson | History-based tracking of user preference settings |
| US7640512B1 (en) * | 2000-12-22 | 2009-12-29 | Automated Logic Corporation | Updating objects contained within a webpage |
| US20090328063A1 (en) * | 2008-06-27 | 2009-12-31 | Microsoft Corporation | Inter-frame messaging between different domains |
| US20100088354A1 (en) * | 2006-11-30 | 2010-04-08 | Alibaba Group Holding Limited | Method and System for Log File Analysis Based on Distributed Computing Network |
Family Cites Families (3)
| Publication number | Priority date | Publication date | Assignee | Title |
|---|---|---|---|---|
| IL142815A (en) * | 2001-04-25 | 2010-06-16 | Gal Trifon | A method for dynamically changing one web page to another web page |
| US8280819B2 (en) * | 2004-07-09 | 2012-10-02 | Ebay Inc. | Method and apparatus for securely displaying and communicating trusted and untrusted internet content |
| US7506248B2 (en) * | 2005-10-14 | 2009-03-17 | Ebay Inc. | Asynchronously loading dynamically generated content across multiple internet domains |
-
2008
- 2008-08-25 CN CN200810147259.3A patent/CN101662460B/zh active Active
-
2009
- 2009-08-18 US US12/583,362 patent/US8090763B2/en not_active Ceased
- 2009-08-20 JP JP2011524974A patent/JP5689799B2/ja active Active
- 2009-08-20 WO PCT/US2009/004751 patent/WO2010024863A1/en active Application Filing
- 2009-08-20 EP EP09810347.6A patent/EP2318941A4/en not_active Withdrawn
-
2010
- 2010-08-03 HK HK10107404.3A patent/HK1141170A1/zh unknown
-
2013
- 2013-12-23 US US14/139,426 patent/USRE45139E1/en active Active
Patent Citations (26)
| Publication number | Priority date | Publication date | Assignee | Title |
|---|---|---|---|---|
| US5142622A (en) | 1989-01-31 | 1992-08-25 | International Business Machines Corporation | System for interconnecting applications across different networks of data processing systems by mapping protocols across different network domains |
| US5802590A (en) | 1994-12-13 | 1998-09-01 | Microsoft Corporation | Method and system for providing secure access to computer resources |
| US5895499A (en) | 1995-07-03 | 1999-04-20 | Sun Microsystems, Inc. | Cross-domain data transfer using deferred page remapping |
| US6125384A (en) | 1996-12-23 | 2000-09-26 | International Business Machines Corporation | Computer apparatus and method for communicating between software applications and computers on the world-wide web |
| US5961593A (en) | 1997-01-22 | 1999-10-05 | Lucent Technologies, Inc. | System and method for providing anonymous personalized browsing by a proxy system in a network |
| US6934757B1 (en) | 2000-01-06 | 2005-08-23 | International Business Machines Corporation | Method and system for cross-domain service invocation using a single data handle associated with the stored common data and invocation-specific data |
| US7640512B1 (en) * | 2000-12-22 | 2009-12-29 | Automated Logic Corporation | Updating objects contained within a webpage |
| US20070113237A1 (en) | 2005-11-17 | 2007-05-17 | Ian Hickson | Method and device for event communication between documents |
| US20070256003A1 (en) * | 2006-04-24 | 2007-11-01 | Seth Wagoner | Platform for the interactive contextual augmentation of the web |
| US20070300064A1 (en) | 2006-06-23 | 2007-12-27 | Microsoft Corporation | Communication across domains |
| US20070299857A1 (en) * | 2006-06-23 | 2007-12-27 | Microsoft Corporation | Cross Domain Communication |
| US20070299735A1 (en) | 2006-06-27 | 2007-12-27 | Piyush Mangalick | Cross domain customer interface updates |
| US20080010359A1 (en) * | 2006-07-10 | 2008-01-10 | Jeffrey Mark Achtermann | Computer implemented method and system for managing server-based rendering of messages in a heterogeneous environment |
| US20080033956A1 (en) * | 2006-08-07 | 2008-02-07 | Shoumen Saha | Distribution of Content Document to Varying Users With Security Customization and Scalability |
| US20090006996A1 (en) * | 2006-08-07 | 2009-01-01 | Shoumen Saha | Updating Content Within A Container Document For User Groups |
| US20090037935A1 (en) * | 2006-08-07 | 2009-02-05 | Shoumen Saha | Updating The Configuration of Container Documents |
| US20080034441A1 (en) * | 2006-08-07 | 2008-02-07 | Shoumen Saha | Updating content within a container document for user groups |
| US20080046562A1 (en) * | 2006-08-21 | 2008-02-21 | Crazy Egg, Inc. | Visual web page analytics |
| US20100088354A1 (en) * | 2006-11-30 | 2010-04-08 | Alibaba Group Holding Limited | Method and System for Log File Analysis Based on Distributed Computing Network |
| US20080281944A1 (en) * | 2007-05-07 | 2008-11-13 | Vorne Industries, Inc. | Method and system for extending the capabilities of embedded devices through network clients |
| US20080298342A1 (en) * | 2007-05-28 | 2008-12-04 | Benjamin Charles Appleton | Inter-Domain Communication |
| US20090037806A1 (en) * | 2007-07-30 | 2009-02-05 | Jun Yang | Cross-Domain Communication |
| US20090199083A1 (en) * | 2008-01-17 | 2009-08-06 | Can Sar | Method of enabling the modification and annotation of a webpage from a web browser |
| US20090248494A1 (en) * | 2008-04-01 | 2009-10-01 | Certona Corporation | System and method for collecting and targeting visitor behavior |
| US20090293018A1 (en) * | 2008-05-23 | 2009-11-26 | Jeffrey Wilson | History-based tracking of user preference settings |
| US20090328063A1 (en) * | 2008-06-27 | 2009-12-31 | Microsoft Corporation | Inter-frame messaging between different domains |
Non-Patent Citations (1)
| Title |
|---|
| U.S. Appl. No. 11/426,174, Gwozdz et al. |
Cited By (15)
| Publication number | Priority date | Publication date | Assignee | Title |
|---|---|---|---|---|
| US8769416B2 (en) | 2010-03-12 | 2014-07-01 | Salesforce.Com, Inc. | Service cloud console |
| US9830054B2 (en) | 2010-03-12 | 2017-11-28 | Salesforce.Com, Inc. | Service cloud console |
| US20110225232A1 (en) * | 2010-03-12 | 2011-09-15 | Salesforce.Com, Inc. | Service Cloud Console |
| US20110225233A1 (en) * | 2010-03-12 | 2011-09-15 | Salesforce.Com, Inc. | Service Cloud Console |
| US10101883B2 (en) | 2010-03-12 | 2018-10-16 | Salesforce.Com, Inc. | Service cloud console |
| US8745272B2 (en) | 2010-03-12 | 2014-06-03 | Salesforce.Com, Inc. | Service cloud console |
| US20110225500A1 (en) * | 2010-03-12 | 2011-09-15 | Salesforce.Com, Inc. | Service Cloud Console |
| US8984409B2 (en) | 2010-03-12 | 2015-03-17 | Salesforce.Com, Inc. | Service cloud console |
| US20110225495A1 (en) * | 2010-03-12 | 2011-09-15 | Salesforce.Com, Inc. | Service Cloud Console |
| US9971482B2 (en) | 2010-03-12 | 2018-05-15 | Salesforce.Com, Inc. | Service cloud console |
| US8914539B2 (en) * | 2010-03-12 | 2014-12-16 | Salesforce.Com, Inc. | Service cloud console |
| US9215096B2 (en) | 2011-08-26 | 2015-12-15 | Salesforce.Com, Inc. | Computer implemented methods and apparatus for providing communication between network domains in a service cloud |
| US10044660B2 (en) | 2011-08-26 | 2018-08-07 | Salesforce.Com, Inc. | Computer implemented methods and apparatus for providing communication between network domains in a service cloud |
| US20130262977A1 (en) * | 2012-03-30 | 2013-10-03 | International Business Machines Corporation | Controlling Browser Preferences with a Rich Internet Application |
| US9154470B2 (en) | 2012-05-25 | 2015-10-06 | Canon U.S.A., Inc. | System and method for processing transactions |
Also Published As
| Publication number | Publication date |
|---|---|
| WO2010024863A1 (en) | 2010-03-04 |
| EP2318941A1 (en) | 2011-05-11 |
| CN101662460B (zh) | 2015-07-15 |
| USRE45139E1 (en) | 2014-09-16 |
| CN101662460A (zh) | 2010-03-03 |
| HK1141170A1 (zh) | 2010-10-29 |
| JP5689799B2 (ja) | 2015-03-25 |
| JP2012501034A (ja) | 2012-01-12 |
| EP2318941A4 (en) | 2013-05-08 |
| US20100049782A1 (en) | 2010-02-25 |
Similar Documents
| Publication | Publication Date | Title |
|---|---|---|
| USRE45139E1 (en) | Method and apparatus for cross-domain communication using designated response processing page | |
| US9697188B2 (en) | Method to enable cross-origin resource sharing from a webpage inside a private network | |
| US8464318B1 (en) | System and method for protecting web clients and web-based applications | |
| US8819819B1 (en) | Method and system for automatically obtaining webpage content in the presence of javascript | |
| US8448241B1 (en) | Browser extension for checking website susceptibility to cross site scripting | |
| US11736446B2 (en) | Object property getter and setter for clientless VPN | |
| US20080222736A1 (en) | Scrambling HTML to prevent CSRF attacks and transactional crimeware attacks | |
| Putthacharoen et al. | Protecting cookies from cross site script attacks using dynamic cookies rewriting technique | |
| US9509691B2 (en) | Secure transfer of web application client persistent state information into a new domain | |
| US11836213B2 (en) | Encoding-free JavaScript stringify for clientless VPN | |
| US10360379B2 (en) | Method and apparatus for detecting exploits | |
| CN105205078A (zh) | 访问网页的方法和装置 | |
| CN110633432A (zh) | 一种获取数据的方法、装置、终端设备及介质 | |
| CN109670279A (zh) | 一种网站灵活配置网页嵌入权限的方法 | |
| JP2010079431A (ja) | 情報漏洩防止プログラム | |
| US20200034483A1 (en) | Browser storage for clientless vpn | |
| CN115086393B (zh) | 一种接口调用方法、装置、设备及存储介质 | |
| TWI486039B (zh) | Inter-domain communication methods, systems and devices | |
| Petty | The Not-So-Same-Origin Policy | |
| TWI234377B (en) | Network security protection system | |
| Nu1L Team | Advanced Web | |
| JP5986695B2 (ja) | 情報処理装置、処理方法およびプログラム | |
| JP5893787B2 (ja) | 情報処理装置、処理方法およびプログラム | |
| Grossman | Hacking intranet websites from the outside (take 2) | |
| Macia et al. | Improving Security in Web Sessions: Special Management of Cookies |
Legal Events
| Date | Code | Title | Description |
|---|---|---|---|
| AS | Assignment |
Owner name: ALIBABA GROUP HOLDING LIMITED,CAYMAN ISLANDS Free format text: ASSIGNMENT OF ASSIGNORS INTEREST;ASSIGNOR:LI, ZHANYUAN;REEL/FRAME:023152/0738 Effective date: 20090806 Owner name: ALIBABA GROUP HOLDING LIMITED, CAYMAN ISLANDS Free format text: ASSIGNMENT OF ASSIGNORS INTEREST;ASSIGNOR:LI, ZHANYUAN;REEL/FRAME:023152/0738 Effective date: 20090806 |
|
| STCF | Information on status: patent grant |
Free format text: PATENTED CASE |
|
| RF | Reissue application filed |
Effective date: 20131223 |