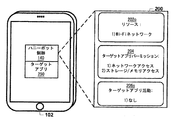
JP2018536932A - 動的ハニーポットシステム - Google Patents
動的ハニーポットシステム Download PDFInfo
- Publication number
- JP2018536932A JP2018536932A JP2018521349A JP2018521349A JP2018536932A JP 2018536932 A JP2018536932 A JP 2018536932A JP 2018521349 A JP2018521349 A JP 2018521349A JP 2018521349 A JP2018521349 A JP 2018521349A JP 2018536932 A JP2018536932 A JP 2018536932A
- Authority
- JP
- Japan
- Prior art keywords
- processor
- target application
- computing device
- application
- resources
- Prior art date
- Legal status (The legal status is an assumption and is not a legal conclusion. Google has not performed a legal analysis and makes no representation as to the accuracy of the status listed.)
- Ceased
Links
Images
Classifications
-
- H—ELECTRICITY
- H04—ELECTRIC COMMUNICATION TECHNIQUE
- H04L—TRANSMISSION OF DIGITAL INFORMATION, e.g. TELEGRAPHIC COMMUNICATION
- H04L63/00—Network architectures or network communication protocols for network security
- H04L63/14—Network architectures or network communication protocols for network security for detecting or protecting against malicious traffic
- H04L63/1441—Countermeasures against malicious traffic
- H04L63/1491—Countermeasures against malicious traffic using deception as countermeasure, e.g. honeypots, honeynets, decoys or entrapment
-
- H—ELECTRICITY
- H04—ELECTRIC COMMUNICATION TECHNIQUE
- H04L—TRANSMISSION OF DIGITAL INFORMATION, e.g. TELEGRAPHIC COMMUNICATION
- H04L63/00—Network architectures or network communication protocols for network security
- H04L63/14—Network architectures or network communication protocols for network security for detecting or protecting against malicious traffic
- H04L63/1408—Network architectures or network communication protocols for network security for detecting or protecting against malicious traffic by monitoring network traffic
- H04L63/1416—Event detection, e.g. attack signature detection
-
- G—PHYSICS
- G06—COMPUTING OR CALCULATING; COUNTING
- G06F—ELECTRIC DIGITAL DATA PROCESSING
- G06F21/00—Security arrangements for protecting computers, components thereof, programs or data against unauthorised activity
- G06F21/50—Monitoring users, programs or devices to maintain the integrity of platforms, e.g. of processors, firmware or operating systems
- G06F21/55—Detecting local intrusion or implementing counter-measures
- G06F21/552—Detecting local intrusion or implementing counter-measures involving long-term monitoring or reporting
-
- G—PHYSICS
- G06—COMPUTING OR CALCULATING; COUNTING
- G06F—ELECTRIC DIGITAL DATA PROCESSING
- G06F21/00—Security arrangements for protecting computers, components thereof, programs or data against unauthorised activity
- G06F21/50—Monitoring users, programs or devices to maintain the integrity of platforms, e.g. of processors, firmware or operating systems
- G06F21/55—Detecting local intrusion or implementing counter-measures
- G06F21/554—Detecting local intrusion or implementing counter-measures involving event detection and direct action
-
- G—PHYSICS
- G06—COMPUTING OR CALCULATING; COUNTING
- G06F—ELECTRIC DIGITAL DATA PROCESSING
- G06F21/00—Security arrangements for protecting computers, components thereof, programs or data against unauthorised activity
- G06F21/50—Monitoring users, programs or devices to maintain the integrity of platforms, e.g. of processors, firmware or operating systems
- G06F21/55—Detecting local intrusion or implementing counter-measures
- G06F21/56—Computer malware detection or handling, e.g. anti-virus arrangements
- G06F21/566—Dynamic detection, i.e. detection performed at run-time, e.g. emulation, suspicious activities
-
- G—PHYSICS
- G06—COMPUTING OR CALCULATING; COUNTING
- G06F—ELECTRIC DIGITAL DATA PROCESSING
- G06F21/00—Security arrangements for protecting computers, components thereof, programs or data against unauthorised activity
- G06F21/50—Monitoring users, programs or devices to maintain the integrity of platforms, e.g. of processors, firmware or operating systems
- G06F21/57—Certifying or maintaining trusted computer platforms, e.g. secure boots or power-downs, version controls, system software checks, secure updates or assessing vulnerabilities
- G06F21/577—Assessing vulnerabilities and evaluating computer system security
-
- H—ELECTRICITY
- H04—ELECTRIC COMMUNICATION TECHNIQUE
- H04L—TRANSMISSION OF DIGITAL INFORMATION, e.g. TELEGRAPHIC COMMUNICATION
- H04L63/00—Network architectures or network communication protocols for network security
- H04L63/14—Network architectures or network communication protocols for network security for detecting or protecting against malicious traffic
- H04L63/1433—Vulnerability analysis
-
- G—PHYSICS
- G06—COMPUTING OR CALCULATING; COUNTING
- G06F—ELECTRIC DIGITAL DATA PROCESSING
- G06F2221/00—Indexing scheme relating to security arrangements for protecting computers, components thereof, programs or data against unauthorised activity
- G06F2221/03—Indexing scheme relating to G06F21/50, monitoring users, programs or devices to maintain the integrity of platforms
- G06F2221/033—Test or assess software
-
- H—ELECTRICITY
- H04—ELECTRIC COMMUNICATION TECHNIQUE
- H04L—TRANSMISSION OF DIGITAL INFORMATION, e.g. TELEGRAPHIC COMMUNICATION
- H04L63/00—Network architectures or network communication protocols for network security
- H04L63/14—Network architectures or network communication protocols for network security for detecting or protecting against malicious traffic
- H04L63/1408—Network architectures or network communication protocols for network security for detecting or protecting against malicious traffic by monitoring network traffic
- H04L63/1425—Traffic logging, e.g. anomaly detection
Landscapes
- Engineering & Computer Science (AREA)
- Computer Security & Cryptography (AREA)
- Computer Hardware Design (AREA)
- General Engineering & Computer Science (AREA)
- Software Systems (AREA)
- Theoretical Computer Science (AREA)
- Physics & Mathematics (AREA)
- General Physics & Mathematics (AREA)
- Computing Systems (AREA)
- Signal Processing (AREA)
- Computer Networks & Wireless Communication (AREA)
- Health & Medical Sciences (AREA)
- General Health & Medical Sciences (AREA)
- Virology (AREA)
- Telephone Function (AREA)
- Telephonic Communication Services (AREA)
Applications Claiming Priority (3)
| Application Number | Priority Date | Filing Date | Title |
|---|---|---|---|
| US14/935,522 | 2015-11-09 | ||
| US14/935,522 US20170134405A1 (en) | 2015-11-09 | 2015-11-09 | Dynamic Honeypot System |
| PCT/US2016/056438 WO2017083043A1 (en) | 2015-11-09 | 2016-10-11 | Dynamic honeypot system |
Publications (2)
| Publication Number | Publication Date |
|---|---|
| JP2018536932A true JP2018536932A (ja) | 2018-12-13 |
| JP2018536932A5 JP2018536932A5 (enExample) | 2019-10-31 |
Family
ID=57218995
Family Applications (1)
| Application Number | Title | Priority Date | Filing Date |
|---|---|---|---|
| JP2018521349A Ceased JP2018536932A (ja) | 2015-11-09 | 2016-10-11 | 動的ハニーポットシステム |
Country Status (8)
| Country | Link |
|---|---|
| US (1) | US20170134405A1 (enExample) |
| EP (1) | EP3375159B1 (enExample) |
| JP (1) | JP2018536932A (enExample) |
| KR (1) | KR20180080227A (enExample) |
| CN (1) | CN108353078A (enExample) |
| BR (1) | BR112018009375A8 (enExample) |
| TW (1) | TW201717088A (enExample) |
| WO (1) | WO2017083043A1 (enExample) |
Families Citing this family (78)
| Publication number | Priority date | Publication date | Assignee | Title |
|---|---|---|---|---|
| US9710648B2 (en) | 2014-08-11 | 2017-07-18 | Sentinel Labs Israel Ltd. | Method of malware detection and system thereof |
| US11507663B2 (en) | 2014-08-11 | 2022-11-22 | Sentinel Labs Israel Ltd. | Method of remediating operations performed by a program and system thereof |
| US9602536B1 (en) | 2014-12-04 | 2017-03-21 | Amazon Technologies, Inc. | Virtualized network honeypots |
| US10178195B2 (en) | 2015-12-04 | 2019-01-08 | Cloudflare, Inc. | Origin server protection notification |
| US10135867B2 (en) * | 2015-12-08 | 2018-11-20 | Bank Of America Corporation | Dynamically updated computing environments for detecting and capturing unauthorized computer activities |
| US20170228540A1 (en) * | 2016-02-09 | 2017-08-10 | Appdome Ltd. | Method and a system for detecting malicious code activity by generating software traps per application |
| GB201603118D0 (en) * | 2016-02-23 | 2016-04-06 | Eitc Holdings Ltd | Reactive and pre-emptive security system based on choice theory |
| US10419472B2 (en) * | 2016-03-18 | 2019-09-17 | AO Kaspersky Lab | System and method for repairing vulnerabilities of devices connected to a data network |
| US10528734B2 (en) * | 2016-03-25 | 2020-01-07 | The Mitre Corporation | System and method for vetting mobile phone software applications |
| US9979750B2 (en) | 2016-04-26 | 2018-05-22 | Acalvio Technologies, Inc. | Tunneling for network deceptions |
| US10326796B1 (en) * | 2016-04-26 | 2019-06-18 | Acalvio Technologies, Inc. | Dynamic security mechanisms for mixed networks |
| US10581914B2 (en) | 2016-06-03 | 2020-03-03 | Ciena Corporation | Method and system of mitigating network attacks |
| JP6738013B2 (ja) * | 2016-06-23 | 2020-08-12 | 富士通株式会社 | 攻撃内容分析プログラム、攻撃内容分析方法及び攻撃内容分析装置 |
| US10715533B2 (en) * | 2016-07-26 | 2020-07-14 | Microsoft Technology Licensing, Llc. | Remediation for ransomware attacks on cloud drive folders |
| EP3291501A1 (en) * | 2016-08-31 | 2018-03-07 | Siemens Aktiengesellschaft | System and method for using a virtual honeypot in an industrial automation system and cloud connector |
| US10447734B2 (en) | 2016-11-11 | 2019-10-15 | Rapid7, Inc. | Monitoring scan attempts in a network |
| US10298605B2 (en) * | 2016-11-16 | 2019-05-21 | Red Hat, Inc. | Multi-tenant cloud security threat detection |
| US11695800B2 (en) | 2016-12-19 | 2023-07-04 | SentinelOne, Inc. | Deceiving attackers accessing network data |
| US11616812B2 (en) | 2016-12-19 | 2023-03-28 | Attivo Networks Inc. | Deceiving attackers accessing active directory data |
| US10599842B2 (en) * | 2016-12-19 | 2020-03-24 | Attivo Networks Inc. | Deceiving attackers in endpoint systems |
| US10223536B2 (en) * | 2016-12-29 | 2019-03-05 | Paypal, Inc. | Device monitoring policy |
| US10924502B2 (en) * | 2016-12-29 | 2021-02-16 | Noblis, Inc. | Network security using inflated files for anomaly detection |
| US10628585B2 (en) | 2017-01-23 | 2020-04-21 | Microsoft Technology Licensing, Llc | Ransomware resilient databases |
| CN109033885B (zh) | 2017-06-09 | 2022-11-18 | 腾讯科技(深圳)有限公司 | 一种数据响应方法、终端设备以及服务器 |
| WO2019032728A1 (en) | 2017-08-08 | 2019-02-14 | Sentinel Labs, Inc. | METHODS, SYSTEMS AND DEVICES FOR DYNAMICALLY MODELING AND REGROUPING END POINTS FOR ONBOARD NETWORKING |
| US20190108355A1 (en) * | 2017-10-09 | 2019-04-11 | Digital Guardian, Inc. | Systems and methods for identifying potential misuse or exfiltration of data |
| US10867039B2 (en) * | 2017-10-19 | 2020-12-15 | AO Kaspersky Lab | System and method of detecting a malicious file |
| US10915629B2 (en) * | 2017-11-02 | 2021-02-09 | Paypal, Inc. | Systems and methods for detecting data exfiltration |
| US10771482B1 (en) * | 2017-11-14 | 2020-09-08 | Ca, Inc. | Systems and methods for detecting geolocation-aware malware |
| US10826939B2 (en) * | 2018-01-19 | 2020-11-03 | Rapid7, Inc. | Blended honeypot |
| US11368474B2 (en) | 2018-01-23 | 2022-06-21 | Rapid7, Inc. | Detecting anomalous internet behavior |
| US11470115B2 (en) | 2018-02-09 | 2022-10-11 | Attivo Networks, Inc. | Implementing decoys in a network environment |
| US11615208B2 (en) | 2018-07-06 | 2023-03-28 | Capital One Services, Llc | Systems and methods for synthetic data generation |
| US10404747B1 (en) * | 2018-07-24 | 2019-09-03 | Illusive Networks Ltd. | Detecting malicious activity by using endemic network hosts as decoys |
| US11209795B2 (en) | 2019-02-28 | 2021-12-28 | Nanotronics Imaging, Inc. | Assembly error correction for assembly lines |
| US12289321B2 (en) * | 2019-03-04 | 2025-04-29 | Microsoft Technology Licensing, Llc | Automated generation and deployment of honey tokens in provisioned resources on a remote computer resource platform |
| EP3918500B1 (en) * | 2019-03-05 | 2024-04-24 | Siemens Industry Software Inc. | Machine learning-based anomaly detections for embedded software applications |
| US11057428B1 (en) * | 2019-03-28 | 2021-07-06 | Rapid7, Inc. | Honeytoken tracker |
| WO2020236981A1 (en) | 2019-05-20 | 2020-11-26 | Sentinel Labs Israel Ltd. | Systems and methods for executable code detection, automatic feature extraction and position independent code detection |
| US10936712B1 (en) * | 2019-06-06 | 2021-03-02 | NortonLifeLock Inc. | Systems and methods for protecting users |
| US11156991B2 (en) | 2019-06-24 | 2021-10-26 | Nanotronics Imaging, Inc. | Predictive process control for a manufacturing process |
| CN110677408B (zh) * | 2019-07-09 | 2021-07-09 | 腾讯科技(深圳)有限公司 | 攻击信息的处理方法和装置、存储介质及电子装置 |
| CN110675228B (zh) * | 2019-09-27 | 2021-05-28 | 支付宝(杭州)信息技术有限公司 | 用户购票行为检测方法以及装置 |
| US11100221B2 (en) | 2019-10-08 | 2021-08-24 | Nanotronics Imaging, Inc. | Dynamic monitoring and securing of factory processes, equipment and automated systems |
| US11063965B1 (en) | 2019-12-19 | 2021-07-13 | Nanotronics Imaging, Inc. | Dynamic monitoring and securing of factory processes, equipment and automated systems |
| TW202223567A (zh) | 2019-11-06 | 2022-06-16 | 美商奈米創尼克影像公司 | 用於工廠自動化生產線之製造系統及方法 |
| US12153408B2 (en) | 2019-11-06 | 2024-11-26 | Nanotronics Imaging, Inc. | Systems, methods, and media for manufacturing processes |
| CN111308958B (zh) * | 2019-11-14 | 2021-04-20 | 广州安加互联科技有限公司 | 一种基于蜜罐技术的cnc设备仿真方法、系统和工控蜜罐 |
| WO2021102223A1 (en) | 2019-11-20 | 2021-05-27 | Nanotronics Imaging, Inc. | Securing industrial production from sophisticated attacks |
| CN113132293B (zh) * | 2019-12-30 | 2022-10-04 | 中国移动通信集团湖南有限公司 | 攻击检测方法、设备及公共蜜罐系统 |
| TWI892075B (zh) * | 2020-02-28 | 2025-08-01 | 美商奈米創尼克影像公司 | 用於智慧地模仿工廠控制系統及模擬回應資料之方法、系統及設備 |
| US11086988B1 (en) | 2020-02-28 | 2021-08-10 | Nanotronics Imaging, Inc. | Method, systems and apparatus for intelligently emulating factory control systems and simulating response data |
| CN111431891A (zh) * | 2020-03-20 | 2020-07-17 | 广州锦行网络科技有限公司 | 一种蜜罐部署方法 |
| CN111541670A (zh) * | 2020-04-17 | 2020-08-14 | 广州锦行网络科技有限公司 | 一种新型动态蜜罐系统 |
| US11030261B1 (en) * | 2020-08-06 | 2021-06-08 | Coupang Corp. | Computerized systems and methods for managing and monitoring services and modules on an online platform |
| CN112039861B (zh) * | 2020-08-20 | 2023-04-18 | 咪咕文化科技有限公司 | 风险识别方法、装置、电子设备和计算机可读存储介质 |
| US11824894B2 (en) * | 2020-11-25 | 2023-11-21 | International Business Machines Corporation | Defense of targeted database attacks through dynamic honeypot database response generation |
| US11720709B1 (en) | 2020-12-04 | 2023-08-08 | Wells Fargo Bank, N.A. | Systems and methods for ad hoc synthetic persona creation |
| US11579857B2 (en) | 2020-12-16 | 2023-02-14 | Sentinel Labs Israel Ltd. | Systems, methods and devices for device fingerprinting and automatic deployment of software in a computing network using a peer-to-peer approach |
| CN112788023B (zh) * | 2020-12-30 | 2023-02-24 | 成都知道创宇信息技术有限公司 | 基于安全网络的蜜罐管理方法及相关装置 |
| US11641366B2 (en) | 2021-01-11 | 2023-05-02 | Bank Of America Corporation | Centralized tool for identifying and blocking malicious communications transmitted within a network |
| US11386197B1 (en) | 2021-01-11 | 2022-07-12 | Bank Of America Corporation | System and method for securing a network against malicious communications through peer-based cooperation |
| US12289343B2 (en) | 2021-02-18 | 2025-04-29 | Ciena Corporation | Detecting malicious threats in a 5G network slice |
| US11777988B1 (en) * | 2021-03-09 | 2023-10-03 | Rapid7, Inc. | Probabilistically identifying anomalous honeypot activity |
| CN112800417B (zh) * | 2021-04-15 | 2021-07-06 | 远江盛邦(北京)网络安全科技股份有限公司 | 基于服务状态机的反馈式蜜罐系统的识别方法及系统 |
| WO2022246134A1 (en) * | 2021-05-20 | 2022-11-24 | Stairwell, Inc. | Real time threat knowledge graph |
| US11947694B2 (en) | 2021-06-29 | 2024-04-02 | International Business Machines Corporation | Dynamic virtual honeypot utilizing honey tokens and data masking |
| US11899782B1 (en) | 2021-07-13 | 2024-02-13 | SentinelOne, Inc. | Preserving DLL hooks |
| CN113609483B (zh) * | 2021-07-16 | 2024-05-03 | 山东云海国创云计算装备产业创新中心有限公司 | 一种服务器病毒处理的方法、装置、设备及可读介质 |
| US12401601B2 (en) | 2021-12-13 | 2025-08-26 | International Business Machines Corporation | Recertification of access control information based on context information estimated from network traffic |
| CN114168947B (zh) * | 2021-12-14 | 2022-10-25 | Tcl通讯科技(成都)有限公司 | 一种攻击检测方法、装置、电子设备及存储介质 |
| IT202100033158A1 (it) * | 2021-12-30 | 2023-06-30 | Thegg Domotica S R L | Dispositivo honeypot tailor-made e relativo metodo di realizzazione nel rispetto normativo di applicazione |
| US12452273B2 (en) | 2022-03-30 | 2025-10-21 | SentinelOne, Inc | Systems, methods, and devices for preventing credential passing attacks |
| US20230421562A1 (en) * | 2022-05-19 | 2023-12-28 | Capital One Services, Llc | Method and system for protection of cloud-based infrastructure |
| WO2024152041A1 (en) | 2023-01-13 | 2024-07-18 | SentinelOne, Inc. | Classifying cybersecurity threats using machine learning on non-euclidean data |
| US20240406173A1 (en) * | 2023-06-05 | 2024-12-05 | U.S. Army DEVCOM, Army Research Laboratory | System for automated process substitution with connection-preserving capabilities |
| KR102657010B1 (ko) * | 2023-12-04 | 2024-04-12 | 주식회사 심시스글로벌 | 샌드박스 기반의 가상 망 분리 방법 및 시스템 |
| CN119996025B (zh) * | 2025-02-28 | 2025-10-17 | 广州大学 | 一种基于gpt的高交互蜜点设计方法及系统 |
Citations (2)
| Publication number | Priority date | Publication date | Assignee | Title |
|---|---|---|---|---|
| JP2013514594A (ja) * | 2009-12-15 | 2013-04-25 | マカフィー, インコーポレイテッド | 挙動サンドボックスのためのシステム及び方法 |
| US20150161024A1 (en) * | 2013-12-06 | 2015-06-11 | Qualcomm Incorporated | Methods and Systems of Generating Application-Specific Models for the Targeted Protection of Vital Applications |
Family Cites Families (9)
| Publication number | Priority date | Publication date | Assignee | Title |
|---|---|---|---|---|
| US20050166072A1 (en) * | 2002-12-31 | 2005-07-28 | Converse Vikki K. | Method and system for wireless morphing honeypot |
| CN101185063A (zh) * | 2005-04-18 | 2008-05-21 | 纽约市哥伦比亚大学理事会 | 用于使用“蜜罐”检测和阻止攻击的系统和方法 |
| US9171157B2 (en) * | 2006-03-28 | 2015-10-27 | Blue Coat Systems, Inc. | Method and system for tracking access to application data and preventing data exploitation by malicious programs |
| CN101567887B (zh) * | 2008-12-25 | 2012-05-23 | 中国人民解放军总参谋部第五十四研究所 | 一种漏洞拟真超载蜜罐方法 |
| CN102088379B (zh) * | 2011-01-24 | 2013-03-13 | 国家计算机网络与信息安全管理中心 | 基于沙箱技术的客户端蜜罐网页恶意代码检测方法与装置 |
| EP2610776B1 (en) * | 2011-09-16 | 2019-08-21 | Veracode, Inc. | Automated behavioural and static analysis using an instrumented sandbox and machine learning classification for mobile security |
| US8739281B2 (en) * | 2011-12-06 | 2014-05-27 | At&T Intellectual Property I, L.P. | Multilayered deception for intrusion detection and prevention |
| CN103051615B (zh) * | 2012-12-14 | 2015-07-29 | 陈晶 | 一种蜜场系统中抗大流量攻击的动态防御系统 |
| CN103268448B (zh) * | 2013-05-24 | 2016-04-20 | 北京网秦天下科技有限公司 | 动态检测移动应用的安全性的方法和系统 |
-
2015
- 2015-11-09 US US14/935,522 patent/US20170134405A1/en not_active Abandoned
-
2016
- 2016-10-11 JP JP2018521349A patent/JP2018536932A/ja not_active Ceased
- 2016-10-11 BR BR112018009375A patent/BR112018009375A8/pt not_active Application Discontinuation
- 2016-10-11 KR KR1020187012814A patent/KR20180080227A/ko not_active Withdrawn
- 2016-10-11 EP EP16788852.8A patent/EP3375159B1/en active Active
- 2016-10-11 WO PCT/US2016/056438 patent/WO2017083043A1/en not_active Ceased
- 2016-10-11 CN CN201680062961.2A patent/CN108353078A/zh active Pending
- 2016-10-13 TW TW105132994A patent/TW201717088A/zh unknown
Patent Citations (3)
| Publication number | Priority date | Publication date | Assignee | Title |
|---|---|---|---|---|
| JP2013514594A (ja) * | 2009-12-15 | 2013-04-25 | マカフィー, インコーポレイテッド | 挙動サンドボックスのためのシステム及び方法 |
| US20130254884A1 (en) * | 2009-12-15 | 2013-09-26 | Mcafee, Inc. | Systems and methods for behavioral sandboxing |
| US20150161024A1 (en) * | 2013-12-06 | 2015-06-11 | Qualcomm Incorporated | Methods and Systems of Generating Application-Specific Models for the Targeted Protection of Vital Applications |
Also Published As
| Publication number | Publication date |
|---|---|
| TW201717088A (zh) | 2017-05-16 |
| EP3375159B1 (en) | 2020-03-18 |
| KR20180080227A (ko) | 2018-07-11 |
| BR112018009375A8 (pt) | 2019-02-26 |
| CN108353078A (zh) | 2018-07-31 |
| BR112018009375A2 (pt) | 2018-11-13 |
| EP3375159A1 (en) | 2018-09-19 |
| US20170134405A1 (en) | 2017-05-11 |
| WO2017083043A1 (en) | 2017-05-18 |
Similar Documents
| Publication | Publication Date | Title |
|---|---|---|
| EP3375159B1 (en) | Dynamic honeypot system | |
| KR102498168B1 (ko) | 적응형 기계 학습 피처들을 가진 사이버 보안 시스템 | |
| EP3314854B1 (en) | Router based securing of internet of things devices on local area networks | |
| US20200344257A1 (en) | Mobile risk assessment | |
| US20170206351A1 (en) | Mobile device security monitoring and notification | |
| US20130254880A1 (en) | System and method for crowdsourcing of mobile application reputations | |
| US20150180908A1 (en) | System and method for whitelisting applications in a mobile network environment | |
| US20130097659A1 (en) | System and method for whitelisting applications in a mobile network environment | |
| EP2348440A2 (en) | Collaborative malware detection and prevention on mobile devices | |
| US20140282908A1 (en) | Intelligent agent for privacy and security | |
| US9693233B2 (en) | Intelligent agent for privacy and security application | |
| CN112513848A (zh) | 隐私保护内容分类 | |
| KR20160145574A (ko) | 모바일 컴퓨팅에서의 보안을 강제하는 시스템 및 방법 | |
| CN117413490A (zh) | 检测并减轻基于蓝牙的攻击 | |
| Milosevic et al. | A resource-optimized approach to efficient early detection of mobile malware | |
| US10609030B1 (en) | Systems and methods for identifying untrusted devices in peer-to-peer communication | |
| US11132447B1 (en) | Determining security vulnerabilities of Internet of Things devices | |
| US12495051B2 (en) | Service level verification in distributed system | |
| Muthumanickam et al. | Research Article Demanding Requirement of Security for Wireless Mobile Devices: A Survey |
Legal Events
| Date | Code | Title | Description |
|---|---|---|---|
| A521 | Request for written amendment filed |
Free format text: JAPANESE INTERMEDIATE CODE: A523 Effective date: 20180510 |
|
| A521 | Request for written amendment filed |
Free format text: JAPANESE INTERMEDIATE CODE: A523 Effective date: 20190918 |
|
| A621 | Written request for application examination |
Free format text: JAPANESE INTERMEDIATE CODE: A621 Effective date: 20190918 |
|
| A977 | Report on retrieval |
Free format text: JAPANESE INTERMEDIATE CODE: A971007 Effective date: 20200903 |
|
| A01 | Written decision to grant a patent or to grant a registration (utility model) |
Free format text: JAPANESE INTERMEDIATE CODE: A01 Effective date: 20200914 |
|
| A045 | Written measure of dismissal of application [lapsed due to lack of payment] |
Free format text: JAPANESE INTERMEDIATE CODE: A045 Effective date: 20210125 |