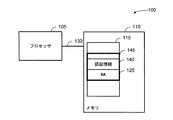
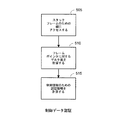
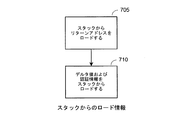
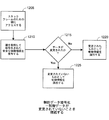
JP2017518661A - ハードウェアベースのスタック制御情報の保護 - Google Patents
ハードウェアベースのスタック制御情報の保護 Download PDFInfo
- Publication number
- JP2017518661A JP2017518661A JP2016560996A JP2016560996A JP2017518661A JP 2017518661 A JP2017518661 A JP 2017518661A JP 2016560996 A JP2016560996 A JP 2016560996A JP 2016560996 A JP2016560996 A JP 2016560996A JP 2017518661 A JP2017518661 A JP 2017518661A
- Authority
- JP
- Japan
- Prior art keywords
- control information
- stack
- processor
- secure
- generate
- Prior art date
- Legal status (The legal status is an assumption and is not a legal conclusion. Google has not performed a legal analysis and makes no representation as to the accuracy of the status listed.)
- Pending
Links
Images
Classifications
-
- G—PHYSICS
- G06—COMPUTING OR CALCULATING; COUNTING
- G06F—ELECTRIC DIGITAL DATA PROCESSING
- G06F11/00—Error detection; Error correction; Monitoring
- G06F11/36—Prevention of errors by analysis, debugging or testing of software
- G06F11/3604—Analysis of software for verifying properties of programs
- G06F11/3612—Analysis of software for verifying properties of programs by runtime analysis
-
- G—PHYSICS
- G06—COMPUTING OR CALCULATING; COUNTING
- G06F—ELECTRIC DIGITAL DATA PROCESSING
- G06F21/00—Security arrangements for protecting computers, components thereof, programs or data against unauthorised activity
- G06F21/50—Monitoring users, programs or devices to maintain the integrity of platforms, e.g. of processors, firmware or operating systems
- G06F21/55—Detecting local intrusion or implementing counter-measures
- G06F21/56—Computer malware detection or handling, e.g. anti-virus arrangements
-
- G—PHYSICS
- G06—COMPUTING OR CALCULATING; COUNTING
- G06F—ELECTRIC DIGITAL DATA PROCESSING
- G06F21/00—Security arrangements for protecting computers, components thereof, programs or data against unauthorised activity
- G06F21/50—Monitoring users, programs or devices to maintain the integrity of platforms, e.g. of processors, firmware or operating systems
- G06F21/52—Monitoring users, programs or devices to maintain the integrity of platforms, e.g. of processors, firmware or operating systems during program execution, e.g. stack integrity ; Preventing unwanted data erasure; Buffer overflow
-
- G—PHYSICS
- G06—COMPUTING OR CALCULATING; COUNTING
- G06F—ELECTRIC DIGITAL DATA PROCESSING
- G06F21/00—Security arrangements for protecting computers, components thereof, programs or data against unauthorised activity
- G06F21/50—Monitoring users, programs or devices to maintain the integrity of platforms, e.g. of processors, firmware or operating systems
- G06F21/52—Monitoring users, programs or devices to maintain the integrity of platforms, e.g. of processors, firmware or operating systems during program execution, e.g. stack integrity ; Preventing unwanted data erasure; Buffer overflow
- G06F21/54—Monitoring users, programs or devices to maintain the integrity of platforms, e.g. of processors, firmware or operating systems during program execution, e.g. stack integrity ; Preventing unwanted data erasure; Buffer overflow by adding security routines or objects to programs
Landscapes
- Engineering & Computer Science (AREA)
- Computer Security & Cryptography (AREA)
- Software Systems (AREA)
- Theoretical Computer Science (AREA)
- Computer Hardware Design (AREA)
- General Engineering & Computer Science (AREA)
- General Physics & Mathematics (AREA)
- Physics & Mathematics (AREA)
- Health & Medical Sciences (AREA)
- General Health & Medical Sciences (AREA)
- Virology (AREA)
- Quality & Reliability (AREA)
- Storage Device Security (AREA)
Applications Claiming Priority (3)
| Application Number | Priority Date | Filing Date | Title |
|---|---|---|---|
| US14/256,681 | 2014-04-18 | ||
| US14/256,681 US9390264B2 (en) | 2014-04-18 | 2014-04-18 | Hardware-based stack control information protection |
| PCT/US2015/025685 WO2015160759A1 (en) | 2014-04-18 | 2015-04-14 | Hardware-based stack control information protection |
Publications (2)
| Publication Number | Publication Date |
|---|---|
| JP2017518661A true JP2017518661A (ja) | 2017-07-06 |
| JP2017518661A5 JP2017518661A5 (enExample) | 2018-05-10 |
Family
ID=53039622
Family Applications (1)
| Application Number | Title | Priority Date | Filing Date |
|---|---|---|---|
| JP2016560996A Pending JP2017518661A (ja) | 2014-04-18 | 2015-04-14 | ハードウェアベースのスタック制御情報の保護 |
Country Status (7)
| Country | Link |
|---|---|
| US (1) | US9390264B2 (enExample) |
| EP (1) | EP3132374A1 (enExample) |
| JP (1) | JP2017518661A (enExample) |
| KR (1) | KR20160145014A (enExample) |
| CN (1) | CN106164872A (enExample) |
| BR (1) | BR112016024245A2 (enExample) |
| WO (1) | WO2015160759A1 (enExample) |
Cited By (2)
| Publication number | Priority date | Publication date | Assignee | Title |
|---|---|---|---|---|
| WO2023132210A1 (ja) * | 2022-01-07 | 2023-07-13 | ソニーセミコンダクタソリューションズ株式会社 | 情報処理装置および情報処理方法 |
| JP2023554266A (ja) * | 2020-12-16 | 2023-12-27 | インターナショナル・ビジネス・マシーンズ・コーポレーション | コンピューティング・システムにおけるソフトウェア・ポインタ認証のためのハードウェア・サポート |
Families Citing this family (14)
| Publication number | Priority date | Publication date | Assignee | Title |
|---|---|---|---|---|
| EP2993605A1 (en) * | 2014-09-02 | 2016-03-09 | Gemalto Sa | System and method for protecting a device against attacks on processing flow using a code pointer complement |
| US10248434B2 (en) * | 2015-10-27 | 2019-04-02 | Blackberry Limited | Launching an application |
| US10157268B2 (en) | 2016-09-27 | 2018-12-18 | Microsoft Technology Licensing, Llc | Return flow guard using control stack identified by processor register |
| US10360373B2 (en) * | 2016-09-28 | 2019-07-23 | Intel Corporation | Return address encryption |
| US10409981B2 (en) | 2017-04-21 | 2019-09-10 | International Business Machines Corporation | In-process stack memory protection |
| US10740452B2 (en) * | 2017-09-15 | 2020-08-11 | Arm Limited | Call path dependent authentication |
| WO2020079676A1 (en) * | 2018-10-18 | 2020-04-23 | Sternum Ltd. | Applying security mitigation measures for stack corruption exploitation in intermediate code files |
| US20200210626A1 (en) * | 2018-12-28 | 2020-07-02 | Samsung Electronics Co., Ltd. | Secure branch predictor with context-specific learned instruction target address encryption |
| CN109785537B (zh) * | 2018-12-29 | 2022-09-30 | 奇安信安全技术(珠海)有限公司 | 一种atm机的安全防护方法及装置 |
| US11232195B2 (en) * | 2019-07-29 | 2022-01-25 | Intertrust Technologies Corporation | Systems and methods for managing state |
| US20220277072A1 (en) * | 2019-08-16 | 2022-09-01 | Regents Of The University Of Michigan | Thwarting control plane attacks with displaced and dilated address spaces |
| US11784786B2 (en) * | 2020-08-14 | 2023-10-10 | Intel Corporation | Mitigating security vulnerabilities with memory allocation markers in cryptographic computing systems |
| GB2618116B (en) * | 2022-04-28 | 2025-10-22 | Advanced Risc Mach Ltd | Exception return state lock parameter |
| GB2620125B (en) * | 2022-06-28 | 2026-01-21 | Advanced Risc Mach Ltd | Methods and apparatus for pointer security |
Citations (3)
| Publication number | Priority date | Publication date | Assignee | Title |
|---|---|---|---|---|
| US20030065929A1 (en) * | 2001-09-28 | 2003-04-03 | Milliken Walter Clark | Method and program for inhibiting attack upon a computer |
| US20030182572A1 (en) * | 2001-12-06 | 2003-09-25 | Cowan Stanley Crispin | Pointguard: method and system for protecting programs against pointer corruption attacks |
| US20030217277A1 (en) * | 2002-05-15 | 2003-11-20 | Nokia, Inc. | Preventing stack buffer overflow attacks |
Family Cites Families (11)
| Publication number | Priority date | Publication date | Assignee | Title |
|---|---|---|---|---|
| EP1620997B1 (en) * | 2003-04-25 | 2014-10-15 | Koninklijke Philips N.V. | Overhead reduction and address protection in communication stack |
| US7856538B2 (en) * | 2005-12-12 | 2010-12-21 | Systex, Inc. | Methods, systems and computer readable medium for detecting memory overflow conditions |
| WO2012040198A1 (en) | 2010-09-20 | 2012-03-29 | Interdigital Patent Holdings, Inc. | Identity management on a wireless device |
| DE102012203521A1 (de) | 2011-03-28 | 2012-10-04 | International Business Machines Corp. | Architektur mit zwei Vertrauenswürdigkeitsstufen |
| US8839429B2 (en) | 2011-11-07 | 2014-09-16 | Qualcomm Incorporated | Methods, devices, and systems for detecting return-oriented programming exploits |
| US8776223B2 (en) | 2012-01-16 | 2014-07-08 | Qualcomm Incorporated | Dynamic execution prevention to inhibit return-oriented programming |
| US10210349B2 (en) | 2012-02-08 | 2019-02-19 | Arm Limited | Data processing apparatus and method using secure domain and less secure domain |
| US9037872B2 (en) * | 2012-12-17 | 2015-05-19 | Advanced Micro Devices, Inc. | Hardware based return pointer encryption |
| US20140173290A1 (en) * | 2012-12-17 | 2014-06-19 | Advanced Micro Devices, Inc. | Return address tracking mechanism |
| CA2809516C (en) * | 2013-03-13 | 2016-11-08 | Khalid Nawaf Alharbi | Preventing stack buffer overflow attacks |
| US9218467B2 (en) * | 2013-05-29 | 2015-12-22 | Raytheon Cyber Products, Llc | Intra stack frame randomization for protecting applications against code injection attack |
-
2014
- 2014-04-18 US US14/256,681 patent/US9390264B2/en active Active
-
2015
- 2015-04-14 WO PCT/US2015/025685 patent/WO2015160759A1/en not_active Ceased
- 2015-04-14 KR KR1020167028458A patent/KR20160145014A/ko not_active Withdrawn
- 2015-04-14 JP JP2016560996A patent/JP2017518661A/ja active Pending
- 2015-04-14 EP EP15719934.0A patent/EP3132374A1/en not_active Withdrawn
- 2015-04-14 BR BR112016024245A patent/BR112016024245A2/pt not_active IP Right Cessation
- 2015-04-14 CN CN201580019549.8A patent/CN106164872A/zh active Pending
Patent Citations (3)
| Publication number | Priority date | Publication date | Assignee | Title |
|---|---|---|---|---|
| US20030065929A1 (en) * | 2001-09-28 | 2003-04-03 | Milliken Walter Clark | Method and program for inhibiting attack upon a computer |
| US20030182572A1 (en) * | 2001-12-06 | 2003-09-25 | Cowan Stanley Crispin | Pointguard: method and system for protecting programs against pointer corruption attacks |
| US20030217277A1 (en) * | 2002-05-15 | 2003-11-20 | Nokia, Inc. | Preventing stack buffer overflow attacks |
Cited By (3)
| Publication number | Priority date | Publication date | Assignee | Title |
|---|---|---|---|---|
| JP2023554266A (ja) * | 2020-12-16 | 2023-12-27 | インターナショナル・ビジネス・マシーンズ・コーポレーション | コンピューティング・システムにおけるソフトウェア・ポインタ認証のためのハードウェア・サポート |
| JP7751953B2 (ja) | 2020-12-16 | 2025-10-09 | インターナショナル・ビジネス・マシーンズ・コーポレーション | コンピューティング・システムにおけるソフトウェア・ポインタ認証のためのハードウェア・サポート |
| WO2023132210A1 (ja) * | 2022-01-07 | 2023-07-13 | ソニーセミコンダクタソリューションズ株式会社 | 情報処理装置および情報処理方法 |
Also Published As
| Publication number | Publication date |
|---|---|
| WO2015160759A1 (en) | 2015-10-22 |
| KR20160145014A (ko) | 2016-12-19 |
| US20150302195A1 (en) | 2015-10-22 |
| US9390264B2 (en) | 2016-07-12 |
| BR112016024245A2 (pt) | 2017-08-15 |
| EP3132374A1 (en) | 2017-02-22 |
| CN106164872A (zh) | 2016-11-23 |
Similar Documents
| Publication | Publication Date | Title |
|---|---|---|
| US9390264B2 (en) | Hardware-based stack control information protection | |
| JP6266843B2 (ja) | ハードウェアフロー制御のためのコードポインタ認証 | |
| TWI567580B (zh) | 用於防止惡意軟體執行的方法與系統 | |
| US8397082B2 (en) | System and method for thwarting buffer overflow attacks using encrypted process pointers | |
| CN111052115B (zh) | 取决于调用路径的认证的数据处理装置和方法 | |
| KR101888712B1 (ko) | 운영 체제 구성 값 보호 기법 | |
| US8281115B2 (en) | Security method using self-generated encryption key, and security apparatus using the same | |
| CN107077562B (zh) | 用于动态控制代码执行的计算机实现的方法和系统 | |
| US20140237255A1 (en) | Decryption and Encryption of Application Data | |
| CN104392188A (zh) | 一种安全数据存储方法和系统 | |
| US9177121B2 (en) | Code protection using online authentication and encrypted code execution | |
| WO2017000648A1 (zh) | 一种被加固软件的认证方法及装置 | |
| KR20080100674A (ko) | 펌웨어의 무결성 검사 방법 및 장치 | |
| US20170046280A1 (en) | Data processing device and method for protecting a data processing device against attacks | |
| US9003201B2 (en) | Hardware protection for encrypted strings and protection of security parameters | |
| CN119026153A (zh) | 一种固件加密方法、装置、设备及可读存储介质 | |
| KR20080096054A (ko) | 데이터의 암호화 저장 방법 및 암호화된 데이터의 판독방법 | |
| US9560032B2 (en) | Method and apparatus for preventing illegitimate outflow of electronic document | |
| KR20220108152A (ko) | 비신뢰 메모리에 저장된 데이터에 대한 액세스를 제어하는 장치 및 방법 | |
| JP4474267B2 (ja) | 暗号処理装置 | |
| CN114547651A (zh) | 一种基于链式加密的操作系统中断上下文保护方法 |
Legal Events
| Date | Code | Title | Description |
|---|---|---|---|
| A521 | Request for written amendment filed |
Free format text: JAPANESE INTERMEDIATE CODE: A523 Effective date: 20161019 |
|
| A521 | Request for written amendment filed |
Free format text: JAPANESE INTERMEDIATE CODE: A523 Effective date: 20180320 |
|
| A621 | Written request for application examination |
Free format text: JAPANESE INTERMEDIATE CODE: A621 Effective date: 20180320 |
|
| A977 | Report on retrieval |
Free format text: JAPANESE INTERMEDIATE CODE: A971007 Effective date: 20181127 |
|
| A131 | Notification of reasons for refusal |
Free format text: JAPANESE INTERMEDIATE CODE: A131 Effective date: 20181210 |
|
| A02 | Decision of refusal |
Free format text: JAPANESE INTERMEDIATE CODE: A02 Effective date: 20190708 |